
Introduction
Security-Enhanced Linux (SELinux) is a powerful security feature integrated into many Linux distributions, including AlmaLinux. It provides a robust framework for enforcing access control policies, thereby enhancing the security of the system. Understanding the basic operations of SELinux is crucial for managing and securing your server effectively.
Operating Mode
SELinux is a set of kernel modifications and user-space tools that provide mandatory access control (MAC) security policies. It enables the system administrator to define access controls and policies that govern the interactions between processes and files, thereby preventing unauthorized access and potential security breaches.
This is the Basic Usage and Configuration for SELinux (Security-Enhanced Linux). It's possible to use MAC (Mandatory Access Control) feature on AlmaLinux for various resources by SELinux.
Step [1]Confirm the current status of SELinux like follows. (default mode is [Enforcing])
# display current mode
[root@vms ~]# getenforce
Enforcing
# enforcing ⇒ SELinux is enabled (default)
# permissive ⇒ MAC is not enabled, but only records audit logs according to Policies
# disabled ⇒ SELinux is disabled
# also possible to display with the command
[root@vms ~]# sestatus
SELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: targeted
Current mode: enforcing
Mode from config file: enforcing
Policy MLS status: enabled
Policy deny_unknown status: allowed
Memory protection checking: actual (secure)
Max kernel policy version: 33
Step [2]It's possible to switch current mode between [permissive] ⇔ [enforcing] with [setenforce] command. But if AlmaLinux System is restarted, the mode returns to default.
[root@vms ~]# getenforce
Enforcing
# switch to [Permissive] with [setenforce 0]
[root@vms ~]# setenforce 0
[root@vms ~]# getenforce
Permissive
# switch to [Enforcing] with [setenforce 1]
[root@vms ~]# setenforce 1
[root@vms ~]# getenforce
Enforcing
Step [3]If you'd like to change Operating Mode permanently, change value in Configuration file.
[root@vms ~]# vi /etc/selinux/config
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
# See also:
# https://docs.fedoraproject.org/en-US/quick-docs/getting-started-with-selinux/#getting-started-with-selinux-selinux-states-and-modes
#
# NOTE: In earlier Fedora kernel builds, SELINUX=disabled would also
# fully disable SELinux during boot. If you need a system with SELinux
# fully disabled instead of SELinux running with no policy loaded, you
# need to pass selinux=0 to the kernel command line. You can use grubby
# to persistently set the bootloader to boot with selinux=0:
#
# grubby --update-kernel ALL --args selinux=0
#
# To revert back to SELinux enabled:
#
# grubby --update-kernel ALL --remove-args selinux
#
# change value you'd like to set
SELINUX=enforcing
# SELINUXTYPE= can take one of these three values:
# targeted - Targeted processes are protected,
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
# restart to apply change
[root@vms ~]# reboot
Step [4]To disable SELinux, if you set [SELINUX=disabled] in configuration file as usual, SELinux runs with no policy loaded, however, if you'd like to fully disable it, add kernel parameter like follows.
# disable SELinux
[root@localhost ~]# grubby --update-kernel ALL --args selinux=0
# restart to appy changes
[root@localhost ~]# reboot
# to back to enabled, set like follows (need restarting)
[root@localhost ~]# grubby --update-kernel ALL --remove-args selinux
Step [5]If you change the Operating Mode from [Disabled] to [Enforcing/Permissive], it needs to re-label the filesystem with SELinux Contexts. Because when some files or directories are created in [Disabled] mode, they are not labeled with SELinux Contexts, it needs to label to them, too.
# run the command, then re-labeling will be run on next booting
[root@vms ~]# fixfiles -F onboot
System will relabel on next boot
# the file is created with the command above
[root@vms ~]# ll /.autorelabel
-rw-r--r--. 1 root root 3 Mar 10 19:34 /.autorelabel
Policy Type
If SELinux is in [Enforcing/Permissive], it's possible to choose Policy Type. You can modify the selected policy for your own environment if you need. It's possible to set Policy Type in [/etc/selinux/config] file. AlmaLinux 9 Default Policy is [targeted] Policy. However, if you change the Policy Type, it needs to install Policy File. For AlmaLinux 9 Minimal, only [targeted] Policy is installed by default. If you change to a Policy without installing Policy File, System will not start, so Be Careful well.
Step [1]Set Policy Type on [SELINUXTYPE=***] section.
# default is [targeted]
[root@vms ~]# cat /etc/selinux/config
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
# See also:
# https://docs.fedoraproject.org/en-US/quick-docs/getting-started-with-selinux/#getting-started-with-selinux-selinux-states-and-modes
#
# NOTE: In earlier Fedora kernel builds, SELINUX=disabled would also
# fully disable SELinux during boot. If you need a system with SELinux
# fully disabled instead of SELinux running with no policy loaded, you
# need to pass selinux=0 to the kernel command line. You can use grubby
# to persistently set the bootloader to boot with selinux=0:
#
# grubby --update-kernel ALL --args selinux=0
#
# To revert back to SELinux enabled:
#
# grubby --update-kernel ALL --remove-args selinux
#
SELINUX=enforcing
# SELINUXTYPE= can take one of these three values:
# targeted - Targeted processes are protected,
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
# for example, change to [mls] Policy
# install policy file first, don't forget it
[root@vms ~]# dnf -y install selinux-policy-mls
# policy file is installed under [minimum] directory
[root@vms ~]# ll /etc/selinux
total 8
-rw-r--r--. 1 root root 1187 Nov 25 18:03 config
drwxr-xr-x. 6 root root 150 Mar 10 20:06 mls
-rw-r--r--. 1 root root 2668 Feb 15 05:45 semanage.conf
drwxr-xr-x. 5 root root 133 Mar 10 19:04 targeted
[root@vms ~]# vi /etc/selinux/config
# change [SELINUXTYPE]
# change SELINUX mode to [permissive], too. to re-label files normally
.....
