
Introduction
This guide covers the installation and configuration of Samba on Fedora 40 using the 5W1H approach. We will explore the What, Who, Where, When, Why, How, Consequences, and Conclusion of setting up Samba.
Overview
What
Samba is a free software re-implementation of the SMB/CIFS networking protocol. It facilitates file and printer sharing between Unix/Linux and Windows systems.
Who
This guide is intended for system administrators and IT professionals who need to set up a network file sharing service on Fedora 40.
Where
The setup process can be carried out on any server running Fedora 40, whether it's a physical machine, virtual machine, or cloud instance.
When
Setting up Samba should be done during a planned maintenance window to avoid potential disruptions to existing services.
Why
Implementing Samba on your server offers several advantages:
| Pros | Cons |
|---|---|
| Enables file sharing between Linux/Unix and Windows systems | Complex initial configuration |
| Supports printer sharing | Potential security risks if not properly configured |
| Robust and reliable | Requires ongoing management and updates |
How
Follow these steps to set up Samba on Fedora 40:
| Step 1 | Update your system: sudo dnf update -y |
| Step 2 | Install the Samba package: sudo dnf install -y samba |
| Step 3 | Start and enable the Samba service: sudo systemctl start smb sudo systemctl enable smb sudo systemctl start nmb sudo systemctl enable nmb |
| Step 4 | Configure Samba by editing the configuration file:(``sudo nano /etc/samba/smb.conf``) Adjust settings as needed, such as defining shared directories and setting permissions. |
| Step 5 | Allow Samba traffic through the firewall: sudo firewall-cmd --permanent --add-service=samba sudo firewall-cmd --reload |
| Step 6 | Restart the Samba service to apply the changes: sudo systemctl restart smb sudo systemctl restart nmb |
Consequences
Setting up Samba on Fedora 40 can have the following consequences:
| Positive |
|
| Negative |
|
Conclusion
Setting up Samba on Fedora 40 is essential for achieving seamless file and printer sharing across different operating systems. While the initial setup can be complex and demands regular maintenance, the benefits of a reliable, flexible, and robust network sharing service make Samba a valuable addition to any IT infrastructure. By following this guide, system administrators can ensure their file sharing services are efficient and secure.
Fully Accessed Shared Folder
Install Samba to Configure File Server. For example, Create a fully accessed shared Folder which anybody can read and write, and also authentication is not required.
Step [1]Install and Configure Samba.
[root@smb ~]# dnf -y install samba
[root@smb ~]# mkdir /home/share
[root@smb ~]# chmod 777 /home/share
[root@smb ~]# vi /etc/samba/smb.conf
[global]
# line 11 : add (set charset)
unix charset = UTF-8
workgroup = SAMBA
security = user
# add (IP addresses you allow to access)
hosts allow = 127. 10.0.0.
# add (no authentication)
map to guest = Bad User
.....
.....
# add to the end
# any Share name you like
[Share]
# specify shared directory
path = /home/share
# allow writing
writable = yes
# allow guest user (nobody)
guest ok = yes
# looks all as guest user
guest only = yes
# set permission [777] when file created
force create mode = 777
# set permission [777] when folder created
force directory mode = 777
[root@smb ~]# systemctl enable --now smb
Step [2]If SELinux is enabled and also use [/home] like this example, Change SELinux policy.
[root@smb ~]# setsebool -P samba_enable_home_dirs on
[root@smb ~]# restorecon -R /home/share
Step [3]If Firewalld is running, allow Samba service.
[root@smb ~]# firewall-cmd --add-service=samba
success
[root@smb ~]# firewall-cmd --runtime-to-permanent
success
Limited Shared Folder
Install Samba to Configure File Server. For example, Create a shared Folder that users in [smbgroup01] group can only access to shared folder [/home/share01] and also they are required user authentication.
Step [1]Install and Configure Samba.
[root@smb ~]# dnf -y install samba
[root@smb ~]# groupadd smbgroup01
[root@smb ~]# mkdir /home/share01
[root@smb ~]# chgrp smbgroup01 /home/share01
[root@smb ~]# chmod 770 /home/share01
[root@smb ~]# vi /etc/samba/smb.conf
[global]
# line 11 : add (set charset)
unix charset = UTF-8
workgroup = SAMBA
security = user
# add (IP addresses you allow to access)
hosts allow = 127. 10.0.0.
.....
.....
