
Manage Accounts
To add user accounts on AlmaLinux Server, Configure like follows.
Step [1]For example, Add [alma] user.
[root@localhost ~]# useradd alma
[root@localhost ~]# passwd alma
Changing password for user alma.
New UNIX password: # input any password you'd like to set
Retype new UNIX password: # confirm
passwd: all authentication tokens updated successfully.
Step [2]If you'd like to switch to root account from a user added above, use [su] command to do so.
localhost login: alma # login username
password: # input user password
[alma@localhost ~]$ su - # switch to root
Password: # input root password
[root@localhost ~]# # just switched to root
Step [3]If you'd like to limit users to run [su] command, configure like follows. On the example below, only users in [wheel] group can run [su] command.
[root@localhost ~]# usermod -aG wheel alma
[root@localhost ~]# vi /etc/pam.d/su
#%PAM-1.0
auth sufficient pam_rootok.so
# Uncomment the following line to implicitly trust users in the "wheel" group.
#auth sufficient pam_wheel.so trust use_uid
# Uncomment the following line to require a user to be in the "wheel" group.
# uncomment the following line
auth required pam_wheel.so use_uid
auth substack system-auth
auth include postlogin
account sufficient pam_succeed_if.so uid = 0 use_uid quiet
account include system-auth
password include system-auth
session include system-auth
session include postlogin
session optional pam_xauth.so
# verify settings with a user who is not in allowed group
[redhat@localhost ~]$ su -
Password:
su: Permission denied # denied normally
Step [4]If you'd like to remove a user accounts, Set like follows.
# remove a user [alma] (only removed user account)
[root@localhost ~]# userdel alma
# remove a user [alma] (removed user account and his home directory both)
[root@localhost ~]# userdel -r alma
Manage Firewall
Below are simple configuration to Configure Firewall and SELinux.
Firewall
Step [1]It's possible to display FireWall Service Status like follows. (enabled by default).
[root@localhost ~]# systemctl status firewalld
* firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor>
Active: active (running) since Mon 2023-02-20 09:41:13 JST; 3min 57s ago
Docs: man:firewalld(1)
Main PID: 772 (firewalld)
Tasks: 2 (limit: 24744)
Memory: 41.0M
CPU: 259ms
CGroup: /system.slice/firewalld.service
+- 772 /usr/bin/python3 -s /usr/sbin/firewalld --nofork --nopid
# [Active: active (running) ***] means firewalld is running now
Step [2]If you use FireWall service, it needs to modify FireWall settings manually because incoming requests for services are mostly not allowed by default. Refer to here for basic Firewall operation and settings. Configuration examples of AlmaLinux 9 on this site are based on the environment Firewalld service is always enabled.
Step [3]If you don't need FireWall service because of some reasons like that some FireWall Machines are running in your Local Netowrk or others, it's possbile to stop and disable FireWall service on AlmaLinux server like follows.
# stop service
[root@localhost ~]# systemctl stop firewalld
# disable service
[root@localhost ~]# systemctl disable firewalld
Removed /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
SELinux
Step [4]It's possible to display current SELinux (Security-Enhanced Linux) Status like follows. (enabled by default).
[root@localhost ~]# getenforce
Enforcing # SELinux is enabled
Step [5]If you enable SELinux, there are cases to modify SELinux policies manually because sometimes SELinux stops applications. Refer to here for basic SELinux operation and settings. Configuration examples of AlmaLinux 9 on this site are based on the environment SELinux is always Enforcing.
Step [6]If you don't need SELinux feature because of some reasons like that your server is running only in Local safety Network or others, it's possbile to disable SELinux like follows.
# disable SELinux
[root@localhost ~]# grubby --update-kernel ALL --args selinux=0
# apply changes to restart computer
[root@localhost ~]# reboot
# if falling back to enable, run like follows
[root@localhost ~]# grubby --update-kernel ALL --remove-args selinux
Manage Network
If you did not configure networking during the AlmaLinux 9 installation, Configure it like follows.
Step [1]To set static IP address to the server, Modify settings like follows. ( Replace the interface name [enp1s0] to your own one because it's not the same on any System ).
# if you did not set HostName, set it like follows
[root@localhost ~]# hostnamectl set-hostname vms.bizantum.lab
# display devices
[root@localhost ~]# nmcli device
DEVICE TYPE STATE CONNECTION
enp1s0 ethernet connected enp1s0
lo loopback unmanaged --
# set IPv4 address
[root@localhost ~]# nmcli connection modify enp1s0 ipv4.addresses 10.0.0.30/24
# set gateway
[root@localhost ~]# nmcli connection modify enp1s0 ipv4.gateway 10.0.0.1
# set DNS
# for multiple DNS, specify with space separated ⇒ ipv4.dns "10.0.0.10 10.0.0.11 10.0.0.12"
[root@localhost ~]# nmcli connection modify enp1s0 ipv4.dns 10.0.0.10
# set DNS search base (your domain name -for multiple one, specify with space separated)
[root@localhost ~]# nmcli connection modify enp1s0 ipv4.dns-search bizantum.lab
# set [manual] for static setting (it's [auto] for DHCP)
[root@localhost ~]# nmcli connection modify enp1s0 ipv4.method manual
# restart the interface to reload settings
[root@localhost ~]# nmcli connection down enp1s0; nmcli connection up enp1s0
Connection 'enp1s0' successfully deactivated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/1)
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2)
# confirm settings
[root@localhost ~]# nmcli device show enp1s0
GENERAL.DEVICE: enp1s0
GENERAL.TYPE: ethernet
GENERAL.HWADDR: 52:54:00:DF:87:AD
GENERAL.MTU: 1500
GENERAL.STATE: 100 (connected)
GENERAL.CONNECTION: enp1s0
GENERAL.CON-PATH: /org/freedesktop/NetworkManager/ActiveC>
WIRED-PROPERTIES.CARRIER: on
IP4.ADDRESS[1]: 10.0.0.30/24
IP4.GATEWAY: 10.0.0.1
IP4.ROUTE[1]: dst = 10.0.0.0/24, nh = 0.0.0.0, mt = 1>
IP4.ROUTE[2]: dst = 0.0.0.0/0, nh = 10.0.0.1, mt = 100
IP4.DNS[1]: 10.0.0.10
IP4.SEARCHES[1]: bizantum.lab
IP6.ADDRESS[1]: fe80::5054:ff:fedf:87ad/64
IP6.GATEWAY: --
IP6.ROUTE[1]: dst = fe80::/64, nh = ::, mt = 100
# confirm state
[root@localhost ~]# ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:df:87:ad brd ff:ff:ff:ff:ff:ff
inet 10.0.0.30/24 brd 10.0.0.255 scope global noprefixroute enp1s0
valid_lft forever preferred_lft forever
inet6 fe80::5054:ff:fedf:87ad/64 scope link noprefixroute
valid_lft forever preferred_lft forever
Step [2]If you don't need IPv6, it's possible to disable it like follows.
