
Introduction
This guide covers the installation and configuration of a mail server on Fedora 40. It will help you understand the what, who, where, when, why, and how of setting up a mail server.
Overview
What
A mail server is a software application that handles the sending, receiving, and storage of email messages. It consists of various components such as the Mail Transfer Agent (MTA), Mail Delivery Agent (MDA), and IMAP/POP3 servers.
Who
This guide is intended for system administrators and IT professionals who need to set up and manage email services for their organization or personal use on Fedora 40.
Where
The steps outlined in this guide should be performed on a Fedora 40 system with administrative privileges. Ensure your system is connected to the internet and has sufficient resources to run a mail server.
When
This guide can be followed whenever you need to set up a mail server on Fedora 40. There are no specific timing requirements, but ensure regular maintenance and updates to keep the mail server running smoothly and securely.
Why
Setting up a mail server on Fedora 40 offers several benefits, but it also comes with some challenges. Here are the pros and cons:
| Pros | Cons |
|---|---|
| Full control over email services | Requires technical knowledge for setup and maintenance |
| Enhanced security and privacy | Potential security risks if not properly configured |
| Customization to meet specific needs | Resource-intensive, requiring sufficient hardware |
| Cost-effective compared to third-party services | Ongoing maintenance and updates needed |
How
Follow these steps to set up Apache HTTPD on Fedora 40:
Follow these steps to install and configure a mail server on Fedora 40:
- Update your system: sudo dnf update -y
- Install necessary packages (Postfix, Dovecot, etc.): sudo dnf install postfix dovecot -y
- Start and enable Postfix service: sudo systemctl start postfix and sudo systemctl enable postfix
- Start and enable Dovecot service: sudo systemctl start dovecot and sudo systemctl enable dovecot
- Edit the Postfix configuration file: sudo nano /etc/postfix/main.cf
- Edit the Dovecot configuration file: sudo nano /etc/dovecot/dovecot.conf
- Add necessary configuration settings (e.g., domain, user accounts, authentication methods)
- Restart the services: sudo systemctl restart postfix and sudo systemctl restart dovecot
- Verify the mail server is running: sudo systemctl status postfix and sudo systemctl status dovecot
Consequences
Setting up a mail server on Fedora 40 can have several consequences:
| Positive |
|
| Negative |
|
Conclusion
Setting up and configuring a mail server on Fedora 40 can provide full control over email services, enhanced security, and cost savings. While there are some potential drawbacks, such as the need for technical expertise and regular maintenance
Install Postfix
Install Postfix to configure SMTP Server.
Step [1]Install Postfix.
[root@bizantum ~]# dnf -y install postfix
Step [2]This example shows to configure SMTP-Auth to use Dovecot's SASL feature.
[root@bizantum ~]# vi /etc/postfix/main.cf
# line 98 : uncomment and specify hostname
myhostname = mail.bizantum.lab
# line 106 : uncomment and specify domain name
mydomain = bizantum.lab
# line 122 : uncomment
myorigin = $mydomain
# line 139 : change
inet_interfaces = all
# line 142 : change it if use only IPv4
inet_protocols = ipv4
# line 187 : add
mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain
# line 290 : uncomment and specify your local network
mynetworks = 127.0.0.0/8, 10.0.0.0/24
# line 447 : uncomment (use Maildir)
home_mailbox = Maildir/
# line 602 : add
smtpd_banner = $myhostname ESMTP
# add follows to last line
# disable SMTP VRFY command
disable_vrfy_command = yes
# require HELO command to sender hosts
smtpd_helo_required = yes
# limit an email size
# example below means 10M bytes limit
message_size_limit = 10240000
# SMTP-Auth settings
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
smtpd_sasl_auth_enable = yes
smtpd_sasl_security_options = noanonymous
smtpd_sasl_local_domain = $myhostname
smtpd_recipient_restrictions = permit_mynetworks, permit_auth_destination, permit_sasl_authenticated, reject
[root@bizantum ~]# systemctl enable --now postfix
Step [3]If Firewalld is running, allow SMTP service. SMTP uses [25/TCP].
[root@bizantum ~]# firewall-cmd --add-service=smtp
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Install Dovecot
Install Dovecot to configure POP/IMAP Server.
Step [1]Install Dovecot.
[root@bizantum ~]# dnf -y install dovecot
Step [2]This example shows to configure to provide SASL function to Postfix.
[root@bizantum ~]# vi /etc/dovecot/dovecot.conf
# line 30 : uncomment (if not use IPv6, remove [::])
listen = *, ::
[root@bizantum ~]# vi /etc/dovecot/conf.d/10-auth.conf
# line 10 : uncomment and change (allow plain text auth)
disable_plaintext_auth = no
# line 100 : add
auth_mechanisms = plain login
[root@bizantum ~]# vi /etc/dovecot/conf.d/10-mail.conf
# line 30 : uncomment and add
mail_location = maildir:~/Maildir
[root@bizantum ~]# vi /etc/dovecot/conf.d/10-master.conf
# line 110-112 : uncomment and add like follows
# Postfix smtp-auth
unix_listener /var/spool/postfix/private/auth {
mode = 0666
user = postfix
group = postfix
}
[root@bizantum ~]# vi /etc/dovecot/conf.d/10-ssl.conf
# line 8 : change (not require SSL)
ssl = yes
[root@bizantum ~]# systemctl enable --now dovecot
Step [3]If Firewalld is running, allow POP/IMAP service. POP uses [110/TCP], IMAP uses [143/TCP].
[root@bizantum ~]# firewall-cmd --add-service={pop3,imap}
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Add Mail User Accounts
Add Mail User Accounts to use Mail Service. This example is for the case you use OS user accounts. Configure basic Postfix settings, and basic Dovecot settings first.
Step [1]To use OS user accounts, that's only adding OS user like follows.
# install mail client program
[root@bizantum ~]# dnf -y install s-nail
# set environment variables to use Maildir
[root@bizantum ~]# echo 'export MAIL=$HOME/Maildir' >> /etc/profile.d/mail.sh
# add a user [fedora]
[root@bizantum ~]# useradd fedora
[root@bizantum ~]# passwd fedora
Step [2]Login as a user added in [1] and try to send an email.
# send to myself [mail (username)@(hostname)]
[fedora@mail ~]$ mail fedora@localhost
# input subject
Subject: Test Mail#1
# input messages
This is the first mail.
# to finish messages, push [Ctrl + D] key
(Preliminary) Envelope contains:
To: fedora@localhost
Subject: Test Mail#1
Send this message [yes/no, empty: recompose]? yes
# see received emails
[fedora@mail ~]$ mail
s-nail version v14.9.24. Type `?' for help
/home/fedora/Maildir: 1 message 1 unread
>U 1 fedora@bizantum.lab 2024-05-16 11:13 15/421 "Test Mail#1 "
# input a number you'd like to see an email
& 1
[-- Message 1 -- 15 lines, 421 bytes --]:
Date: Thu, 16 May 2024 11:13:04 +0900
To: fedora@localhost
Subject: Test Mail#1
Message-Id: <20240516021304.7AA2B89C49A@mail.bizantum.lab>
From: fedora@bizantum.lab
This is the first mail.
