
Introduction
This guide covers the installation and configuration of Vsftpd on Fedora 40 using the 5W1H approach. We will explore the What, Who, Where, When, Why, How, Consequences, and Conclusion of setting up Vsftpd.
Overview
What
Vsftpd (Very Secure FTP Daemon) is a fast, secure, and stable FTP server for Unix-like systems. It supports many functionalities, including user management and secure connections.
Who
This guide is intended for system administrators and IT professionals who need to set up an FTP server to manage file transfers on Fedora 40.
Where
The setup process can be carried out on any server running Fedora 40, whether it's a physical machine, virtual machine, or cloud instance.
When
Setting up Vsftpd should be done during a planned maintenance window to avoid potential disruptions to existing services.
Why
Implementing Vsftpd on your server offers several advantages:
| Pros | Cons |
|---|---|
| High security and performance | Initial setup complexity for beginners |
| Supports secure FTP (FTPS) | Requires careful configuration to avoid vulnerabilities |
| Robust user management | Limited GUI tools for management |
How
Follow these steps to set up Vsftpd on Fedora 40:
| Step 1 | Update your system: sudo dnf update -y |
| Step 2 | Install the Vsftpd package: sudo dnf install -y vsftpd |
| Step 3 | Start and enable the Vsftpd service: sudo systemctl start vsftpd sudo systemctl enable vsftpd |
| Step 4 | Configure Vsftpd by editing the configuration file: sudo nano /etc/vsftpd/vsftpd.conf Adjust settings as needed, such as enabling anonymous FTP or local user FTP. |
| Step 5 | Allow FTP traffic through the firewall: sudo firewall-cmd --permanent --add-service=ftp sudo firewall-cmd --reload |
| Step 6 | Restart the Vsftpd service to apply the changes: sudo systemctl restart vsftpd |
Consequences
Setting up Vsftpd on Fedora 40 can have the following consequences:
| Positive |
|
| Negative |
|
Conclusion
Setting up Vsftpd on Fedora 40 is essential for achieving secure and efficient file transfers. While the initial setup can be complex and demands regular maintenance, the benefits of a secure, reliable, and high-performance FTP server make Vsftpd a valuable addition to any IT infrastructure. By following this guide, system administrators can ensure their file transfer services are secure and efficient.
Install Vsftpd
Install Vsftpd to configure FTP Server.
Step [1]Install and Configure Vsftpd.
[root@bizantum ~]# dnf -y install vsftpd
[root@bizantum ~]# vi /etc/vsftpd/vsftpd.conf
# line 12 : make sure value is [NO] (no anonymous)
anonymous_enable=NO
# line 100, 101 : uncomment (enable chroot)
# and add the line to enable writable under the chroot directory
chroot_local_user=YES
chroot_list_enable=YES
allow_writeable_chroot=YES
# line 103 : uncomment (chroot list file)
chroot_list_file=/etc/vsftpd/chroot_list
# line 109 : uncomment
ls_recurse_enable=YES
# line 114 : change (if listening IPv4 only)
# if listening IPv4 and IPv6 both, specify [NO]
listen=YES
# line 123 : change (if listening IPv6 only)
# if listening IPv4 and IPv6 both, specify [YES]
listen_ipv6=NO
# add to the end
# specify root directory (if don't specify, users' home directory become FTP home directory)
local_root=public_html
# use local time
use_localtime=YES
[root@bizantum ~]# vi /etc/vsftpd/chroot_list
# add users you allow to move over their home directory
fedora
[root@bizantum ~]# systemctl enable --now vsftpd
Step [2]If Firewalld is running, allow FTP service.
[root@bizantum ~]# firewall-cmd --add-service=ftp
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [3]If SELinux is enabled, change Boolean setting.
[root@bizantum ~]# setsebool -P ftpd_full_access on
Install ProFTPD
Install ProFTPD to configure FTP Server.
Step [1]Install and configure ProFTPD.
[root@bizantum ~]# dnf -y install proftpd
[root@bizantum ~]# vi /etc/proftpd.conf
# line 80 : change to your hostname
ServerName "www.bizantum.lab"
# line 82 : change to your email address
ServerAdmin root@bizantum.lab
# line 119 : add
# get access-log and auth-log
ExtendedLog /var/log/proftpd/access.log WRITE,READ default
ExtendedLog /var/log/proftpd/auth.log AUTH auth
[root@bizantum ~]# vi /etc/ftpusers
# add users you prohibit to FTP access
test
[root@bizantum ~]# systemctl enable --now proftpd
Step [2]If Firewalld is running, allow FTP service.