# disable IPv6
[root@localhost ~]# grubby --update-kernel ALL --args ipv6.disable=1
# verify kernel parameters
[root@localhost ~]# grubby --info DEFAULT
index=0 kernel="/boot/vmlinuz-5.14.0-17.el9.x86_64" args="ro crashkernel=1G-4G:192M,4G-64G:256M,64G-:512M resume=/dev/mapper/cs-swap rd.lvm.lv=cs/root rd.lvm.lv=cs/swap console=ttyS0,115200n8 selinux=0 ipv6.disable=1" root="/dev/mapper/cs-root" initrd="/boot/initramfs-5.14.0-17.el9.x86_64.img" title="CentOS Stream (5.14.0-17.el9.x86_64) 9" id="ab414d4792d04b9dbc1e2361f936e849-5.14.0-17.el9.x86_64"
[root@localhost ~]# reboot
[root@localhost ~]# ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:df:87:ad brd ff:ff:ff:ff:ff:ff
inet 10.0.0.30/24 brd 10.0.0.255 scope global noprefixroute enp1s0
valid_lft forever preferred_lft forever
# if falling back to enable, run like follows
[root@localhost ~]# grubby --update-kernel ALL --remove-args ipv6.disable
Manage Services
To manage services like enable or disable services, Configure like follows.
Step [1]Display services list.
# the list of services that are active now
[root@vms ~]# systemctl -t service
UNIT LOAD ACTIVE SUB DESCRIPTION >
atd.service loaded active running Deferred execution s>
auditd.service loaded active running Security Auditing Se>
chronyd.service loaded active running NTP client/server
crond.service loaded active running Command Scheduler
dbus-broker.service loaded active running D-Bus System Message>
dracut-shutdown.service loaded active exited Restore /run/initram>
fprintd.service loaded active running Fingerprint Authenti>
.....
.....
systemd-vconsole-setup.service loaded active exited Setup Virtual Console
user-runtime-dir@0.service loaded active exited User Runtime Directo>
user@0.service loaded active running User Manager for UID>
LOAD = Reflects whether the unit definition was properly loaded.
ACTIVE = The high-level unit activation state, i.e. generalization of SUB.
SUB = The low-level unit activation state, values depend on unit type.
45 loaded units listed. Pass --all to see loaded but inactive units, too.
To show all installed unit files use 'systemctl list-unit-files'.
# list of all services
[root@vms ~]# systemctl list-unit-files -t service
UNIT FILE STATE VENDOR PRESET
arp-ethers.service disabled disabled
atd.service enabled enabled
auditd.service enabled enabled
autovt@.service alias -
blk-availability.service disabled disabled
bolt.service static -
chrony-wait.service disabled disabled
chronyd.service enabled enabled
.....
.....
usb_modeswitch@.service static -
user-runtime-dir@.service static -
user@.service static -
194 unit files listed.
Step [2]Stop and turn OFF auto-start setting for a service if you don'd need it. For example, disable [nis-domainname] as an example below.
[root@vms ~]# systemctl stop nis-domainname
[root@vms ~]# systemctl disable nis-domainname
# to disable and stop with a command, run like follows
[root@vms ~]# systemctl disable --now nis-domainname
Update System
After AlmaLinux Server has been a production System, maybe it's difficult to update System, however, at least after Installing, Update AlmaLinux Server to the latest.
Step [1]For commands to updating System, it's possible to use [yum] or [dnf], but both are the link to [dnf-3], so you may use [yum] or [dnf] as you like.
[root@vms ~]# which yum
/usr/bin/yum
[root@vms ~]# ll /usr/bin/yum
lrwxrwxrwx. 1 root root 5 Aug 5 2020 /usr/bin/yum -> dnf-3
[root@vms ~]# which dnf
/usr/bin/dnf
[root@vms ~]# ll /usr/bin/dnf
lrwxrwxrwx. 1 root root 5 Oct 25 23:06 /usr/bin/dnf -> dnf-3
[root@vms ~]# ll /usr/bin/dnf-3
-rwxr-xr-x. 1 root root 1942 Oct 25 23:06 /usr/bin/dnf-3
# installed [yum] package
[root@vms ~]# rpm -q yum
yum-4.10.0-1.el9.noarch
[root@vms ~]# rpm -ql yum
/etc/dnf/protected.d/yum.conf
/etc/yum.conf
/etc/yum/pluginconf.d
/etc/yum/protected.d
/etc/yum/vars
/usr/bin/yum
/usr/share/man/man1/yum-aliases.1.gz
/usr/share/man/man5/yum.conf.5.gz
/usr/share/man/man8/yum-shell.8.gz
/usr/share/man/man8/yum.8.gz
# included files are all links to [dnf]
[root@vms ~]# ll /etc/yum.conf /etc/yum/vars /etc/yum/pluginconf.d
lrwxrwxrwx. 1 root root 12 Oct 25 23:06 /etc/yum.conf -> dnf/dnf.conf
lrwxrwxrwx. 1 root root 14 Oct 25 23:06 /etc/yum/pluginconf.d -> ../dnf/plugins
lrwxrwxrwx. 1 root root 11 Oct 25 23:06 /etc/yum/vars -> ../dnf/vars
Step [2]Update AlmaLinux Server like follows.
