
Introduction
In this guide, we will walk you through the steps to configure both Network Time Protocol (NTP) and Secure Shell (SSH) on AlmaLinux 9. NTP ensures that your server's clock is synchronized with a reliable time source, which is crucial for various network services and applications. SSH, on the other hand, provides a secure method for remote login and file transfer between your server and clients.
Configure NTP
NTP ensures that your server's clock is synchronized with a reliable time source, which is crucial for various network services and applications.
NTP Server
Step [1]Install and Configure Chrony.
[root@dlp ~]# dnf -y install chrony
[root@dlp ~]# vi /etc/chrony.conf
# line 3 : change servers to synchronize (replace to your own timezone NTP server)
# need NTP server itself to sync time with other NTP server
#pool 2.almalinux.pool.ntp.org iburst
pool ntp.nict.jp iburst
# line 27 : add network range to allow to receive time synchronization requests from NTP Clients
# specify your local network and so on
# if not specified, only localhost is allowed
allow 10.0.0.0/24
[root@dlp ~]# systemctl enable --now chronyd
Step [2]If Firewalld is running, allow NTP service. NTP uses [123/UDP].
[root@dlp ~]# firewall-cmd --add-service=ntp
success
[root@dlp ~]# firewall-cmd --runtime-to-permanent
success
Step [3]Verify it works normally.
[root@dlp ~]# chronyc sources
MS Name/IP address Stratum Poll Reach LastRx Last sample
===============================================================================
^+ ntp-b3.nict.go.eu 1 6 17 33 -794us[ -129us] +/- 9285us
^+ ntp-a3.nict.go.eu 1 6 17 34 +851us[+1515us] +/- 8783us
^- ntp-b2.nict.go.eu 1 6 17 34 -736us[ -736us] +/- 9296us
^* ntp-a2.nict.go.eu 1 6 17 34 -4982ns[ +659us] +/- 9399us
NTP Client
Step [1]NTP Client configuration is mostly the same with the Server's one, however, NTP Clients do not need to receive time synchronization requests from other hosts, so it does not need to specify the line [allow ***].
[root@node01 ~]# dnf -y install chrony
[root@node01 ~]# vi /etc/chrony.conf
# line 3 : change to your own NTP server or others in your timezone
#pool 2.almalinux.pool.ntp.org iburst
pool dlp.bizantum.lab iburst
[root@node01 ~]# systemctl enable --now chronyd
# verify status
[root@node01 ~]# chronyc sources
MS Name/IP address Stratum Poll Reach LastRx Last sample
===============================================================================
^* dlp.bizantum.lab 2 6 7 1 +101us[ -396us] +/- 10ms
Step [1]To Install NTPStat, it's possible to display time synchronization status.
[root@node01 ~]# dnf -y install ntpstat
[root@node01 ~]# ntpstat
synchronised to NTP server (10.0.0.30) at stratum 3
time correct to within 11 ms
polling server every 64 s
Configure SSH Server
SSH, on the other hand, provides a secure method for remote login and file transfer between your server and clients.
Password Authentication
Step [1]OpenSSH is already installed by default even if you installed AlmaLinux with [Minimal] Install, so it does not need to install new packages. You can login with Password Authentication by default. If you like to improve the security, you should change PermitRootLogin parameter.
[root@dlp ~]# vi /etc/ssh/sshd_config
# line 40: change ( prohibit root login )
# for other options, there are [prohibit-password], [forced-commands-only]
PermitRootLogin no
[root@dlp ~]# systemctl restart sshd
Step [2]If Firewalld is running, allow SSH service. SSH uses [22/TCP].
[root@dlp ~]# firewall-cmd --add-service=ssh
success
[root@dlp ~]# firewall-cmd --runtime-to-permanent
success
Step [3]Configure SSH Client for AlmaLinux. Install SSH Client.
[root@node01 ~]# dnf -y install openssh-clients
Step [4]Connect to SSH server with any common user.
# ssh [username@(hostname or IP address)]
[alma@node01 ~]$ ssh alma@dlp.bizantum.lab
The authenticity of host 'dlp.bizantum.lab (10.0.0.30)' can't be established.
ED25519 key fingerprint is SHA256:HpNlL+G8ceaugq5hFtzPJMDIu6MSSzGIwM4CxyhNDuw.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'dlp.bizantum.lab' (ED25519) to the list of known hosts.
alma@dlp.bizantum.lab's password:
[alma@dlp ~]$ # logined
Step [5]It's possbile to execute commands on remote Host with SSH like follows.
# for example, run [cat /etc/passwd]
[alma@node01 ~]$ ssh alma@dlp.bizantum.lab "cat /etc/passwd"
alma@dlp.bizantum.lab's password:
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
.....
.....
systemd-oom:x:984:984:systemd Userspace OOM Killer:/:/usr/sbin/nologin
systemd-resolve:x:983:983:systemd Resolver:/:/usr/sbin/nologin
alma:x:1000:1000::/home/alma:/bin/bash
Step [6]Configure SSH Client for Windows. Download a SSH Client software for Windows. On this example, it uses Putty. Install and start Putty, then Input your server's Hostname or IP address on [Host name] field and Click [Open] button to connect.