[root@bizantum ~]# firewall-cmd --add-service=ftp --permanent
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [3]If SELinux is enabled, change Boolean setting.
[root@bizantum ~]# setsebool -P ftpd_full_access on
FTP Client : Fedora
For how to connect to FTP server from Clients computer, the example follows is on Fedora.
Step [1]Install FTP Client.
[root@dlp ~]# dnf -y install lftp
Step [2]Login as a common user and use FTP access.
# lftp [option] [hostname]
[redhat@dlp ~]$ lftp -u fedora www.bizantum.lab
Password: # login user password
lftp fedora@www.bizantum.lab:~>
# show current directory on FTP server
lftp fedora@www.bizantum.lab:~> pwd
ftp://fedora@www.bizantum.lab
# show current directory on localhost
lftp fedora@www.bizantum.lab:~> !pwd
/home/redhat
# show files in current directory on FTP server
lftp fedora@www.bizantum.lab:~> ls
drwxr-xr-x 2 1000 1000 23 May 15 01:33 public_html
-rw-r--r-- 1 1000 1000 399 May 15 16:32 test.py
# show files in current directory on localhost
lftp fedora@www.bizantum.lab:~> !ls -l
total 12
-rw-rw-r-- 1 redhat redhat 10 May 15 14:30 redhat.txt
-rw-rw-r-- 1 redhat redhat 10 May 15 14:59 test2.txt
-rw-rw-r-- 1 redhat redhat 10 May 15 14:59 test.txt
# change directory
lftp fedora@www.bizantum.lab:~> cd public_html
lftp fedora@www.bizantum.lab:~/public_html> pwd
ftp://fedora@www.bizantum.lab/%2Fhome/fedora/public_html
# upload a file to FTP server
lftp fedora@www.bizantum.lab:~> put redhat.txt
22 bytes transferred
Total 2 files transferred
lftp fedora@www.bizantum.lab:~> ls
drwxr-xr-x 2 1000 1000 23 May 15 01:33 public_html
-rw-r--r-- 1 1000 1000 10 May 15 17:01 redhat.txt
-rw-r--r-- 1 1000 1000 399 May 15 16:32 test.py
-rw-r--r-- 1 1000 1000 10 May 15 17:01 test.txt
# upload some files to FTP server
lftp fedora@www.bizantum.lab:~> mput test.txt test2.txt
22 bytes transferred
Total 2 files transferred
lftp fedora@www.bizantum.lab:~> ls
drwxr-xr-x 2 1000 1000 23 May 15 01:33 public_html
-rw-r--r-- 1 1000 1000 399 May 15 16:32 test.py
-rw-r--r-- 1 1000 1000 10 May 15 17:06 test.txt
-rw-r--r-- 1 1000 1000 10 May 15 17:06 test2.txt
# set permission to overwrite files on localhost when using [get/mget]
lftp fedora@www.bizantum.lab:~> set xfer:clobber on
# download a file to localhost
lftp fedora@www.bizantum.lab:~> get test.py