# to quit, input [q]
& q
Held 1 message in /home/fedora/Maildir
Email Client Setting
Configure your Mail Client on your PC. This example shows with Mozilla Thunderbird.
Step [1]Run Thunderbird and Click [New Account] - [Existing Email].
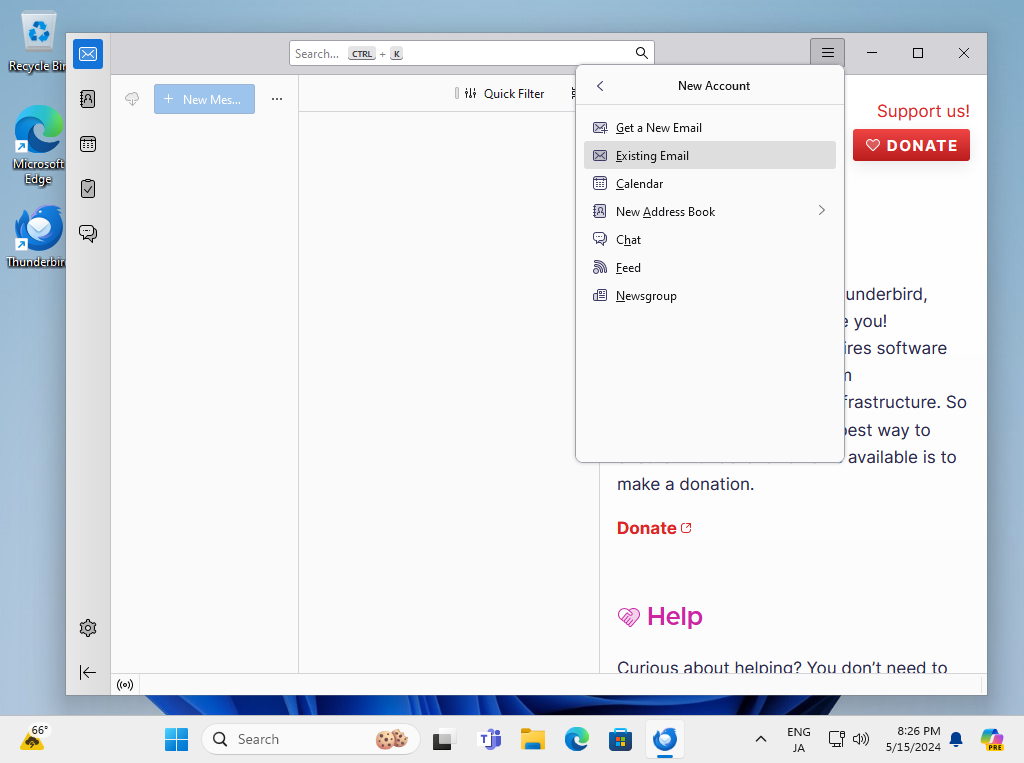
Step [2]Input any name which is displayed as email-Sender and also input email address and password, amd then Click [Continue] button.
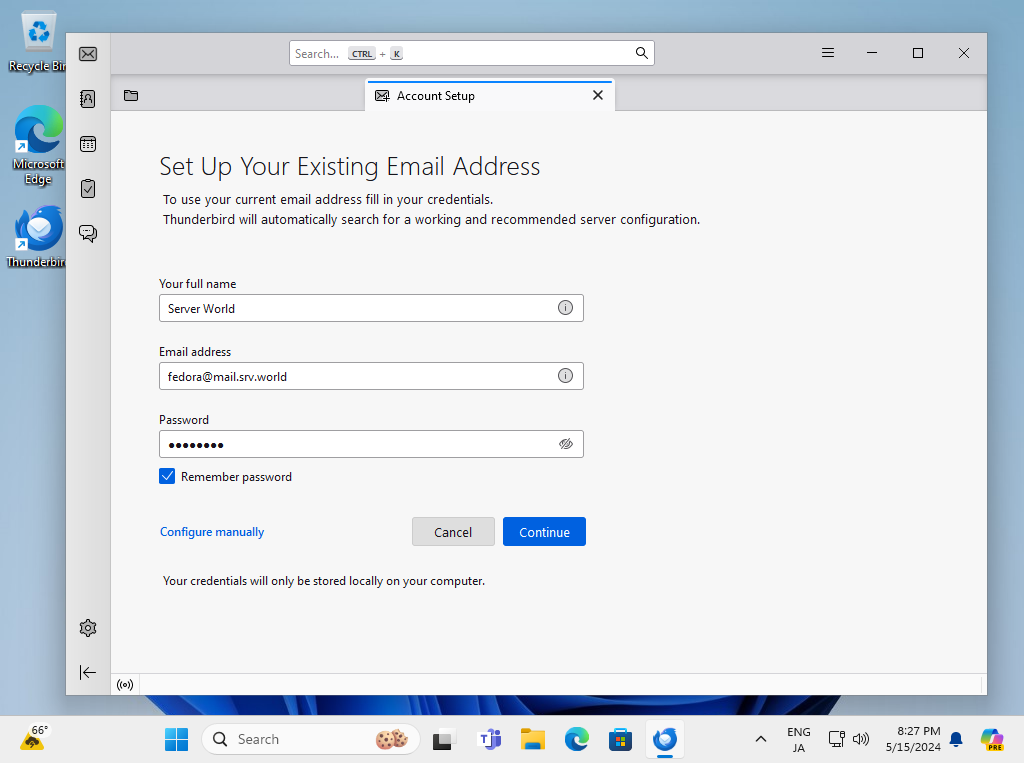
Step [3]Click [Configure Manually] button.