[root@vms ~]# dnf -y upgrade
AlmaLinux 9 - AppStream 4.3 MB/s | 8.0 MB 00:01
AlmaLinux 9 - BaseOS 1.5 MB/s | 2.9 MB 00:01
AlmaLinux 9 - Extras 18 kB/s | 17 kB 00:00
Dependencies resolved.
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
kernel x86_64 5.14.0-162.12.1.el9_1 baseos 1.9 M
Upgrading:
aardvark-dns x86_64 2:1.1.0-5.el9_1 appstream 996 k
authselect x86_64 1.2.5-2.el9_1 baseos 140 k
authselect-libs x86_64 1.2.5-2.el9_1 baseos 223 k
bash x86_64 5.1.8-6.el9_1 baseos 1.7 M
bpftool x86_64 5.14.0-162.12.1.el9_1 baseos 2.6 M
buildah x86_64 1:1.27.3-1.el9_1 appstream 7.9 M
containers-common x86_64 2:1-45.el9_1 appstream 112 k
cryptsetup x86_64 2.4.3-5.el9_1.1 baseos 199 k
cryptsetup-libs x86_64 2.4.3-5.el9_1.1 baseos 434 k
curl x86_64 7.76.1-19.el9_1.1 baseos 295 k
dbus x86_64 1:1.12.20-7.el9_1 baseos 7.0 k
dbus-common noarch 1:1.12.20-7.el9_1 baseos 14 k
dbus-libs x86_64 1:1.12.20-7.el9_1 baseos 152 k
device-mapper-multipath x86_64 0.8.7-12.el9_1.1 baseos 141 k
device-mapper-multipath-libs x86_64 0.8.7-12.el9_1.1 baseos 266 k
expat x86_64 2.4.9-1.el9_1.1 baseos 116 k
.....
.....
Manage Repositories
Add some useful external repositories to install useful softwares.
Step [1]Add EPEL that Fedora project provides packages which are specially built for RHEL. ⇒ https://fedoraproject.org/wiki/EPEL
[root@vms ~]# dnf -y install epel-release
[root@vms ~]# dnf -y install epel-next-release
[root@vms ~]# vi /etc/yum.repos.d/epel.repo
[epel]
name=Extra Packages for Enterprise Linux $releasever - $basearch
# It is much more secure to use the metalink, but if you wish to use a local mirr
ror
# place its address here.
#baseurl=https://download.example/pub/epel/$releasever/Everything/$basearch/
metalink=https://mirrors.fedoraproject.org/metalink?repo=epel-$releasever&arch=$$
basearch&infra=$infra&content=$contentdir
# [enabled=1] = repository enabled, [enabled=0] = repository disabled
enabled=1
# to add [priority=*], it can set priority to repository
# it can specify [1-99], [1] is highest, default without the line is [99]
priority=10
gpgcheck=1
countme=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-EPEL-$releasever
.....
.....
# set EPEL Next, too, for your needs
[root@vms ~]# vi /etc/yum.repos.d/epel-next.repo
[epel-next]
name=Extra Packages for Enterprise Linux $releasever - Next - $basearch
# It is much more secure to use the metalink, but if you wish to use a local mirror
# place its address here.
#baseurl=https://download.example/pub/epel/next/$releasever/Everything/$basearch/
metalink=https://mirrors.fedoraproject.org/metalink?repo=epel-next-$releasever&arch=$basearch&infra=$infra&content=$contentdir
.....
.....
# if disabling with [enabled=0] regulary but want to enable it temporary, run like follows
[root@vms ~]# dnf --enablerepo=epel,epel-next install [Package]
Step [2]Add Remi's RPM repository that provides useful packages like latest PHP and so on. ⇒ https://rpms.remirepo.net/
[root@vms ~]# dnf -y install https://rpms.remirepo.net/enterprise/remi-release-9.rpm
# included repository files
[root@vms ~]# rpm -ql remi-release
/etc/pki/rpm-gpg/RPM-GPG-KEY-remi
/etc/pki/rpm-gpg/RPM-GPG-KEY-remi.el9
/etc/pki/rpm-gpg/RPM-GPG-KEY-remi2017
/etc/pki/rpm-gpg/RPM-GPG-KEY-remi2018
/etc/pki/rpm-gpg/RPM-GPG-KEY-remi2019
/etc/pki/rpm-gpg/RPM-GPG-KEY-remi2020
/etc/pki/rpm-gpg/RPM-GPG-KEY-remi2021
/etc/yum.repos.d/remi-modular.repo
/etc/yum.repos.d/remi-safe.repo
/etc/yum.repos.d/remi.repo
/opt/remi
# only [remi-safe] and [remi-modular] are enabled by default
[root@vms ~]# grep 'enabled=1' /etc/yum.repos.d/remi-*
/etc/yum.repos.d/remi-modular.repo:enabled=1
/etc/yum.repos.d/remi-safe.repo:enabled=1
[root@vms ~]# vi /etc/yum.repos.d/remi-safe.repo
[remi-safe]
name=Safe Remi's RPM repository for Enterprise Linux 9 - $basearch
#baseurl=http://rpms.remirepo.net/enterprise/9/safe/$basearch/
#mirrorlist=https://rpms.remirepo.net/enterprise/9/safe/$basearch/httpsmirror
mirrorlist=http://cdn.remirepo.net/enterprise/9/safe/$basearch/mirror
# [enabled=1] = repository enabled, [enabled=0] = repository disabled
enabled=1
# to add [priority=*], it can set priority to repository
# it can specify [1-99], [1] is highest, default without the line is [99]
priority=10
gpgcheck=1
repo_gpgcheck=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-remi.el9
.....
.....