416 bytes transferred
# download some remote files to localhost
lftp fedora@www.bizantum.lab:~> mget test.txt test2.txt
20 bytes transferred
Total 2 files transferred
# create a directory on remote current directory
lftp fedora@www.bizantum.lab:~> mkdir testdir
mkdir ok, `testdir' created
lftp fedora@www.bizantum.lab:~> ls
drwxr-xr-x 2 1000 1000 23 May 15 01:33 public_html
-rw-r--r-- 1 1000 1000 399 May 15 16:32 test.py
-rw-r--r-- 1 1000 1000 10 May 15 17:06 test.txt
-rw-r--r-- 1 1000 1000 10 May 15 17:06 test2.txt
drwxr-xr-x 2 1000 1000 6 May 15 17:16 testdir
226 Directory send OK.
# remove a directory on remote current directory
lftp fedora@www.bizantum.lab:~> rmdir testdir
rmdir ok, `testdir' removed
lftp fedora@www.bizantum.lab:~> ls
drwxr-xr-x 2 1000 1000 23 May 15 01:33 public_html
-rw-r--r-- 1 1000 1000 399 May 15 16:32 test.py
-rw-r--r-- 1 1000 1000 10 May 15 17:06 test.txt
-rw-r--r-- 1 1000 1000 10 May 15 17:06 test2.txt
# remove a remote file
lftp fedora@www.bizantum.lab:~> rm test2.txt
rm ok, `test2.txt' removed
lftp fedora@www.bizantum.lab:~> ls
drwxr-xr-x 2 1000 1000 23 May 15 01:33 public_html
-rw-r--r-- 1 1000 1000 399 May 15 16:32 test.py
-rw-r--r-- 1 1000 1000 10 May 15 17:06 test.txt
# remove some remote files
lftp fedora@www.bizantum.lab:~> mrm redhat.txt test.txt
rm ok, 2 files removed
lftp fedora@www.bizantum.lab:~> ls
drwxr-xr-x 2 1000 1000 23 May 15 01:33 public_html
# execute commands with ![command]
lftp fedora@www.bizantum.lab:~> !cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
.....
.....
fedora:x:1001:1001::/home/fedora:/bin/bash
# exit
lftp fedora@www.bizantum.lab:~> quit
221 Goodbye.
FTP Client : Windows
Configure Client computer to connect to FTP Server. The example below is for Windows.
Step [1] For example, use FileZilla for FTP Client software. Download FileZilla from the follows. ⇒ https://filezilla-project.org/download.php?type=client
Step [2] Install FileZilla to your Windows PC and start it, then following screen is shown. Input your FTP Hostname, username. password, connection-port, like follows. Next Click [Quick connect].
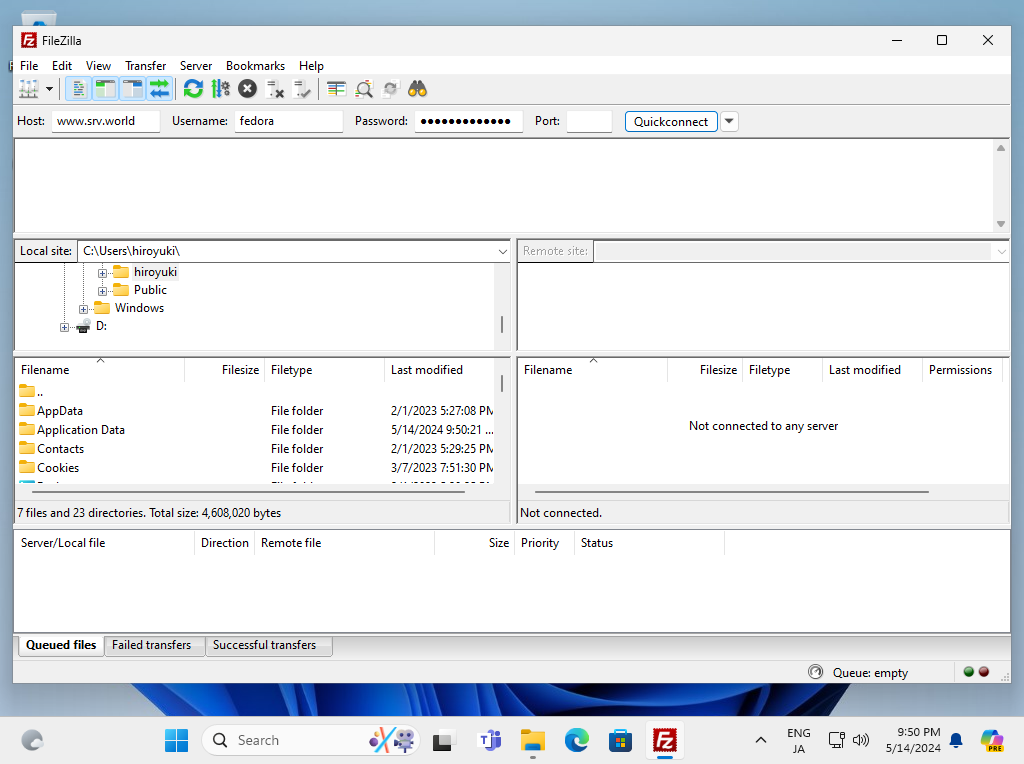
Step [3]After successfully passed authentication, it's possible to transfer files on it.
