
Introduction
Internet Information Services (IIS) is a flexible, secure, and manageable Web server for hosting anything on the Web. From media streaming to web applications, IIS's scalable and open architecture is ready to handle the most demanding tasks.
Overview
This document provides a comprehensive overview of IIS, covering the What, Who, Where, When, Why, How, Consequences, and Conclusion.
What
Internet Information Services (IIS) is a web server software created by Microsoft for use with the Windows NT family. It supports HTTP, HTTPS, FTP, FTPS, SMTP, and NNTP, allowing it to serve web pages, host web applications, and facilitate file transfers.
Who
IIS is designed for IT professionals, web developers, and system administrators who need to host and manage websites and web applications. It is used by businesses of all sizes, educational institutions, and government organizations.
Where
IIS can be deployed on any machine running Windows Server operating systems and also on Windows client operating systems for development and testing purposes. It is commonly used in enterprise environments, hosting providers, and development workstations.
When
IIS was first introduced as part of Windows NT 3.51 in 1995. It has been included in every release of Windows Server since then, with numerous updates and new features in each version. The latest versions are IIS 10.0, which comes with Windows Server 2016 and Windows Server 2019.
Why
Understanding the pros and cons of IIS can help determine its suitability for various use cases.
| Pros | Cons |
|---|---|
| Integrated with Windows Server | Platform-dependent (Windows only) |
| Supports multiple protocols | Licensing costs |
| Strong security features | Complex configuration |
How
Here is a basic workflow to set up and manage IIS:
| Step 1 | Install IIS via Server Manager or PowerShell |
| Step 2 | Configure websites and applications using IIS Manager |
| Step 3 | Manage and monitor server performance through IIS Manager and performance counters |
Consequences
The implementation of IIS brings various positive and negative consequences:
| Positive |
|
| Negative |
|
Conclusion
IIS is a powerful and versatile web server solution that offers numerous benefits, such as seamless integration with Windows Server, strong security features, and extensive support. However, it also has some limitations, including licensing costs and platform dependency. Overall, IIS is an excellent choice for organizations looking for a reliable and secure web server for their applications and services.
Install and Configure
Install IIS (Internet Information Services) and Configure Web Server.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Install IIS.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# install IIS with admin tools
PS C:\Users\Administrator> Install-WindowsFeature Web-Server -IncludeManagementTools
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {Common HTTP Features, Default Document, D...
# verify running to access to default web site
PS C:\Users\Administrator> Invoke-WebRequest http://localhost
StatusCode : 200
StatusDescription : OK
Content :
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" cont...
RawContent : HTTP/1.1 200 OK
Accept-Ranges: bytes
Content-Length: 703
Content-Type: text/html
Date: Wed, 28 Aug 2019 02:02:51 GMT
ETag: "a40a0f9435dd51:0"
Last-Modified: Wed, 28 Aug 2019 01:57:40 GMT
Server...
Forms : {}
Headers : {[Accept-Ranges, bytes], [Content-Length, 703], [Content-Type, text/html], [Date, Wed, 28 Aug 2019
02:02:51 GMT]...}
href="http://go.microsoft.com/fwlink/?linkid=66138&clcid=0x409"><IMG alt=IIS
src="iisstart.png" width=960 height=600></A>; outerText=; tagName=A;
href=http://go.microsoft.com/fwlink/?linkid=66138&clcid=0x409}}
ParsedHtml : System.__ComObject
RawContentLength : 703
Using Graphical User Interface (GUI)
Step [2]Run Server Manager and Click [Add roles and features].
Step [3]Click [Next] button.
Step [4]Select [Role-based or feature-based installation].
Step [5]Select a Host which you'd like to add services.
Step [6]Check a box [Web Server (IIS)].
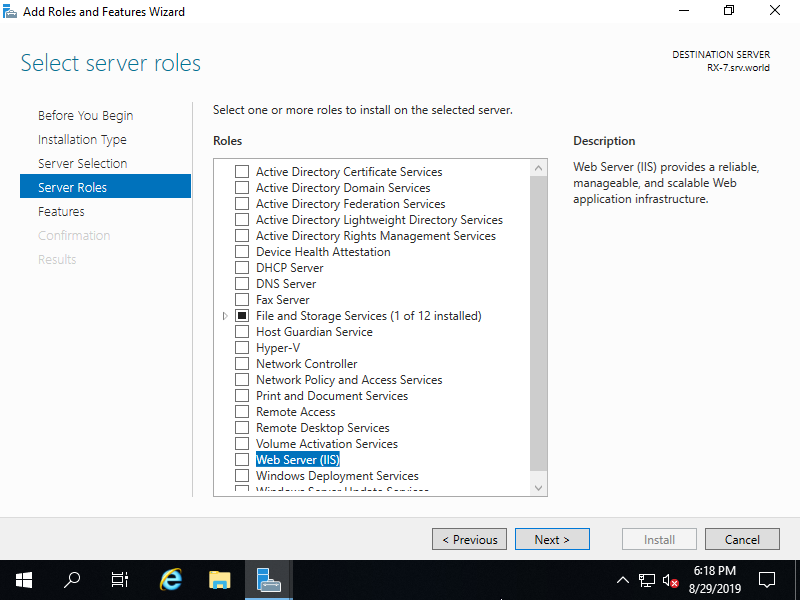
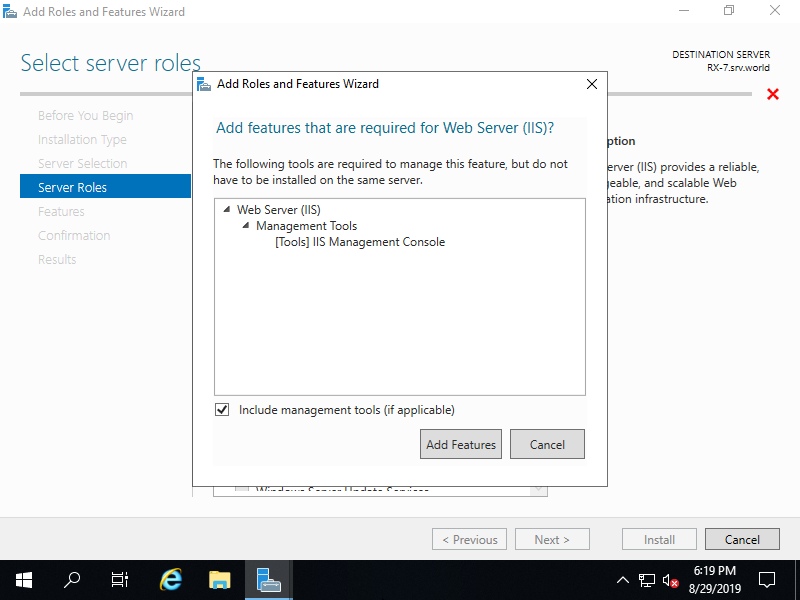
Step [7]Addtional features are required to add IIS Server. Click [Add Features] button and then Click [Next] button.
Step [8]Click [Next] button.
Step [9]Click [Next] button.
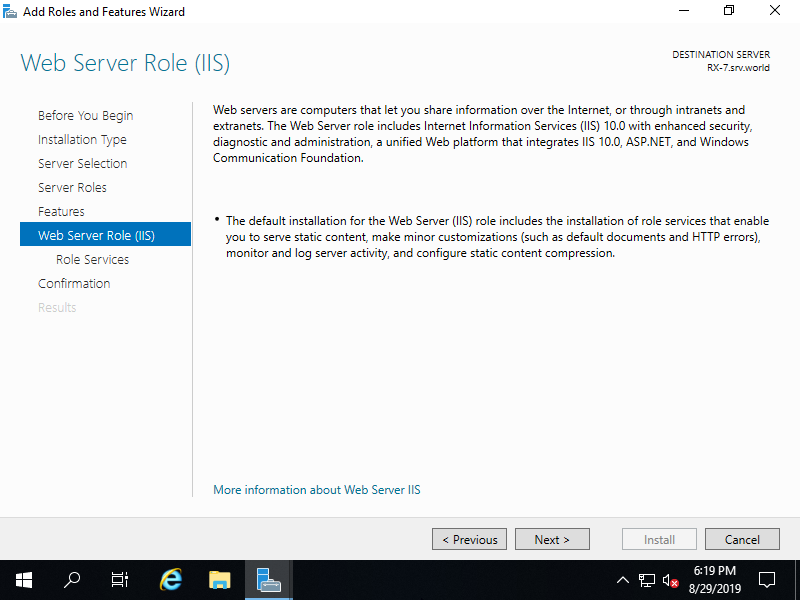
Step [10]This is the section to select Web Server features. Select them your'd like to add. On this example, keep default and proceed next. It's possible to add these features after installing IIS, of course.
Step [11]Click [Install] button.
Step [12]After finishing Installation, click [Close] button.
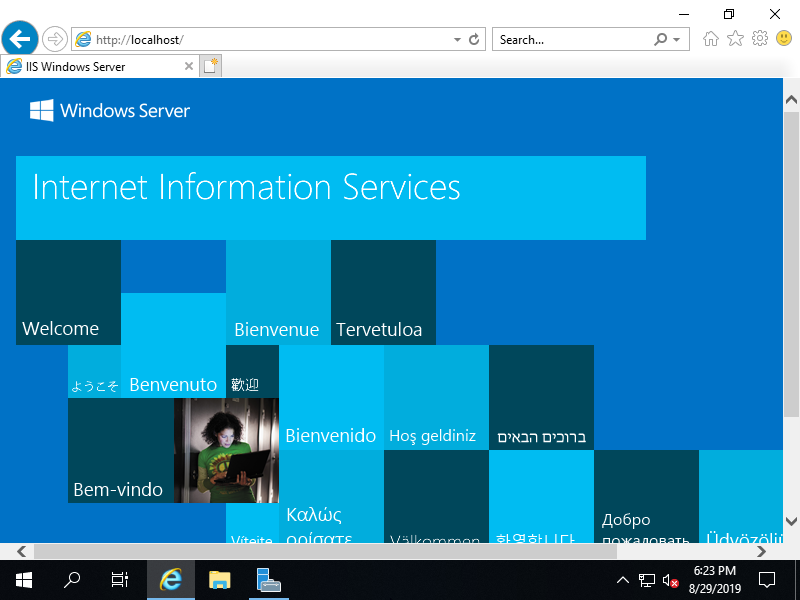
Step [13]Run Web browser and access to [localhost], then it's possible to verify IIS is running normally.
Use Default Web Site
After installing IIS, a Web Site setting [Default Web Site] is configured. If you use [Default Web Site], refer to follows.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# show Sites list : [Default Web Site] is only set
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
# [Physical Path] is the Document Root
PS C:\Users\Administrator> Get-ChildItem C:\inetpub\wwwroot
Directory: C:\inetpub\wwwroot
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/27/2019 6:57 PM 703 iisstart.htm
-a---- 8/27/2019 6:57 PM 99710 iisstart.png
# verify accesses : [iisstart.htm] responds
PS C:\Users\Administrator> Invoke-WebRequest localhost
StatusCode : 200
StatusDescription : OK
Content : Get-WebConfigurationProperty -Filter "//defaultDocument/files/add" -PSPath "IIS:\Sites\Default Web Site" -Name "value" | select value
Value
-----
Default.htm
Default.asp
index.htm
index.html
iisstart.htm
# create a test page under the Document Root and verify working
# [Write-Output] generates with UTF-16, so specify encoding explicitly with [Out-File]
PS C:\Users\Administrator> Write-Output "IIS Default Start Page" | Out-File C:\inetpub\wwwroot\Default.htm -Encoding Default
# verify accesses
# for [curl.exe], specify extension ⇒ if not specify extension, [curl] is an Alias from [Invoke-WebRequest]
PS C:\Users\Administrator> curl.exe localhost
IIS Default Start Page
Using Graphical User Interface (GUI)
Step [2]Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager].
Step [3]Open items on left pabe, [Default Web Site] is configured.
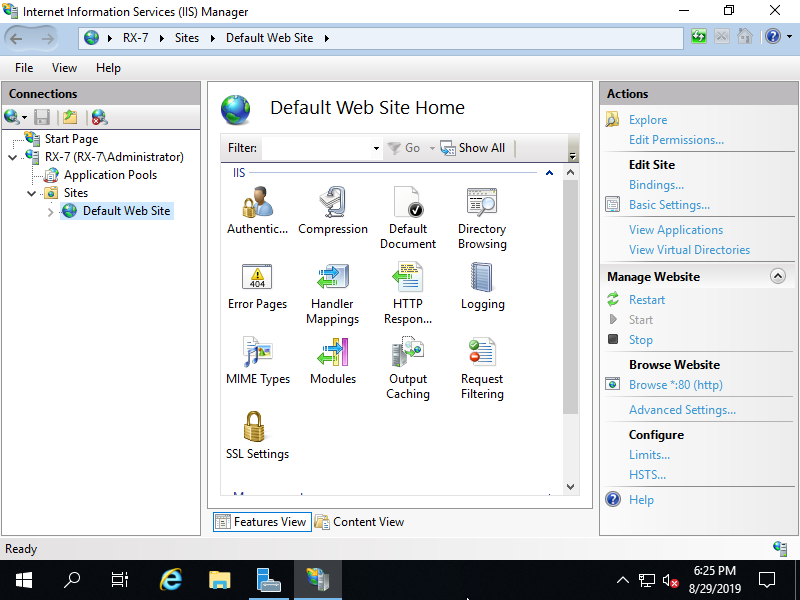
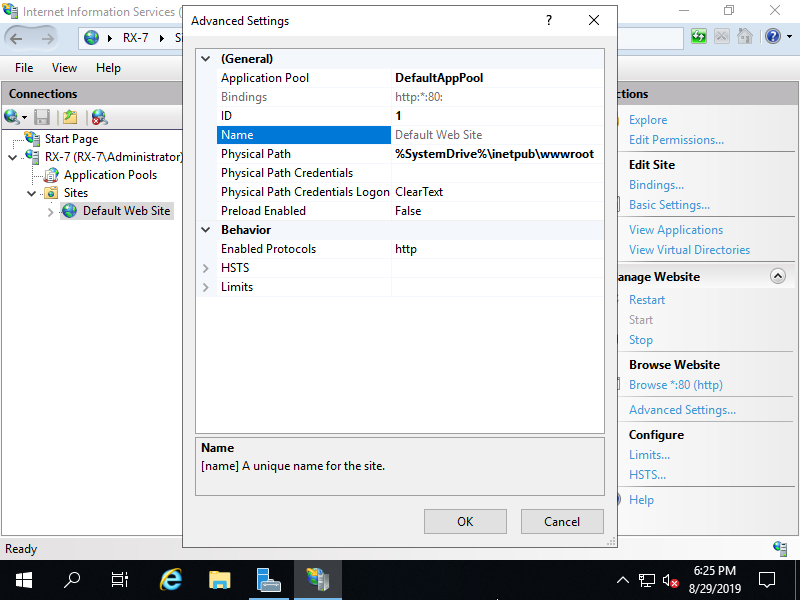
Step [4]Select [Default Web Site] and Click [Advanced Settings...], then it's possible to confirm settings like [Physical Path] (Document Root) and so on.
Step [5]Open [Default Document], then it's possible to confirm default documents.
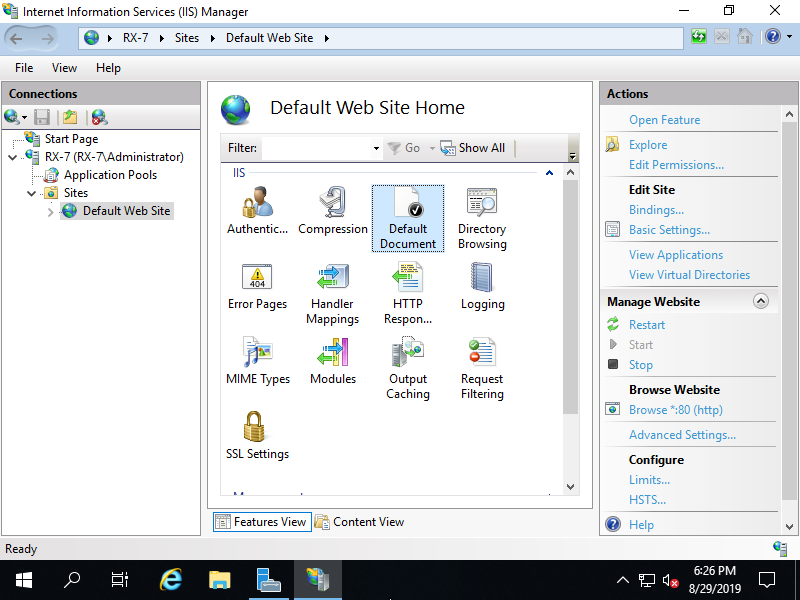
Step [6]You can see default documents.