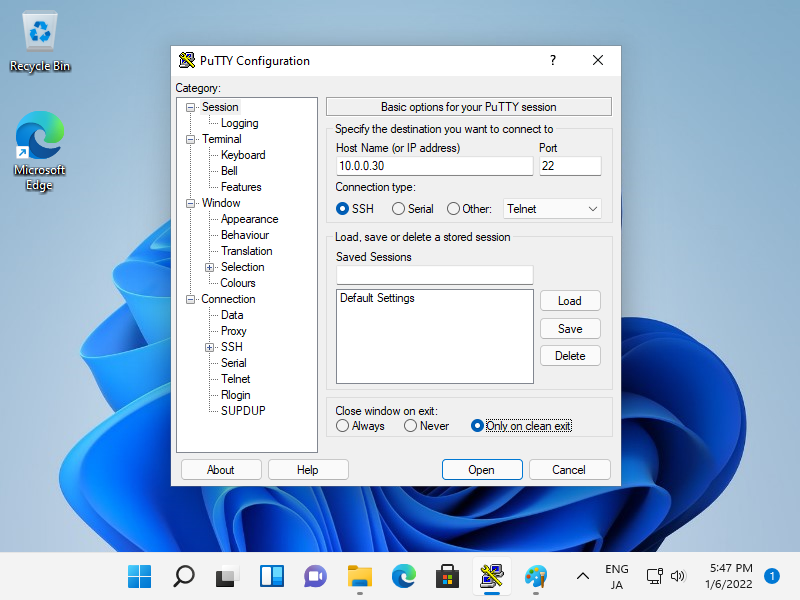
Step [7]After successing authentication, it's possible to login and operate AlmaLinux server from remote computer.
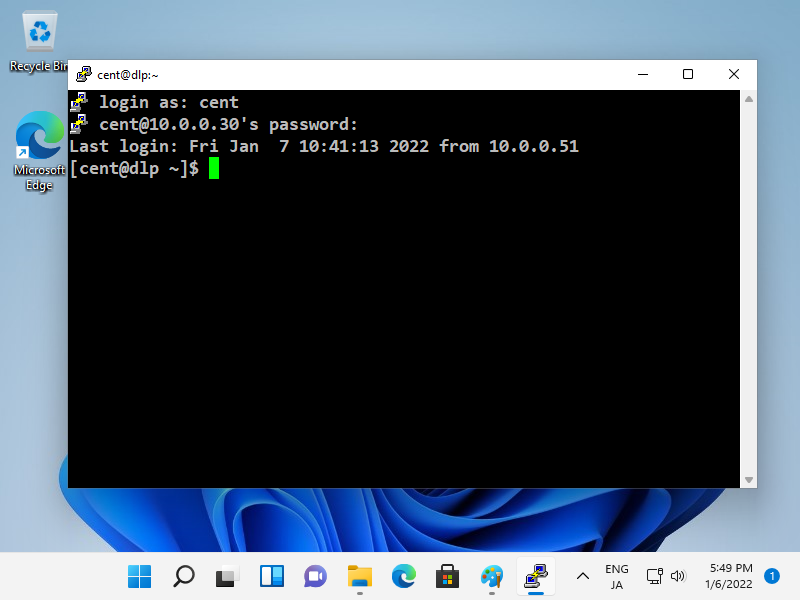
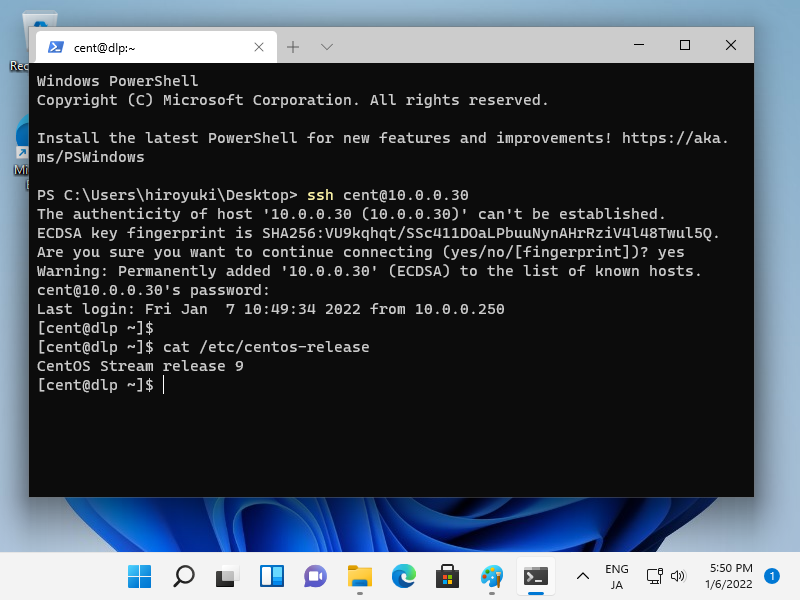
Step [8]If you are using Windows 11, OpenSSH Client has been implemented as a Windows feature, so it's possible to use [ssh] command on PowerShell or Command Prompt without Putty or other 3rd party SSH softwares.
File Transfer (Linux)
Step [1]It's the exmaple for using SCP (Secure Copy).