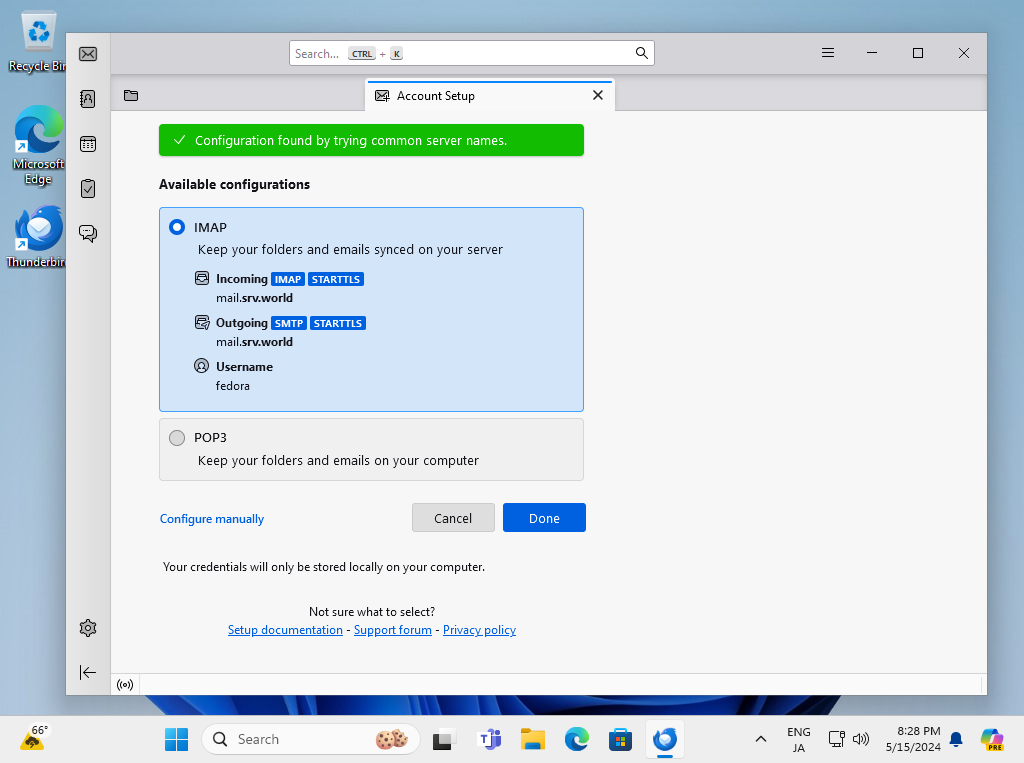
Step [4]Confirm selection and also confirm [Authentication] fields are selected [Normal password] like follows, then Click [Done] to finish.
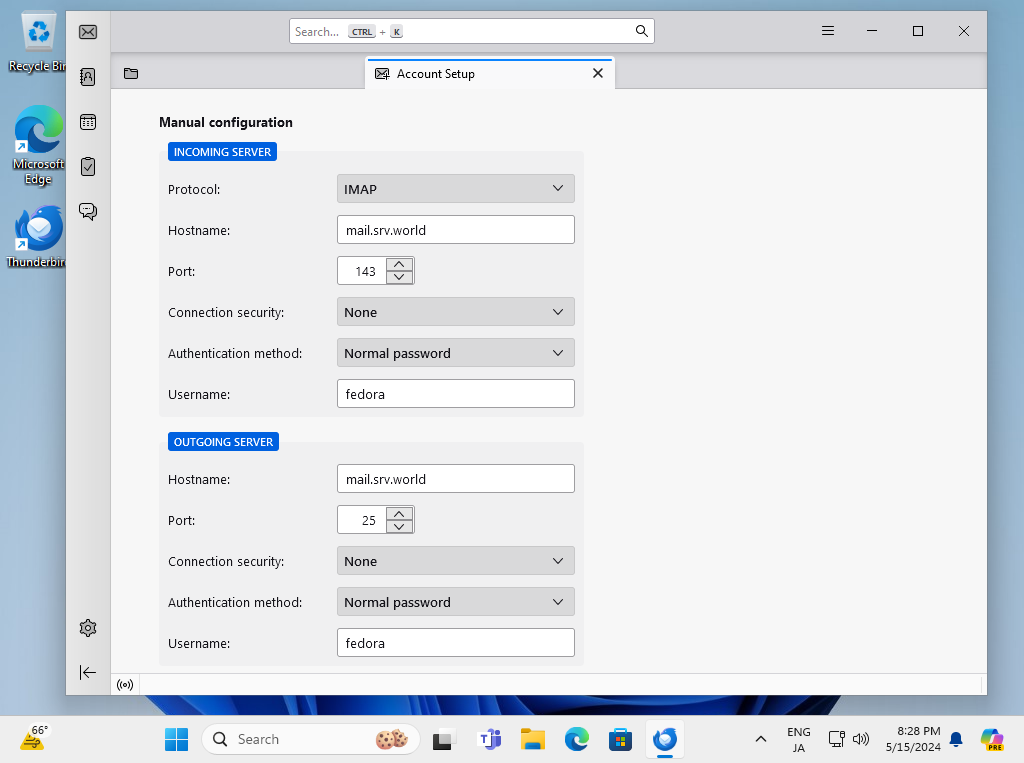
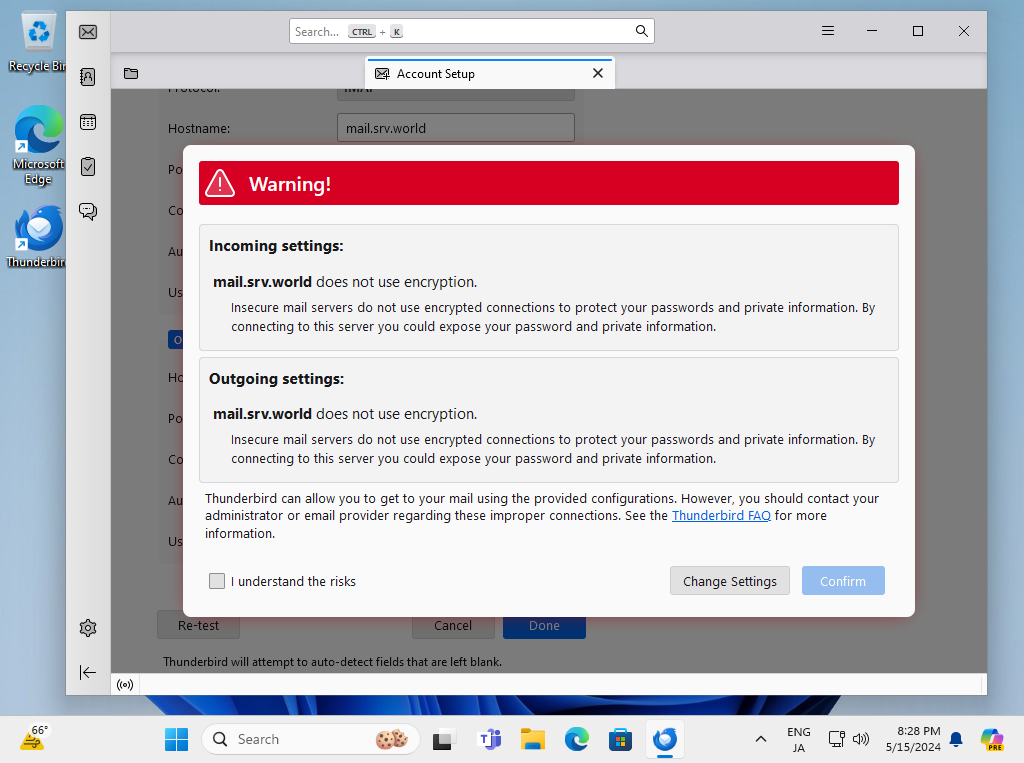
Step [5]The warnings is shown because connection is not encrypted. If OK, Click [Done] button, If not OK, Configure more to refer to SSL/TLS settings section.