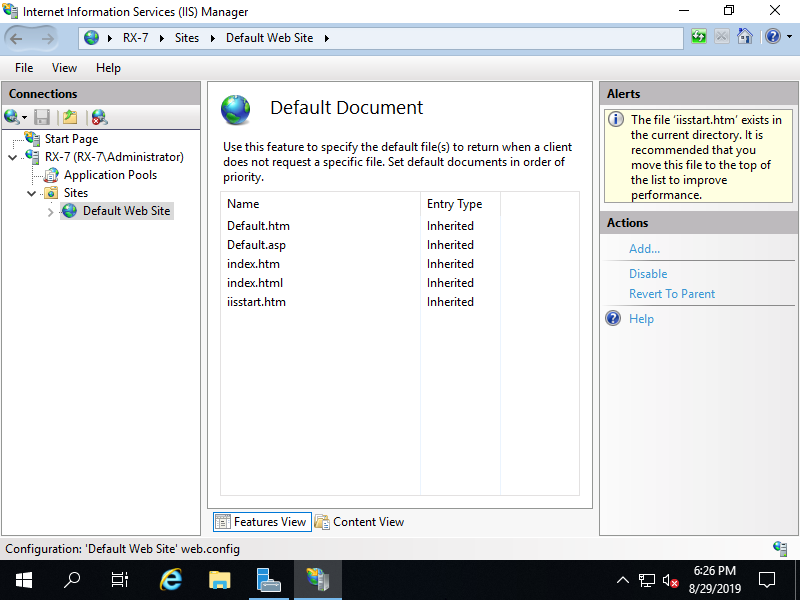
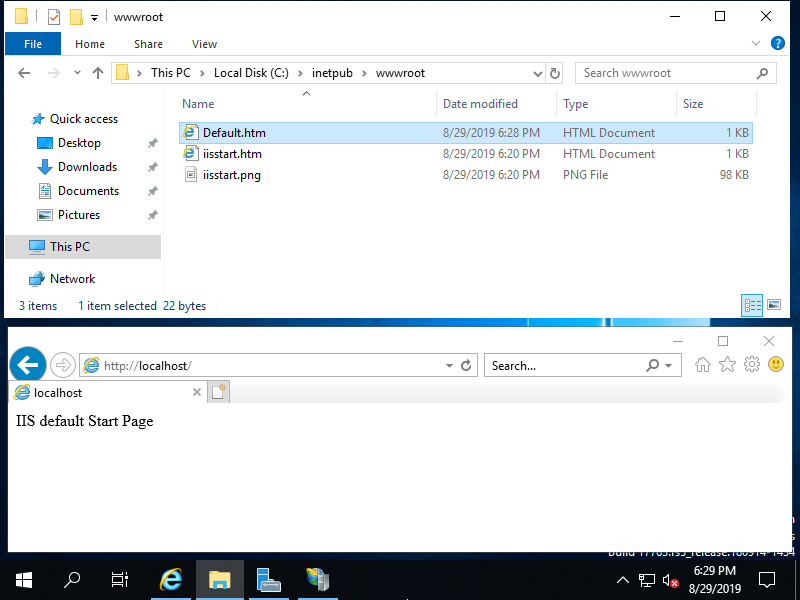
Step [7]Create a test page under the Physical Path (Document Root) and verify accesses with Web browser.
Configure Virtual Directory
Configure Virtual Directory. It's possible to set specific physical folder as a specific URL Path.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator> Get-Website -Name "Default Web Site"
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
# for example, set physical folder [C:\inetpub\wwwroot\virtual_dir], URL Path [/vDir] on [Default Web Site]
PS C:\Users\Administrator> mkdir C:\inetpub\wwwroot\virtual_dir
PS C:\Users\Administrator> New-WebVirtualDirectory -Site "Default Web Site" -Name "vDir" -PhysicalPath "C:\inetpub\wwwroot\virtual_dir"
Name PhysicalPath
---- ------------
vDir C:\inetpub\wwwroot\virtual_dir
PS C:\Users\Administrator> Get-WebVirtualDirectory -Site "Default Web Site"
Name Physical Path
---- -------------
vDir C:\inetpub\wwwroot\virtual_dir
# create a test page
PS C:\Users\Administrator> Write-Output "IIS Virtual Directory Test Page" | Out-File C:\inetpub\wwwroot\virtual_dir\index.html -Encoding Default
# verify accesses
PS C:\Users\Administrator> curl.exe localhost/vDir/
IIS Virtual Directory Test Page
Using Graphical User Interface (GUI)
Step [2]Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager], and then Click [View Virtual Directories] on the right pane.
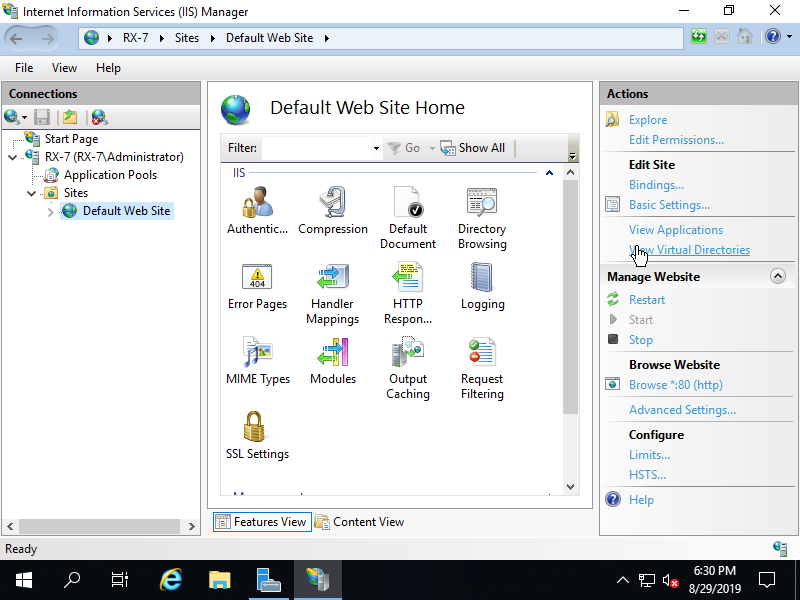
Step [3]Right Click on any place on the center pane and open [Add Virtual Directory].
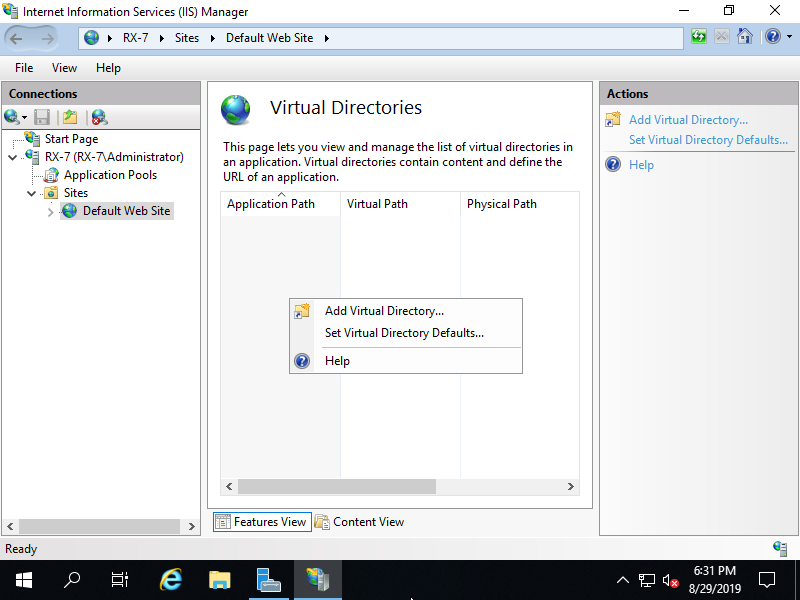
Step [4]Input URL Path for [Alias] field, for [Physical Path] field, input Physical folder Path.
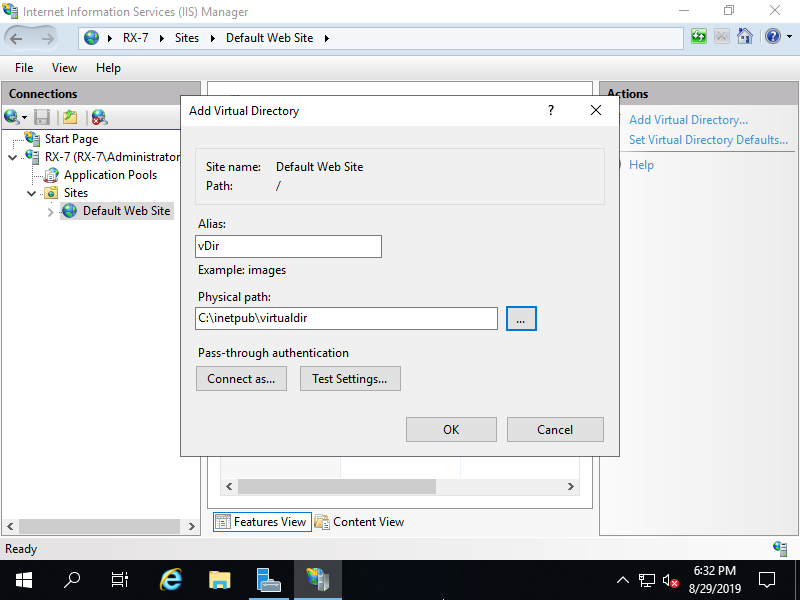
Step [5]After added normally, new virtual directory is listed.
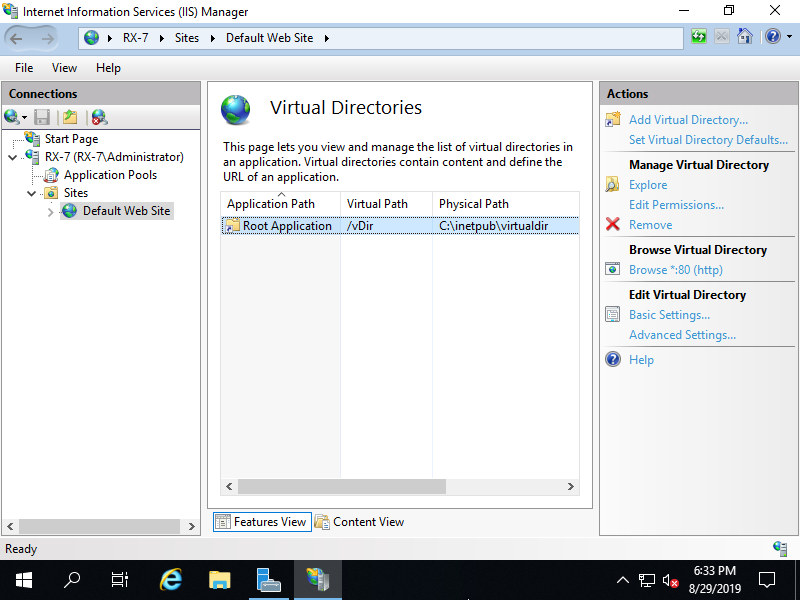
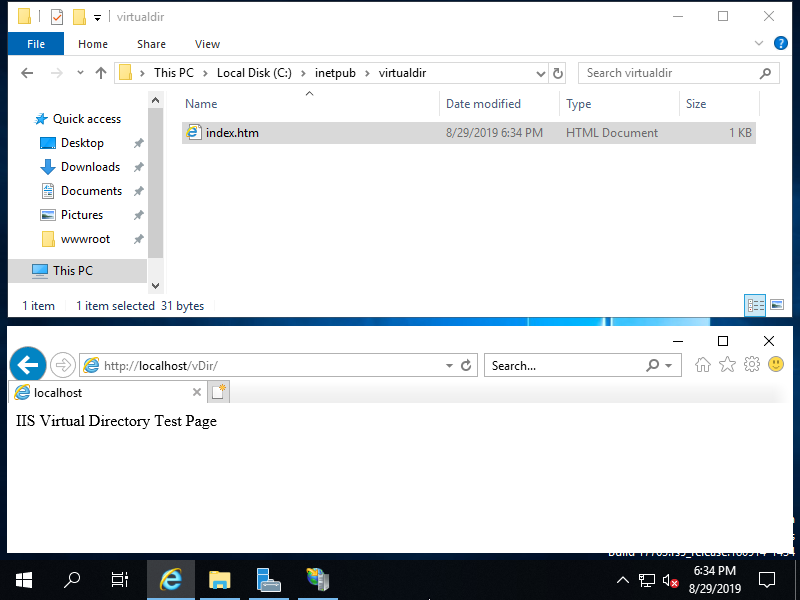
Step [6]Create a test page under the directory you set as Physical Path for virtual directory setting, and verify accesses.
Add Web Sites
Add new Web Sites on IIS. This setting is like the Virtual Hosting on Apache httpd that is often used on Unix/Linux.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# current Web Sites list
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
# for example, add [NewSite] Site
# physical path [C:\inetpub\newsite], hostname [RX-8.bizantum.lab]
PS C:\Users\Administrator> mkdir C:\inetpub\newsite
PS C:\Users\Administrator> New-WebSite -Name "NewSite" -Port 80 -HostHeader "RX-8.bizantum.lab" -PhysicalPath "C:\inetpub\newsite"
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
NewSite 2 Started C:\inetpub\newsite http *:80:RX-8.bizantum.lab
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
NewSite 2 Started C:\inetpub\newsite http *:80:RX-8.bizantum.lab
# create a test page
PS C:\Users\Administrator> Write-Output "IIS Virtual Host Test Page" | Out-File C:\inetpub\newsite\index.html -Encoding Default
# verisy accesses
# default site
PS C:\Users\Administrator> curl.exe localhost
IIS Default Start Page
# new site
PS C:\Users\Administrator> curl.exe RX-8.bizantum.lab
IIS Virtual Host Test Page
Using Graphical User Interface (GUI)
Step [2]Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager], and then Right Click [Sites] on the left pane and Select [Add Website].
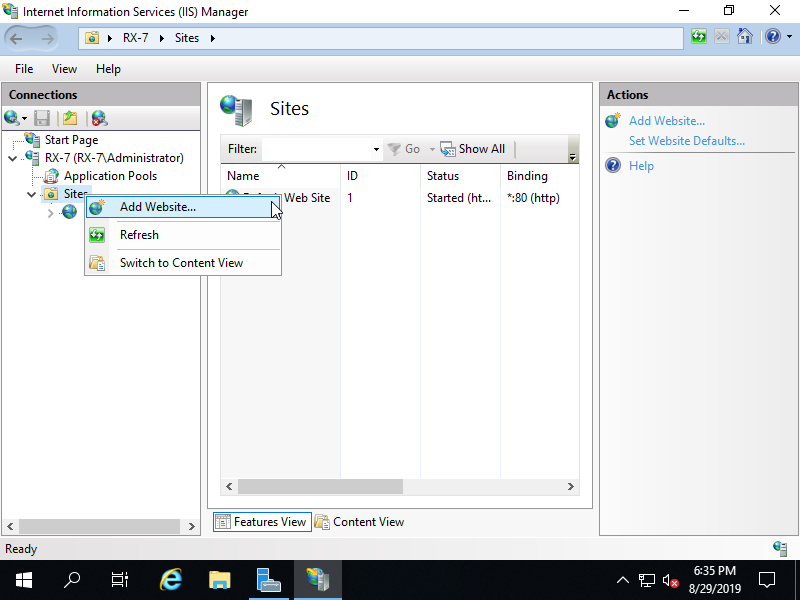
Step [3]Input any Site name (it is used on IIS Manager) for [Site name] field, for [Physical path] field, input Physical folder Path for this new site, and for [Host name], input server's hostname.