# command ⇒ scp [Option] Source Target
# copy the [test.txt] on localhost to remote host [node01.bizantum.lab]
[alma@dlp ~]$ scp ./test.txt alma@node01.bizantum.lab:~/
alma@node01.bizantum.lab's password: # password of the user
test.txt 100% 10 0.0KB/s 00:00
# copy the [/home/alma/test.txt] on remote host [node01.bizantum.lab] to the localhost
[alma@dlp ~]$ scp alma@node01.bizantum.lab:/home/alma/test.txt ./test.txt
alma@node01.bizantum.lab's password:
test.txt 100% 10 0.0KB/s 00:00
Step [2] It's the examples to use SFTP (SSH File Transfer Protocol). SFTP server feature is enabled by default, but if not, enable it to add the line [Subsystem sftp /usr/libexec/openssh/sftp-server] in [/etc/ssh/sshd_config].
# sftp [Option] [user@host]
[redhat@dlp ~]$ sftp alma@node01.bizantum.lab
alma@node01.bizantum.lab's password: # password of the user
Connected to node01.bizantum.lab.
sftp>
# show current directory on remote host
sftp> pwd
Remote working directory: /home/alma
# show current directory on localhost
sftp> !pwd
/home/redhat
# show files in current directory on remote host
sftp> ls -l
drwxrwxr-x 2 alma alma 7 Jan 04 21:33 public_html
-rw-rw-r-- 1 alma alma 10 Jan 04 22:53 test.txt
# show files in current directory on localhost
sftp> !ls -l
total 4
-rw-rw-r-- 1 redhat redhat 10 Jan 04 21:53 test.txt
# change directory
sftp> cd public_html
sftp> pwd
Remote working directory: /home/alma/public_html
# upload a file to remote host
sftp> put test.txt redhat.txt
Uploading test.txt to /home/alma/redhat.txt
test.txt 100% 10 0.0KB/s 00:00
sftp> ls -l
drwxrwxr-x 2 alma alma 6 Jan 04 21:33 public_html
-rw-rw-r-- 1 alma alma 10 Jan 04 21:39 redhat.txt
-rw-rw-r-- 1 alma alma 10 Jan 04 22:53 test.txt
# upload some files to remote host
sftp> put *.txt
Uploading test.txt to /home/alma/test.txt
test.txt 100% 10 0.0KB/s 00:00
Uploading test2.txt to /home/alma/test2.txt
test2.txt 100% 0 0.0KB/s 00:00
sftp> ls -l
drwxrwxr-x 2 alma alma 6 Jan 04 21:33 public_html
-rw-rw-r-- 1 alma alma 10 Jan 04 21:39 redhat.txt
-rw-rw-r-- 1 alma alma 10 Jan 04 21:45 test.txt
-rw-rw-r-- 1 alma alma 10 Jan 04 21:46 test2.txt
# download a file from remote host
sftp> get test.txt
Fetching /home/alma/test.txt to test.txt
/home/alma/test.txt 100% 10 0.0KB/s 00:00
# download some files from remote host
sftp> get *.txt
Fetching /home/alma/alma.txt to alma.txt
/home/alma/alma.txt 100% 10 0.0KB/s 00:00
Fetching /home/alma/test.txt to test.txt
/home/alma/test.txt 100% 10 0.0KB/s 00:00
Fetching /home/alma/test2.txt to test2.txt
/home/alma/test2.txt 100% 10 0.0KB/s 00:00
# create a directory on remote host
sftp> mkdir testdir
sftp> ls -l
drwxrwxr-x 2 alma alma 6 Jan 04 21:33 public_html
-rw-rw-r-- 1 alma alma 10 Jan 04 21:39 redhat.txt
-rw-rw-r-- 1 alma alma 10 Jan 04 21:45 test.txt
-rw-rw-r-- 1 alma alma 10 Jan 04 21:46 test2.txt
drwxrwxr-x 2 alma alma 6 Jan 04 21:53 testdir
# delete a directory on remote host
sftp> rmdir testdir
rmdir ok, `testdir' removed
sftp> ls -l
drwxrwxr-x 2 alma alma 6 Jan 04 21:33 public_html
-rw-rw-r-- 1 alma alma 10 Jan 04 21:39 redhat.txt
-rw-rw-r-- 1 alma alma 10 Jan 04 21:45 test.txt
-rw-rw-r-- 1 alma alma 10 Jan 04 21:46 test2.txt
# delete a file on remote host
sftp> rm test2.txt
Removing /home/alma/test2.txt
sftp> ls -l
drwxrwxr-x 2 alma alma 6 Jan 04 21:33 public_html
-rw-rw-r-- 1 alma alma 10 Jan 04 21:39 redhat.txt
-rw-rw-r-- 1 alma alma 10 Jan 04 21:45 test.txt
# execute commands with ![command]
sftp> !cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
.....
.....
