
Introduction
Overview
SSL/TLS certificates are used to encrypt data transmitted between a web server and a client, ensuring data privacy and security. A self-signed SSL/TLS certificate is one that is signed by the same entity to which it belongs, rather than by a trusted Certificate Authority (CA).
What
A self-signed SSL/TLS certificate is a type of digital certificate that is not signed by a public or private trusted CA but by the entity that owns the certificate. It provides the same level of encryption as certificates signed by CAs but lacks the verification of the certificate holder's identity.
Who
Self-signed certificates are typically used by developers, IT professionals, and organizations for internal purposes, such as testing environments, intranet sites, and personal projects where external trust is not required.
Where
Self-signed certificates can be used on any server or system that requires encryption but does not need external validation. Common use cases include local development environments, internal networks, and secure communications within an organization.
When
Self-signed certificates are used when encryption is needed, but the additional cost and complexity of obtaining a CA-signed certificate are not justified. They are often used during development stages and for internal applications where trust chains are not a critical concern.
Why
Understanding the pros and cons of self-signed SSL/TLS certificates can help determine their suitability for different scenarios.
| Pros | Cons |
|---|---|
| Free and easy to create | Not trusted by default in most browsers |
| Provides encryption for data in transit | Lacks identity verification |
| Useful for internal and development environments | May require manual installation and configuration |
How
Here is a basic workflow to create and use a self-signed SSL/TLS certificate:
| Step 1 | Generate a private key using a tool like OpenSSL |
| Step 2 | Create a certificate signing request (CSR) and then sign it with the private key to generate the self-signed certificate |
| Step 3 | Install the self-signed certificate on your server and configure your server to use it for SSL/TLS connections |
Consequences
The use of self-signed SSL/TLS certificates brings various positive and negative consequences:
| Positive |
|
| Negative |
|
Conclusion
Self-signed SSL/TLS certificates offer a cost-effective solution for encrypting data in transit, especially in development and internal environments. While they provide the same encryption capabilities as CA-signed certificates, they lack the identity verification and trust typically required for public-facing applications. Therefore, self-signed certificates are best suited for scenarios where external trust is not critical. For production environments, CA-signed certificates are recommended to ensure user trust and compliance with security standards.
Create Self-Signed SSL/TLS Certificate
Self Signed SSL Certificate is for the purpose of development or testing, if you use your server as a business, it had better buy and use a Formal Certificates.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and work.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# make sure certificates stored PATH
PS C:\Users\Administrator> Get-PSDrive | Format-Table -AutoSize -Wrap
Name Used (GB) Free (GB) Provider Root CurrentLocation
---- --------- --------- -------- ---- ---------------
Alias Alias
C 14.65 64.81 FileSystem C:\ Users\Administrator
Cert Certificate \
Env Environment
Function Function
HKCU Registry HKEY_CURRENT_USER
HKLM Registry HKEY_LOCAL_MACHINE
Variable Variable
WSMan WSMan
# create self signed certificate
# -DnsName (DNS name)
# -KeyAlgorithm (RSA | ECDSA)
# -KeyLength (Key Length)
# -CertStoreLocation (certificate store PATH)
# -NotAfter (valid term : the example below is 10 years)
PS C:\Users\Administrator> New-SelfSignedCertificate `
-DnsName "dns-01.bizantum.lab" `
-KeyAlgorithm RSA `
-KeyLength 2048 `
-CertStoreLocation "Cert:\LocalMachine\My" `
-NotAfter (Get-Date).AddYears(10)
PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\My
Thumbprint Subject
---------- -------
8F34D5F95B3283273D54EA187FFF314CBEB09920 CN=dns-01.bizantum.lab
Step [2]If you'd like to see the your self signed certificate on GUI, run [Run] and input [certlm.msc].
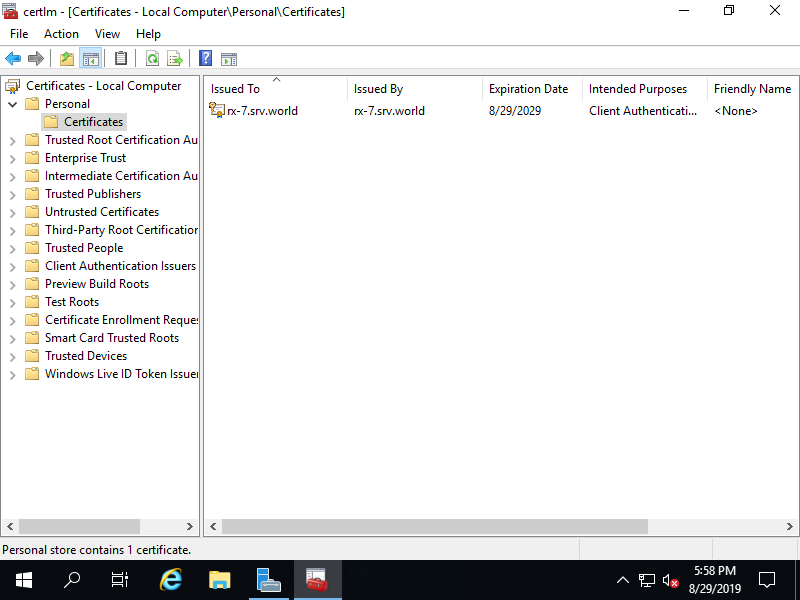
Step [3]If you created self signed certificate like this example [Cert:\LocalMachine\My], it is stored under [Personal] - [Certificate].
- Get link
- X
- Other Apps








Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.