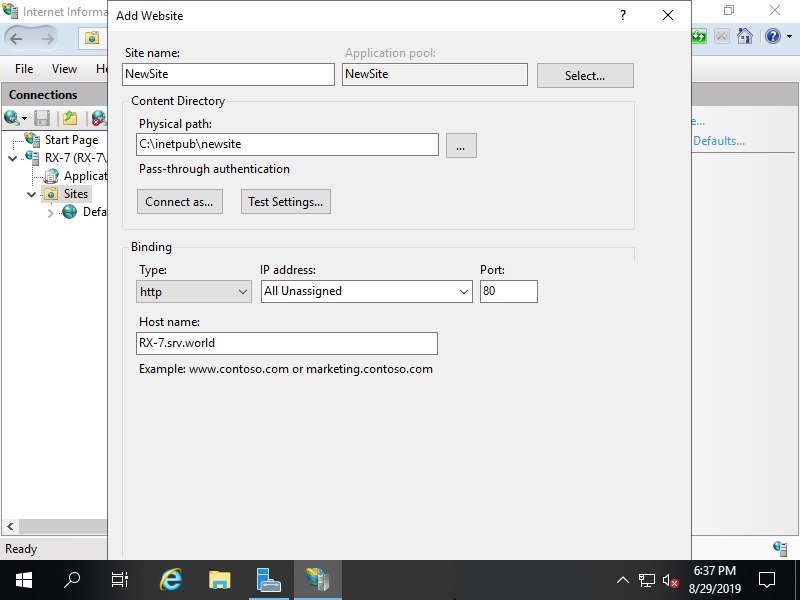
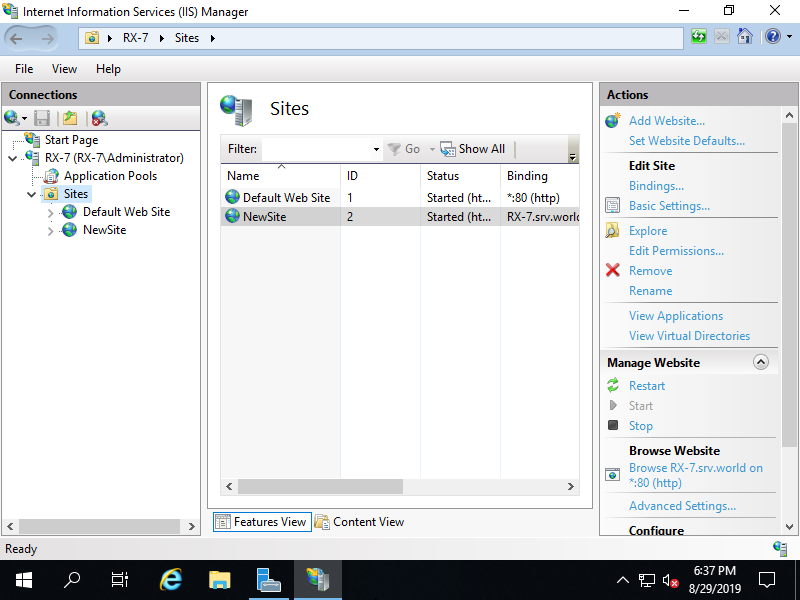
Step [4]If added normally, new Web Site is displayed on Sites list.
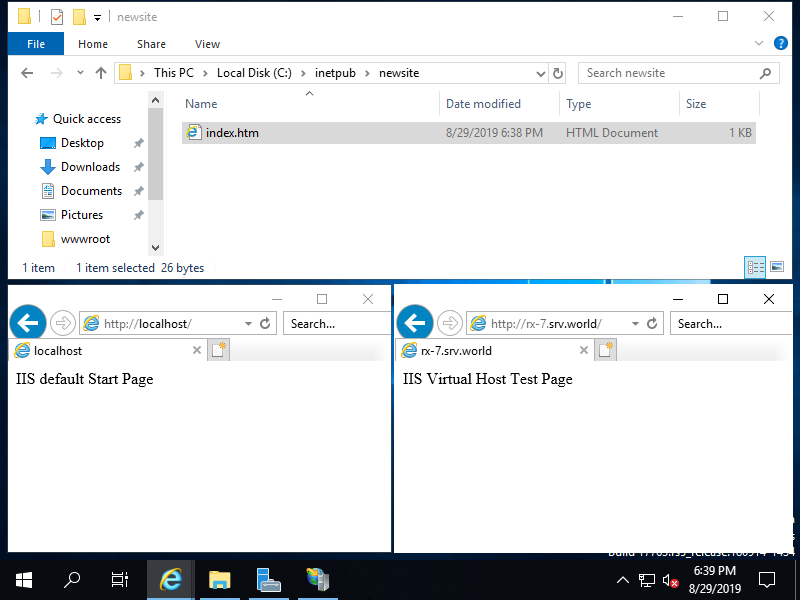
Step [5]Create a test page for new Web Site and verify accesses.
SSL/TLS Settings
Enable SSL/TLS Settings for Web Sites.
Step [1]First, Buy or Get ot Create SSL Certificate. If you use self signed certificate, refer to here. On this example, Use certificate from Let's Encrypt, refer to here (Linux tutorial) to get Let's Encrypt certificate and convert it to PKCS12 (PFX) for Windows.
Using Command Line Interface (CLI)
Step [2]Run PowerShell with Admin Privilege and Configure. If you use SSL certificate that you got or create it on another Host, import it first. If you created self signed certificate on the same Host with IIS like the link of [1], this work does not need, skip here.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# store export password you set on certificate to a variable
PS C:\Users\Administrator> $Password = ConvertTo-SecureString -AsPlainText -Force "P@ssw0rd"
# import to [Cert:\LocalMachine\My]
# ⇒ on GUI look, stored under [Certificates - Local Computer] - [Personal]
PS C:\Users\Administrator> Import-PfxCertificate -FilePath C:\Users\Administrator\rx-7.pfx -CertStoreLocation Cert:\LocalMachine\My -Password $Password
PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\My
Thumbprint Subject
---------- -------
228940060FF922175C2F435A135FD1CB26FC3A84 CN=rx-7.bizantum.lab
Step [3]Configure SSL/TLS settings on a Web Site. This example is based on the environment that certificate is stored under the [Cert:\LocalMachine\My].
# confirm certificate
PS C:\Users\Administrator> Get-ChildItem Cert:\LocalMachine\My
PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\My
Thumbprint Subject
---------- -------
228940060FF922175C2F435A135FD1CB26FC3A84 CN=rx-7.bizantum.lab
# store target certificate to a variable $Cert
PS C:\Users\Administrator> $Cert = Get-ChildItem Cert:\LocalMachine\My\228940060FF922175C2F435A135FD1CB26FC3A84
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
RX-7.bizantum.lab 2 Started C:\inetpub\wwwroot\newsite http *:80:rx-7.bizantum.lab
# set SSL Binding to [RX-7.bizantum.lab] site
PS C:\Users\Administrator> New-WebBinding -Name "RX-7.bizantum.lab" -IPAddress "*" -HostHeader "rx-7.bizantum.lab" -Port 443 -Protocol https
# set $Cert to SSL Binding
PS C:\Users\Administrator> New-Item IIS:\SslBindings\0.0.0.0!443!rx-7.bizantum.lab -Value $Cert
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
RX-7.bizantum.lab 2 Started C:\inetpub\wwwroot\newsite http *:80:rx-7.bizantum.lab
https *:443:rx-7.bizantum.lab sslFlags=0
# verify accesses
# if self signed certificate, add [-k] (--insecure) option
PS C:\Users\Administrator> curl.exe https://rx-7.bizantum.lab/
RX-7.bizantum.lab Top Page
Using Graphical User Interface (GUI)
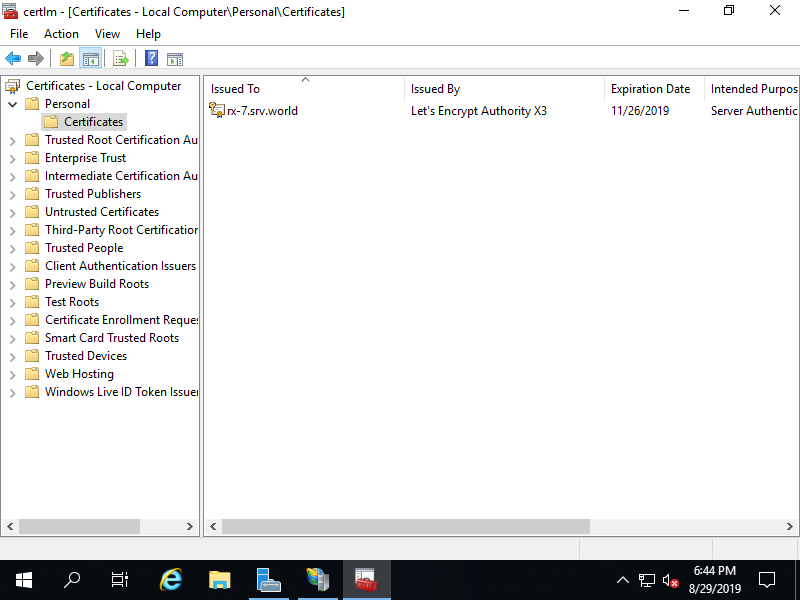
Step [4]First, import SSL certificate in certificates store. On this example, import it under [Certificates - Local Computer] - [Personal] like follows.
Step [5]Configure SSL/TLS Setting for a Web Site. Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager] and then Right Click the Site you'd like to set SSL binding on the left pane and Select [Edit Bindings].
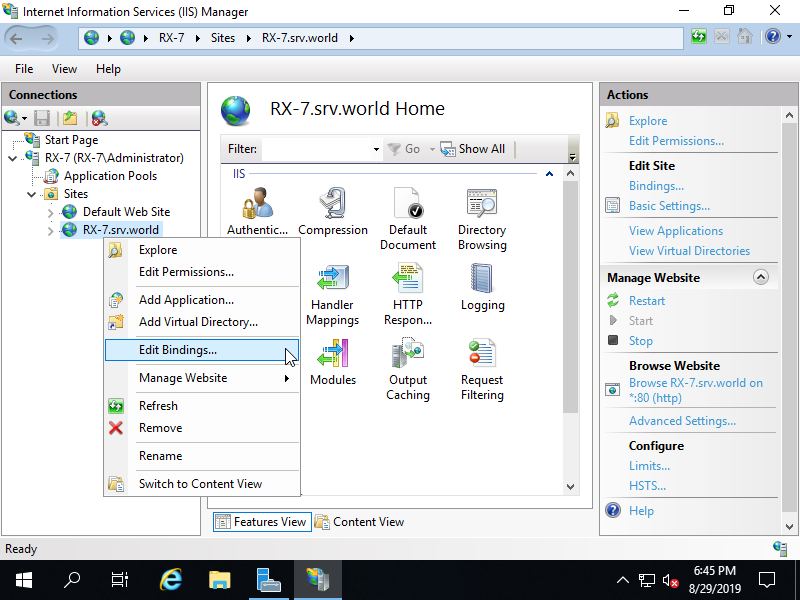
Step [6]Click [Add] button.
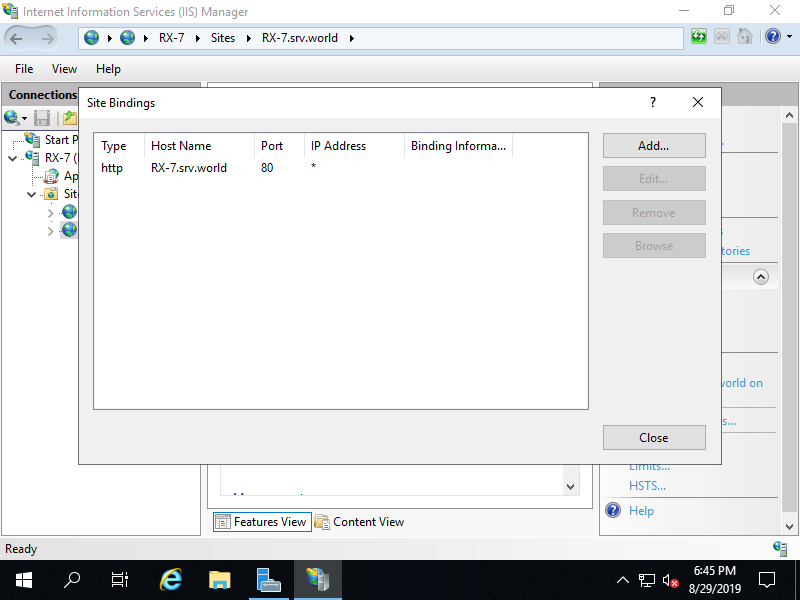
Step [7]Select [https] on [Type] filed and input Web Site's Hostname on [Host name] field. For [SSL certificate] field, Select your certificate that you imported on [4] section.
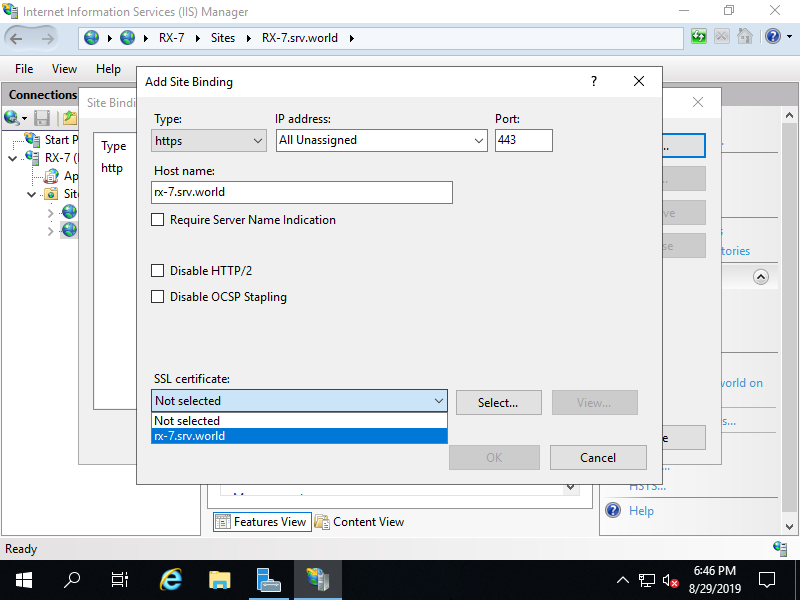
Step [8]SSL binding is configured.
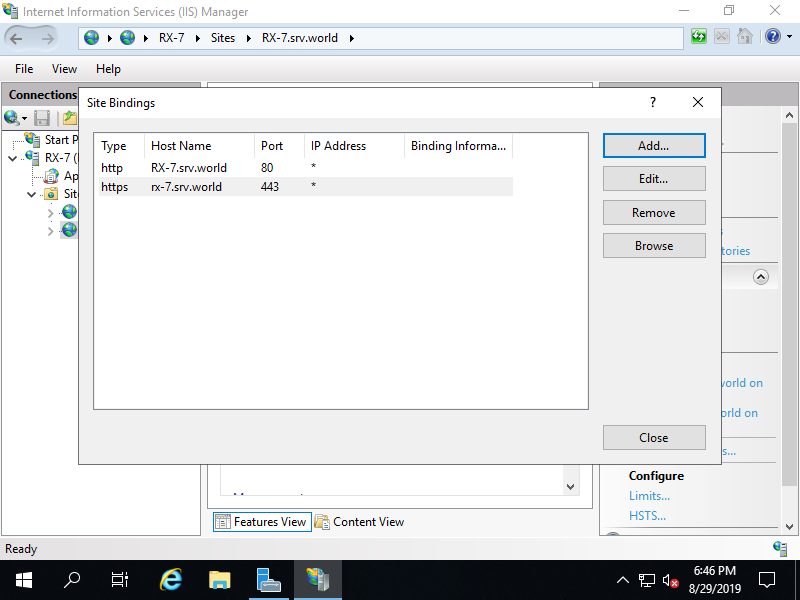
Step [9]Access to the Web Site with HTTPS to verify working.