# if disabling with [enabled=0] regulary but want to enable it temporary, run like follows
[root@vms ~]# dnf --enablerepo=remi-safe install [Package]
# also possible to use Moduler Repository
[root@vms ~]# dnf --enablerepo=remi-modular --disablerepo=appstream module list
Remi's Modular repository for Enterprise Linux 9 - x86_64
Name Stream Profiles Summary
composer 2 [d] common [d] Dependency Manager for PHP
memcached remi common [d] High Performance, Distributed Memory Object Cache
php remi-7.4 common [d], devel, minimal PHP scripting language
php remi-8.0 common [d], devel, minimal PHP scripting language
php remi-8.1 common [d], devel, minimal PHP scripting language
redis remi-5.0 common [d] Redis persistent key-value database
redis remi-6.0 common [d] Redis persistent key-value database
redis remi-6.2 common [d] Redis persistent key-value database
Hint: [d]efault, [e]nabled, [x]disabled, [i]nstalled
Configure Web Admin Console
Cockpit Admin Console is installed with AlmaLinux 9 Base Environment [Server] or others. It's possbile to manage your AlmaLinux server on a Web browser to enable it.
Step [1]On console login prompt, as message is shown like [Activate the web console ***], it's possible to use Admin Console to enable it.
[root@vms ~]# systemctl enable --now cockpit.socket
[root@vms ~]# ss -napt
State Recv-Q Send-Q Local Address:Port Peer Address:PortProcess
LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=733,fd=3))
LISTEN 0 4096 *:9090 *:* users:(("systemd",pid=1,fd=46))
LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=733,fd=4))
# Cockpit listens 9090 port
# if Firewalld is running, confirm inbound settings (generally cockpit is allowed by default)
[root@vms ~]# firewall-cmd --list-service
cockpit dhcpv6-client ssh
# if [cockpit] is not allowed, set it to allow
[root@vms ~]# firewall-cmd --add-service=cockpit
success
[root@vms ~]# firewall-cmd --runtime-to-permanent
success
Step [2]Access to [https://(server's hostname or IP address):9090/] with Web browser from localhost or other Client compuers, then Cockpit login form is displayed like follows. Login with a local user on your Server. (It uses root user on this example)
Step [3]This is the Cockpit index page. It's possible to manage various system settings on here.
Step [4]For [Logs] on the left pane, it's possible to manage or opereate [Journal] service that is the log management tool.
Step [5]For [Storage] on the left pane, it's possible to manage or opereate Storages.
Step [6]For [Networking] on the left pane, it's possible to manage or opereate Network settings.
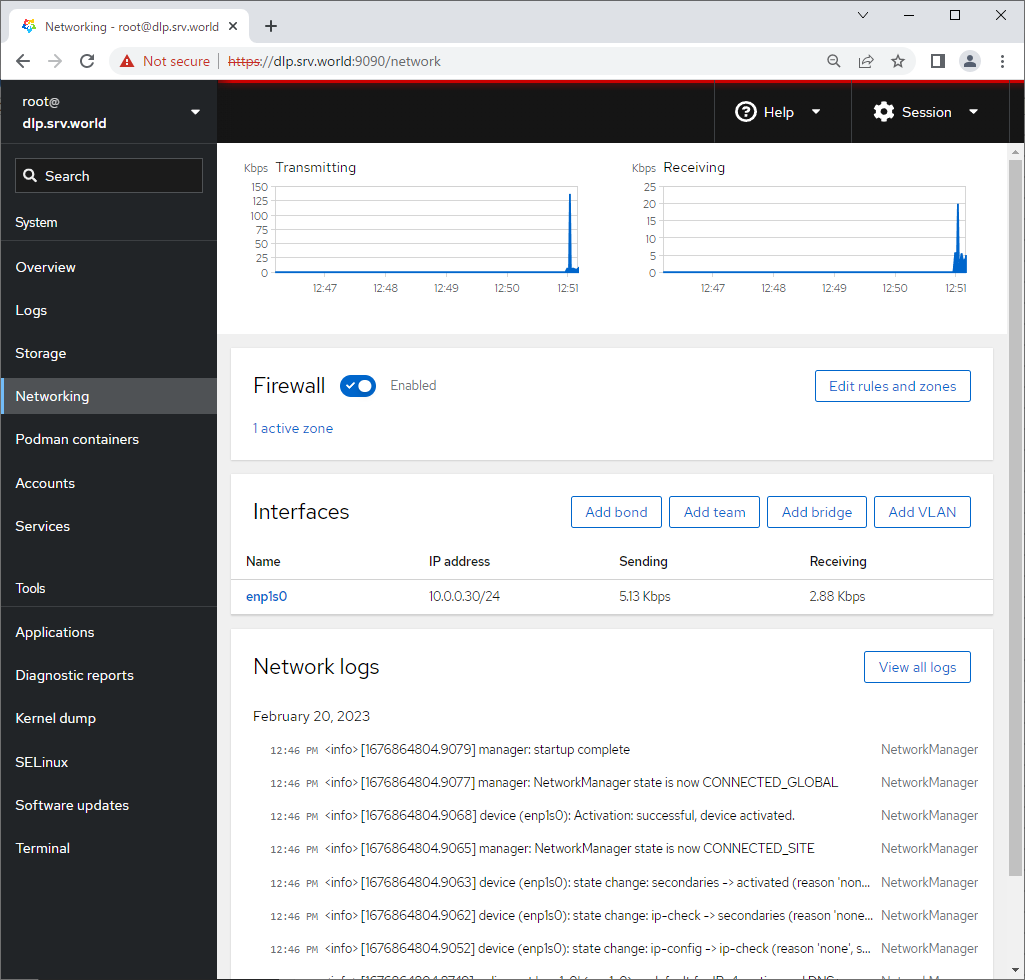
Step [7]For [Accounts] on the left pane, it's possible to manage or opereate system accounts.