redhat:x:1001:1001::/home/redhat:/bin/bash
# exit
sftp> quit
221 Goodbye.
File Transfer (Windows)
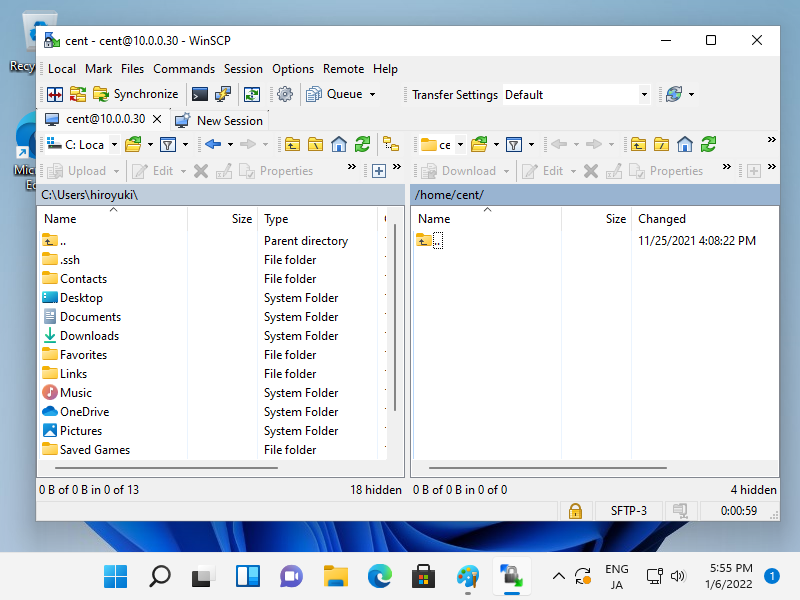
It's possible to transfer files via SSH on Windows Client. On this example, it shows WinSCP (winscp.net/eng/download.php) for it. If you are using Windows 11, OpenSSH Client has been implemented as a Windows feature, so it's possible to use [scp], [sftp] commands like the examples here.
Step [1]Install and start WinSCP, then following window is displayed. Input Hostname, Username, User's Password and then Click [Login] button.
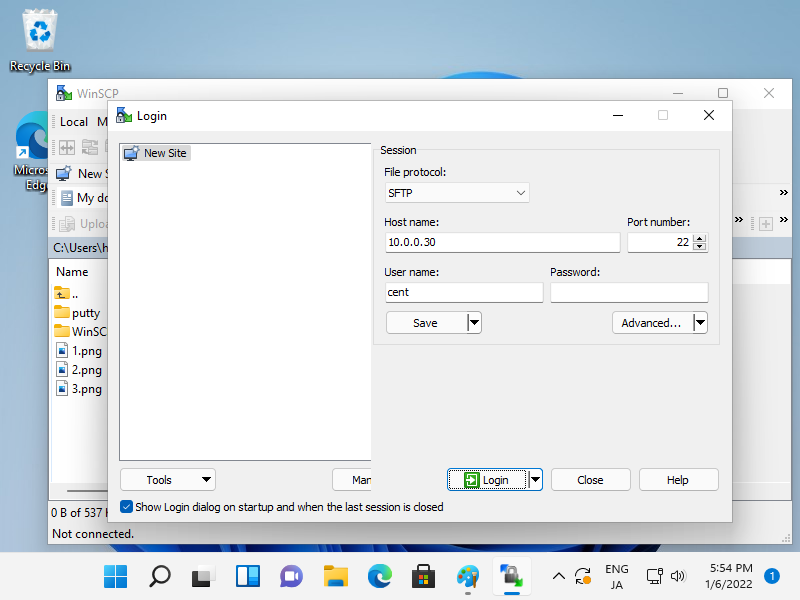
Step [2]After successing authentication, it's possible to transfer files on WinSCP via SSH.
Keys Pair Authentication
Configure SSH server to login with Key-Pair Authentication. Create a private key for client and a public key for server to do it.
Step [1]Create Key-Pair by each user, so login with a common user on SSH Server Host and work like follows.
# create key-pair
[alma@dlp ~]$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/alma/.ssh/id_rsa): # Enter or input changes if you want
Created directory '/home/alma/.ssh'.
Enter passphrase (empty for no passphrase): # set passphrase (if set no passphrase, Enter with empty)
Enter same passphrase again:
Your identification has been saved in /home/alma/.ssh/id_rsa
Your public key has been saved in /home/alma/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:yYOKaIcT25Jd0ZaOOYLa+rgrU0c/M/rVmJx4q4MVZB0 alma@node01.bizantum.lab
The key's randomart image is:
.....
.....
[alma@dlp ~]$ ll ~/.ssh
total 8
-rw-------. 1 alma alma 2655 Jan 7 19:07 id_rsa
-rw-r--r--. 1 alma alma 575 Jan 7 19:07 id_rsa.pub
[alma@dlp ~]$ mv ~/.ssh/id_rsa.pub ~/.ssh/authorized_keys
Step [2]Transfer the private key created on the Server to a Client, then it's possbile to login with Key-Pair authentication.
[alma@node01 ~]$ mkdir ~/.ssh
[alma@node01 ~]$ chmod 700 ~/.ssh
# transfer the private key to the local ssh directory
[alma@node01 ~]$ scp alma@dlp.bizantum.lab:/home/alma/.ssh/id_rsa ~/.ssh/
alma@dlp.bizantum.lab's password:
id_rsa 100% 1876 193.2KB/s 00:00
[alma@node01 ~]$ ssh alma@dlp.bizantum.lab
Enter passphrase for key '/home/alma/.ssh/id_rsa': # passphrase if you set
[alma@dlp ~]$ # logined
Step [3]If you set [PasswordAuthentication no], it's more secure.