.....
SELINUX=permissive
# SELINUXTYPE= can take one of these three values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are proo
tected.
# mls - Multi Level Security protection.
SELINUXTYPE=mls
# set re-labeling and restart to apply changes
[root@vms ~]# fixfiles -F onboot
System will relabel on next boot
[root@vms ~]# reboot
[root@vms ~]# sestatus
SELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: mls
Current mode: permissive
Mode from config file: permissive
Policy MLS status: enabled
Policy deny_unknown status: denied
Memory protection checking: actual (secure)
Max kernel policy version: 33
Step [2]There are 2 kinds of Policies provided with RPM Package such as examples in Configuration file.
| Policy | Description |
| Targeted | This Policy applies Access Controls to Proccesses that they are often targeted by attacking. (Default) |
| MLS | Multilevel Security Policy. It implements Bell-LaPadula (BLP) model and possible to apply more complex controls. |
Context
Access Controls to files or directories are controled by additional informations that is called SELinux Context. SELinux Context has following syntax.
⇒ [SELinux User]:[Role]:[Type]:[Level]
| SELinux User | SELinux User Attribute Each Linux User is mapped to an SELinux User by SELinux Policy. |
| SELinux Role | RBAC (Role Based Access Control) Attribute It defines SELinux User's Roles. It controls Accesses which defined role can access to Domains by SELinux Policy. |
| SELinux Type | TE (Type Enforcement) Attribute It defines Domains for processes, and also defines Types for Files. |
| SELinux Level |
|
Step [1]For displaying SELinux Contexts for files or processes, add [Z] option to commands.
# files/directories
[root@vms ~]# ls -lZ /root
total 4
-rw-------. 1 root root system_u:object_r:admin_home_t:s0 1100 Nov 25 18:08 anaconda-ks.cfg
---------:--------:-------------:------
User : Role : Type : Level
# processes
[root@vms ~]# ps axZ
LABEL PID TTY STAT TIME COMMAND
system_u:system_r:init_t:s0 1 ? Ss 0:01 /usr/lib/systemd/systemd --switched-root --system --deserialize 31
system_u:system_r:kernel_t:s0 2 ? S 0:00 [kthreadd]
system_u:system_r:kernel_t:s0 3 ? I< 0:00 [rcu_gp]
system_u:system_r:kernel_t:s0 4 ? I< 0:00 [rcu_par_gp]
.....
.....
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1204 ? Ss 0:00 /usr/lib/systemd/systemd --user
system_u:system_r:init_t:s0 1206 ? S 0:00 (sd-pam)
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1213 ttyS0 Ss 0:00 -bash
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1238 ttyS0 R+ 0:00 ps axZ
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1239 ttyS0 S+ 0:00 tail -5
# own ID
[root@vms ~]# id -Z
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
Step [2]Each Linux User is mapped to an SELinux User by SELinux Policy. It's possible to show the mapping list like follows.
[root@vms ~]# semanage login -l
Login Name SELinux User MLS/MCS Range Service
__default__ unconfined_u s0-s0:c0.c1023 *
root unconfined_u s0-s0:c0.c1023 *
* if [semanage] command does not exist, install it
[root@vms ~]# dnf -y install policycoreutils-python-utils
For the example above (RHEL/AlmaLinux Default), [root] is mapped to [unconfined_u]. Other common users are mapped to [__default__] once and finally mapped to [unconfined_u]. [unconfined_u] users are assigned [unconfined_t] Role, and Processes which are started by [unconfined_u] users are run as [unconfined_t] Domain. Processes that [unconfined_t] Domain are assigned are not controled by SELinux.
[root@vms ~]# ps axZ | grep unconfined_t
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1204 ? Ss 0:00 /usr/lib/systemd/systemd --user
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1213 ttyS0 Ss 0:00 -bash
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1249 ttyS0 R+ 0:00 ps axZ
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1250 ttyS0 S+ 0:00 grep --color=auto unconfined_t
Boolean Values
On SELinux Policy provided with RPM package like [targeted], it's possible to change SELinux settings easily to switch Boolean Values. The example below is on [targeted] Policy environment.
Step [1]It's possible to confirm Boolean Values like follows.
# show the list and current settings
[root@vms ~]# getsebool -a
abrt_anon_write --> off
abrt_handle_event --> off
abrt_upload_watch_anon_write --> on
antivirus_can_scan_system --> off
antivirus_use_jit --> off
.....
.....
zabbix_run_sudo --> off
zarafa_setrlimit --> off
zebra_write_config --> off
zoneminder_anon_write --> off
zoneminder_run_sudo --> off
# show with descriptions
[root@vms ~]# semanage boolean -l
SELinux boolean State Default Description
abrt_anon_write (off , off) Allow abrt to anon write
abrt_handle_event (off , off) Allow abrt to handle event
abrt_upload_watch_anon_write (on , on) Allow abrt to upload watch anon write
antivirus_can_scan_system (off , off) Allow antivirus to can scan system
antivirus_use_jit (off , off) Allow antivirus to use jit
.....
.....
zabbix_run_sudo (off , off) Allow zabbix to run sudo
zarafa_setrlimit (off , off) Allow zarafa to setrlimit
zebra_write_config (off , off) Allow zebra to write config
zoneminder_anon_write (off , off) Allow zoneminder to anon write
zoneminder_run_sudo (off , off) Allow zoneminder to run sudo
* if [semanage] command does not exist, install it
[root@vms ~]# dnf -y install policycoreutils-python-utils
Step [2]For example, Configure [samba_enable_home_dirs] boolean value. [samba_enable_home_dirs] is set [off] by default, it means access control by SELinux is enabled. Even if you configured Samba with fully accessed share to [/home/share] (777), it's impossible to access to it because SELinux denies it because correct SELinux Context is not assigned to the Folder.