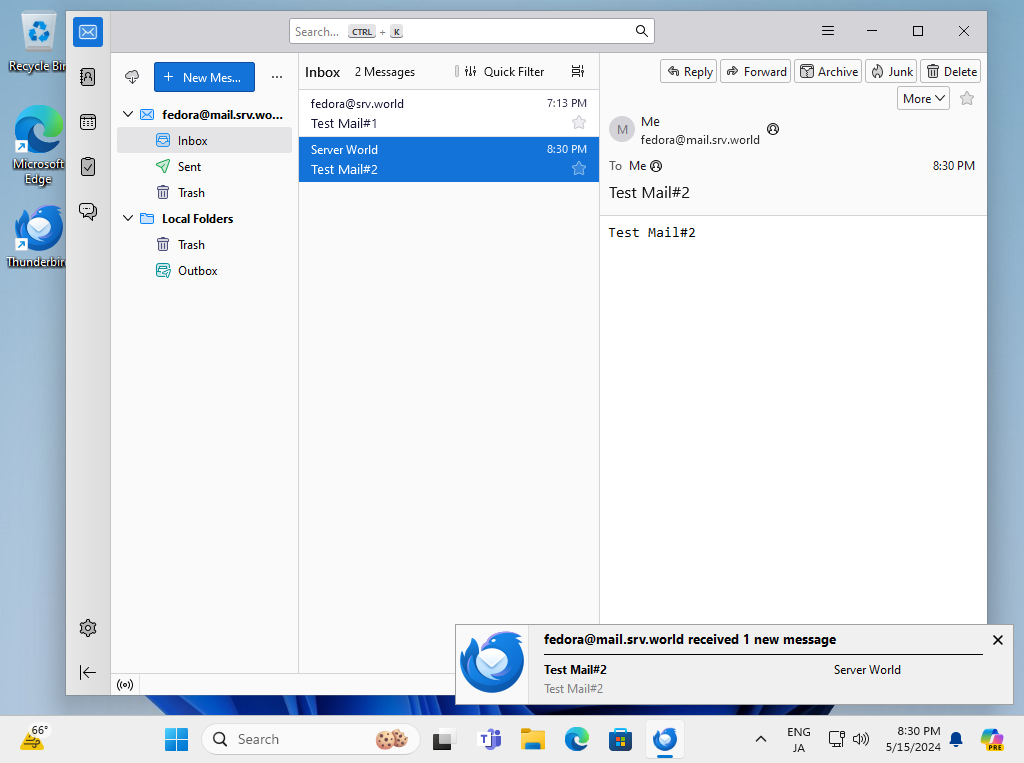
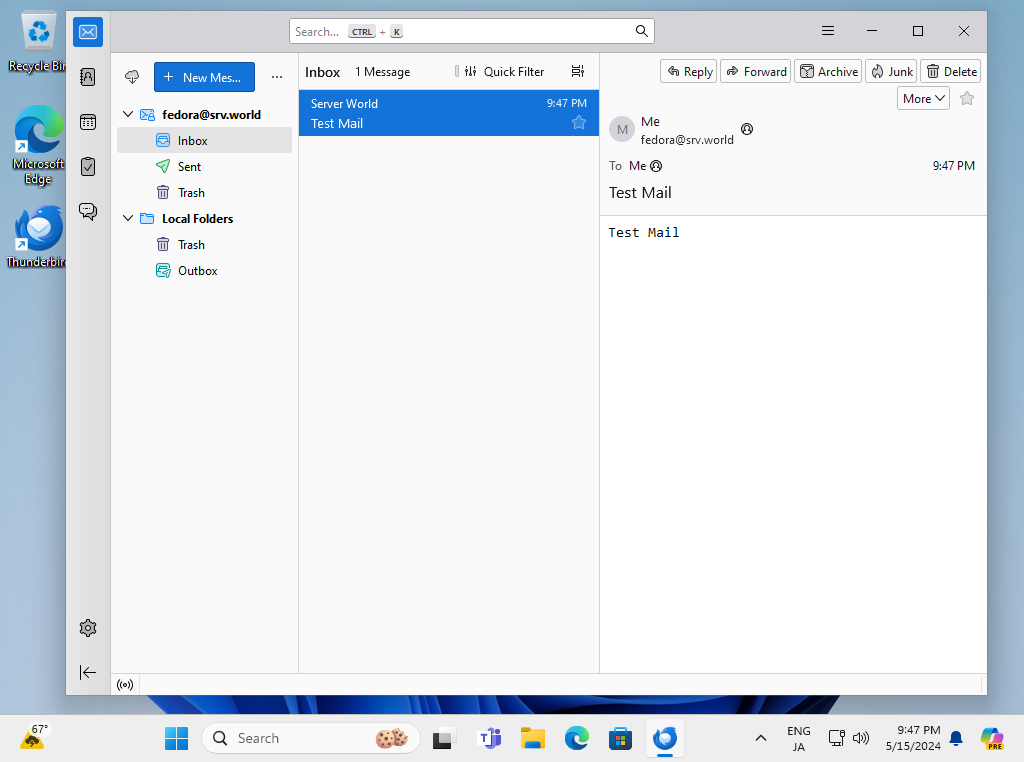
Step [6]If email account setup normally, it's possible to send or receive emails like follows.
SSL/TLS Setting
Configure SSL/TLS to encrypt connections.
Step [1]Get SSL certificate, Refer to here.
Step [2]Configure Postfix and Dovecot.
[root@bizantum ~]# vi /etc/postfix/main.cf
# line 718, 724 : comment out
#smtpd_tls_cert_file = /etc/pki/tls/certs/postfix.pem
#smtpd_tls_key_file = /etc/pki/tls/private/postfix.key
# add to last line (replace certificate to your own one)
smtpd_tls_security_level = may
smtpd_tls_cert_file = /etc/letsencrypt/live/mail.bizantum.lab/fullchain.pem
smtpd_tls_key_file = /etc/letsencrypt/live/mail.bizantum.lab/privkey.pem
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
[root@bizantum ~]# vi /etc/postfix/master.cf
# line 19, 20, 22 : uncomment
submission inet n - n - - smtpd
-o syslog_name=postfix/submission
# -o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
# if you use SMTPS (465), add follows to the end
smtps inet n - n - - smtpd
-o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
[root@bizantum ~]# vi /etc/dovecot/conf.d/10-ssl.conf
# line 8 : change (if set SSL required, specify [required])
ssl = yes
# line 14,15 : specify certificates
ssl_cert = </etc/letsencrypt/live/mail.bizantum.lab/fullchain.pem
ssl_key = </etc/letsencrypt/live/mail.bizantum.lab/privkey.pem
[root@bizantum ~]# systemctl restart postfix dovecot
Step [3]If SELinux is enabled, restore context for certificates.