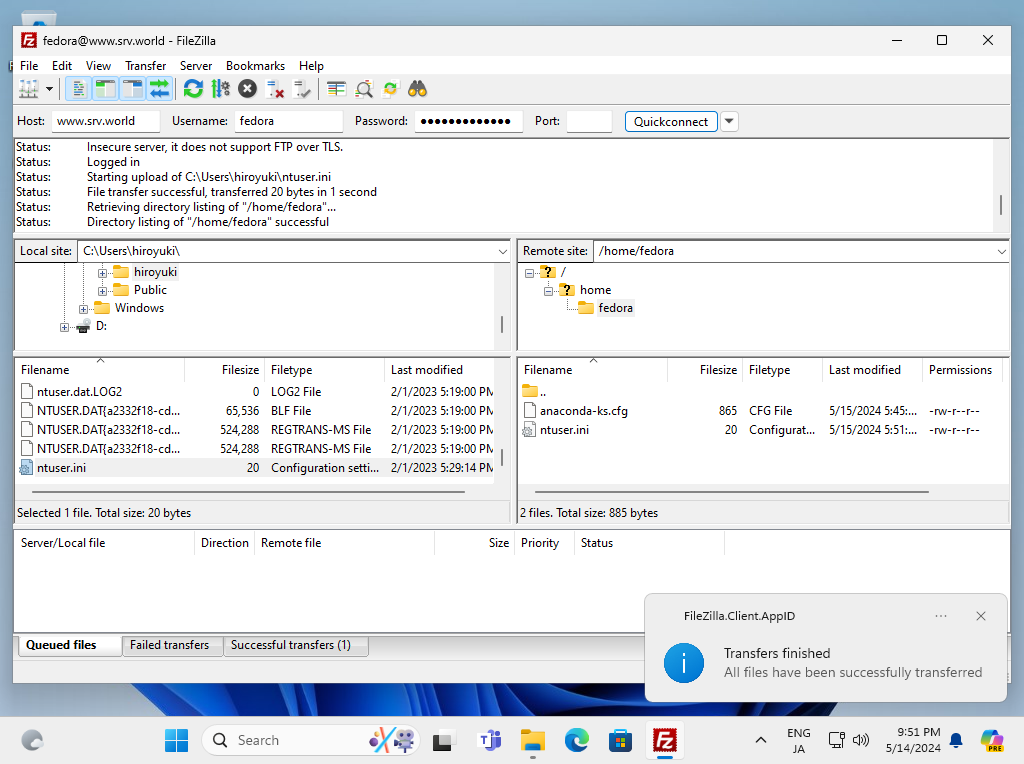
FTP : Vsftpd Over SSL/TLS
Enable SSL/TLS for Vsftpd to use secure FTP connections.
Step [1] Create self-signed certificates. But if you use valid certificates like from Let's Encrypt or others, you don't need to create this one.
[root@bizantum ~]# cd /etc/pki/tls/certs
[root@bizantum certs]# openssl req -x509 -nodes -newkey rsa:3072 -keyout vsftpd.pem -out vsftpd.pem -days 3650
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:JP # country code
State or Province Name (full name) []:Hiroshima # State
Locality Name (eg, city) [Default City]:Hiroshima # city
Organization Name (eg, company) [Default Company Ltd]:GTS # company
Organizational Unit Name (eg, section) []:Server World # department
Common Name (eg, your name or your server's hostname) []:www.bizantum.lab # server's FQDN
Email Address []:root@bizantum.lab # admin's email
[root@bizantum certs]# chmod 600 vsftpd.pem
Step [2]Configure Vsftpd. Configure basic settings before it, refer to here.
[root@bizantum ~]# vi /etc/vsftpd/vsftpd.conf
# add to last line (enable SSL/TLS)
rsa_cert_file=/etc/pki/tls/certs/vsftpd.pem
ssl_enable=YES
force_local_data_ssl=YES
force_local_logins_ssl=YES
[root@bizantum ~]# systemctl restart vsftpd
Step [3]If Firewalld is running, allow FTP related ports.
[root@bizantum ~]# vi /etc/vsftpd/vsftpd.conf
# add to the end : fix PASV ports
pasv_enable=YES
pasv_min_port=21000
pasv_max_port=21100
[root@bizantum ~]# systemctl restart vsftpd
[root@bizantum ~]# firewall-cmd --add-service=ftp
success
[root@bizantum ~]# firewall-cmd --add-port=21000-21100/tcp
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
FTP Client : Fedora
Configure FTP Client to use FTPS connection.