# set off by default
[root@vms ~]# semanage boolean -l | grep samba_enable_home_dirs
samba_enable_home_dirs (off , off) Allow samba to enable home dirs
Accesses are denied like follows even if files have read permission and parent directory has [777] permission.
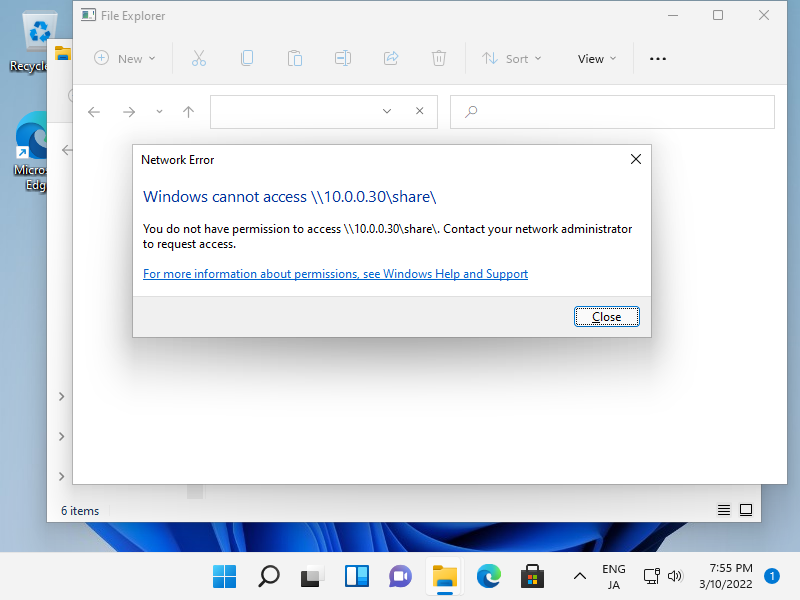
Step [3]Change Boolean Value of [samba_enable_home_dirs] to [on] to be able to access to the Folder normally.
# turn to ON [samba_enable_home_dirs]
[root@vms ~]# setsebool -P samba_enable_home_dirs on
[root@vms ~]# getsebool samba_enable_home_dirs
samba_enable_home_dirs --> on # changed
# restore to default SELinux Contexts for [samba_enable_home_dirs]
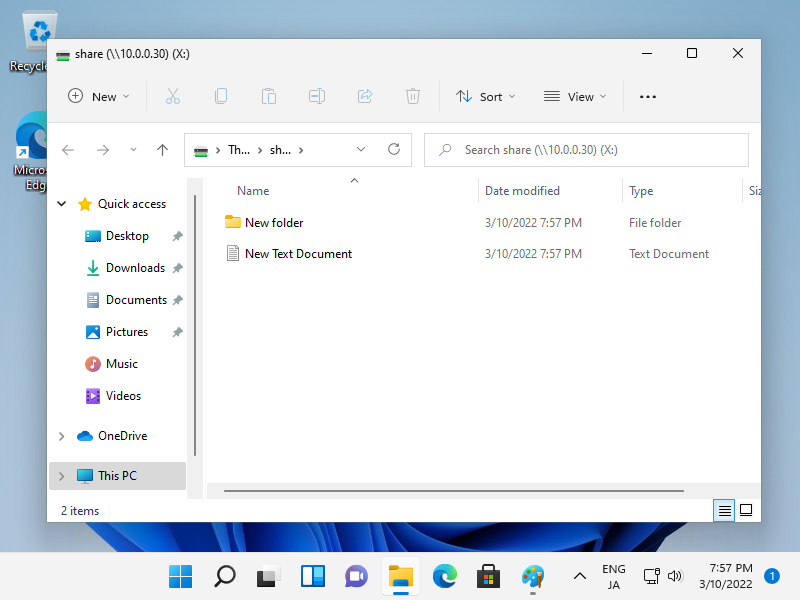
[root@vms ~]# restorecon -R /home/share
That's OK, it's possible to access to the Folder like follows.
File Types
It's possbile to modify access control settings to change File Type without changing boolean value. This example is based on [targeted] Policy environment.
Step [1]Settings of default SELinux Contexts are placed under the [(policy directory)/contexts/files] like follows.
[root@vms ~]# ll /etc/selinux/targeted/contexts/files
total 1020
-rw-r--r--. 1 root root 410080 Mar 10 21:56 file_contexts
-rw-r--r--. 1 root root 577846 Mar 10 21:56 file_contexts.bin
-rw-r--r--. 1 root root 15475 Mar 10 21:56 file_contexts.homedirs
-rw-r--r--. 1 root root 21219 Mar 10 21:56 file_contexts.homedirs.bin
-rw-r--r--. 1 root root 0 Feb 24 08:55 file_contexts.local
-rw-r--r--. 1 root root 0 Feb 24 08:55 file_contexts.subs
-rw-r--r--. 1 root root 651 Feb 24 08:55 file_contexts.subs_dist
-rw-r--r--. 1 root root 139 Feb 24 08:55 media
[root@vms ~]# head /etc/selinux/targeted/contexts/files/file_contexts
/.* system_u:object_r:default_t:s0
/[^/]+ -- system_u:object_r:etc_runtime_t:s0
/a?quota\.(user|group) -- system_u:object_r:quota_db_t:s0
/efi(/.*)? system_u:object_r:boot_t:s0
/nsr(/.*)? system_u:object_r:var_t:s0
/sys(/.*)? system_u:object_r:sysfs_t:s0
/xen(/.*)? system_u:object_r:xen_image_t:s0
/mnt(/[^/]*)? -d system_u:object_r:mnt_t:s0
/mnt(/[^/]*)? -l system_u:object_r:mnt_t:s0
/bin/.* system_u:object_r:bin_t:s0
Step [2]For example, Modify File Type for the case to use CGI on httpd. The boolean value for using CGI on httpd is set [on] by default, so it's possible to run CGI under the default directory [/var/www/cgi-bin/] on httpd settings with default SELinux settings.