# add to the end
# any Share name you like
[Share01]
# specify shared directory
path = /home/share01
# allow writing
writable = yes
# not allow guest user (nobody)
guest ok = no
# allow only [smbgroup01] group
valid users = @smbgroup01
# set group for new files/directories to [smbgroup01]
force group = smbgroup01
# set permission [770] when file created
force create mode = 770
# set permission [770] when folder created
force directory mode = 770
# inherit permissions from parent folder
inherit permissions = yes
[root@smb ~]# systemctl enable --now smb
# add Samba user
[root@smb ~]# useradd fedora
[root@smb ~]# smbpasswd -a fedora
New SMB password: # set password
Retype new SMB password:
Added user fedora.
[root@smb ~]# usermod -aG smbgroup01 fedora
Step [2]If SELinux is enabled and also use [/home] like this example, Change SELinux policy.
[root@smb ~]# setsebool -P samba_enable_home_dirs on
[root@smb ~]# restorecon -R /home/share01
Step [3]If Firewalld is running, allow Samba service.
[root@smb ~]# firewall-cmd --add-service=samba
success
[root@smb ~]# firewall-cmd --runtime-to-permanent
success
Access to Share from Clients (Fedora)
Access to Share from Client Hosts.
Step [1]On Fedora clients with CUI, access like follows.
[root@node01 ~]# dnf -y install samba-client cifs-utils
# with [smbclient] command access
# smbclient (share name) -U (user name)
[root@node01 ~]# smbclient '\\smb.bizantum.lab\Share01' -U fedora
Password for [SAMBA\fedora]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed May 15 12:23:27 2024
.. D 0 Wed May 15 12:23:27 2024
New folder D 0 Wed May 15 12:23:23 2024
New Text Document.txt A 701707 Wed May 15 12:27:15 2024
15663104 blocks of size 1024. 13678320 blocks available
# download a file
smb: \> mget "New Text Document.txt"
Get file New Text Document.txt? y
getting file \New Text Document.txt of size 701707 as New Text Document.txt (76139.3 KiloBytes/sec) (average 76140.1 KiloBytes/sec)
smb: \> !ls
anaconda-ks.cfg 'New Text Document.txt'
smb: \> exit
# with [mount] command access
# [vers=(SMB protocol version)]
[root@node01 ~]# mount -t cifs -o vers=3.0,username=fedora '\\smb.bizantum.lab\Share01' /mnt
Password for fedora@\smb.bizantum.lab\Share01: ******** # user's SMB password
[root@node01 ~]# df -hT
Filesystem Type Size Used Avail Use% Mounted on
/dev/mapper/fedora-root xfs 15G 1.9G 14G 13% /
devtmpfs devtmpfs 4.0M 0 4.0M 0% /dev
tmpfs tmpfs 2.0G 0 2.0G 0% /dev/shm
tmpfs tmpfs 782M 1.1M 781M 1% /run
tmpfs tmpfs 2.0G 0 2.0G 0% /tmp
/dev/vda2 xfs 960M 344M 617M 36% /boot
tmpfs tmpfs 391M 4.0K 391M 1% /run/user/0
//smb.bizantum.lab/Share01 cifs 15G 1.9G 14G 13% /mnt
# if SMB share does not require authentication, specify [none] for username
[root@node01 ~]# mount -t cifs -o vers=3,username=none,password=none '\\smb.bizantum.lab\Share' /mnt
Samba : Access to Share from Clients (Windows)
It's the way to access to the shared folder. This example is on Windows 11.
Step [2]Open File Explorer and right-click the [Network] on the left pane, then select [Show more options] - [Map Network Drive].