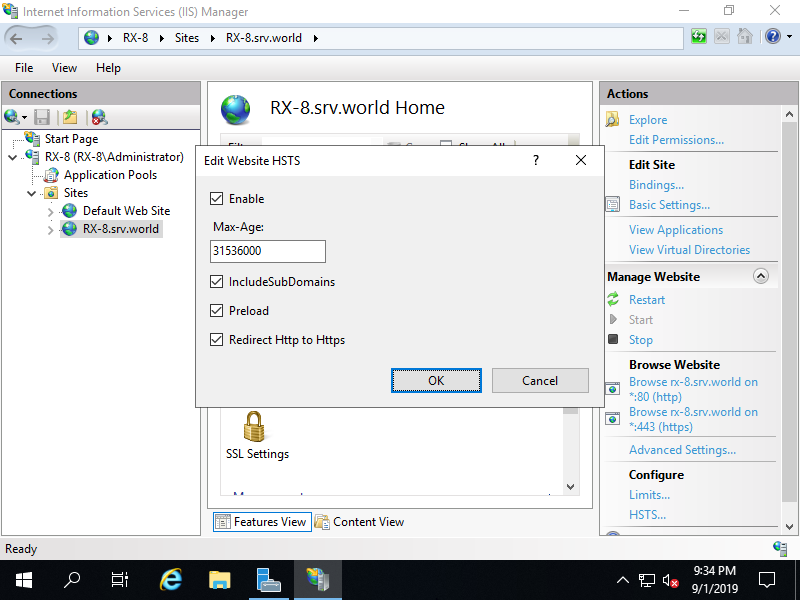
Enable HSTS
Enable HSTS (Hypertext Strict Transport Security) for Web Sites. For [includeSubDomains] option below, all subdomains are included in HSTS target, so you need to verify well before setting it's possible to access to all subdomains with HTTS if specify this option.
Step [1]Enable SSL/TLS settings for Web Sites you's like to enable HSTS.
Using Command Line Interface (CLI)
Step [2]Run PowerShell with Admin Privilege and Configure.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# get site collection
PS C:\Users\Administrator> $sitesCollection = Get-IISConfigSection -SectionPath "system.applicationHost/sites" | Get-IISConfigCollection
# get web site you'd like to set HSTS
# specify the name of site for "name"="***"
PS C:\Users\Administrator> $siteElement = Get-IISConfigCollectionElement -ConfigCollection $sitesCollection -ConfigAttribute @{"name"="RX-7.bizantum.lab"}
# get setting of HSTS for target site
PS C:\Users\Administrator> $hstsElement = Get-IISConfigElement -ConfigElement $siteElement -ChildElementName "hsts"
# enable HSTS for target site
PS C:\Users\Administrator> Set-IISConfigAttributeValue -ConfigElement $hstsElement -AttributeName "enabled" -AttributeValue $true
# set [max-age] of HSTS as 31536000 sec (365 days)
# for [max-age], refer to https://hstspreload.org/
PS C:\Users\Administrator> Set-IISConfigAttributeValue -ConfigElement $hstsElement -AttributeName "max-age" -AttributeValue 31536000
# set [includeSubDomains] of HSTS as enabled
# this option applys to all subdomains
PS C:\Users\Administrator> Set-IISConfigAttributeValue -ConfigElement $hstsElement -AttributeName "includeSubDomains" -AttributeValue $true
# set [redirectHttpToHttps] of HSTS as enabled
PS C:\Users\Administrator> Set-IISConfigAttributeValue -ConfigElement $hstsElement -AttributeName "redirectHttpToHttps" -AttributeValue $true
Using Graphical User Interface (GUI)
Step [3]Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager], and then Select a Web Site you'd like to set HSTS and Click [HSTS...] on the right pane.
Step [4]Check a box [Enable]. For other items, refer to [https://hstspreload.org/].
Install ASP.NET Feature
Install Install ASP.NET feature to configure Web Application environment.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# install ASP.NET 4.7
# if also install ASP.NET 3.5, specify [Web-Asp-Net] with comma separated
PS C:\Users\Administrator> Install-WindowsFeature Web-Asp-Net45
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {ASP.NET 4.7, Application Development, ASP...
# create a test page to verify (example below is with C#)
PS C:\Users\Administrator> $str_document = @'
<%@ Page Language="C#" %>
<script runat="server">
private void Page_Load() {
Msg.Text = "Hello ASP.NET World!";
}
</script>
<html>
<body>
<asp:Label runat="server" id="Msg" />
</body>
</html>
'@
# redirect contents to a page
PS C:\Users\Administrator> $str_document > C:\inetpub\newsite\index.aspx
# verify accesses
PS C:\Users\Administrator> curl.exe rx-7.bizantum.lab/index.aspx
<html>
<body>
<span id="Msg">Hello ASP.NET World!</span>
</body>
</html>
Using Graphical User Interface (GUI)
Step [2]Run [Start] - [Server Manager] and enter [Add roles and features], then check a box [ASP.NET 4.7] like follows. (if install ASP.NET 3.5, check a box, too).
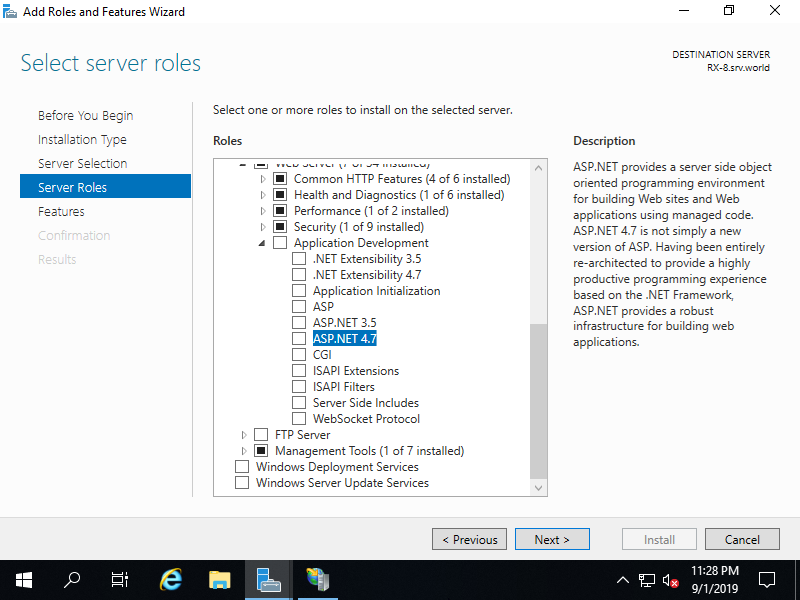
Step [3]Addtional features are required to add ASP.NET, Click [Add Features] button and proceed to Install.
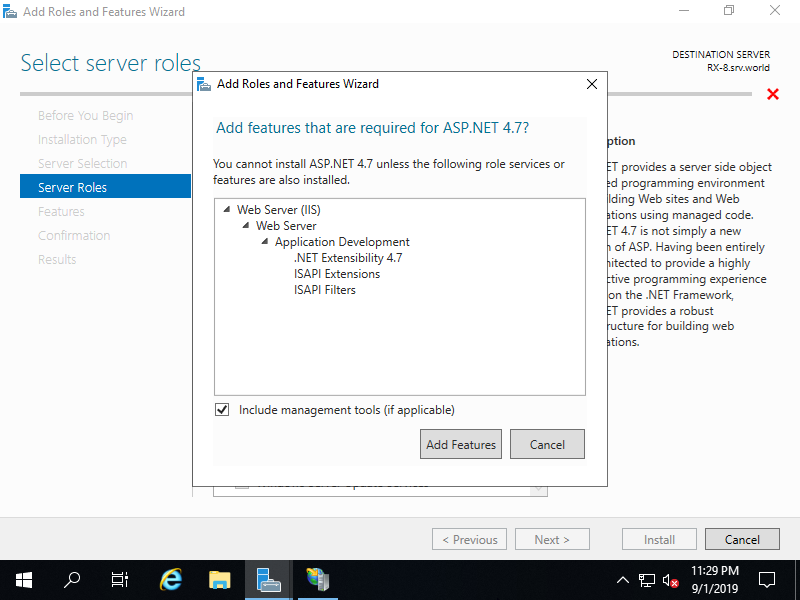
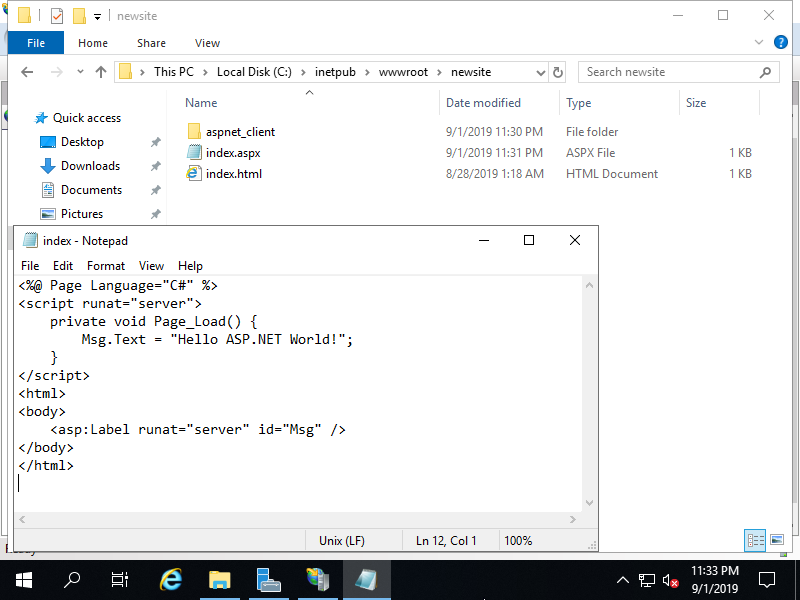
Step [4]After finishing installation, create a test page to verify working.
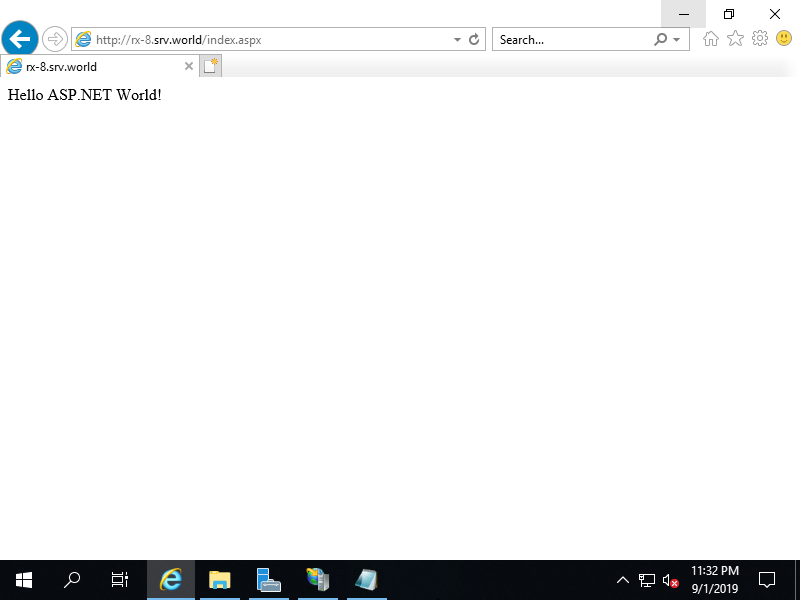
Step [5]That's OK if test aspx page returns normally.
Basic Authentication
Set Basic Authentication to a folder to require authentication for users. On Basic Authentication, username and password sends with plain text, so it should be configured SSL setting, too. Refer to here for SSL config.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure. On this example, Configure settings that create a [auth_basic] folder under the [RX-7.bizantum.lab] site and set Basic Authentication to the Folder.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# install Basic Authentication feature
PS C:\Users\Administrator> Install-WindowsFeature Web-Basic-Auth
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {Basic Authentication}
# restart IIS
PS C:\Users\Administrator> Restart-Service W3SVC
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
RX-7.bizantum.lab 2 Started C:\inetpub\newsite http *:80:RX-7.bizantum.lab
https *:443:rx-7.bizantum.lab sslFlags=0
# create [auth_basic] folder
PS C:\Users\Administrator> New-Item -ItemType Directory -Path "IIS:\Sites\RX-7.bizantum.lab\auth_basic"
Directory: WebAdministration::\\RX-7\Sites\RX-7.bizantum.lab
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/9/2019 7:21 PM auth_basic
# disable anonymous authentication for target folder
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/security/authentication/anonymousAuthentication' -Location "RX-7.bizantum.lab/auth_basic" -Name enabled -Value False
# enable basic authentication for target folder
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/security/authentication/basicAuthentication' -Location "RX-7.bizantum.lab/auth_basic" -Name enabled -Value True
# restart target Web site
PS C:\Users\Administrator> Restart-WebItem -PSPath 'IIS:\Sites\RX-7.bizantum.lab'
# create a test page
PS C:\Users\Administrator> Write-Output "Basic Authentication Test Page" | Out-File C:\inetpub\newsite\auth_basic\index.html -Encoding Default
# verify accesses ⇒ [-u (username)]
PS C:\Users\Administrator> curl.exe -u Serverworld https://rx-7.bizantum.lab/auth_basic/
Enter host password for user 'Serverworld': # user password
Basic Authentication Test Page
Using Graphical User Interface (GUI)
Step [2]Run [Start] - [Server Manager] and enter [Add roles and features], then check a box [Basic Authentication] and install it.
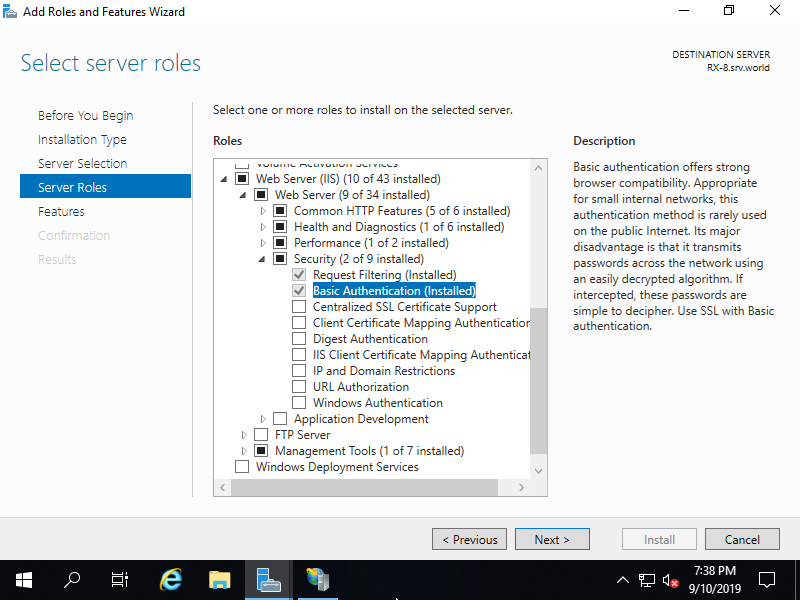
Step [3]After installing, restart IIS.
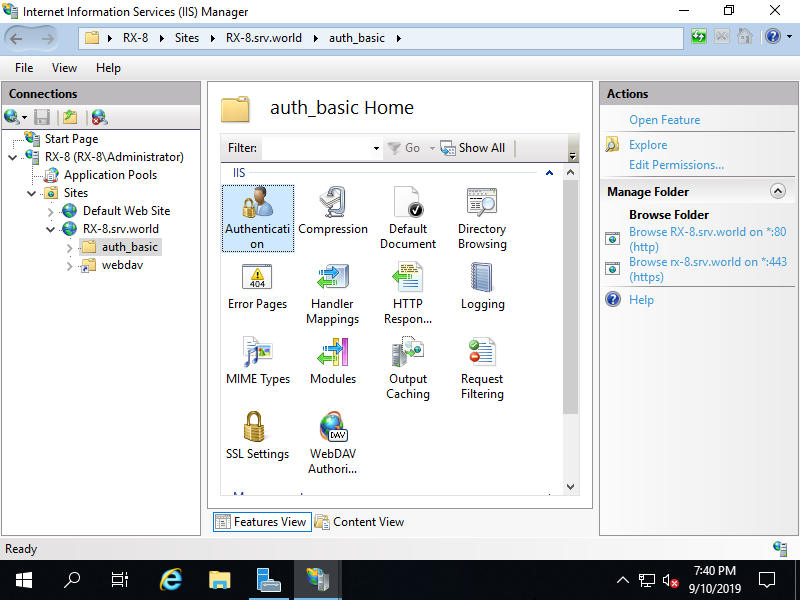
Step [4]Create a folder that you'd like to set Basic Authentication. On this example, create a [auth_basic] folder for it. Also add NTFS access permission for users or groups you'd like to allow to access to the folder. Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager], and then Select a folder you'd like to set Basic Authentication on the left pane and then Open to click [Authentication] on the center pane.