Step [4]Install FTP Client and configure like follows.
[redhat@dlp ~]$ vi ~/.lftprc
# create new
set ftp:ssl-auth TLS
set ftp:ssl-force true
set ftp:ssl-protect-list yes
set ftp:ssl-protect-data yes
set ftp:ssl-protect-fxp yes
set ssl:verify-certificate no
[redhat@dlp ~]$ lftp -u fedora www.bizantum.lab
Password:
lftp fedora@www.bizantum.lab:~>
FTP Client : Windows
Step [5]For example of FileZilla on Windows, Open [File] - [Site Manager].
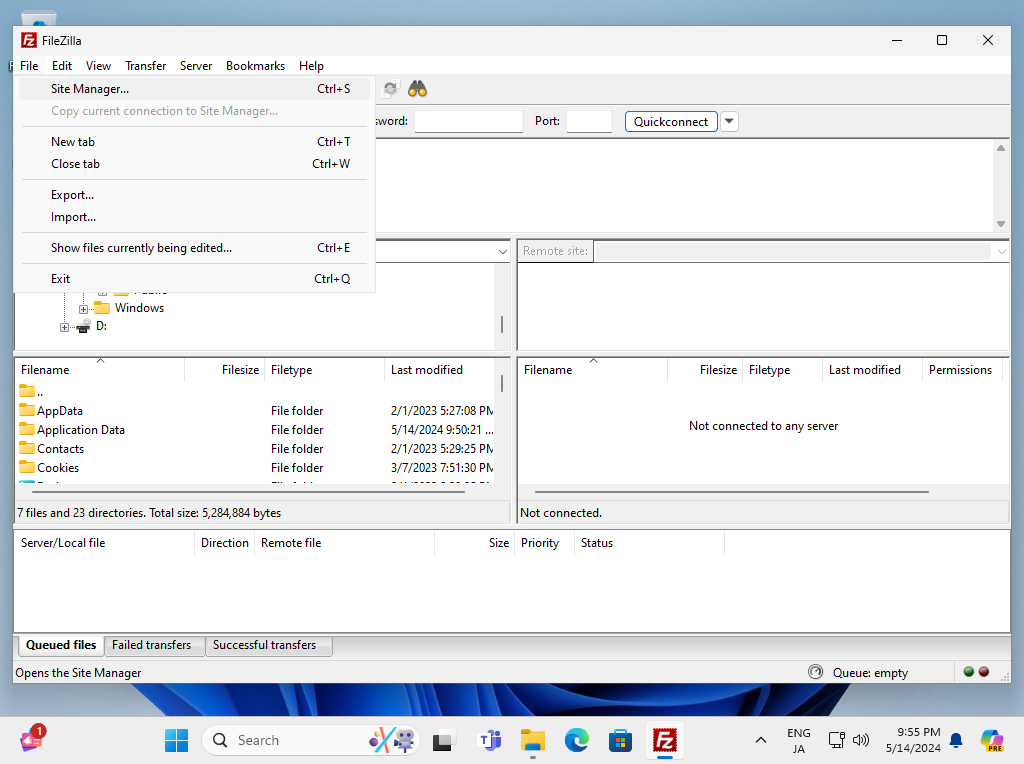
Step [6]Input user info like follows, for encryption field, select [explicit FTP over TLS].