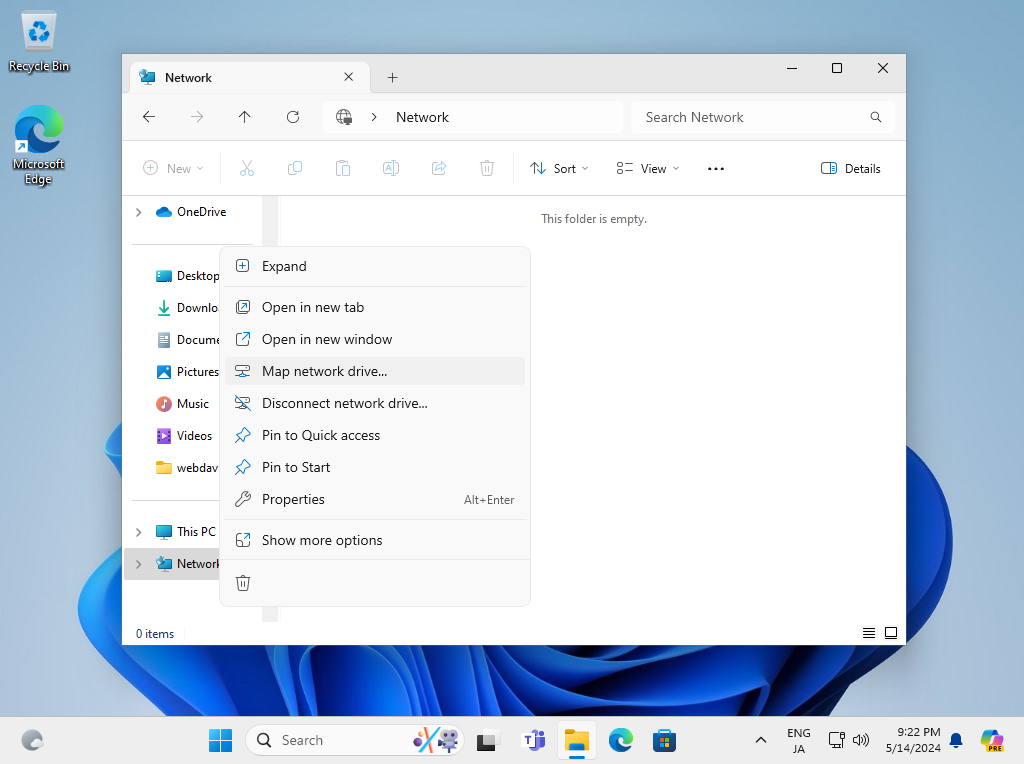
Step [3]Specify the shared folder Path on [Folder] section and Click the [Finish] button.
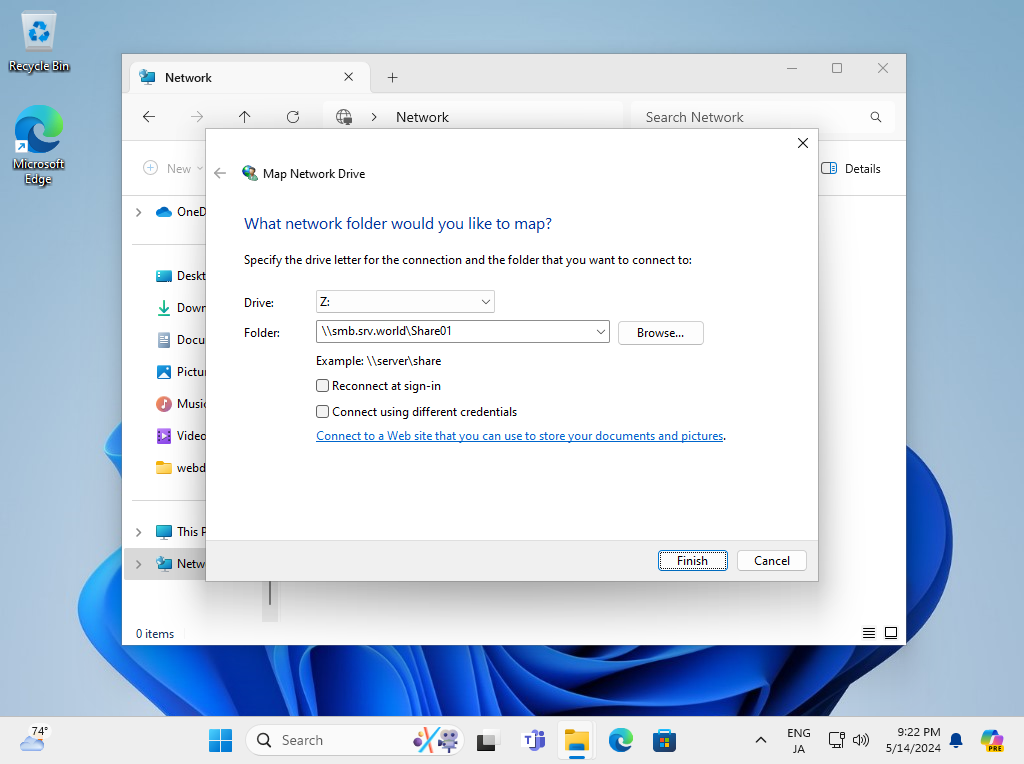
Step [4]Authentication is required if you set common shared folder with authentication, Input Samba username and password you added.