[root@vms ~]# semanage boolean -l | grep httpd_enable_cgi
httpd_enable_cgi (on , on) Allow httpd to enable cgi
[root@vms ~]# grep "cgi" /etc/selinux/targeted/contexts/files/file_contexts | grep "httpd"
/opt/.*\.cgi -- system_u:object_r:httpd_sys_script_exec_t:s0
/usr/.*\.cgi -- system_u:object_r:httpd_sys_script_exec_t:s0
/var/www/[^/]*/cgi-bin(/.*)? system_u:object_r:httpd_sys_script_exec_t:s0
/var/www/html/[^/]*/cgi-bin(/.*)? system_u:object_r:httpd_sys_script_exec_t:s0
/usr/lib/cgi-bin(/.*)? system_u:object_r:httpd_sys_script_exec_t:s0
/var/www/cgi-bin(/.*)? system_u:object_r:httpd_sys_script_exec_t:s0
/usr/lib/cgi-bin/(nph-)?cgiwrap(d)? -- system_u:object_r:httpd_suexec_exec_t:s0
/var/log/cgiwrap\.log.* -- system_u:object_r:httpd_log_t:s0
# create a test script and access to it, then it's OK to access
[root@vms ~]# curl localhost/cgi-bin/index.py
CGI Test Page
However, if you'd like to use CGI on another directory, accesses are denied like follows even if httpd settings are correct.
[root@vms ~]# curl localhost/cgi-enabled/index.py
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>500 Internal Server Error</title>
</head><body>
<h1>Internal Server Error</h1>
<p>The server encountered an internal error or
misconfiguration and was unable to complete
your request.</p>
.....
.....
# [httpd_sys_content_t] is assinged
[root@vms ~]# ls -lZ /var/www/html/cgi-enabled
total 4
-rwxr-xr-x. 1 root root unconfined_u:object_r:httpd_sys_content_t:s0 96 Mar 10 22:07 index.py
On that case, it needs to change File Type to the one which SELinux allows CGI.
Step [3]Change File Type like follows. But be careful, this change with [chcon] command will be back when using [restorecon] command or re-label to filesystem.
[root@vms ~]# chcon -t httpd_sys_script_exec_t /var/www/html/cgi-enabled/index.py
[root@vms ~]# ls -lZ /var/www/html/cgi-enabled
total 4
-rwxr-xr-x. 1 root root unconfined_u:object_r:httpd_sys_script_exec_t:s0 96 Mar 10 22:07 index.py
[root@vms ~]# curl localhost/cgi-enabled/index.py
CGI Test Page # accessed
Step [4]If you'd like to change Types permanently, set like follows.
[root@vms ~]# semanage fcontext -a -t httpd_sys_script_exec_t /var/www/html/cgi-enabled/index.py
[root@vms ~]# grep "cgi-enabled" /etc/selinux/targeted/contexts/files/file_contexts.local
/var/www/html/cgi-enabled/index.py system_u:object_r:httpd_sys_script_exec_t:s0
# written as default Context
[root@vms ~]# ls -lZ /var/www/html/cgi-enabled
total 4
-rwxr-xr-x. 1 root root unconfined_u:object_r:httpd_sys_content_t:s0 96 Mar 10 22:07 index.py
# reset with [restotecon]
[root@vms ~]# restorecon /var/www/html/cgi-enabled/index.py
[root@vms ~]# ls -lZ /var/www/html/cgi-enabled
total 4
-rwxr-xr-x. 1 root root unconfined_u:object_r:httpd_sys_script_exec_t:s0 96 Mar 10 22:07 index.py
# restored
[root@vms ~]# curl localhost/cgi-enabled/index.py
CGI Test Page # accessed
Port Types
SELinux labels Types to network Ports, so it's impossible to start a Service with a port that Type is not configured.
Step [1]Show Type list for network Ports like follows.
[root@vms ~]# semanage port -l
SELinux Port Type Proto Port Number
afs3_callback_port_t tcp 7001
afs3_callback_port_t udp 7001
afs_bos_port_t udp 7007
afs_fs_port_t tcp 2040
afs_fs_port_t udp 7000, 7005
.....
.....
zented_port_t udp 1229
zookeeper_client_port_t tcp 2181
zookeeper_election_port_t tcp 3888
zookeeper_leader_port_t tcp 2888
zope_port_t tcp 8021
Step [2]For example, Set 82 Port for httpd. Default Port 80 for http and Port 443 for https are labeled with [http_port_t] like follows, but 82 is not set. So if you configured httpd.conf correctly with [listen 82], httpd will not start becuase SELinux denies it. If you'd like to use 82, add it to [http_port_t].
# show current settings
[root@vms ~]# semanage port -l | grep -E -w "80|443"
http_port_t tcp 80, 81, 443, 488, 8008, 8009, 8443, 9000
# add 82 Port
[root@vms ~]# semanage port -a -t http_port_t -p tcp 82
[root@vms ~]# semanage port -l | grep "^http_port_t"
http_port_t tcp 82, 80, 81, 443, 488, 8008, 8009, 8443, 9000
# just added
# after changing httpd.conf correctly, restart httpd and verify running
[root@vms ~]# ss -napt | grep httpd
LISTEN 0 511 *:82 *:* users:(("httpd",pid=2491,fd=4),("httpd",pid=2490,fd=4),("httpd",pid=2489,fd=4),("httpd",pid=2485,fd=4))
# httpd is listening on 82
Logs
Access OK or Deny decisions by SELinux are cached once and Denial Accesses are sent to Log files. Cache of SELinux is called AVC (Access Vector Cache) and Denial Accesses are called [AVC Denials]. AVC Denial Log is generated via Systemd Journald or Audit Service, so it needs either of service is running. If Rsyslog Service is running (enabled by default), logs are also put on [/var/log/messages].