[root@dlp ~]# vi /etc/ssh/sshd_config
# line 65 : change to [no]
PasswordAuthentication no
# line 69 : if it's enabled, change it to [no], too
# Change to no to disable s/key passwords
#KbdInteractiveAuthentication yes
KbdInteractiveAuthentication no
[root@dlp ~]# systemctl restart sshd
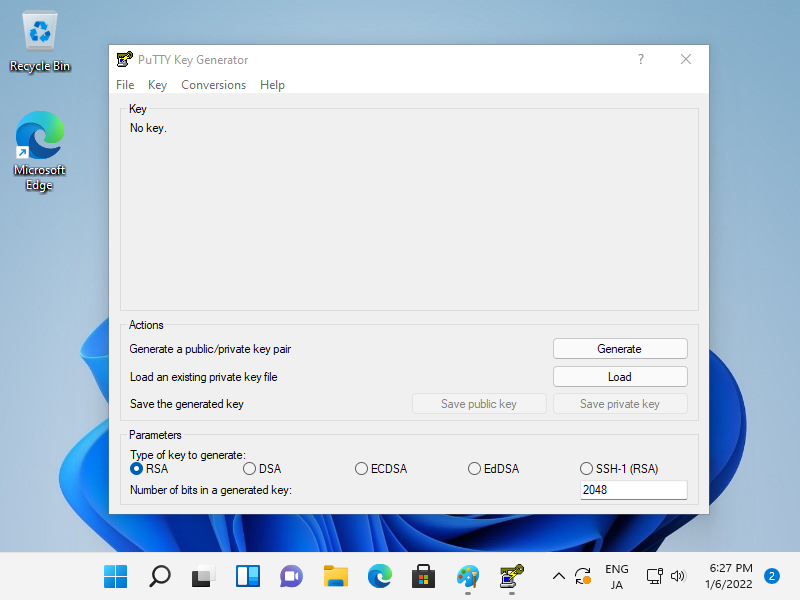
Step [4]This is the example to login to SSH server from Windows Client. On this example, it uses Putty. Before it, Transfer a private key to Windows Client. Run [Puttygen.exe] that is included in [Putty]. (placed in the same folder with [Putty.exe]) If not included, Download it from the official site www.chiark.greenend.org.uk/~sgtatham/putty/). After starting [Puttygen.exe], Click [Load] button on the following window.
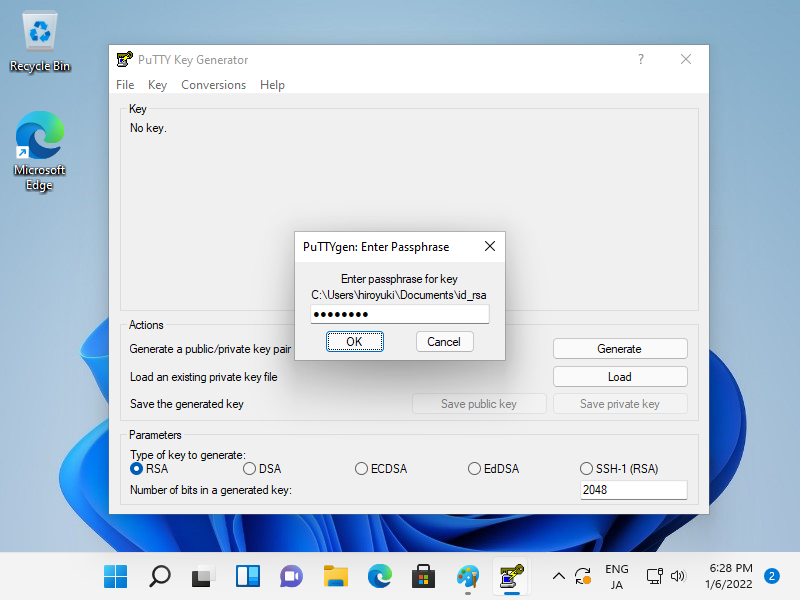
Step [5]Specify the private key that you transfered from SSH server, then passphrase is required like follows, answer it. (if not set passphrase, this step is skipped).
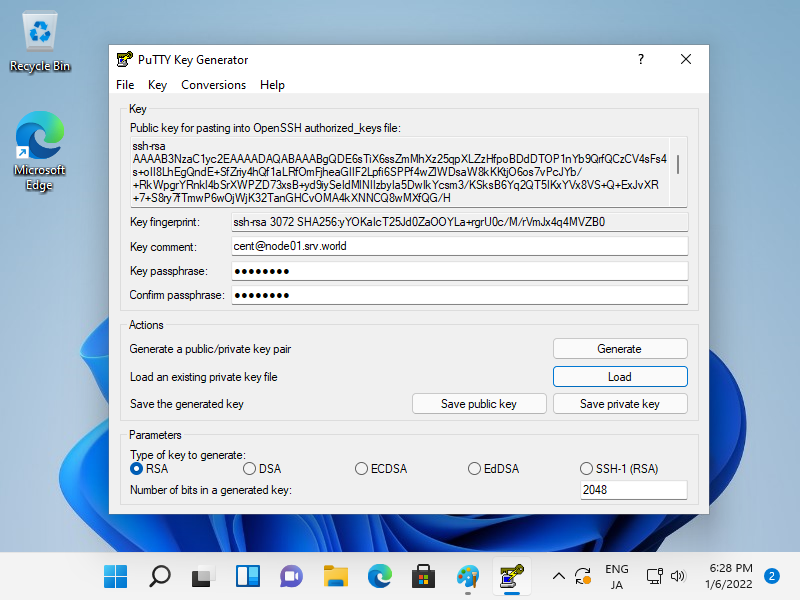
Step [6]Click the [Save private key] button to save it under a folder you like with any file name you like.