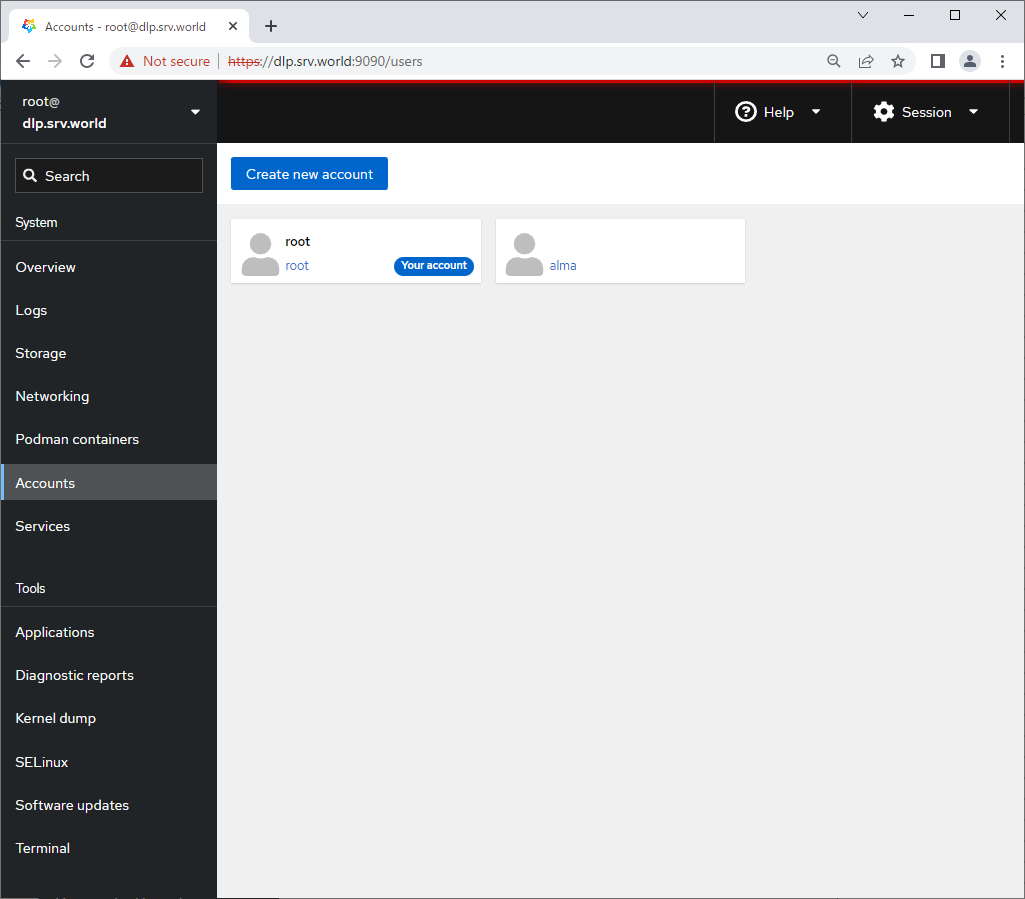
Step [8]For [Services] on the left pane, it's possible to manage or opereate system services.
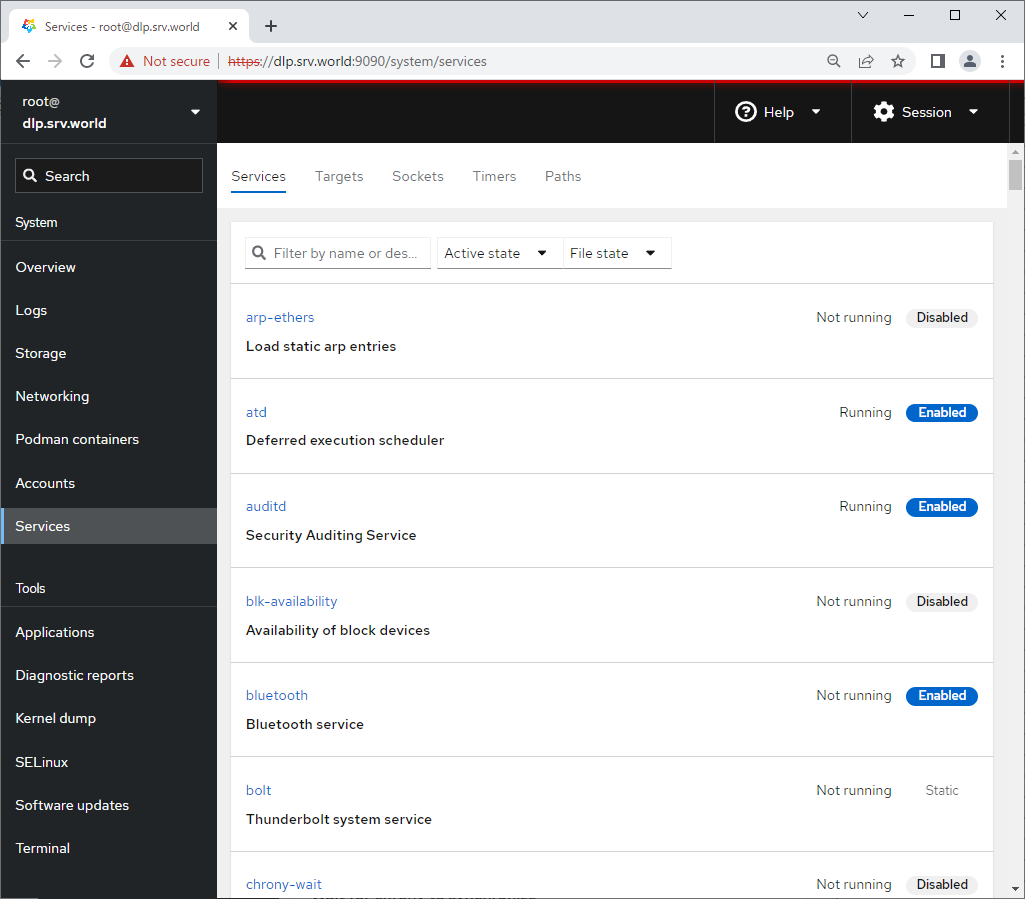
Step [9]For [Applications] on the left pane, it's possible to install or remove applications.