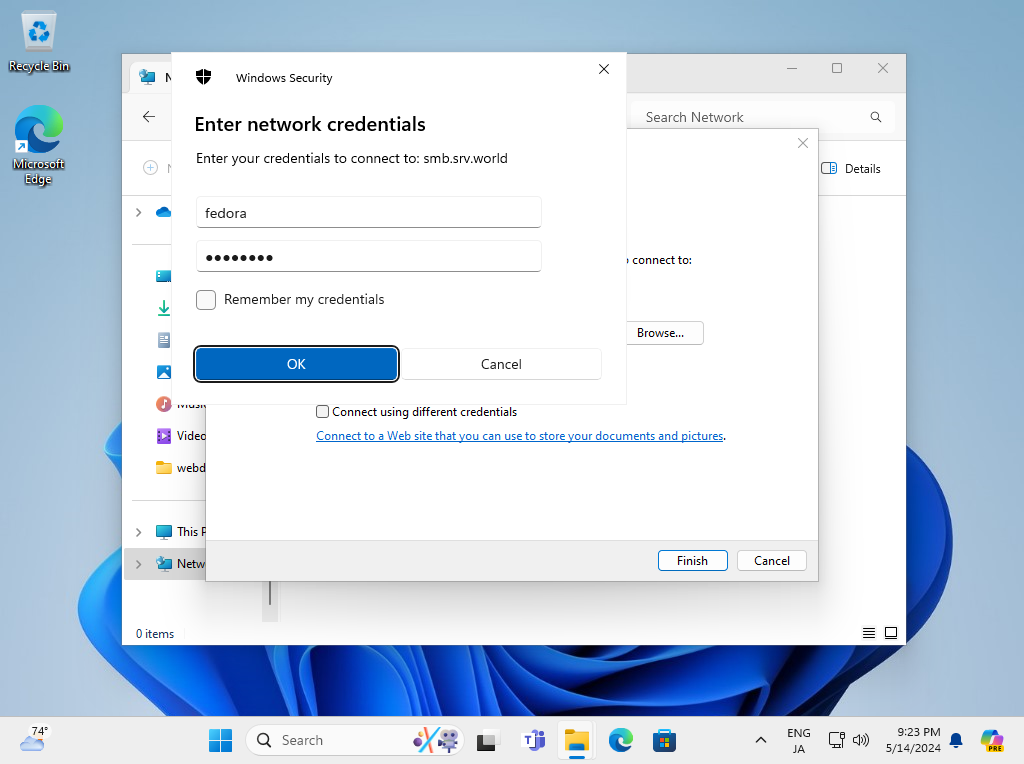
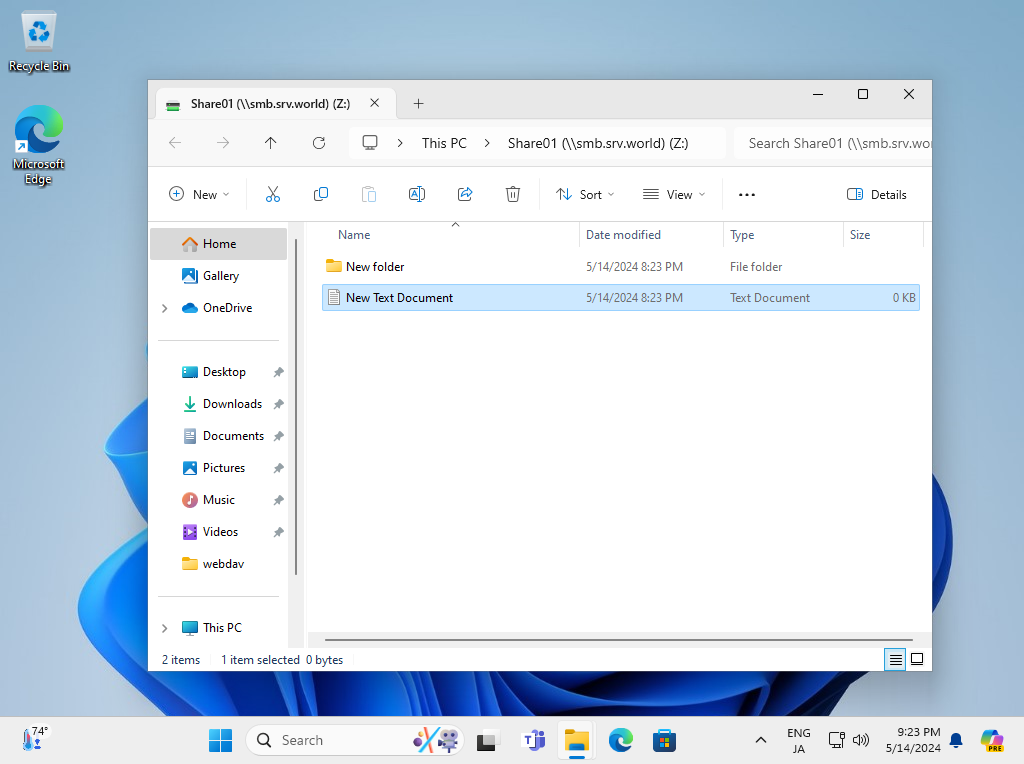
Step [5]After successfully passed authentication, it's possible to access to shared folder.