Step [7]Start Putty and Open [Connection] - [SSH] - [Auth] on the left pane, then specify your private key on the [Private key file] field.
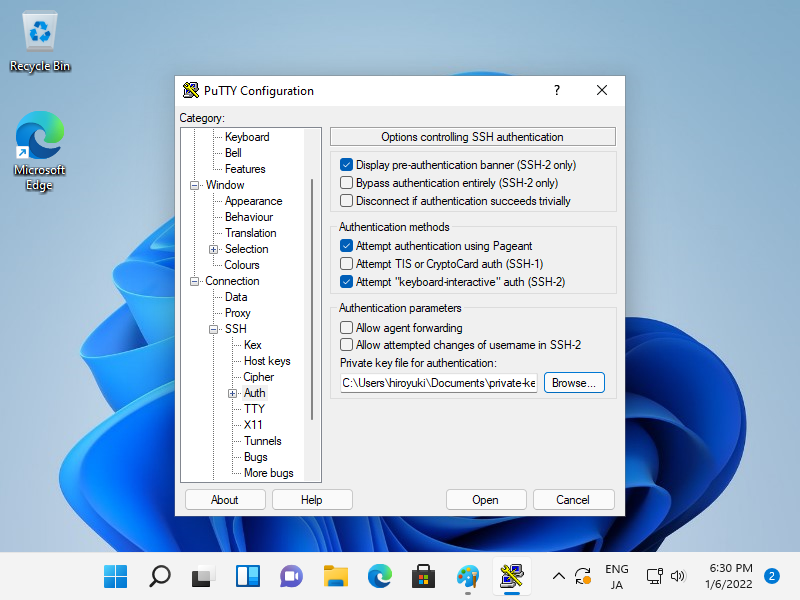
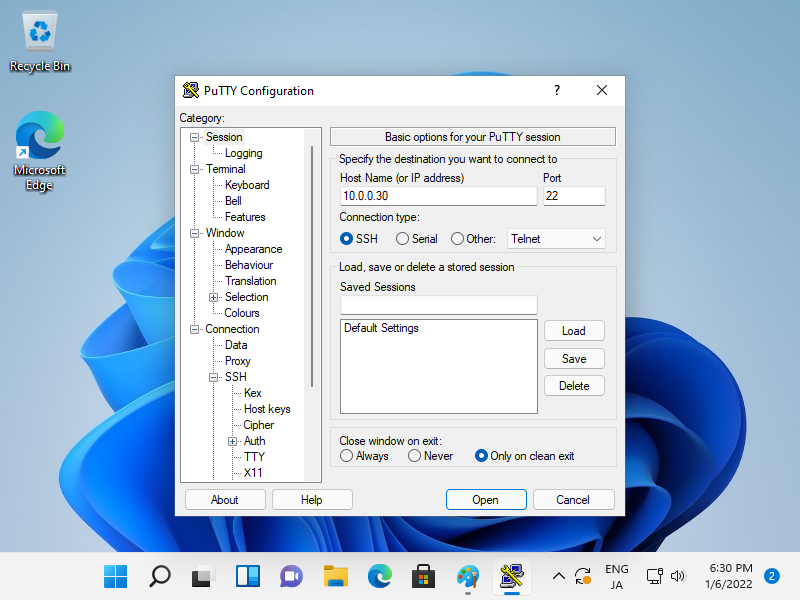
Step [8]Back to the [Session] on the left pane and specify your SSH server host to Connect.
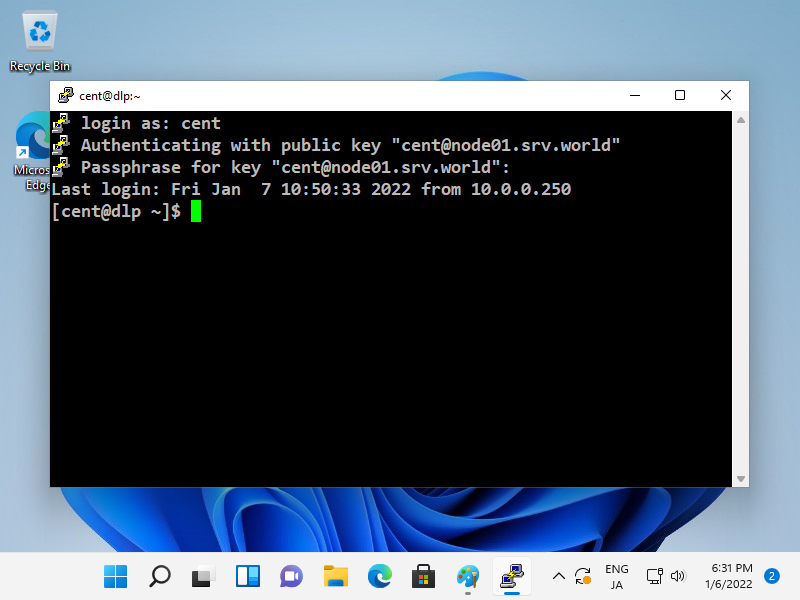
Step [9] When SSH key-pair is set, the passphrase if it is set is required to login like follows, then answer it.