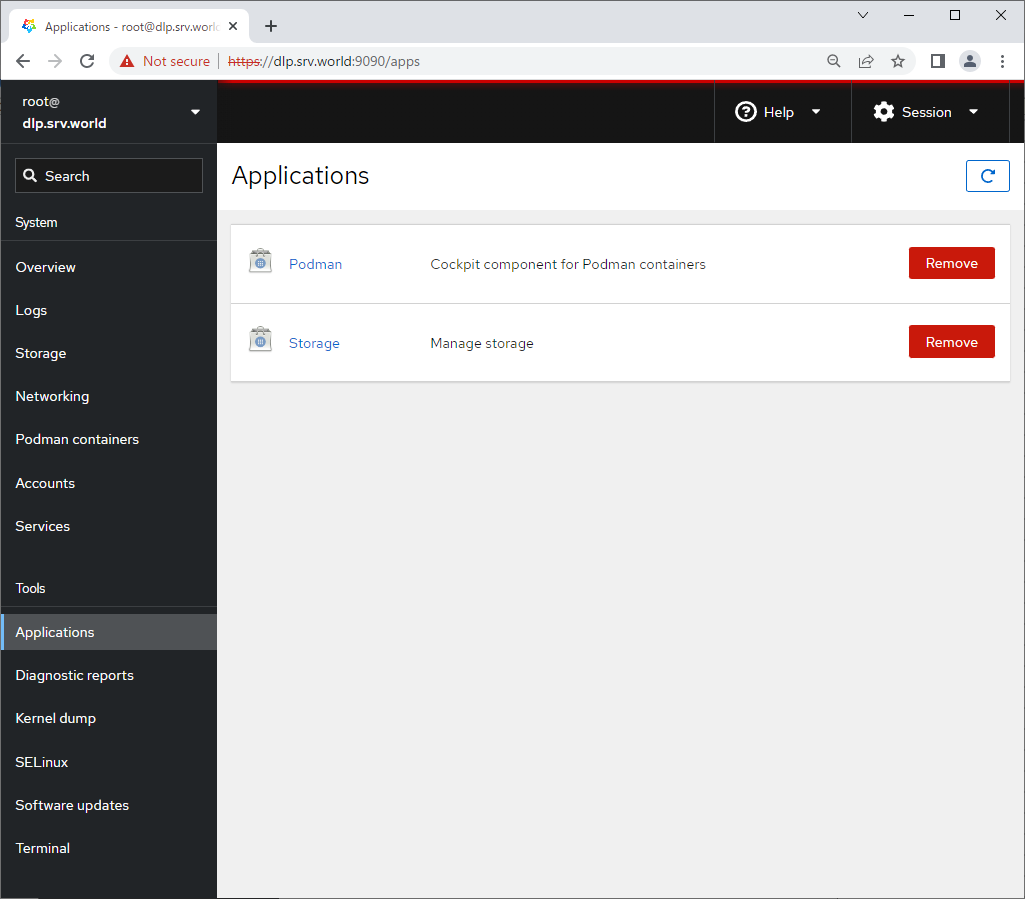
Step [10]For [Diagnostic Reports] on the left pane, it's possible to create or display System Diagnostic Reports.
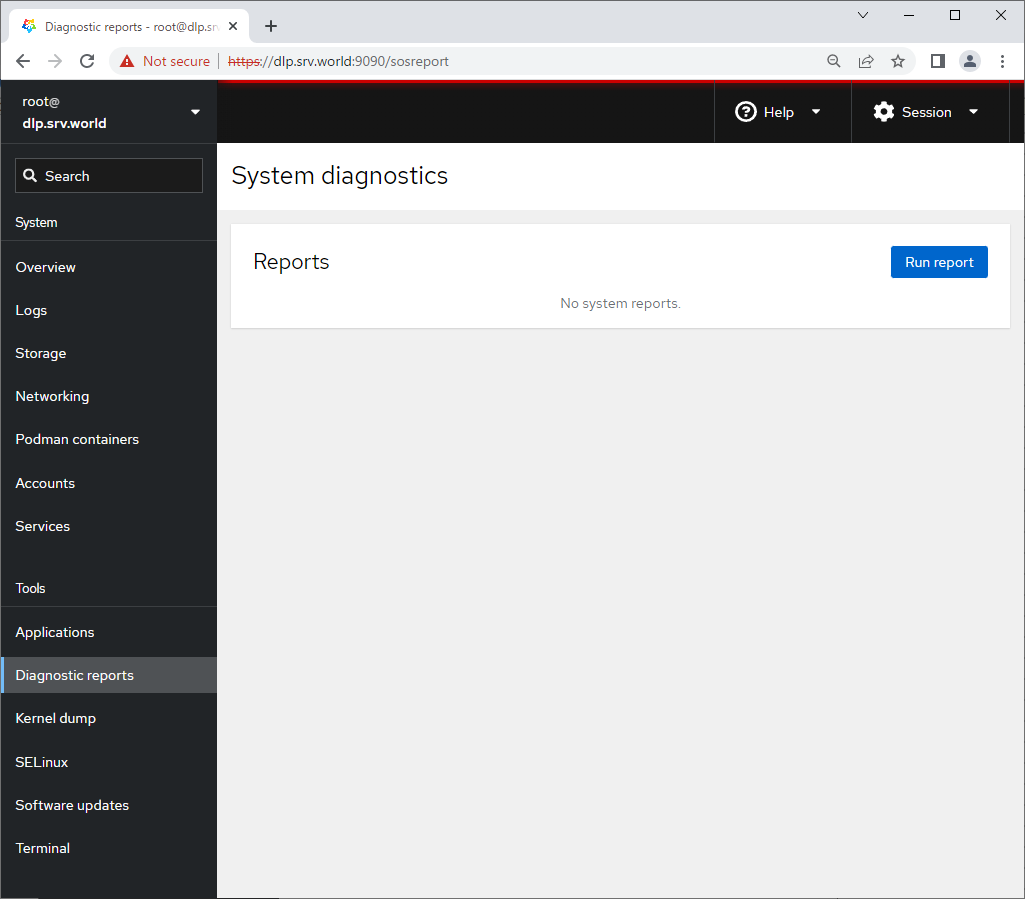
Step [11]For [Kernel Dump] on the left pane, it's possible to display Kernel Dump status. (based on [kdump] service is running state)