Step [1]When Systemd Journald or Rsyslog service is enabled, AVC Denial Logs are recorded to Journald and [/var/log/messages].
[root@vms ~]# journalctl -t setroubleshoot
Mar 10 21:57:34 vms.bizantum.lab setroubleshoot[1840]: AnalyzeThread.run(): Cancel>
Mar 10 21:57:34 vms.bizantum.lab setroubleshoot[1840]: failed to retrieve rpm info>
Mar 10 21:57:35 vms.bizantum.lab setroubleshoot[1840]: SELinux is preventing /usr/>
Mar 10 21:57:35 vms.bizantum.lab setroubleshoot[1840]: SELinux is preventing /usr/>
.....
.....
[root@vms ~]# grep "setroubleshoot" /var/log/messages
Mar 10 21:57:35 vms setroubleshoot[1840]: SELinux is preventing /usr/sbin/smbd from watch access on the directory /home/share. For complete SELinux messages run: sealert -l 08f68245-f415-4f55-a5d5-7a9a27beba12
Mar 10 21:57:35 vms setroubleshoot[1840]: SELinux is preventing /usr/sbin/smbd from watch access on the directory /home/share.#012#012***** Plugin catchall_boolean (89.3 confidence) suggests ******************#012#012If you want to allow samba to export all rw#012Then you must tell SELinux about this by enabling the 'samba_export_all_rw' boolean.#012#012Do#012setsebool -P samba_export_all_rw 1#012#012***** Plugin catchall (11.6 confidence) suggests **************************#012#012If you believe that smbd should be allowed watch access on the share directory by default.#012Then you should report this as a bug.#012You can generate a local policy module to allow this access.#012Do#012allow this access for now by executing:#012# ausearch -c 'smbd-notifyd' --raw | audit2allow -M my-smbdnotifyd#012# semodule -X 300 -i my-smbdnotifyd.pp#012
Step [2]When Audit service is enabled, AVC Denial Logs are recorded to [/var/log/audit/audit.log].
[root@vms ~]# grep "avc: .denied" /var/log/audit/audit.log
type=AVC msg=audit(1644986614.918:178): avc: denied { mac_admin } for pid=1933 comm="restorecon" capability=33 scontext=unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 tcontext=unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 tclass=capability2 permissive=0
type=AVC msg=audit(1646971053.926:140): avc: denied { watch } for pid=1794 comm="smbd-notifyd" path="/home/share" dev="dm-0" ino=61100 scontext=system_u:system_r:smbd_t:s0 tcontext=unconfined_u:object_r:user_home_dir_t:s0 tclass=dir permissive=0
type=AVC msg=audit(1646971053.927:141): avc: denied { watch } for pid=1794 comm="smbd-notifyd" path="/home/share" dev="dm-0" ino=61100 scontext=system_u:system_r:smbd_t:s0 tcontext=unconfined_u:object_r:user_home_dir_t:s0 tclass=dir permissive=0
Step [3]For Messages via Auditd, it's possible to search them with [ausearch] command.
[root@vms ~]# ausearch -m AVC
----
time->Thu Mar 10 21:57:33 2022
type=PROCTITLE msg=audit(1646971053.926:140): proctitle=2F7573722F7362696E2F736D6264002D2D666F726567726F756E64002D2D6E6F2D70726F636573732D67726F7570
type=SYSCALL msg=audit(1646971053.926:140): arch=c000003e syscall=254 success=no exit=-13 a0=f a1=7ffcf269679c a2=210003c0 a3=7ffcf2695fd0 items=0 ppid=1792 pid=1794 auid=4294967295 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=(none) ses=4294967295 comm="smbd-notifyd" exe="/usr/sbin/smbd" subj=system_u:system_r:smbd_t:s0 key=(null)
type=AVC msg=audit(1646971053.926:140): avc: denied { watch } for pid=1794 comm="smbd-notifyd" path="/home/share" dev="dm-0" ino=61100 scontext=system_u:system_r:smbd_t:s0 tcontext=unconfined_u:object_r:user_home_dir_t:s0 tclass=dir permissive=0
----
time->Thu Mar 10 21:57:33 2022
type=PROCTITLE msg=audit(1646971053.927:141): proctitle=2F7573722F7362696E2F736D6264002D2D666F726567726F756E64002D2D6E6F2D70726F636573732D67726F7570
type=SYSCALL msg=audit(1646971053.927:141): arch=c000003e syscall=254 success=no exit=-13 a0=f a1=7ffcf269679c a2=210003c6 a3=7ffcf2696740 items=0 ppid=1792 pid=1794 auid=4294967295 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=(none) ses=4294967295 comm="smbd-notifyd" exe="/usr/sbin/smbd" subj=system_u:system_r:smbd_t:s0 key=(null)
type=AVC msg=audit(1646971053.927:141): avc: denied { watch } for pid=1794 comm="smbd-notifyd" path="/home/share" dev="dm-0" ino=61100 scontext=system_u:system_r:smbd_t:s0 tcontext=unconfined_u:object_r:user_home_dir_t:s0 tclass=dir permissive=0
Step [4]For Messages via Auditd, it's possible to show summary reports with [aureport] command.