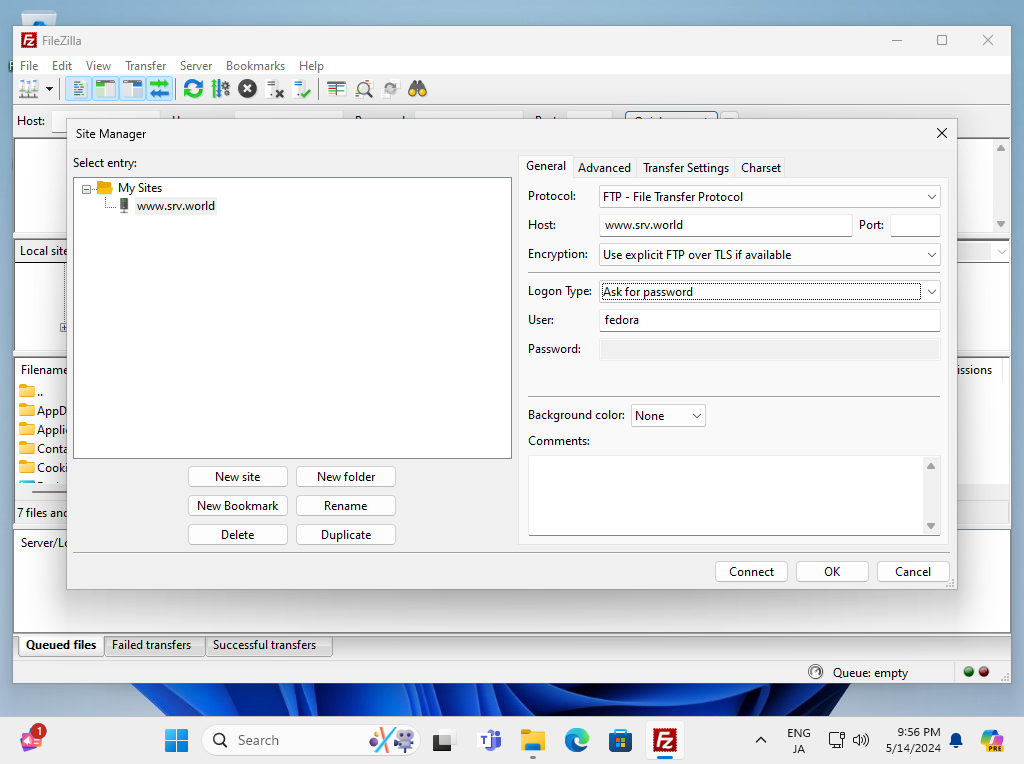
Step [7]User's Password is required. Input it.
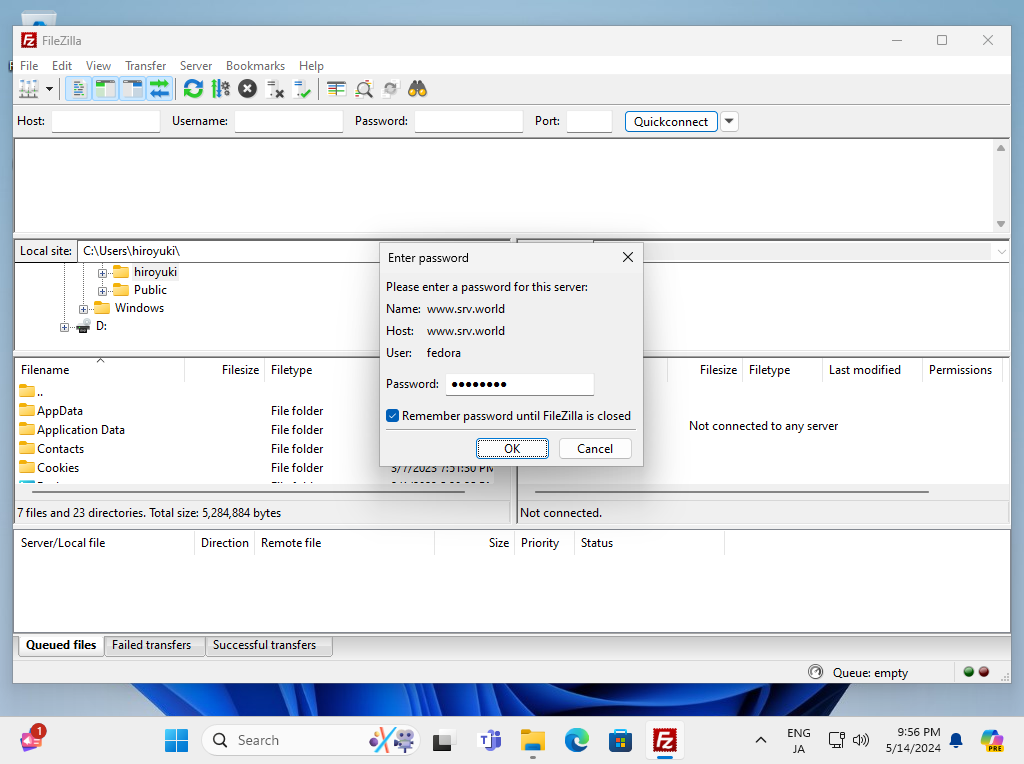
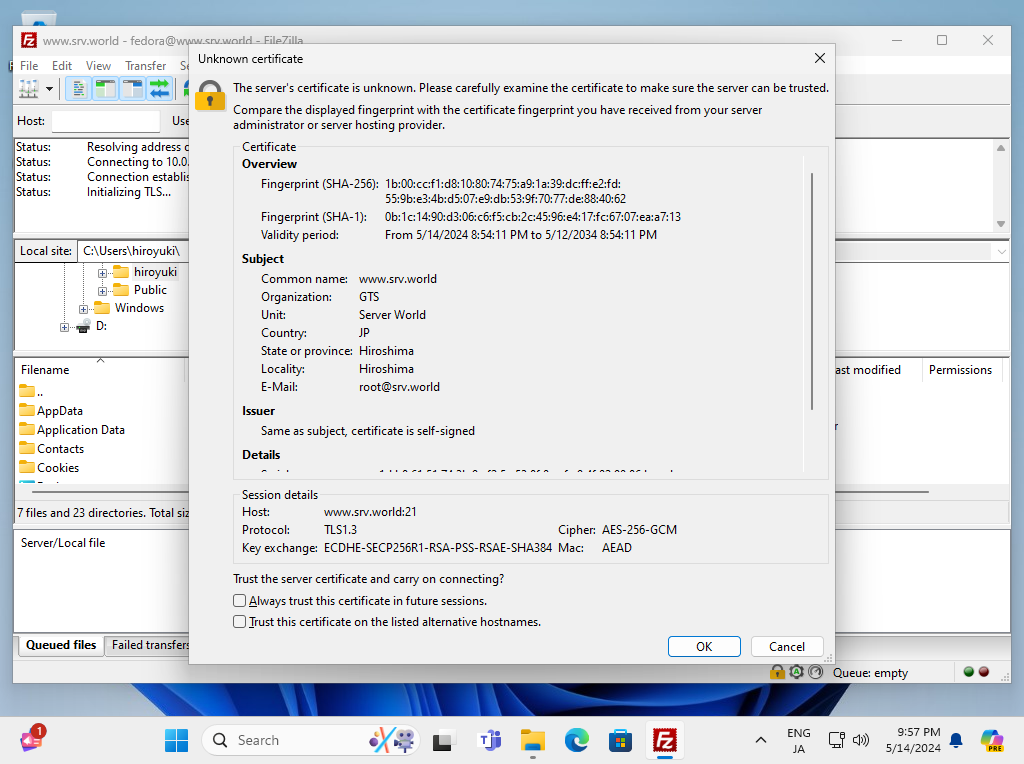