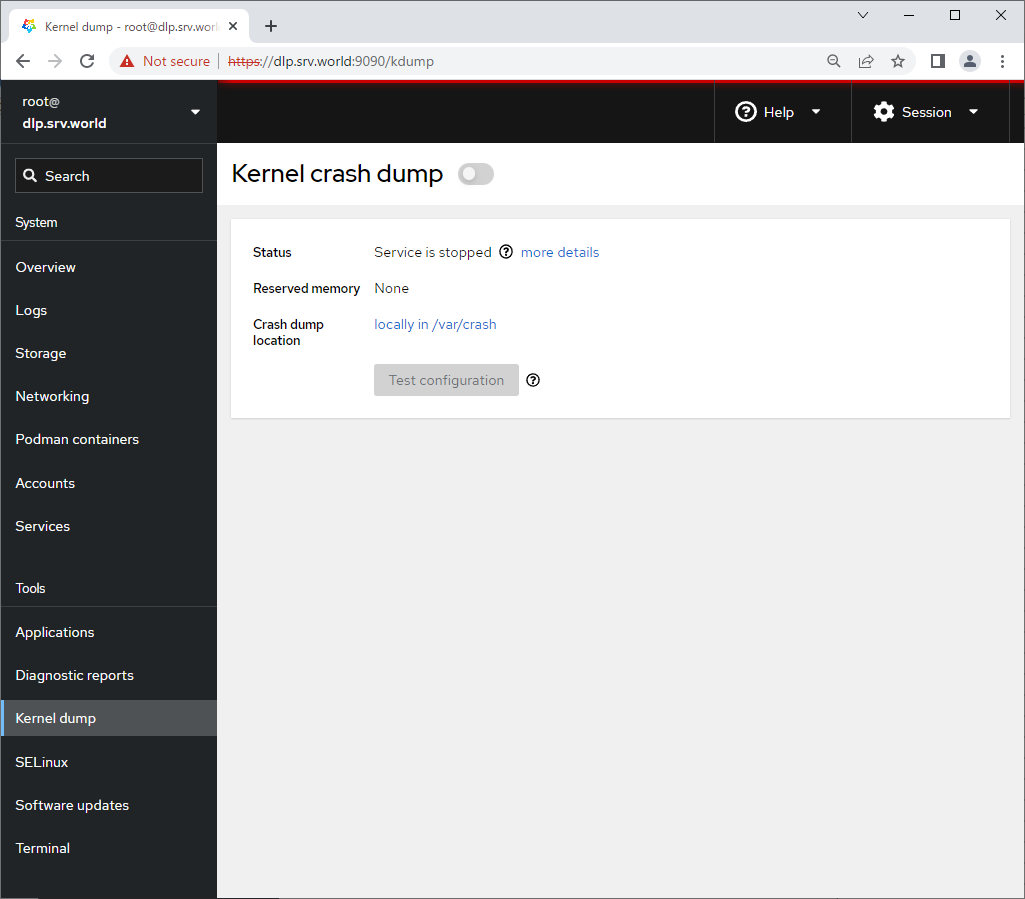
Step [12]For [SELinux] on the left pane, it's possible to display SELinux alert logs. (based on SELinux enabled state)
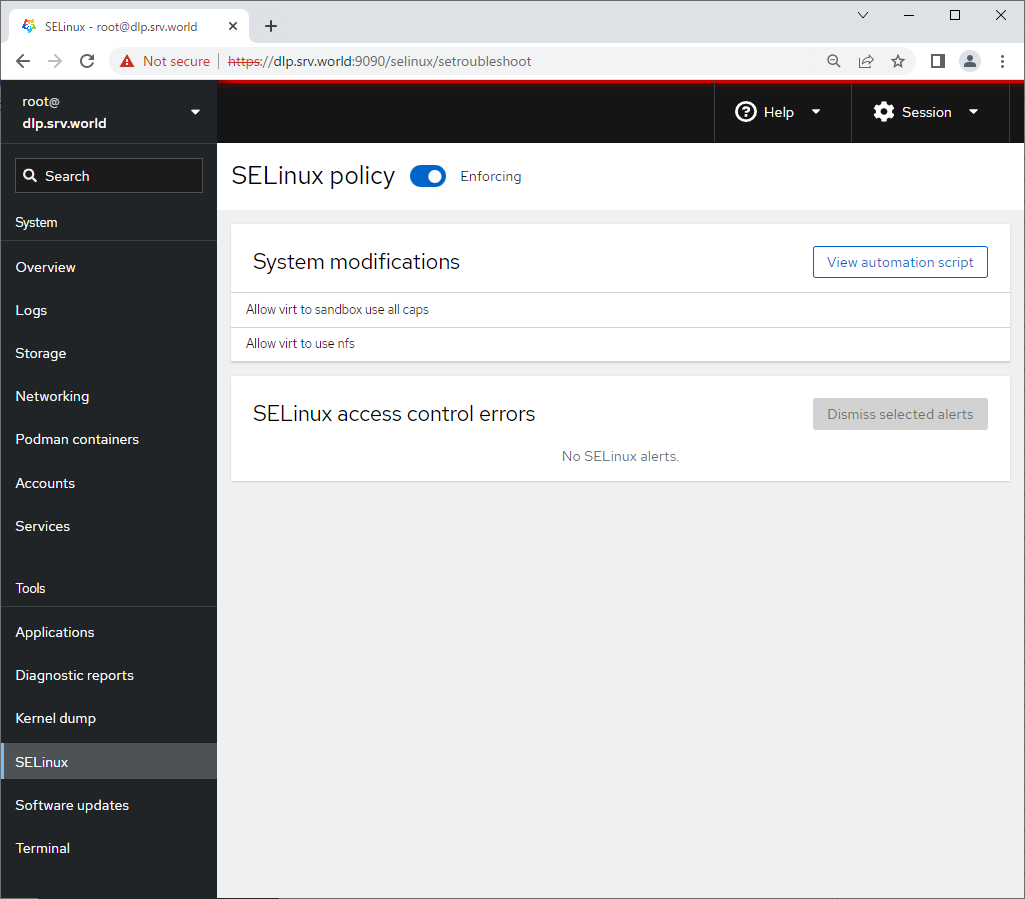
Step [13]For [Software Updates] on the left pane, it's possible to confirm updates or run update packages.