[root@vms ~]# aureport --avc
AVC Report
===============================================================
# date time comm subj syscall class permission obj result event
===============================================================
1. 02/15/2022 22:43:19 restorecon unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 189 capability2 mac_admin unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 denied 166
2. 02/15/2022 22:43:19 restorecon unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 189 capability2 mac_admin unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 denied 167
3. 02/15/2022 22:43:19 restorecon unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 189 capability2 mac_admin unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 denied 168
4. 02/15/2022 22:43:34 restorecon unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 189 capability2 mac_admin unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 denied 175
5. 02/15/2022 22:43:34 restorecon unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 189 capability2 mac_admin unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 denied 176
6. 02/15/2022 22:43:34 restorecon unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 189 capability2 mac_admin unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 denied 177
7. 02/15/2022 22:43:34 restorecon unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 189 capability2 mac_admin unconfined_u:unconfined_r:setfiles_t:s0-s0:c0.c1023 denied 178
8. 03/10/2022 21:57:33 smbd-notifyd system_u:system_r:smbd_t:s0 254 dir watch unconfined_u:object_r:user_home_dir_t:s0 denied 140
9. 03/10/2022 21:57:33 smbd-notifyd system_u:system_r:smbd_t:s0 254 dir watch unconfined_u:object_r:user_home_dir_t:s0 denied 141
SETroubleShoot
To use SETroubleShoot, it's possible to generate additional information for solving SELinux related troubles.
Step [1]Messages from SETroubleShoot are sent by Audit Event Dispatcher to Systemd Journald. (or [/var/log/messages] if Rsyslog enabled) So it needs to run Auditd, refer to here.
Step [2]SETroubleShoot is installed by default if Base Environment is [Server] or others, but if not, Install it.
[root@vms ~]# dnf -y install setroubleshoot-server
Step [3]Additional logs for AVC denial are recorded to Systemd Journald or [/var/log/messages] if Rsyslog is enabled. The logs follows are the one in [/var/log/messages].
[root@vms ~]# grep -E 'setroubleshoot|preventing' /var/log/messages
Mar 10 22:34:41 vms setroubleshoot[2766]: SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port 83. For complete SELinux messages run: sealert -l b0323261-b091-4750-b126-65254d2fa04e
Mar 10 22:34:41 vms setroubleshoot[2766]: SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port 83.#012#012***** Plugin bind_ports (99.5 confidence) suggests ************************#012#012If you want to allow /usr/sbin/httpd to bind to network port 83#012Then you need to modify the port type.#012Do#012# semanage port -a -t PORT_TYPE -p tcp 83#012 where PORT_TYPE is one of the following: http_cache_port_t, http_port_t, jboss_management_port_t, jboss_messaging_port_t, ntop_port_t, puppet_port_t.#012#012***** Plugin catchall (1.49 confidence) suggests **************************#012#012If you believe that httpd should be allowed name_bind access on the port 83 tcp_socket by default.#012Then you should report this as a bug.#012You can generate a local policy module to allow this access.#012Do#012allow this access for now by executing:#012# ausearch -c 'httpd' --raw | audit2allow -M my-httpd#012# semodule -X 300 -i my-httpd.pp#012
Step [4]For the 2nd line on the example above, a command is given to see more details and it displays logs like follows.
[root@vms ~]# sealert -l b0323261-b091-4750-b126-65254d2fa04e
SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port 83.
***** Plugin bind_ports (99.5 confidence) suggests ************************
If you want to allow /usr/sbin/httpd to bind to network port 83
Then you need to modify the port type.
Do
# semanage port -a -t PORT_TYPE -p tcp 83
where PORT_TYPE is one of the following: http_cache_port_t, http_port_t, jboss_management_port_t, jboss_messaging_port_t, ntop_port_t, puppet_port_t.
***** Plugin catchall (1.49 confidence) suggests **************************
If you believe that httpd should be allowed name_bind access on the port 83 tcp_socket by default.
Then you should report this as a bug.
You can generate a local policy module to allow this access.
Do
allow this access for now by executing:
# ausearch -c 'httpd' --raw | audit2allow -M my-httpd
# semodule -X 300 -i my-httpd.pp
Additional Information:
Source Context system_u:system_r:httpd_t:s0
Target Context system_u:object_r:reserved_port_t:s0
Target Objects port 83 [ tcp_socket ]
Source httpd
Source Path /usr/sbin/httpd
Port 83
Host vms.bizantum.lab
Source RPM Packages httpd-2.4.51-5.el9.x86_64
Target RPM Packages
SELinux Policy RPM selinux-policy-targeted-34.1.27-1.el9.noarch
Local Policy RPM selinux-policy-targeted-34.1.27-1.el9.noarch
Selinux Enabled True
Policy Type targeted
Enforcing Mode Enforcing
Host Name vms.bizantum.lab
Platform Linux vms.bizantum.lab 5.14.0-70.el9.x86_64 #1 SMP
PREEMPT Thu Feb 24 23:01:31 UTC 2022 x86_64 x86_64
Alert Count 2
First Seen 2022-03-10 22:34:35 CST
Last Seen 2022-03-10 22:34:35 CST
Local ID b0323261-b091-4750-b126-65254d2fa04e
Raw Audit Messages
type=AVC msg=audit(1646973275.751:212): avc: denied { name_bind } for pid=2764 comm="httpd" src=83 scontext=system_u:system_r:httpd_t:s0 tcontext=system_u:object_r:reserved_port_t:s0 tclass=tcp_socket permissive=0
type=SYSCALL msg=audit(1646973275.751:212): arch=x86_64 syscall=bind success=no exit=EACCES a0=3 a1=5620265828b8 a2=10 a3=7fffb309a56c items=0 ppid=1 pid=2764 auid=4294967295 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=(none) ses=4294967295 comm=httpd exe=/usr/sbin/httpd subj=system_u:system_r:httpd_t:s0 key=(null)
Hash: httpd,httpd_t,reserved_port_t,tcp_socket,name_bind
Audit2allow
Using [audit2allow] command, it's possible to generate SELinux policy allow rules easily from logs of denied operations. However, [audit2allow] may allow more access than required, so it's better to configure with [restorecon] or [chcon] command in cases. By the way, if [audit2allow] is none on your System, Install with [dnf install policycoreutils-python-utils].