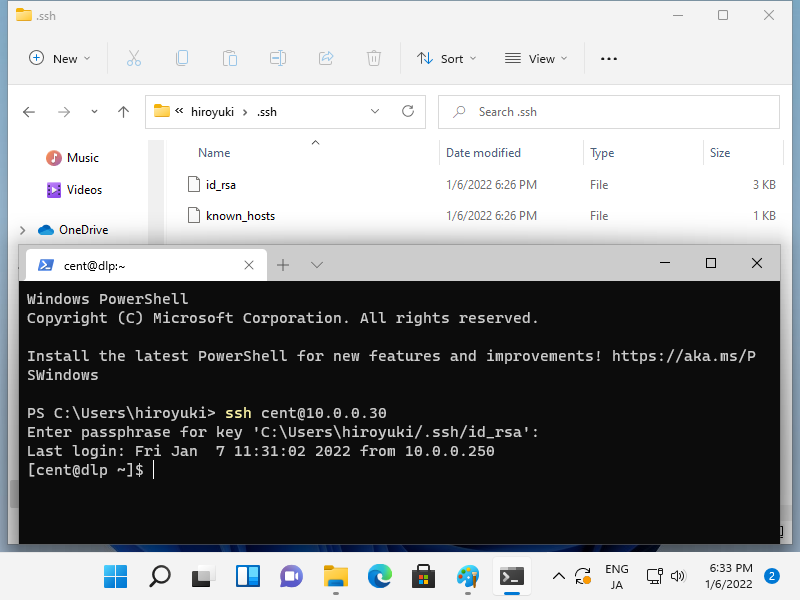
Step [10]If you are using Windows 11 like here [8], OpenSSH Client has been implemented as a Windows feature, so it's possbile to authenticate with SSH Key-Pair without Putty and other 3rd party softwares. Transfer your private key to your Windows and put it under the [(logon user home).ssh] folder like follows, then it's ready to use Key-Pair authentication.
SFTPonly + Chroot
Configure SFTP only + Chroot. Some users who are applied this setting can access only with SFTP and also applied chroot directory.
Step [1]For example, Set [/home] as the Chroot directory.
# create a group for SFTP only
[root@dlp ~]# groupadd sftp_users
[root@dlp ~]# vi /etc/ssh/sshd_config
# line 123 : comment out and add a line
#Subsystem sftp /usr/libexec/openssh/sftp-server
Subsystem sftp internal-sftp
# add to the end
Match Group sftp_users
X11Forwarding no
AllowTcpForwarding no
ChrootDirectory /home
ForceCommand internal-sftp
[root@dlp ~]# systemctl restart sshd
# for example, set [alma] user as SFTP only user
[root@dlp ~]# usermod -aG sftp_users alma
Step [2]Verify working with a user set SFTP only setting.
[alma@node01 ~]$ ssh dlp.bizantum.lab
Enter passphrase for key '/home/alma/.ssh/id_rsa':
This service allows sftp connections only.
Connection to dlp.bizantum.lab closed. # denied normally
[alma@node01 ~]$ sftp dlp.bizantum.lab
Enter passphrase for key '/home/alma/.ssh/id_rsa':
Connected to dlp.bizantum.lab.
sftp> ls -l
drwx------ 3 1000 1000 95 Jan 7 02:08 alma
sftp> pwd
Remote working directory: /
sftp> exit
SSH-Agent
Use SSH-Agent to automate inputting Passphrase on SSH Key Pair authentication. SSH-Agent is useful for users who set SSH Key Pair with Passphrase.
Step [1]This is some example to use SSH-Agent.
# run SSH-Agent
[alma@dlp ~]$ eval $(ssh-agent)
Agent pid 1826
# add passphrase
[alma@dlp ~]$ ssh-add
Enter passphrase for /home/alma/.ssh/id_rsa:
Identity added: /home/alma/.ssh/id_rsa (alma@dlp.bizantum.lab)
# verify
[alma@dlp ~]$ ssh-add -l
3072 SHA256:yYOKaIcT25Jd0ZaOOYLa+rgrU0c/M/rVmJx4q4MVZB0 alma@dlp.bizantum.lab (RSA)
# try to connect without inputting passphrase
[alma@dlp ~]$ ssh node01.bizantum.lab hostname
node01.bizantum.lab
# stop SSH-Agent
# if not execute it, SSH-Agent process remains even if you logout System, be careful
[alma@dlp ~]$ eval $(ssh-agent -k)
Agent pid 1826 killed
SSH-Pass
Use SSHPass to automate inputting password on password authentication. This is convenient but it has security risks (leak of password), take special care if you use it.
Step [1]Install SSHPass.
[root@dlp ~]# dnf -y install sshpass
Step [2]How to use SSHPass.
# [-p password] : from argument
[alma@dlp ~]$ sshpass -p password ssh node01.bizantum.lab hostname
node01.bizantum.lab
# [-f file] : from file
[alma@dlp ~]$ echo 'password' > sshpass.txt
[alma@dlp ~]$ chmod 600 sshpass.txt
[alma@dlp ~]$ sshpass -f sshpass.txt ssh node01.bizantum.lab hostname
node01.bizantum.lab
# [-e] : from environment variable
[alma@dlp ~]$ export SSHPASS=password
[alma@dlp ~]$ sshpass -e ssh node01.bizantum.lab hostname
node01.bizantum.lab
SSH-FS
It's possible to mount filesystem on another Host via SSH to use SSHFS.
Step [1]Install fuse-sshfs.