[root@bizantum ~]# restorecon -v /etc/letsencrypt/live/mail.bizantum.lab/fullchain.pem
[root@bizantum ~]# restorecon -v /etc/letsencrypt/live/mail.bizantum.lab/privkey.pem
Step [4] If Firewalld is running, allow SMTP-Submission/SMTPS/POP3S/IMAPS services. SMTP-Submission uses [587/TCP] (used STARTTLS), SMTPS uses [465/TCP], POP3S uses [995/TCP], IMAPS uses [993/TCP].
[root@bizantum ~]# firewall-cmd --add-service={smtp-submission,smtps,pop3s,imaps}
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
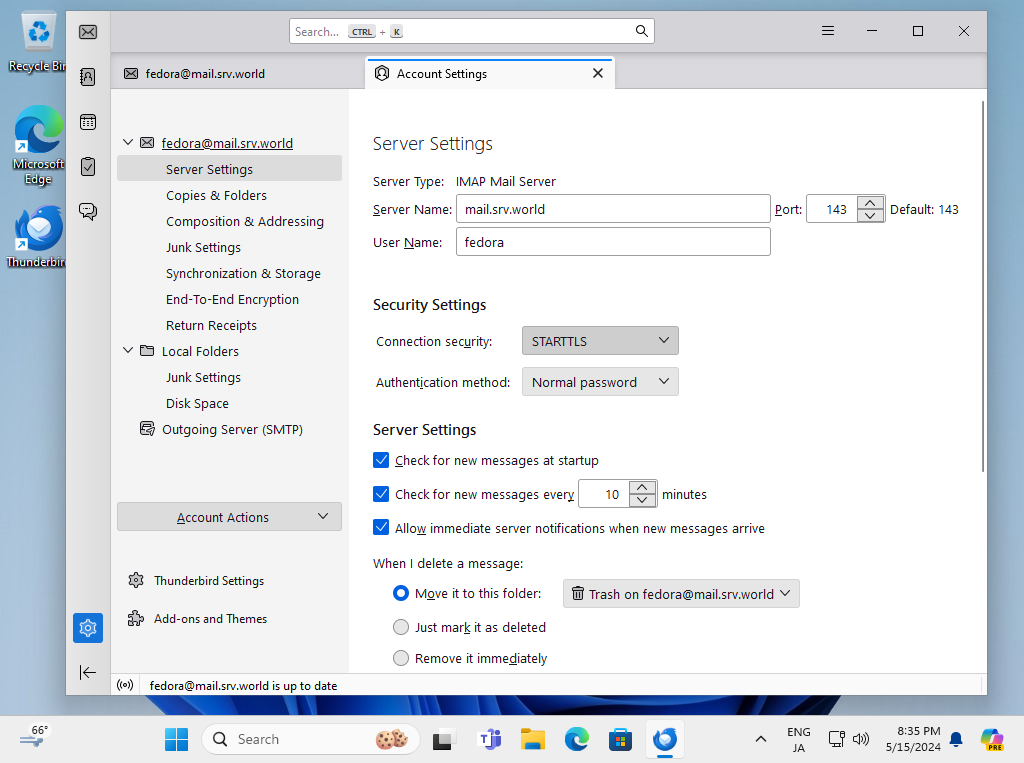
Step [5]For Client's settings, ( Mozilla Thunderbird ) Open account's property and move to [Server Settings] on the left pane, then Select [STARTTLS] or [SSL/TLS] on [Connection security] field on the right pane.
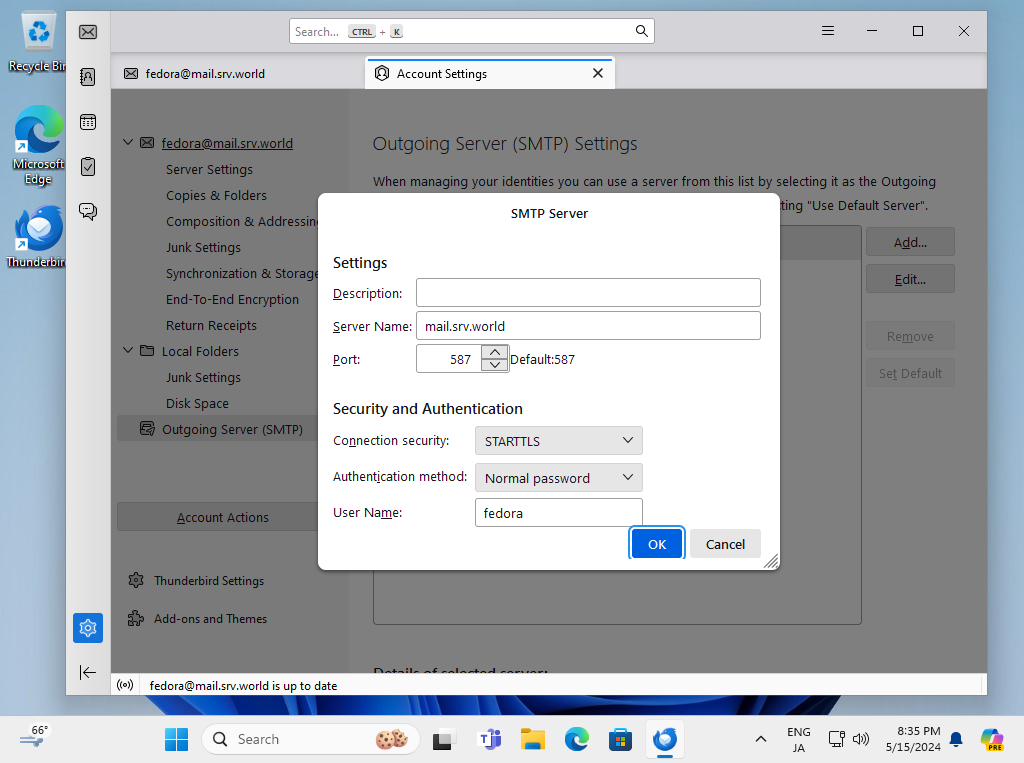
Step [6] Move to [Outgoing Server] on the left pane, then Select [STARTTLS] or [SSL/TLS] on [Connection security] field. Furthermore, change port to the used port. ([STARTTLS] uses [587], [SSL/TLS] uses 465)
Step [7]Verify possible to send or receive Emails normally.