Samba Winbind
oin in Windows Active Directory Domain with Samba Winbind. This tutorial needs Windows Active Directory Domain Service in your Local Network. This example is based on the environment like follows. Domain Server : Windows Server 2022 Domain Name : bizantum.lab Hostname : fd3s.bizantum.lab NetBIOS Name : FD3S01 Realm : bizantum.lab
Step [1]Install Winbind.
[root@smb ~]# dnf -y install samba-winbind samba-winbind-clients oddjob-mkhomedir
Step [2]Configure Samba.
[root@smb ~]# vi /etc/krb5.conf
# line 20 : uncomment and specify Realm
default_realm = bizantum.lab
# line 24-27 : add to specify Realm and Hostname of AD
[realms]
bizantum.lab = {
kdc = fd3s.bizantum.lab
admin_server = fd3s.bizantum.lab
}
[root@smb ~]# mv /etc/samba/smb.conf /etc/samba/smb.conf.org
[root@smb ~]# vi /etc/samba/smb.conf
# create new
# replace [realm] and [workgroup] for your environment
[global]
kerberos method = secrets and keytab
realm = bizantum.lab
workgroup = FD3S01
security = ads
template shell = /bin/bash
winbind enum groups = Yes
winbind enum users = Yes
winbind separator = +
idmap config * : rangesize = 1000000
idmap config * : range = 1000000-19999999
idmap config * : backend = autorid
# switch to Winbind
[root@smb ~]# authselect select winbind --force
Backup stored at /var/lib/authselect/backups/2022-11-24-08-28-17.z84x3Z
Profile "winbind" was selected.
Make sure that winbind service is configured and enabled. See winbind documentation for more information.
# set if you need (create home directory when initial login)
[root@smb ~]# authselect enable-feature with-mkhomedir
[root@smb ~]# systemctl enable --now oddjobd
Step [3]Join in Active Directory Domain.
# change DNS setting to refer to AD
[root@smb ~]# nmcli connection modify enp1s0 ipv4.dns 10.0.0.100
[root@smb ~]# nmcli connection up enp1s0
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2)
# join in domain [-U (AD user)]
[root@smb ~]# net ads join -U Administrator
Password for [FD3S01\Administrator]:
Using short domain name -- FD3S01
Joined 'SMB' to dns domain 'bizantum.lab'
No DNS domain configured for smb. Unable to perform DNS Update.
DNS update failed: NT_STATUS_INVALID_PARAMETER
[root@smb ~]# systemctl enable --now winbind
# show domain info
[root@smb ~]# net ads info
LDAP server: 10.0.0.100
LDAP server name: fd3s.bizantum.lab
Realm: bizantum.lab
Bind Path: dc=SRV,dc=WORLD
LDAP port: 389
Server time: Wed, 15 May 2024 12:33:33 JST
KDC server: 10.0.0.100
Server time offset: 1
Last machine account password change: Wed, 15 May 2024 12:33:21 JST
# show AD user list
[root@smb ~]# wbinfo -u
FD3S01+administrator
FD3S01+guest
FD3S01+krbtgt
FD3S01+bizantum
FD3S01+ldapuser
FD3S01+aduser01
# verify possible to login with AD user
[root@smb ~]# exit
logout
Fedora Linux 40 (Server Edition)
Kernel 6.8.7-300.fc40.x86_64 on an x86_64 (ttyS0)
Activate the web console with: systemctl enable --now cockpit.socket
smb login: FD3S01+bizantum
Password:
[FD3S01+bizantum@smb ~]$ id
uid=2001103(FD3S01+bizantum) gid=2000513(FD3S01+domain users) groups=2000513(FD3S01+domain users),2000512(FD3S01+domain admins),2000572(FD3S01+denied rodc password replication group),2001103(FD3S01+bizantum),2001104(FD3S01+esx admins) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.