Step [1]Display denial reasons to read log files. If not specified any log file, audit2allow reads [/var/log/audit/audit.log]. If specify log files, set [-i logfile] option instead [-a] option.
# display reason for AVC denials from reading audit.log
[root@vms ~]# audit2allow -w -a
type=AVC msg=audit(1646973275.750:211): avc: denied { name_bind } for pid=2764 comm="httpd" src=83 scontext=system_u:system_r:httpd_t:s0 tcontext=system_u:object_r:reserved_port_t:s0 tclass=tcp_socket permissive=0
Was caused by:
Missing type enforcement (TE) allow rule.
You can use audit2allow to generate a loadable module to allow this access.
type=AVC msg=audit(1646973275.751:212): avc: denied { name_bind } for pid=2764 comm="httpd" src=83 scontext=system_u:system_r:httpd_t:s0 tcontext=system_u:object_r:reserved_port_t:s0 tclass=tcp_socket permissive=0
Was caused by:
Missing type enforcement (TE) allow rule.
You can use audit2allow to generate a loadable module to allow this access.
.....
.....
# for example, use ausearch to display specific logs
[root@vms ~]# ausearch -m AVC --start 03/10/2022 12:00:00 --end 03/11/2022 18:00:00 | audit2allow -w
type=AVC msg=audit(1646973275.750:211): avc: denied { name_bind } for pid=2764 comm="httpd" src=83 scontext=system_u:system_r:httpd_t:s0 tcontext=system_u:object_r:reserved_port_t:s0 tclass=tcp_socket permissive=0
Was caused by:
Missing type enforcement (TE) allow rule.
You can use audit2allow to generate a loadable module to allow this access.
type=AVC msg=audit(1646973275.751:212): avc: denied { name_bind } for pid=2764 comm="httpd" src=83 scontext=system_u:system_r:httpd_t:s0 tcontext=system_u:object_r:reserved_port_t:s0 tclass=tcp_socket permissive=0
Was caused by:
Missing type enforcement (TE) allow rule.
You can use audit2allow to generate a loadable module to allow this access.
.....
.....
# display required type with -a option
[root@vms ~]# ausearch -m AVC --start 03/10/2022 12:00:00 --end 03/11/2022 18:00:00 | audit2allow -a
#============= httpd_t ==============
allow httpd_t reserved_port_t:tcp_socket name_bind;
#============= smbd_t ==============
#!!!! This avc can be allowed using the boolean 'samba_export_all_rw'
allow smbd_t user_home_dir_t:dir watch;
Step [2]Generate allow rule like follows.
# for example, generate [test_rule] module
[root@vms ~]# ausearch -m AVC --start 03/10/2022 12:00:00 --end 03/11/2022 18:00:00 | audit2allow -a -M test_rule
******************** IMPORTANT ***********************
To make this policy package active, execute:
semodule -i test_rule.pp
# install module with the command displayed above
[root@vms ~]# semodule -i test_rule.pp
# make sure the module is loaded
[root@vms ~]# semodule -l | grep test_rule
test_rule
That's OK in some cases, but for other cases, it's not yet. If not yet, run [audit2allow] again and make sure the causes.
Matchpathcon
Display Default SELinux Context for the specified Path to use [matchpathcon] command.
Step [1]Some examples of using [matchpathcon] are follows.
# show the default for [/var/www/html/index.html]
[root@vms ~]# matchpathcon /var/www/html/index.html
/var/www/html/index.html system_u:object_r:httpd_sys_content_t:s0
# compare the current context and the default of [/var/www/html]
# if not differ, it shows [verified]
[root@vms ~]# matchpathcon -V /var/www/html
/var/www/html verified.
# compare the current context and the default of [/var/www/html/index.html]
# if differ, it shows like follows
[root@vms ~]# matchpathcon -V /var/www/html/index.html
/var/www/html/index.html has context unconfined_u:object_r:httpd_sys_script_exec_t:s0, should be system_u:object_r:httpd_sys_content_t:s0
# possible to specify target with wildcards
[root@vms ~]# matchpathcon -V /var/www/html/*
/var/www/html/cgi-enabled verified.
/var/www/html/index.html has context unconfined_u:object_r:httpd_sys_script_exec_t:s0, should be system_u:object_r:httpd_sys_content_t:s0
/var/www/html/index.py verified.
Sesearch
Search SELinux Policy to use [sesearch] command.
Step [1]Some examples of using [sesearch] are follows. If [sesearch] command is none, Install it with [dnf install setools-console].
# display allowed rules all (many rules displayed)
[root@vms ~]# sesearch --allow
allow NetworkManager_etc_rw_t NetworkManager_etc_rw_t:filesystem associate;
allow NetworkManager_etc_t NetworkManager_etc_t:filesystem associate;
allow NetworkManager_exec_t NetworkManager_exec_t:filesystem associate;
allow NetworkManager_initrc_exec_t NetworkManager_initrc_exec_t:filesystem associate;
allow NetworkManager_log_t NetworkManager_log_t:filesystem associate;
allow NetworkManager_ssh_t NetworkManager_ssh_t:anon_inode { create getattr ioctl read write };
allow NetworkManager_ssh_t NetworkManager_ssh_t:association sendto;
allow NetworkManager_ssh_t NetworkManager_ssh_t:capability { dac_read_search setgid setuid };
allow NetworkManager_ssh_t NetworkManager_ssh_t:dbus send_msg;
allow NetworkManager_ssh_t NetworkManager_ssh_t:dir { getattr ioctl lock open read search };
.....