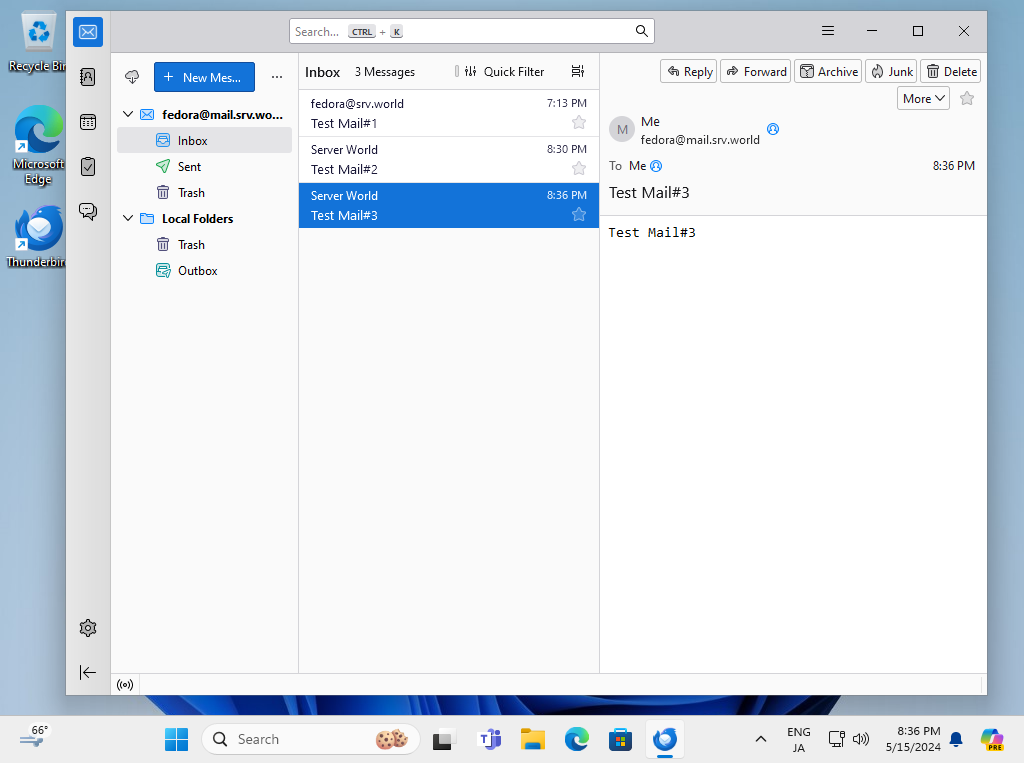
Set Virtual Domain
Configure for Virtual Domain to send an email with another domain name different from original domain. This example is for the case you use OS user accounts. If you use virtual mailbox accounts, refer to here. For example, present domain name ⇒ bizantum.lab new domain name ⇒ virtual.host a User [fedora] has an email address [fedora@mail.bizantum.lab], a User [redhat] has an email address [fedora@mail.virtual.host], the user [redhat] uses the same name for before [@] with [fedora].
Step [1]Configure Postfix.
[root@bizantum ~]# vi /etc/postfix/main.cf
# add to last line of the file
virtual_alias_domains = virtual.host
virtual_alias_maps = hash:/etc/postfix/virtual
[root@bizantum ~]# vi /etc/postfix/virtual
# add to head line of the file
fedora@mail.virtual.host redhat
[root@bizantum ~]# postmap /etc/postfix/virtual
[root@bizantum ~]# systemctl reload postfix
Step [2]Set new account to Email client and verify possible to send emails.
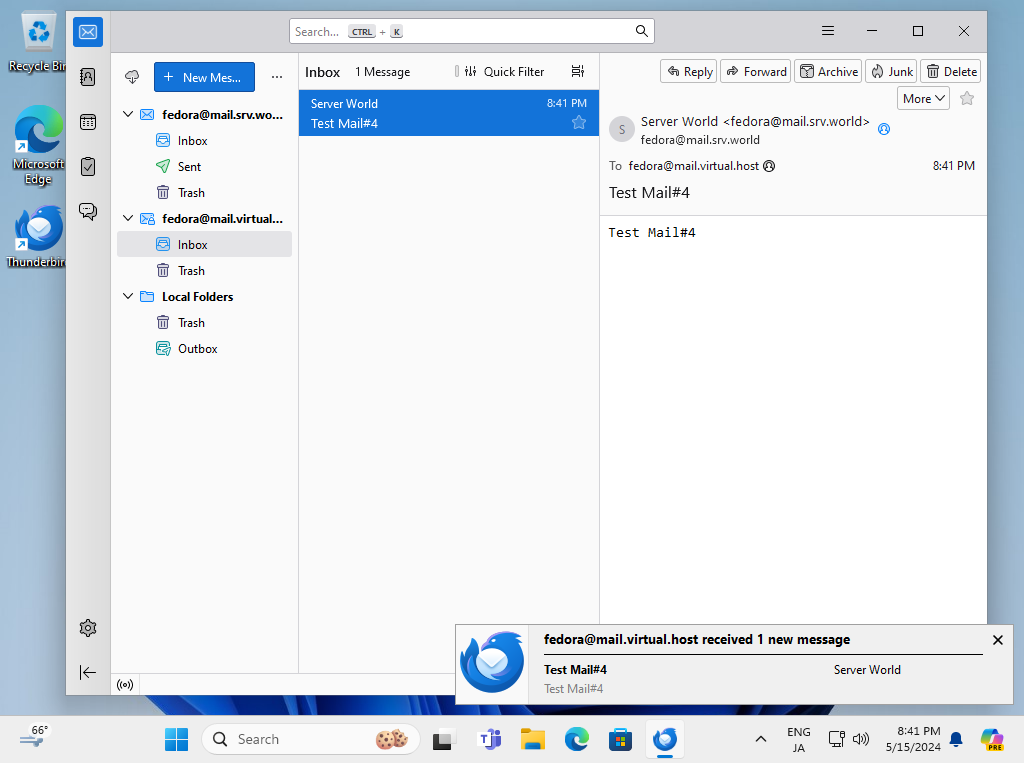
Postfix + Clamav + Amavisd
Configure Virus-Scanning for EMails with Postfix + Clamav.
Step [1]Install Clamav, refer to here.
Step [2]Install Amavisd and Clamav Server.
[root@bizantum ~]# dnf -y install amavis clamd perl-Digest-SHA1 perl-IO-stringy
[root@bizantum ~]# vi /etc/clamd.d/scan.conf
# line 8 : comment out
#Example
# line 14 : uncomment
LogFile /var/log/clamd.scan
# line 77 : uncomment
PidFile /var/run/clamd.scan/clamd.pid
# line 81 : uncomment
TemporaryDirectory /var/tmp
# line 96 : uncomment
LocalSocket /var/run/clamd.scan/clamd.sock
[root@bizantum ~]# touch /var/log/clamd.scan
[root@bizantum ~]# chown clamscan:clamscan /var/log/clamd.scan
[root@bizantum ~]# systemctl enable --now clamd@scan
Step [3] If SELinux is enabled, add rules to start Clamav Server like follows.