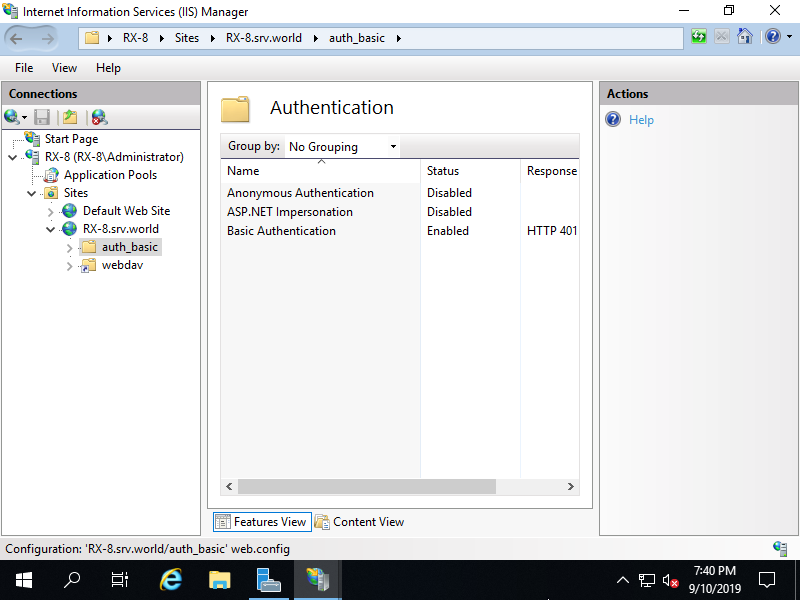
Step [5]Disable [Anonymous Authentication] and Enable [Basic Authentication] like follows.
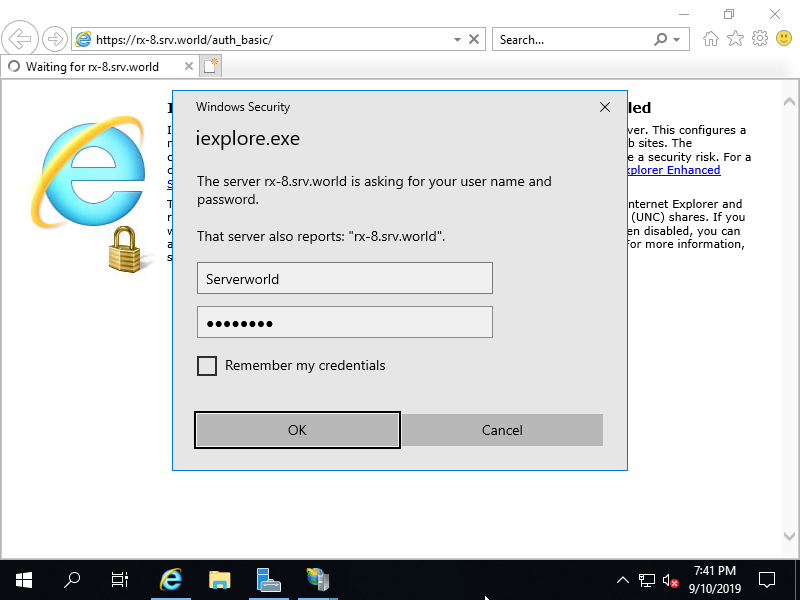
Step [6]Create a test page under the folder you set Basic Authentication and verify accesses. Authenticate with a user you set to allow accesses.
Step [7]That's OK if successfully authenticate and test page is shown normally.
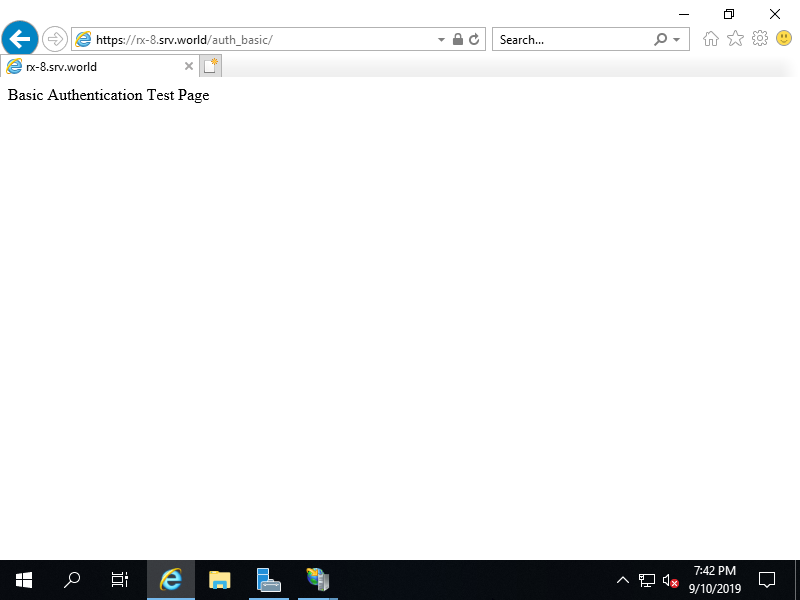
WebDAV Setting
Configure WebDAV Setting to use File sharing over HTTP. It should be configured SSL setting, too, because of using Basic Authentication to WebDAV folder on this example.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure. On this example, Configure settings that set a virtual directory under a Web Site and set WebDAV to the directory. And also create a local group [DavGroup] to allow read and write permission for them to WebDAV directory.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# kinstall WebDAV feature
PS C:\Users\Administrator> Install-WindowsFeature Web-DAV-Publishing
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {WebDAV Publishing}
# restart IIS
PS C:\Users\Administrator> Restart-Service W3SVC
# create a group [DavGroup]
PS C:\Users\Administrator> New-LocalGroup -Name "DavGroup"
Name Description
---- -----------
DavGroup
# add a user to [DavGroup] group
# (the user you allow to access to WebDAV directory)
PS C:\Users\Administrator> Add-LocalGroupMember -Group "DavGroup" -Member "Serverworld"
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
RX-7.bizantum.lab 2 Started C:\inetpub\newsite http *:80:RX-7.bizantum.lab
https *:443:rx-7.bizantum.lab sslFlags=0
# create [webdav] folder
PS C:\Users\Administrator> mkdir C:\inetpub\webdav
# set [webdav] folder as a virtual directory on IIS
PS C:\Users\Administrator> New-WebVirtualDirectory -Site "RX-7.bizantum.lab" -Name "webdav" -PhysicalPath "C:\inetpub\webdav"
Name PhysicalPath
---- ------------
webdav C:\inetpub\webdav
# enable WebDAV feature
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/webdav/authoring' -Location "RX-7.bizantum.lab" -Name enabled -Value True
# disable anonymous authentication on [webdav] folder
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/security/authentication/anonymousAuthentication' -Location "RX-7.bizantum.lab/webdav" -Name enabled -Value False
# enable basic authentication on [webdav] folder
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/security/authentication/basicAuthentication' -Location "RX-7.bizantum.lab/webdav" -Name enabled -Value True
# allow Read,Write,Source persmission to [webdav] folder for [DavGroup] group
PS C:\Users\Administrator> Add-WebConfiguration -Filter "/system.webServer/webdav/authoringRules" -Location "RX-7.bizantum.lab/webdav" -Value @{path="*";roles="DavGroup";access="Read,Write,Source"}
# allow full control NTFS permission to [webdav] folder for [DavGroup] group
PS C:\Users\Administrator> icacls "C:\inetpub\webdav" /grant "DavGroup:(OI)(CI)(F)"
processed file: C:\inetpub\webdav
Successfully processed 1 files; Failed processing 0 files
# enable [Directory Browsing] to [webdav] folder
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/directoryBrowse' -Location "RX-7.bizantum.lab/webdav" -Name enabled -Value True
# restart target Web site
PS C:\Users\Administrator> Restart-WebItem -PSPath 'IIS:\Sites\RX-7.bizantum.lab'
# verify accesse ⇒ [-u (username)]
PS C:\Users\Administrator> curl.exe -u Serverworld https://rx-7.bizantum.lab/webdav/
Enter host password for user 'Serverworld': # user password
<html><head><title>rx-7.bizantum.lab - /webdav/</title></head><body><H1>rx-7.bizantum.lab - /webdav/</H1><hr>
<pre><A> HREF="/">[To Parent Directory]</A><br><br> <br></pre><hr></body></html>
Using Graphical User Interface (GUI)
Configure WebDAV Server
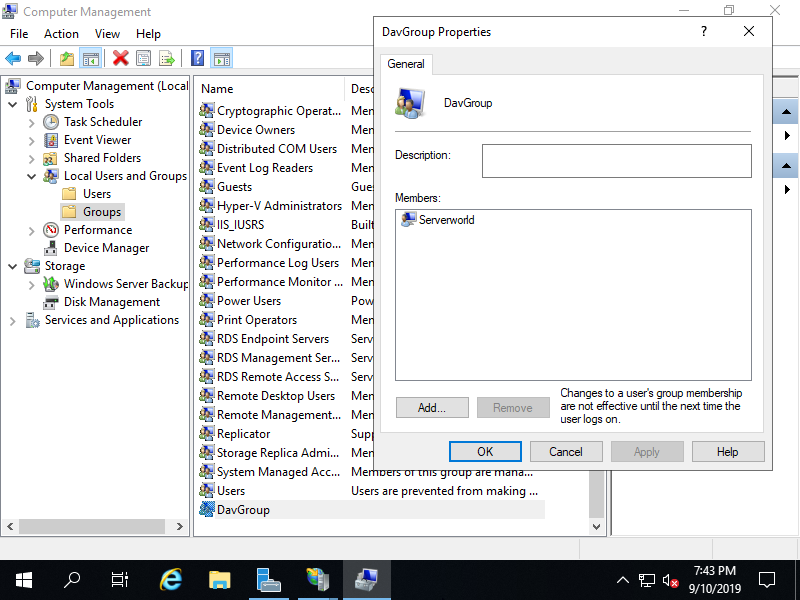
Step [2]Create a users or groups to allow to access to WebDAV folder. On this example, create a [DavGroup] group and add [Serverworld] user to it to allow WebDAV access. To add local users and so on, refer to here.
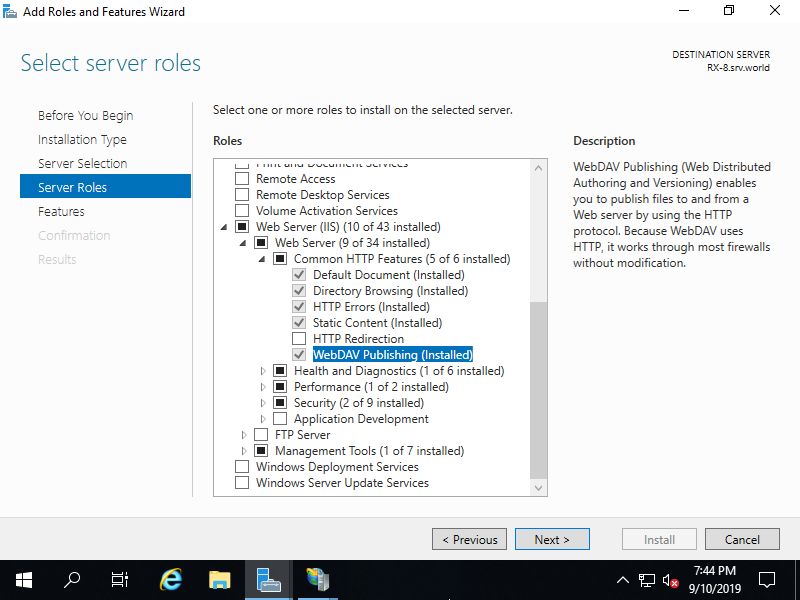
Step [3]Install WebDAV feature. Run [Start] - [Server Manager] and enter [Add roles and features], then check a box [WebDAV Publishing] and install it. After installing it, restart IIS service.
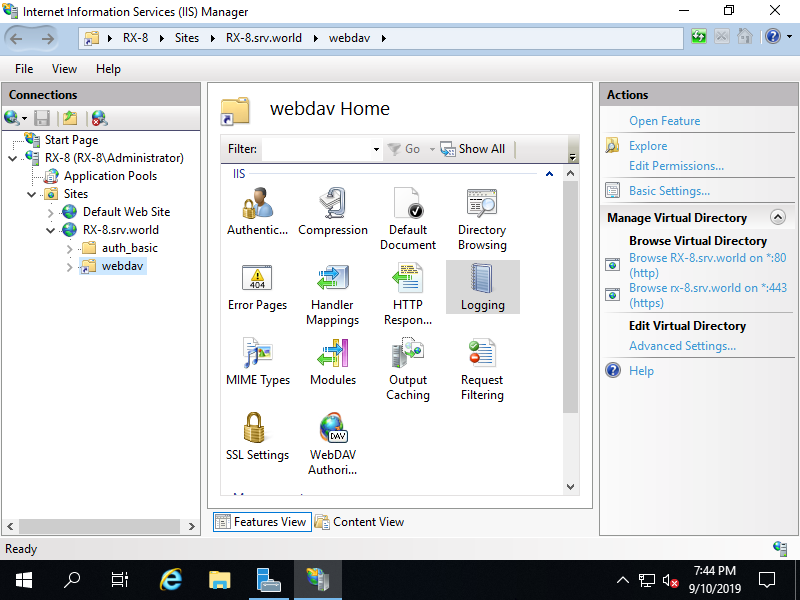
Step [4]Create a folder for WebDAV. On this example, set a virtual directory [webdav] like follows (physical path is [C:\inetpub\webdav]). To set virtual directory, refer to here.
Step [5]Select a Web site you'd like to set WebDAV on the left pane and then, Click to open [WebDAV Authoring Rules] on the center pane.
Step [6]Click [Enable WebDAV] on the right pane.
Step [7]Select a folder for WebDAV and then, Click to open [WebDAV Authoring Rules] on the center pane.
Step [8]Click to open [Add Authoring Rule] on the right pane.
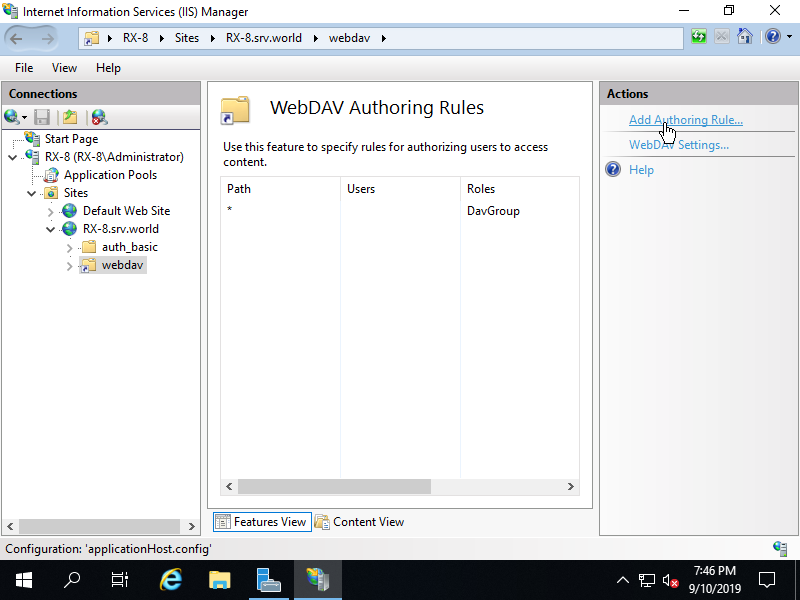
Step [9]Set access permission for WebDAV accesses. On this example, set like follows.