.....
# display rules which [httpd_t] domain is allowed to access
[root@vms ~]# sesearch -s httpd_t --allow
allow corenet_unlabeled_type unlabeled_t:association { recvfrom sendto };
allow corenet_unlabeled_type unlabeled_t:dccp_socket recvfrom;
allow corenet_unlabeled_type unlabeled_t:peer recv;
allow corenet_unlabeled_type unlabeled_t:rawip_socket recvfrom;
allow corenet_unlabeled_type unlabeled_t:tcp_socket recvfrom;
allow corenet_unlabeled_type unlabeled_t:udp_socket recvfrom;
allow daemon abrt_t:unix_stream_socket connectto;
allow daemon abrt_var_run_t:sock_file { append getattr open write };
allow daemon auth_port_t:tcp_socket name_connect; [ daemons_use_tcp_wrapper ]:True
allow daemon cluster_conf_t:dir { add_name create getattr ioctl link lock open read remove_name rename reparent rmdir search setattr unlink watch watch_reads write }; [ daemons_enable_cluster_mode ]:True
.....
.....
# display allowed rules which domain can access to [httpd_sys_script_exec_t] type
[root@vms ~]# sesearch -t httpd_sys_script_exec_t --allow
allow NetworkManager_ssh_t file_type:filesystem getattr;
allow NetworkManager_t file_type:filesystem getattr;
allow abrt_dump_oops_t file_type:filesystem getattr;
allow abrt_dump_oops_t non_security_file_type:dir { add_name create getattr ioctl link lock open read remove_name rename reparent rmdir search setattr unlink watch watch_reads write };
allow abrt_dump_oops_t non_security_file_type:file { append create getattr ioctl link lock map open read rename setattr unlink watch watch_reads write };
allow abrt_dump_oops_t non_security_file_type:lnk_file { append create getattr ioctl link lock read rename setattr unlink watch watch_reads write };
allow abrt_helper_t exec_type:dir { getattr open search };
allow abrt_helper_t exec_type:file { getattr ioctl lock open read };
allow abrt_helper_t file_type:filesystem getattr;
allow abrt_t exec_type:file { execute execute_no_trans ioctl lock map open read };
.....
.....
# display allowed rules which domain can write to [shadow_t type] files
[root@vms ~]# sesearch -t shadow_t -c file -p write --allow
allow cockpit_session_t shadow_t:file { append create getattr ioctl link lock open read rename setattr unlink watch watch_reads write };
allow files_unconfined_type file_type:file { append audit_access create execute execute_no_trans getattr ioctl link lock map mounton open quotaon read relabelfrom relabelto rename setattr swapon unlink watch watch_mount watch_reads watch_sb watch_with_perm write };
allow groupadd_t shadow_t:file { append create getattr ioctl link lock open read relabelfrom relabelto rename setattr unlink watch watch_reads write };
allow passwd_t shadow_t:file { append create getattr ioctl link lock map open read relabelfrom relabelto rename setattr unlink watch watch_reads write };
allow pegasus_openlmi_account_t shadow_t:file { append create getattr ioctl link lock open read relabelfrom relabelto rename setattr unlink watch watch_reads write };
allow sysadm_passwd_t shadow_t:file { append create getattr ioctl link lock open read relabelfrom relabelto rename setattr unlink watch watch_reads write };
allow updpwd_t shadow_t:file { append create getattr ioctl link lock open read rename setattr unlink watch watch_reads write };
allow useradd_t shadow_t:file { append create getattr ioctl link lock open read relabelfrom relabelto rename setattr unlink watch watch_reads write };
allow yppasswdd_t shadow_t:file { append create getattr ioctl link lock open read relabelfrom relabelto rename setattr unlink watch watch_reads write };
.....
.....
# display defined rules on Boolean value [samba_enable_home_dirs]
[root@vms ~]# sesearch -b samba_enable_home_dirs --allow
allow smbd_t httpd_user_content_t:dir { add_name create getattr ioctl link lock open read remove_name rename reparent rmdir search setattr unlink watch watch_reads write }; [ samba_enable_home_dirs ]:True
allow smbd_t httpd_user_content_t:dir { add_name getattr ioctl lock open read remove_name search write }; [ samba_enable_home_dirs ]:True
allow smbd_t httpd_user_content_t:dir { add_name getattr ioctl lock open read remove_name search write }; [ samba_enable_home_dirs ]:True
allow smbd_t httpd_user_content_t:file { append create getattr ioctl link lock open read rename setattr unlink watch watch_reads write }; [ samba_enable_home_dirs ]:True
allow smbd_t httpd_user_content_t:lnk_file { append create getattr ioctl link lock read rename setattr unlink watch watch_reads write }; [ samba_enable_home_dirs ]:True
allow smbd_t user_home_dir_t:dir { add_name ioctl lock read remove_name write }; [ samba_enable_home_dirs ]:True
allow smbd_t user_home_dir_t:dir { add_name ioctl lock read remove_name write }; [ samba_enable_home_dirs ]:True
allow smbd_t user_home_dir_t:dir { add_name ioctl lock read remove_name write }; [ samba_enable_home_dirs ]:True
allow smbd_t user_home_dir_t:dir { add_name ioctl lock read remove_name write }; [ samba_enable_home_dirs ]:True
allow smbd_t user_home_dir_t:dir { add_name ioctl lock read remove_name write }; [ samba_enable_home_dirs ]:True
.....
.....
- Get link
- X
- Other Apps








Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.