[root@bizantum ~]# restorecon -v /var/log/clamd.scan
[root@bizantum ~]# setsebool -P antivirus_can_scan_system on
Step [4]Configure Amavisd.
[root@bizantum ~]# vi /etc/amavisd/amavisd.conf
# line 23 : change to the own domain name
$mydomain = 'bizantum.lab';
# line 171 : uncomment and change to the your hostname
$myhostname = 'mail.bizantum.lab';
[root@bizantum ~]# systemctl enable --now amavisd
Step [5]Configure Postfix.
[root@bizantum ~]# vi /etc/postfix/main.cf
# add follows to last line
content_filter=smtp-amavis:[127.0.0.1]:10024
[root@bizantum ~]# vi /etc/postfix/master.cf
# add follows to last line
smtp-amavis unix - - n - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
-o disable_dns_lookups=yes
127.0.0.1:10025 inet n - n - - smtpd
-o content_filter=
-o local_recipient_maps=
-o relay_recipient_maps=
-o smtpd_restriction_classes=
-o smtpd_client_restrictions=
-o smtpd_helo_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o mynetworks=127.0.0.0/8
-o strict_rfc821_envelopes=yes
-o smtpd_error_sleep_time=0
-o smtpd_soft_error_limit=1001
-o smtpd_hard_error_limit=1000
[root@bizantum ~]# systemctl restart postfix
Step [6]That' OK. [X-Virus-Scanned: ***] lines are added in the header section of emails after this configuration and emails with known Virus will not sent to Clients.
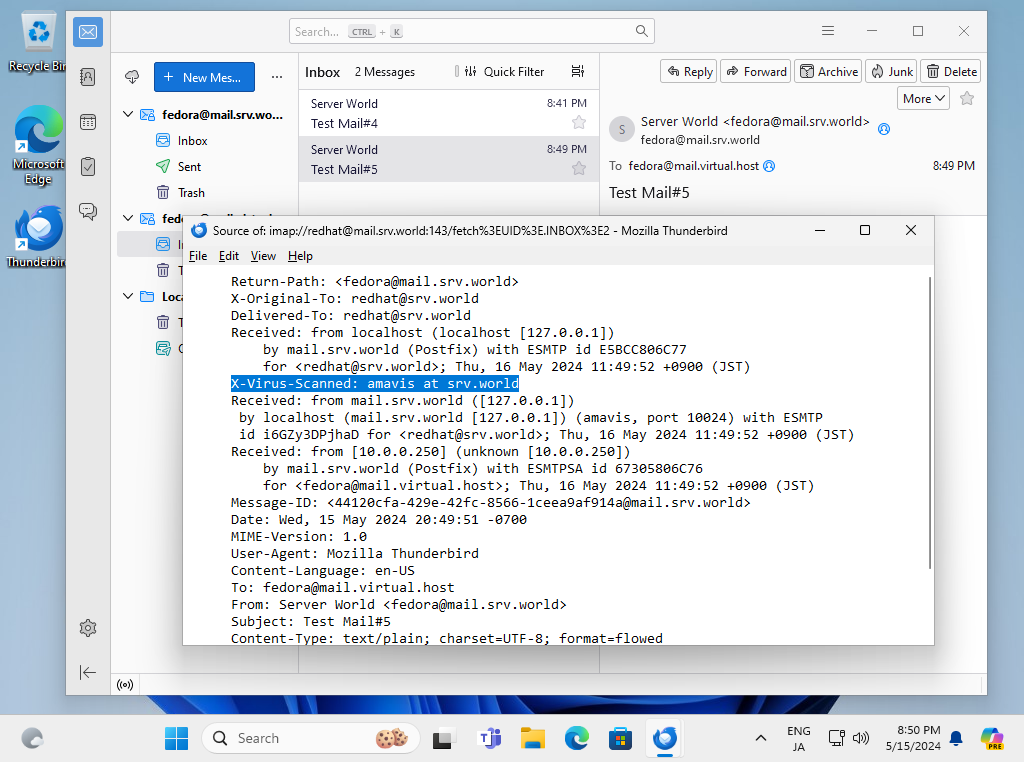
Mail Log Report : pflogsumm
Install pflogsumm which is the Postfix Log reporting tool.
Step [1]Install postfix-perl-scripts package.
[root@bizantum ~]# dnf -y install postfix-perl-scripts
# generate mail log summary for yesterday
[root@bizantum ~]# perl /usr/sbin/pflogsumm -d yesterday /var/log/maillog
Postfix log summaries for May 16
Grand Totals
------------
messages
6 received
6 delivered
0 forwarded
0 deferred
0 bounced
0 rejected (0%)
0 reject warnings
0 held
0 discarded (0%)
3566 bytes received
3566 bytes delivered
2 senders
2 sending hosts/domains
3 recipients
3 recipient hosts/domains
Per-Hour Traffic Summary
------------------------
time received delivered deferred bounced rejected
--------------------------------------------------------------------
0000-0100 0 0 0 0 0
0100-0200 0 0 0 0 0
0200-0300 0 0 0 0 0
0300-0400 0 0 0 0 0
0400-0500 0 0 0 0 0
0500-0600 0 0 0 0 0
0600-0700 0 0 0 0 0
0700-0800 0 0 0 0 0
0800-0900 0 0 0 0 0
0900-1000 0 0 0 0 0
1000-1100 0 0 0 0 0
1100-1200 6 6 0 0 0
1200-1300 0 0 0 0 0
1300-1400 0 0 0 0 0
1400-1500 0 0 0 0 0
1500-1600 0 0 0 0 0
1600-1700 0 0 0 0 0
1700-1800 0 0 0 0 0
1800-1900 0 0 0 0 0
1900-2000 0 0 0 0 0
2000-2100 0 0 0 0 0
2100-2200 0 0 0 0 0
2200-2300 0 0 0 0 0
2300-2400 0 0 0 0 0
Host/Domain Summary: Message Delivery
--------------------------------------
sent cnt bytes defers avg dly max dly host/domain
-------- ------- ------- ------- ------- -----------
3 2110 0 0.2 s 0.5 s bizantum.lab
2 1120 0 0.0 s 0.0 s mail.bizantum.lab
1 336 0 0.1 s 0.1 s localhost
Host/Domain Summary: Messages Received
---------------------------------------
msg cnt bytes host/domain
-------- ------- -----------
5 3230 mail.bizantum.lab
1 336 bizantum.lab
Senders by message count
------------------------
5 fedora@mail.bizantum.lab
1 fedora@bizantum.lab
Recipients by message count
---------------------------
3 redhat@bizantum.lab
2 fedora@mail.bizantum.lab
1 fedora@localhost
Senders by message size
-----------------------
3230 fedora@mail.bizantum.lab
336 fedora@bizantum.lab
Recipients by message size
--------------------------
2110 redhat@bizantum.lab
1120 fedora@mail.bizantum.lab
336 fedora@localhost
message deferral detail: none
message bounce detail (by relay): none
message reject detail: none
message reject warning detail: none
message hold detail: none
message discard detail: none
smtp delivery failures: none
Warnings
--------
smtpd (total: 1)