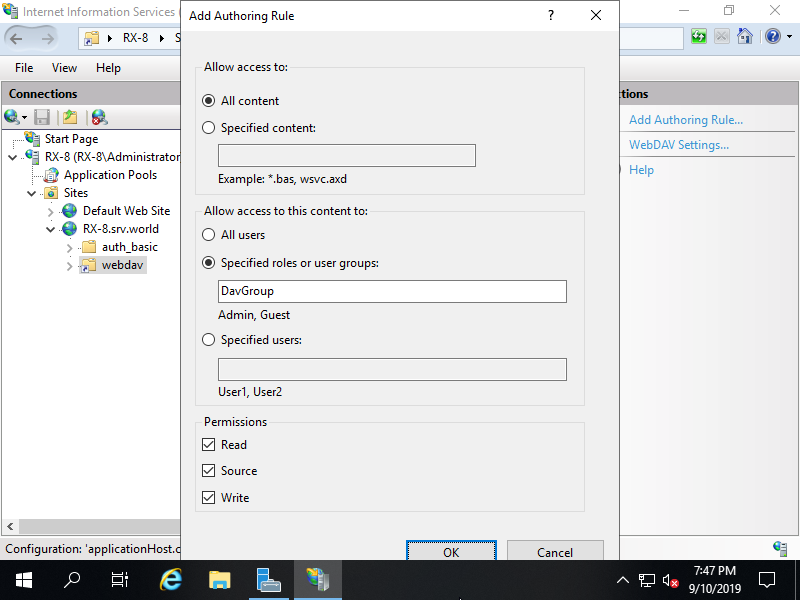
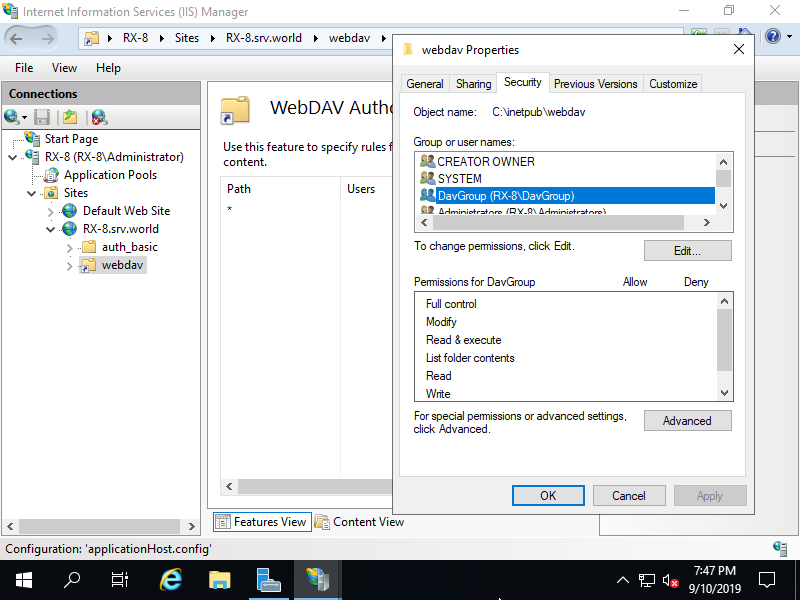
Step [10]It also needs NTFS access permission for WebDAV folder. Select WebDAV folder and right clicking it, then select to open [Access permission], then add permissions for your requirements.
Step [11]Select a folder for WebDAV and then, Click to open [Authentication] on the center pane.
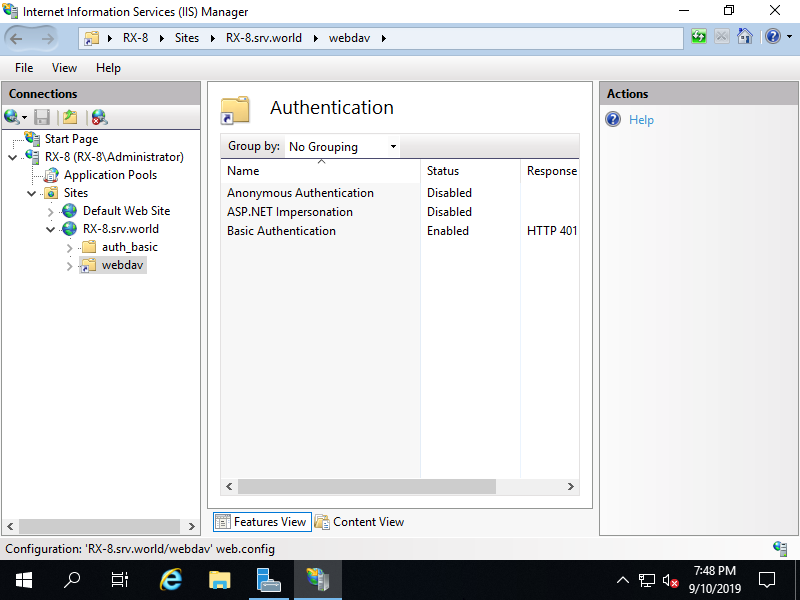
Step [12]Disable [Anonymous Authentication] and Enable [Basic Authentication] like follows.
Step [13]Select a folder for WebDAV and then, Click to open [Directory Browsing] on the center pane.
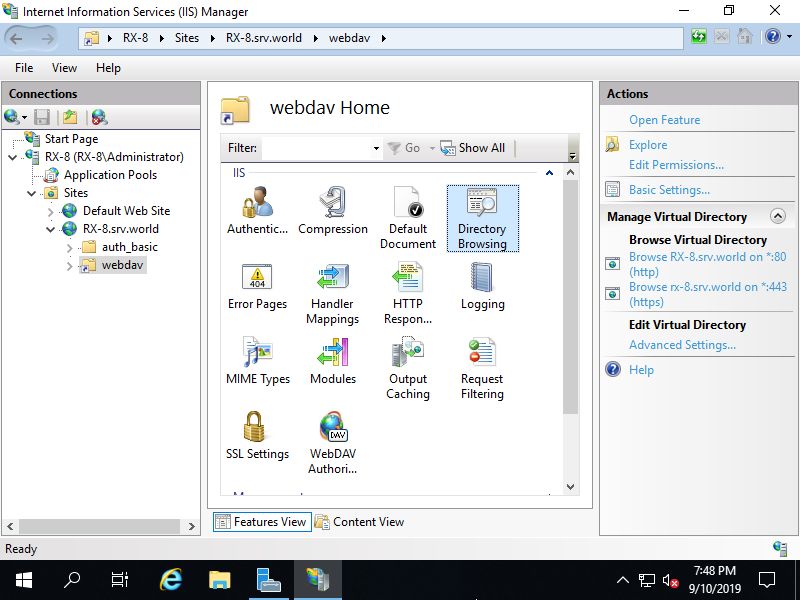
Step [14]Click [Enable] on the right pane. For information to display, select the one you'd like to set.
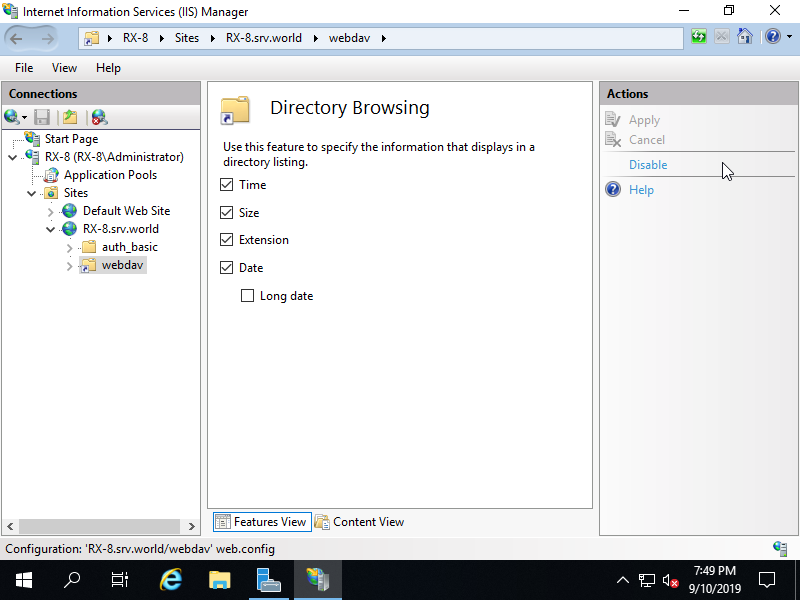
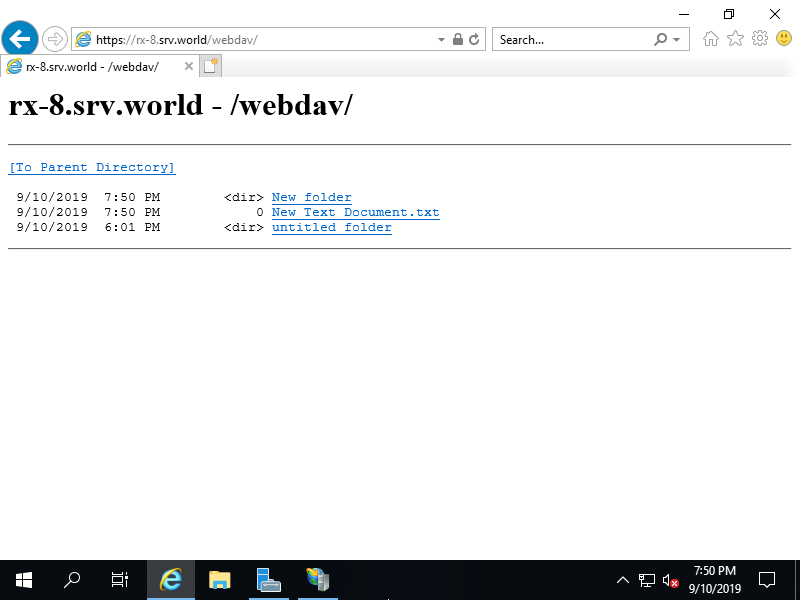
Step [15]That's OK. Access to the URL of WebDAV folder with Web Browser. If success authentication and displayed content of WebDAV folder, settings are no ploblem.
Configure WebDAV Client
This is how to access to WebDAV folder from Client Computers. This example in on Windows 10. There are some WebDAV client softwares in the world, but on this example, use Windows WebDAV client feature.
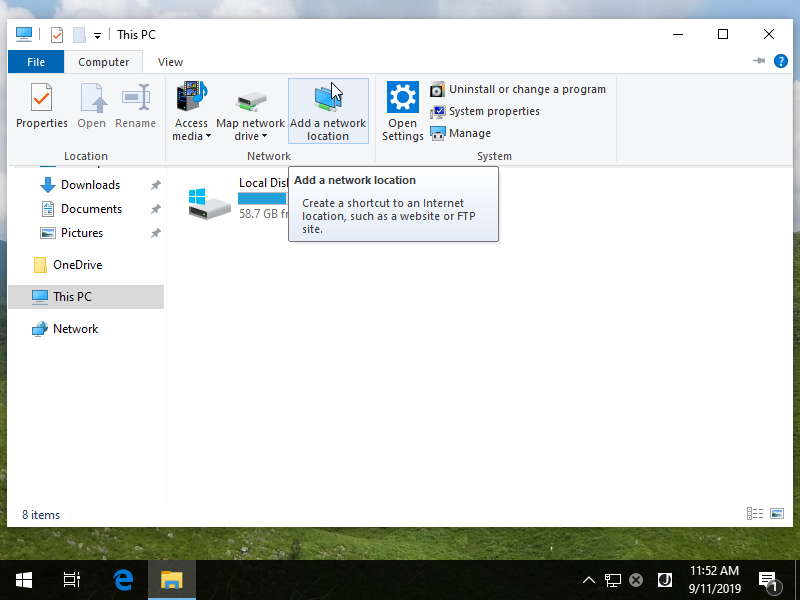
Step [16]Open [This PC] and move to [Computer] tab, then Click [Add a network location].
Step [17]Click [Next] button.
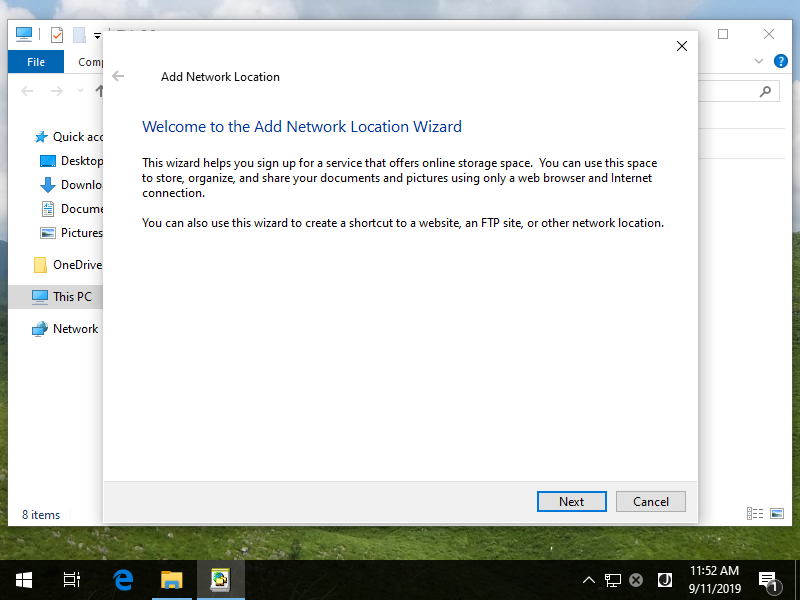
Step [18]Click [Next] button.
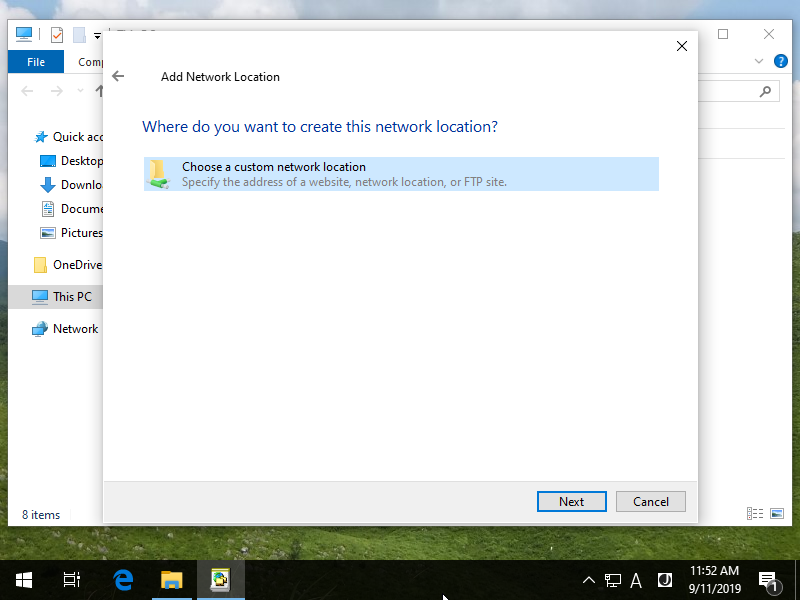
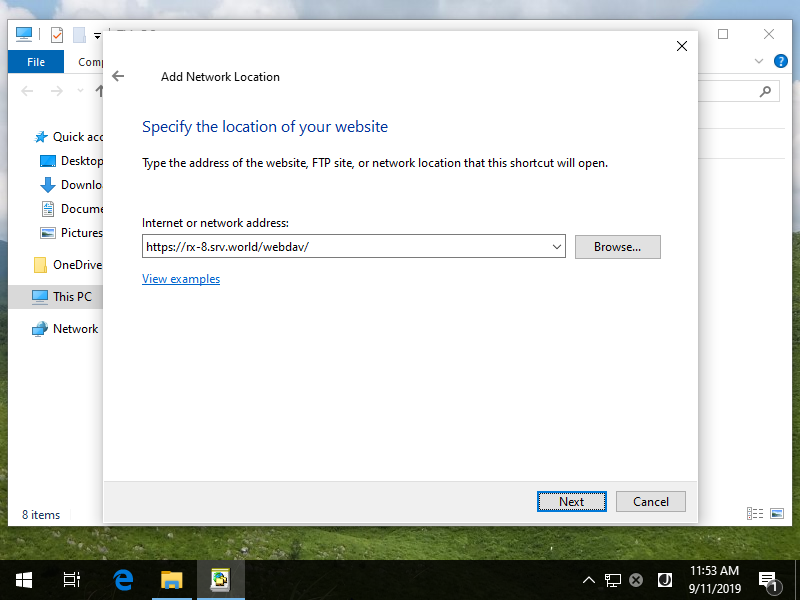
Step [19]Input WebDAV folder's URL and Click [Next] button.