Step [14]For [Terminal] on the left pane, it's possible to opereate system with commands directly.
Manage Vim and Sudo
VIM Setting
There are many cases to use text editor on CUI terminal, so it's more convenient to install editors with advanced features like Vim.
Step [1]Install Vim on this example.
[root@vms ~]# dnf -y install vim-enhanced
Step [2]Set command alias for your own environment.
[root@vms ~]# vi ~/.bashrc
# add alias to the end
alias vi='vim'
# apply changes
[root@vms ~]# source ~/.bashrc
Step [3]Configure Vim for each user environment. (common settings for all users are in [/etc/vimrc])
[root@vms ~]# vi ~/.vimrc
" use extended function of vim
" - no compatible with vi
set nocompatible
" specify encoding
set encoding=utf-8
" specify file encoding
set fileencodings=utf-8,iso-2022-jp,sjis,euc-jp
" specify file formats
set fileformats=unix,dos
" take backup
" - if not, specify [ set nobackup ]
set backup
" specify backup directory
set backupdir=~/backup
" take 50 search histories
set history=50
" ignore Case
set ignorecase
" distinct Capital if you mix it in search words
set smartcase
" highlights matched words
" - if not, specify [ set nohlsearch ]
set hlsearch
" use incremental search
" - if not, specify [ set noincsearch ]
set incsearch
" show line number
" - if not, specify [ set nonumber ]
set number
" visualize break ( $ ) or tab ( ^I )
set list
" highlights parentheses
set showmatch
" not insert LF at the end of file
set binary noeol
" set auto indent
" - if not, specify [ noautoindent ]
set autoindent
" show color display
" - if not, specify [ syntax off ]
syntax on
" change colors for comments if [ syntax on ] is set
highlight Comment ctermfg=LightCyan
" wrap lines
" - if not, specify [ set nowrap ]
set wrap
Sudo Setting
Configure Sudo to separate users' duty if some people share privileges. It does not need to install sudo manually because it is installed by default even if Minimal installed environment.
Step [4]Transfer root privilege all to a user.
[root@vms ~]# visudo
# add to the end: user [alma] can use all root privilege
alma ALL=(ALL) ALL
# how to write ⇒ destination host=(owner) command
# verify with user [alma]
[alma@vms ~]$ /usr/bin/cat /etc/shadow
/usr/bin/cat: /etc/shadow: Permission denied # denied normally
[alma@vms ~]$ sudo /usr/bin/cat /etc/shadow
Password: # user's own password
.....
.....
systemd-oom:!*:18957::::::
systemd-resolve:!*:18957:::::: # just executed
Step [5]In addition to the setting of [1], set some commands prohibit.
[root@vms ~]# visudo
# line 25 : add
# for example, set aliase for the kind of shutdown commands
Cmnd_Alias SHUTDOWN = /usr/sbin/halt, /usr/sbin/shutdown, \
/usr/sbin/poweroff, /usr/sbin/reboot, /usr/sbin/init, /usr/bin/systemctl
# add ( prohibit commands in aliase [SHUTDOWN] )
alma ALL=(ALL) ALL, !SHUTDOWN
# verify with user [alma]
[alma@vms ~]$ sudo /usr/sbin/reboot
[sudo] password for alma:
Sorry, user alma is not allowed to execute '/usr/sbin/reboot' as root on vms.bizantum.lab. # denied normally
Step [6]Transfer some commands with root privilege to users in a group.
[root@vms ~]# visudo
# line 25 : add
# for example, set aliase for the kind of user managment commands
Cmnd_Alias USERMGR = /usr/sbin/useradd, /usr/sbin/userdel, /usr/sbin/usermod, \
/usr/bin/passwd
# add to the end
%usermgr ALL=(ALL) USERMGR
[root@vms ~]# groupadd usermgr
[root@vms ~]# usermod -aG usermgr redhat
# verify with user [redhat]
[redhat@vms ~]$ sudo /usr/sbin/useradd testuser
[redhat@vms ~]$ sudo /usr/bin/passwd testuser
Changing password for user testuser.
New UNIX password:
Retype new UNIX password:
passwd: all authentication tokens updated successfully. # just executed
Step [7]Transfer a command with root privilege to a user.
[root@vms ~]# visudo
# add to the end : settings for each user
fedora ALL=(ALL) /usr/sbin/visudo
ubuntu ALL=(ALL) /usr/sbin/useradd, /usr/sbin/userdel, /usr/sbin/usermod, /usr/bin/passwd
debian ALL=(ALL) /usr/bin/vi
# for example, verify with user [fedora]
[fedora@vms ~]$ sudo /usr/sbin/visudo
## Sudoers allows particular users to run various commands as
## the root user, without needing the root password.
## # just executed
Step [8]It's possible to display Sudo logs on Journald ( with [journalctl] command ) or Rsyslogd ( in [/var/log/secure] file ), however, if you'd like to keep only Sudo logs in another file, Configure like follows.
[root@vms ~]# visudo
# add to the end
# for example, output logs to [local1] facility
Defaults syslog=local1
[root@vms ~]# vi /etc/rsyslog.conf
# line 46,47 : add like follows
*.info;mail.none;authpriv.none;cron.none;local1.none /var/log/messages
local1.* /var/log/sudo.log
# The authpriv file has restricted access.
authpriv.* /var/log/secure
[root@vms ~]# systemctl restart rsyslog
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.