1 TLS library problem: error:0A000412:SSL routines::ssl/tls alert...
Fatal Errors: none
Panics: none
Master daemon messages
----------------------
3 daemon started -- version 3.8.5, configuration /etc/postfix
2 terminating on signal 15
1 reload -- version 3.8.5, configuration /etc/postfix
[root@bizantum ~]# crontab -e
# for example, send mail log summary at AM 1:00 everyday to root
00 01 * * * perl /usr/sbin/pflogsumm -e -d yesterday /var/log/maillog | mail -s 'Logwatch for Postfix' root
Add Mail User Accounts (Virtual User)
Add Mail User Accounts to use Mail Service. This example is for the case you use virtual mail-user accounts, not use OS accounts.
Step [1] Configure basic Postfix settings and basic Dovecot settings first.
Step [2]Configure additional settings to Postfix and Dovecot.
# create admin user for virtual mailboxes
[root@bizantum ~]# useradd --uid 20000 --shell /sbin/nologin vmail
[root@bizantum ~]# vi /etc/postfix/main.cf
# line 187 : comment out
#mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain
# line 447 : change
home_mailbox = /home/vmail/%d/%n/Maildir
# add to last line
# if specify multiple domains, specify comma or space separated
virtual_mailbox_domains = bizantum.lab, virtual.host
virtual_mailbox_base = /home/vmail
virtual_mailbox_maps = hash:/etc/postfix/virtual-mailbox
virtual_uid_maps = static:20000
virtual_gid_maps = static:20000
[root@bizantum ~]# vi /etc/dovecot/conf.d/10-auth.conf
# line 100 : add
auth_mechanisms = cram-md5 plain login
# line 122 : comment out
#!include auth-system.conf.ext
# line 125 : comment out
!include auth-passwdfile.conf.ext
# line 127 : comment out
!include auth-static.conf.ext
[root@bizantum ~]# vi /etc/dovecot/conf.d/auth-passwdfile.conf.ext
# line 8 : change
passdb {
driver = passwd-file
args = scheme=CRAM-MD5 username_format=%u /etc/dovecot/users
# line 11 : comment out all [userdb] section
#userdb {
# driver = passwd-file
# args = username_format=%u /etc/dovecot/users
#.....
#.....
#}
[root@bizantum ~]# vi /etc/dovecot/conf.d/auth-static.conf.ext
# line 21-24 : uncomment and change
userdb {
driver = static
args = uid=vmail gid=vmail home=/home/vmail/%d/%n
}
[root@bizantum ~]# vi /etc/dovecot/conf.d/10-mail.conf
# line 30 : change
mail_location = maildir:/home/vmail/%d/%n/Maildir
[root@bizantum ~]# systemctl restart postfix dovecot
Step [3]Add virtual mail user accounts.
[root@bizantum ~]# vi /etc/postfix/virtual-mailbox
# create new
# [user account] [mailbox]
cent@bizantum.lab bizantum.lab/cent/Maildir/
fedora@bizantum.lab bizantum.lab/fedora/Maildir/
redhat@virtual.host virtual.host/redhat/Maildir/
[root@bizantum ~]# postmap /etc/postfix/virtual-mailbox
# generate encrypted password
[root@bizantum ~]# doveadm pw -s CRAM-MD5
Enter new password:
Retype new password:
{CRAM-MD5}xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
[root@bizantum ~]# vi /etc/dovecot/users
# create new
# [user account] [password]
cent@bizantum.lab:{CRAM-MD5}xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
fedora@bizantum.lab:{CRAM-MD5}xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
redhat@virtual.host:{CRAM-MD5}xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Step [4]That's OK. Verify to test to send emails with E-Mail client. For settings on this example, specify email address for [Username] on Email Client settings.
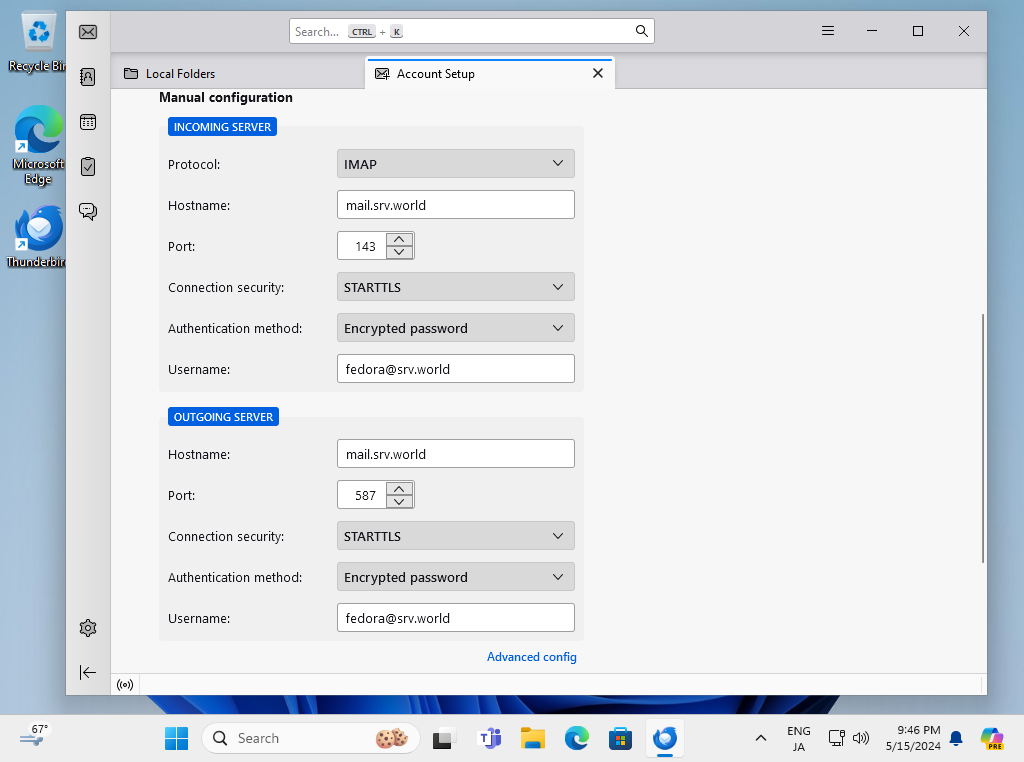
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.