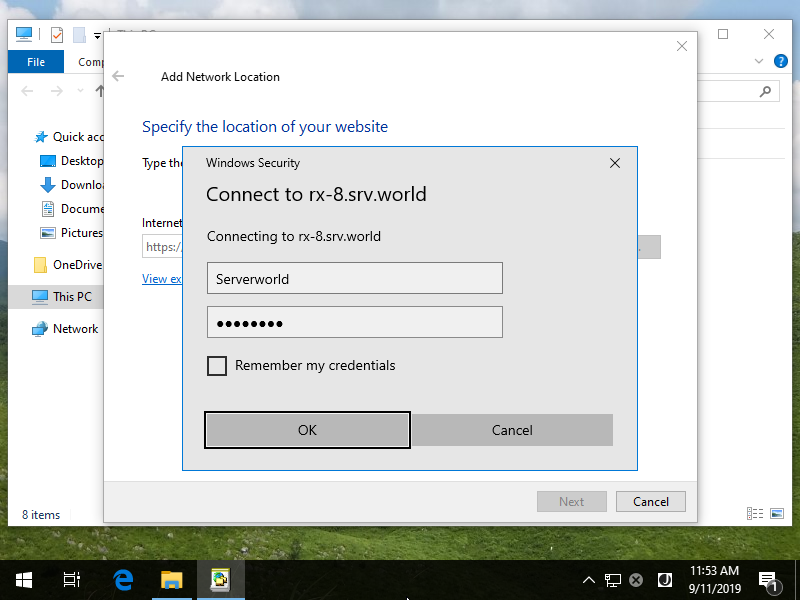
Step [20]Authenticate with a user you set to allow to access.
Step [21]After successfully finished authentication, Input any name to WebDAV folder that is used on your PC.
Step [22]Click [Finish] button.
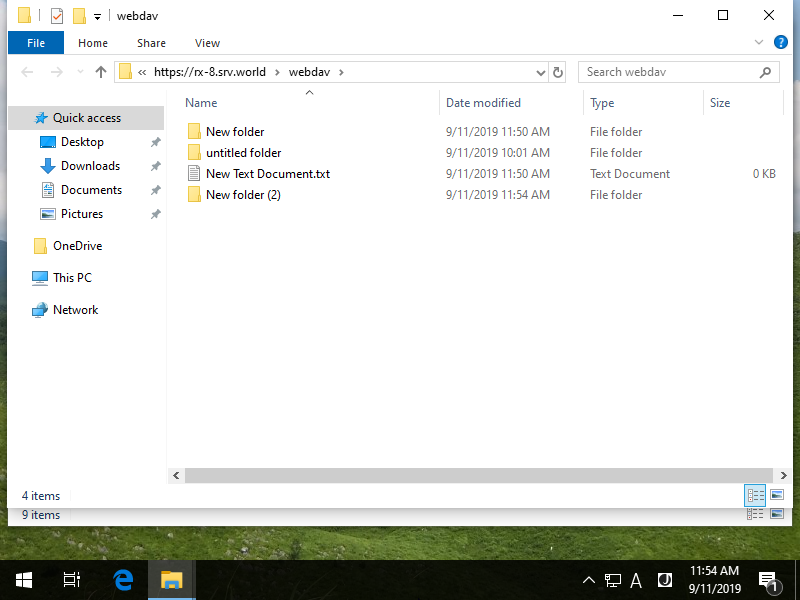
Step [23]If successfully accessed to WebDAV folder, verify to read and write files or directories.
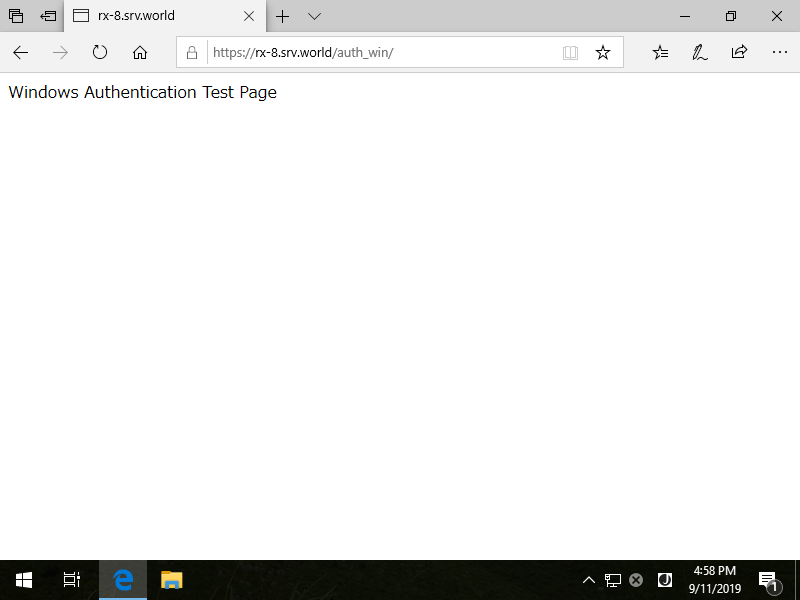
Windows Authentication
Set Windows Authentication to a folder to require authentication for users. For different point from Basic Authentication, On Basic Authentication, user authentication form is always displayed and it needs to input user information to authenticate manually. However, On Windows Authentication, if Client Computer is Windows OS and he accesses to the Windows Authentication folder, current logon user information is sent to IIS server automatically by Web Browser and authentication process runs with it.
Therefore, if IIS Host and Client Windows Host are in the same Windows AD Domain, when accessing to Windows Authentication folder from Windows Client, authentication form is not displayed and can access to the contents in the folder without inputting user infomation because authentication process runs automatically by Web Browser.
Furthermore, even if Client Windows computer is out of AD Domain, there is a case to be able to access without inputting user authentication infomation manually. If there is a local user on Client Host that has the same username and same password with a user on IIS Host, and also set a configration on Internet Explorer that target site is added as Local Intranet Site, then, authentication process succeeds automatically. For a few case of above only, authentication form in not displayed, but on other cases, it needs to input user authentication infomation manually, the behavior is the same with Basic Authetication on users viewpoint.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure. On this example, Configure settings that create a [auth_win] folder under the [RX-7.bizantum.lab] site and set Windows Authentication to the Folder.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# install windows Authentication feature
PS C:\Users\Administrator> Install-WindowsFeature Web-Windows-Auth
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {Windows Authentication}
# restart IIS
PS C:\Users\Administrator> Restart-Service W3SVC
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
RX-7.bizantum.lab 2 Started C:\inetpub\newsite http *:80:RX-7.bizantum.lab
https *:443:rx-7.bizantum.lab sslFlags=0
# create [auth_win] folder
PS C:\Users\Administrator> New-Item -ItemType Directory -Path "IIS:\Sites\RX-7.bizantum.lab\auth_win"
Directory: WebAdministration::\\RX-7\Sites\RX-7.bizantum.lab
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/11/2019 12:21 AM auth_win
# disable anonymous authentication for target folder
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/security/authentication/anonymousAuthentication' -Location "RX-7.bizantum.lab/auth_win" -Name enabled -Value False
# enable Windows authentication for target folder
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/security/authentication/windowsAuthentication' -Location "RX-7.bizantum.lab/auth_win" -Name enabled -Value True
# restart target Web site
PS C:\Users\Administrator> Restart-WebItem -PSPath 'IIS:\Sites\RX-7.bizantum.lab'
# create a test page
PS C:\Users\Administrator> Write-Output "Windows Authentication Test Page" | Out-File C:\inetpub\newsite\auth_win\index.html -Encoding Default
# verify accesses ⇒ [-u (username)]
# need authentication except specific some cases written in the beginning of this page
PS C:\Users\Administrator> curl.exe --ntlm -u Serverworld https://rx-7.bizantum.lab/auth_win/
Enter host password for user 'Serverworld': # user password
Windows Authentication Test Page
Using Graphical User Interface (GUI)
Step [2]Run [Start] - [Server Manager] and enter [Add roles and features], then check a box [Windows Authentication] and install it.
Step [3]After installing, restart IIS.
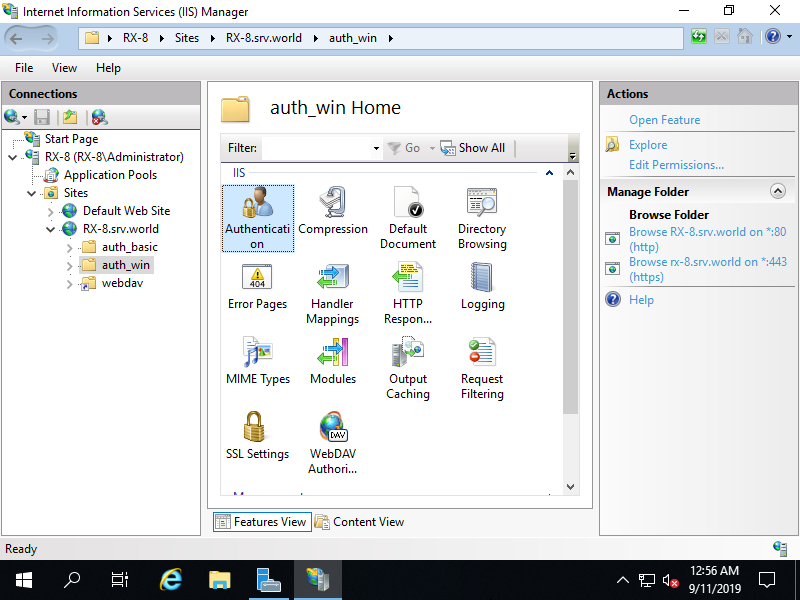
Step [4]Create a folder that you'd like to set Windows Authentication. On this example, create a [auth_win] folder for it. Also add NTFS access permission for users or groups you'd like to allow to access to the folder. Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager], and then Select a folder you'd like to set Windows Authentication on the left pane and then Open to click [Authentication] on the center pane.
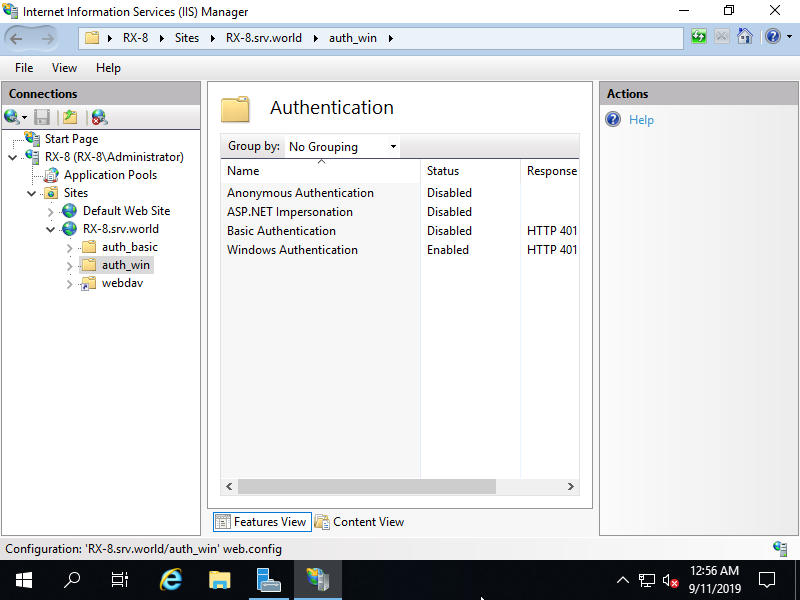
Step [5]Disable [Anonymous Authentication] and Enable [Windows Authentication] like follows.
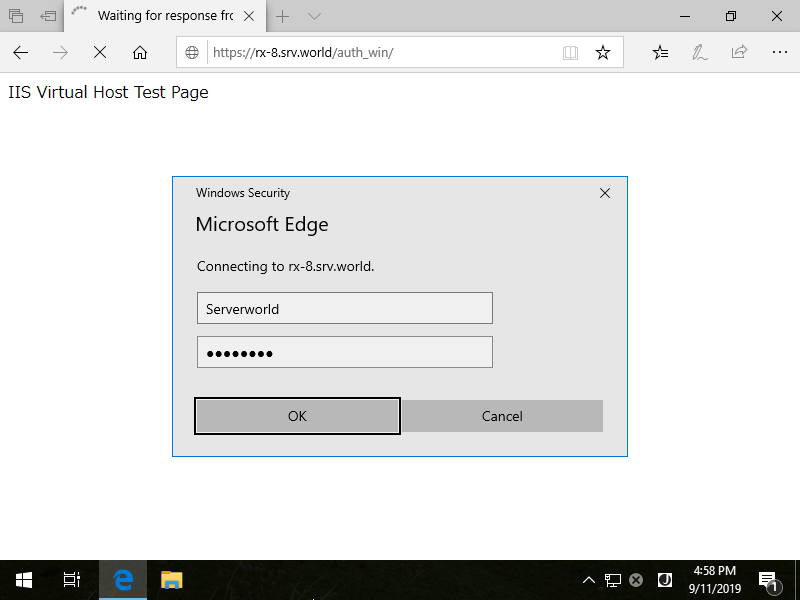
Step [6]Create a test page under the folder you set Windows Authentication and verify accesses. If Client host is also Windows and that is in specific cases written in the beginning of this page, the authentication form like follows are not displayed, but on other cases, following authentication form is displayed and required to input user authentication infomation.
Step [7]That's OK if successfully authenticate and test page is shown normally.
IP and Domain Ristrictions
Set IP and Domain Ristrictions to specific web contents.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# install IP and Domain Ristrictions feature
PS C:\Users\Administrator> Install-WindowsFeature Web-IP-Security
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {IP and Domain Restrictions}
# restart IIS
PS C:\Users\Administrator> Restart-Service W3SVC
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
RX-7.bizantum.lab 2 Started C:\inetpub\newsite http *:80:RX-7.bizantum.lab
https *:443:rx-7.bizantum.lab sslFlags=0
PS C:\Users\Administrator> Get-ChildItem C:\inetpub\newsite
Directory: C:\inetpub\newsite
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/10/2019 1:24 AM auth_basic
d----- 9/11/2019 12:23 AM auth_win
d----- 9/11/2019 7:09 PM content01
d----- 9/11/2019 7:09 PM content02
-a---- 9/9/2019 1:27 AM 28 index.html
# for example, set restriction to [content01] folder on [RX-7.bizantum.lab] site to deny from [10.0.0.128/29]
PS C:\Users\Administrator> Add-WebConfiguration -Filter '/system.webServer/security/ipSecurity' -Location "RX-7.bizantum.lab/content01" -Value @{ipAddress="10.0.0.128";subnetMask="29";allowed="false"}
# for example, change default setting for [content02] folder on [RX-7.bizantum.lab] site as deny all (default is allow all)
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/security/ipSecurity' -Location "RX-7.bizantum.lab/content02" -Name allowUnlisted -Value False
# for example, set permission to [content02] folder on [RX-7.bizantum.lab] site to allow from [10.0.0.240/255.255.255.240]
PS C:\Users\Administrator> Add-WebConfiguration -Filter '/system.webServer/security/ipSecurity' -Location "RX-7.bizantum.lab/content02" -Value @{ipAddress="10.0.0.240";subnetMask="255.255.255.240";allowed="true"}
# restart Web site
PS C:\Users\Administrator> Restart-WebItem -PSPath 'IIS:\Sites\RX-7.bizantum.lab'
Using Graphical User Interface (GUI)
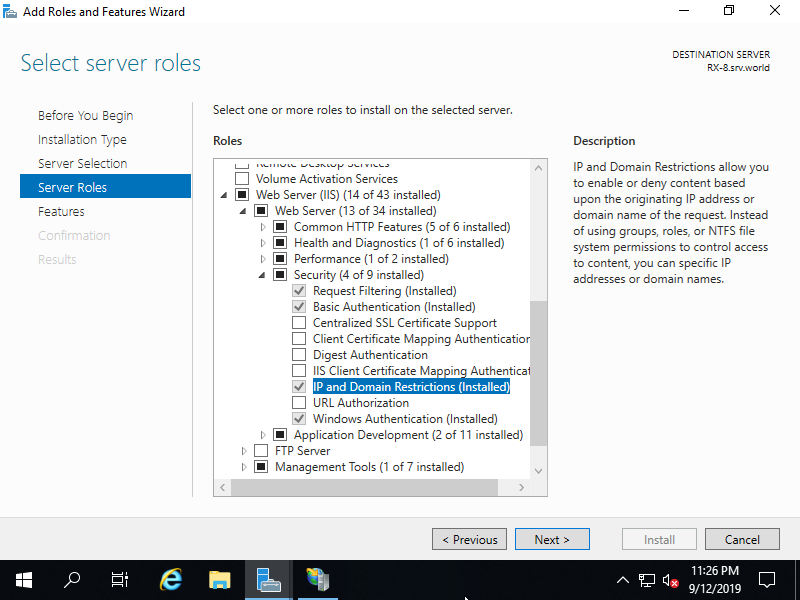
Step [2]Run [Start] - [Server Manager] and enter [Add roles and features], then check a box [IP and Domain Ristrictions] and install it.