Step [8]If you set self-signed certificate, following warning is shown, it's no problem. Go next.
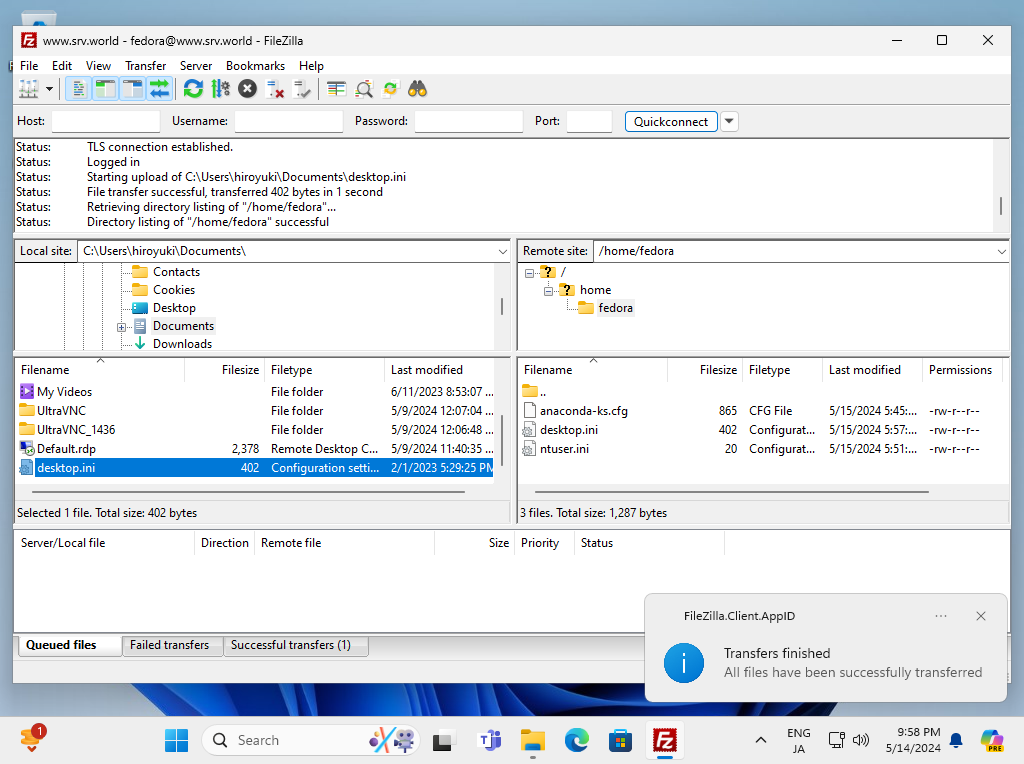
Step [9]If settings are OK, it's possible to connect to FTP server with FTPS like follows.