# install from EPEL
[root@dlp ~]# dnf --enablerepo=epel -y install fuse fuse-sshfs
Step [2] It's possible to use by common users. For example, [alma] user mount [/home/alma/work] on [node01.bizantum.lab] to local [~/sshmnt].
[alma@dlp ~]$ mkdir ~/sshmnt
# mount with SSHFS
[alma@dlp ~]$ sshfs node01.bizantum.lab:/home/alma/work ~/sshmnt
alma@node01.bizantum.lab's password:
[alma@dlp ~]$ df -hT
Filesystem Type Size Used Avail Use% Mounted on
devtmpfs devtmpfs 1.8G 0 1.8G 0% /dev
tmpfs tmpfs 1.9G 0 1.9G 0% /dev/shm
tmpfs tmpfs 745M 8.6M 737M 2% /run
/dev/mapper/cs-root xfs 26G 1.8G 25G 7% /
/dev/vda1 xfs 1014M 374M 641M 37% /boot
tmpfs tmpfs 373M 0 373M 0% /run/user/0
node01.bizantum.lab:/home/alma/work fuse.sshfs 26G 1.8G 25G 7% /home/alma/sshmnt
# just mounted
# for unmount, do like follows
# possible to use [umount] command, too
[alma@dlp ~]$ fusermount -u ~/sshmnt
Port Forwarding
It's possible to forward a port to another port with SSH port forwarding.
Step [1]For example, set SSH Port Forwarding that requests to port [8081] on [dlp.bizantum.lab (10.0.0.30)] are forwarded to port [80] on [node01.bizantum.lab (10.0.0.51)].
# SSH login from source host to target host
[alma@dlp ~]$ ssh -L 10.0.0.30:8081:10.0.0.51:80 alma@node01.bizantum.lab
alma@node01.bizantum.lab's password:
[alma@node01 ~]$
# confirm state
[alma@node01 ~]$ ssh dlp.bizantum.lab "ss -napt | grep 8081"
alma@dlp.bizantum.lab's password:
LISTEN 0 128 10.0.0.30:8081 0.0.0.0:* users:(("ssh",pid=3311,fd=4))
# listen on 8081
# keep this login session
Step [2]Verify to access to a port on source Host you set from any client Host, then target port on target Host replies.
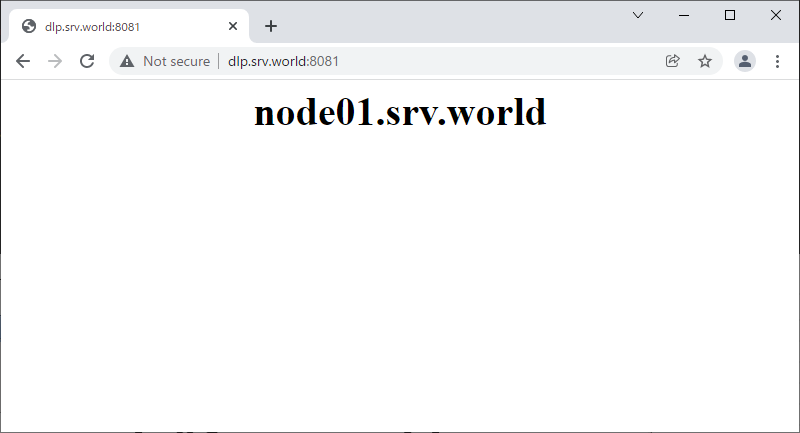
Paralel SSH
Use PSSH (Parallel Secure Shell) to connect to multiple hosts via SSH.
Step [1]Install PSSH.
# install from EPEL
[root@dlp ~]# dnf --enablerepo=epel -y install pssh
Step [2]Basic usage for PSSH. This is based on the environment you set SSH key-pair to target Hosts without passphrase. If set passphrase, run SSH-Agent and set passphrase on it first.
# specify target hosts and access via SSH
[alma@dlp ~]$ pssh -H "10.0.0.51 10.0.0.52" -i "hostname"
[1] 17:28:02 [SUCCESS] 10.0.0.51
node01.bizantum.lab
[2] 17:28:02 [SUCCESS] 10.0.0.52
node02.bizantum.lab
# possible to read hosts-list from a file
[alma@dlp ~]$ vi pssh_hosts.txt
# write a host per line like follows
alma@10.0.0.51
alma@10.0.0.52
[alma@dlp ~]$ pssh -h pssh_hosts.txt -i "uptime"
[1] 19:37:59 [SUCCESS] alma@10.0.0.52
19:37:59 up 1:35, 0 users, load average: 0.00, 0.00, 0.00
[2] 19:37:59 [SUCCESS] alma@10.0.0.51
19:37:59 up 1:35, 0 users, load average: 0.00, 0.00, 0.00
Step [3] It's possible to connect with password authentication too, but it needs passwords on all hosts are the same one.
[alma@dlp ~]$ pssh -h pssh_hosts.txt -A -O PreferredAuthentications=password -i "uname -r"
Warning: do not enter your password if anyone else has superuser
privileges or access to your account.
Password: # input password
[1] 13:34:44 [SUCCESS] alma@10.0.0.51
5.14.0-34.el9.x86_64
[2] 13:34:44 [SUCCESS] alma@10.0.0.52
5.14.0-34.el9.x86_64
Step [4]PSSH package includes pscp.pssh, prsync, pslurp, pnuke commands and you can use them with the same usage of pssh.
- Get link
- X
- Other Apps








Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.