FTP : ProFTPD Over SSL/TLS
Enable SSL/TLS for ProFTPD to use secure FTP connections.
Step [1] Create self-signed certificates. But if you use valid certificates like from Let's Encrypt or others, you don't need to create this one.
[root@bizantum ~]# cd /etc/pki/tls/certs
[root@bizantum certs]# openssl req -x509 -nodes -newkey rsa:3072 -keyout proftpd.pem -out proftpd.pem -days 3650
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:JP # country code
State or Province Name (full name) []:Hiroshima # State
Locality Name (eg, city) [Default City]:Hiroshima # city
Organization Name (eg, company) [Default Company Ltd]:GTS # company
Organizational Unit Name (eg, section) []:Server World # department
Common Name (eg, your name or your server's hostname) []:www.bizantum.lab # server's FQDN
Email Address []:root@bizantum.lab # admin's email
[root@bizantum certs]# chmod 600 proftpd.pem
Step [2]Configure ProFTPD. Configure basic settings before it, refer to here.
[root@bizantum ~]# vi /etc/sysconfig/proftpd
# add
PROFTPD_OPTIONS="-DTLS"
[root@bizantum ~]# vi /etc/proftpd/mod_tls.conf
# change to your own certificate
<IfModule mod_tls.c>
TLSEngine on
TLSRequired off
#TLSCertificateChainFile /etc/pki/tls/certs/proftpd-chain.pem
TLSRSACertificateFile /etc/pki/tls/certs/proftpd.pem
TLSRSACertificateKeyFile /etc/pki/tls/certs/proftpd.pem
TLSCipherSuite PROFILE=SYSTEM
# Relax the requirement that the SSL session be re-used for data transfers
TLSOptions NoSessionReuseRequired
TLSLog /var/log/proftpd/tls.log
<IfModule mod_tls_shmcache.c>
TLSSessionCache shm:/file=/run/proftpd/sesscache
</IfModule>
</IfModule>
[root@bizantum ~]# systemctl restart proftpd
Step [3]If Firewalld is running, allow FTP related ports.
[root@bizantum ~]# vi /etc/proftpd.conf
# add to last line : fix PASV ports
PassivePorts 21000 21100
[root@bizantum ~]# systemctl restart proftpd
[root@bizantum ~]# firewall-cmd --add-service=ftp
success
[root@bizantum ~]# firewall-cmd --add-port=21000-21100/tcp
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
FTP Client : Fedora
Configure FTP Client to use FTPS connection.
Step [4]Install FTP Client and configure like follows.
[redhat@dlp ~]$ vi ~/.lftprc
# create new
set ftp:ssl-auth TLS
set ftp:ssl-force true
set ftp:ssl-protect-list yes
set ftp:ssl-protect-data yes
set ftp:ssl-protect-fxp yes
set ssl:verify-certificate no
[redhat@dlp ~]$ lftp -u fedora www.bizantum.lab
Password:
lftp fedora@www.bizantum.lab:~>
FTP Client : Windows
Step [5]For example of FileZilla on Windows, Open [File] - [Site Manager].

Step [6]Input user info like follows, for encryption field, select [explicit FTP over TLS].

Step [7]User's Password is required. Input it.

Step [8]If you set self-signed certificate, following warning is shown, it's no problem. Go next.

Step [9]If settings are OK, it's possible to connect to FTP server with FTPS like follows.

- Get link
- X
- Other Apps










Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.