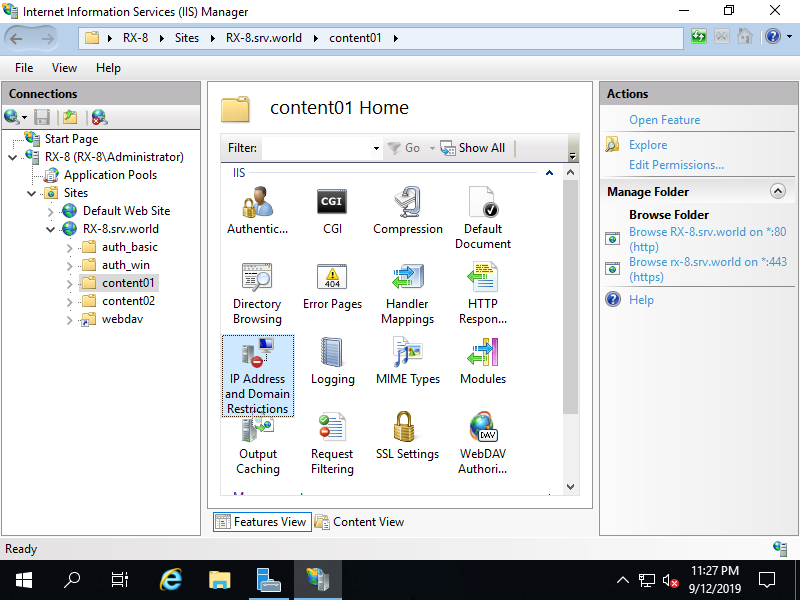
Step [3]On this example, Set restriction to [content01] folder on [RX-8.bizantum.lab] site. Select target folder on the left pane and open [IP Address and Domain Ristrictions] on the center pane.
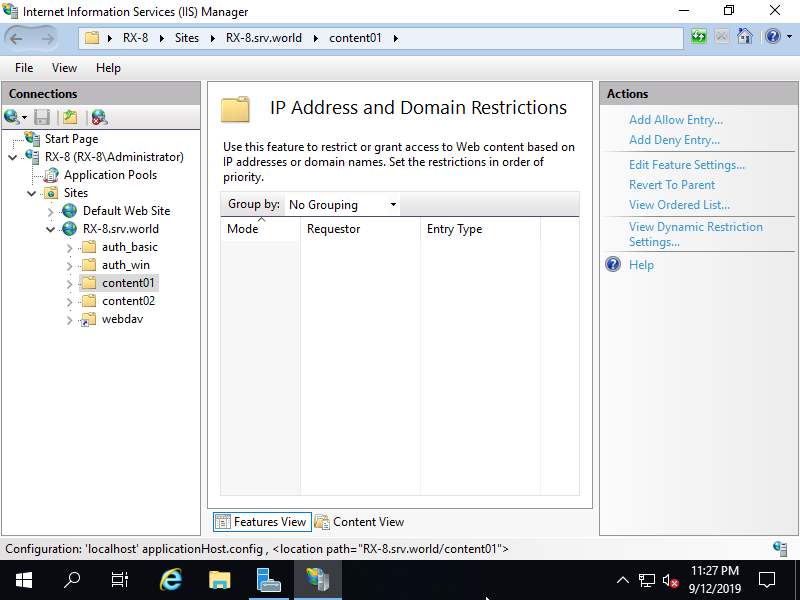
Step [4]By default, setting is allow all, so click [Add Deny Entry] on the right pane to restrict some IP address.
Step [5]Input an IP address on [Specific IP address] field, or IP address range on [IP address range]. On this example, set [10.0.0.128/29] range to deny from them.
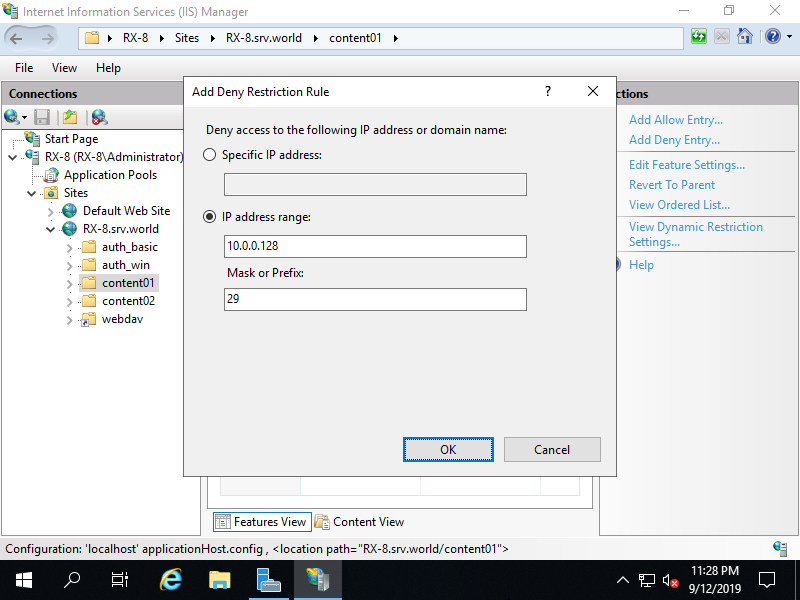
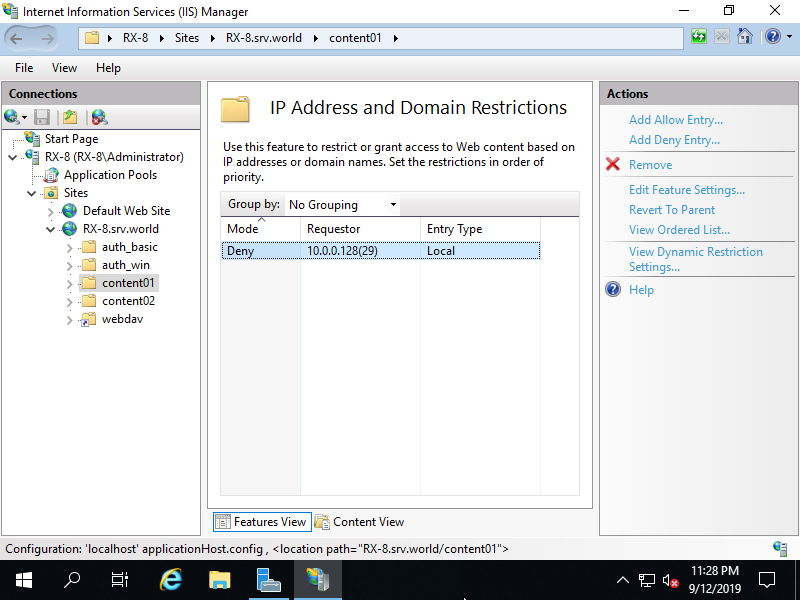
Step [6]After setting, entries are displayed. If you'd like to add more, possible to add with the same operation.
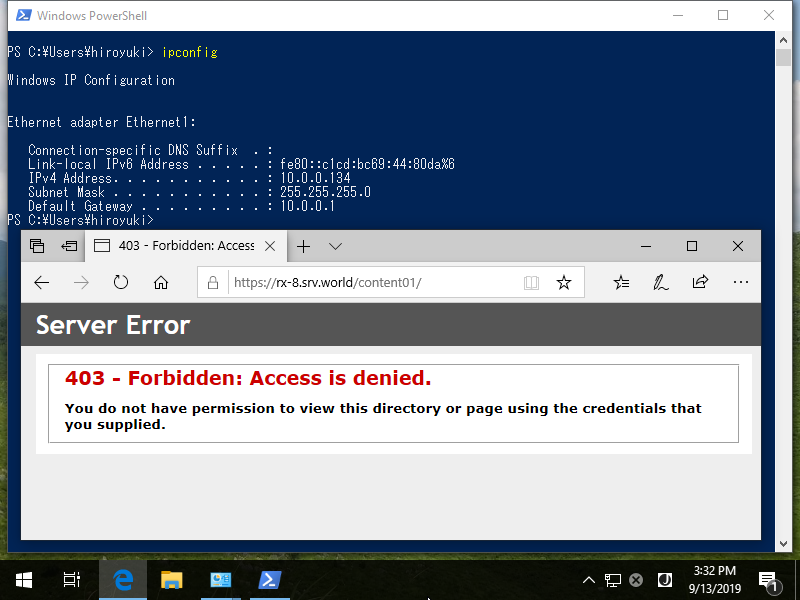
Step [7]After setting, verify working normally to access from denied computer and allowed computer. The example below shows that source computer that has [10.0.0.134] accessed to IIS site but he was denied as restricted settings.
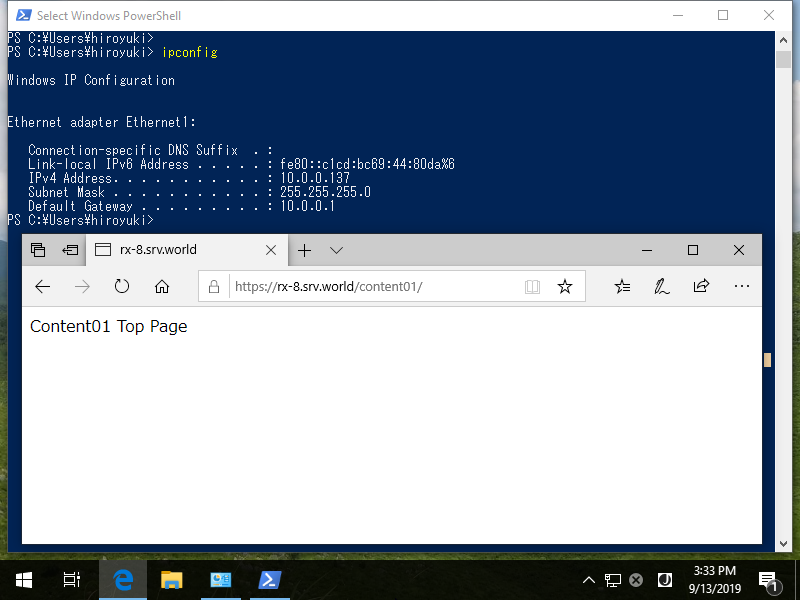
Step [8]The example below shows that source computer that has [10.0.0.137] accessed to IIS site and he could access to it as settings.
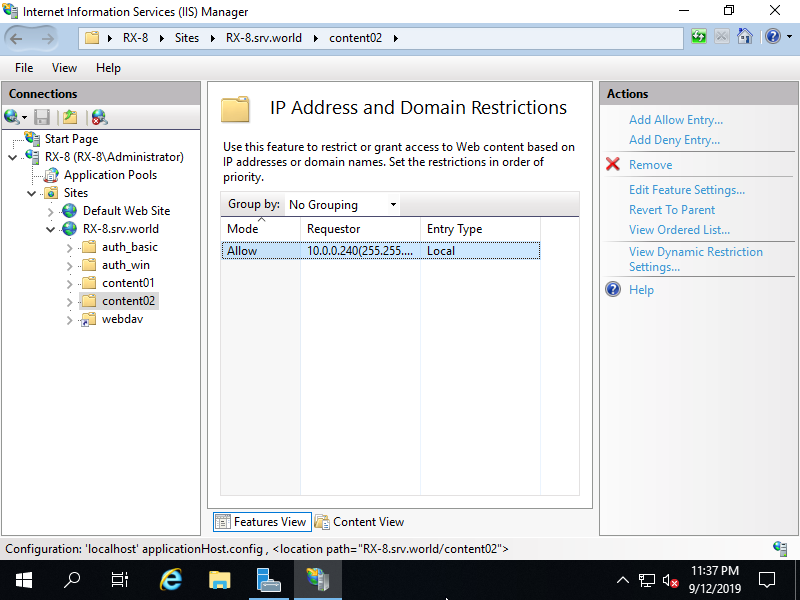
Step [9]For more example, Set config to [content02] folder on [RX-8.bizantum.lab] site. Select target folder on the left pane and click to open [IP Address and Domain Ristrictions] on the center pane, then following windows is shown. Change default [allow all] setting on here, Click [Edit feature setting] on the right pane.
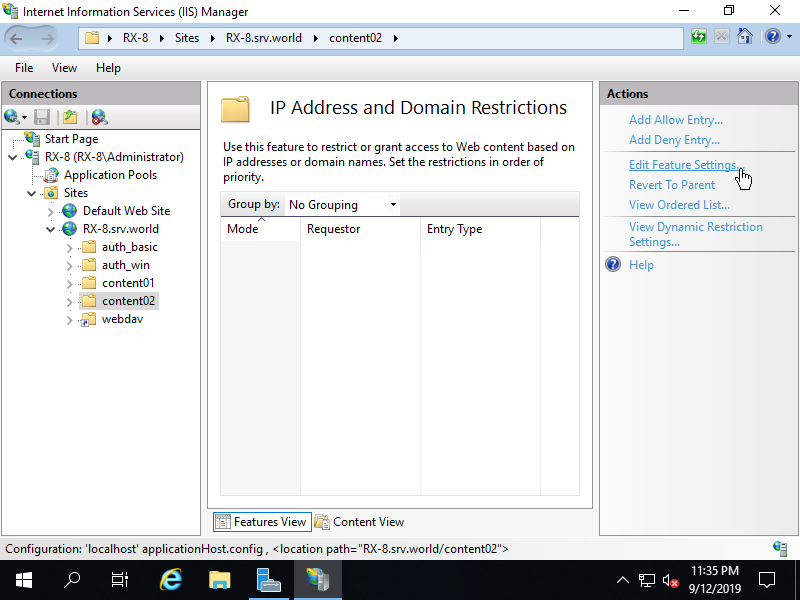
Step [10]Change to [Deny] on [Access for unspecified clients] field. By this change, default setting turns to [deny all].
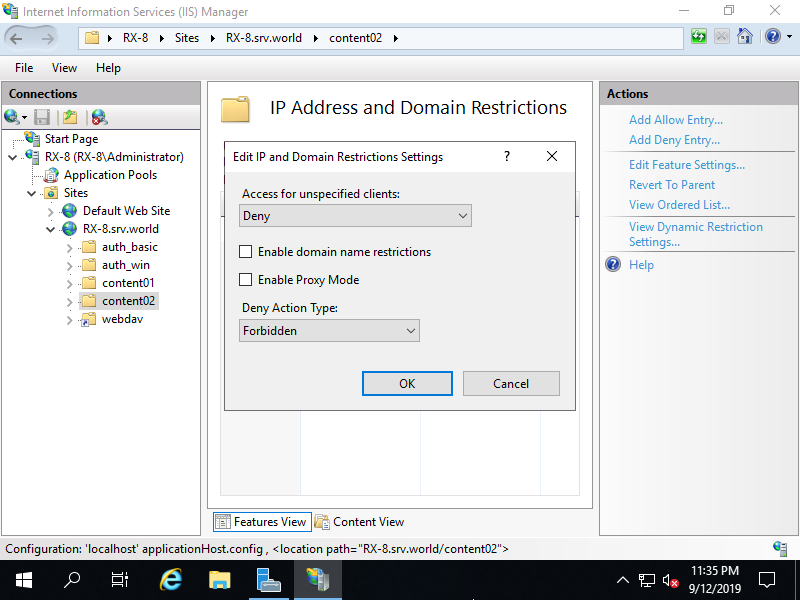
Step [11]Click [Add Allow Entry] on the right pane.
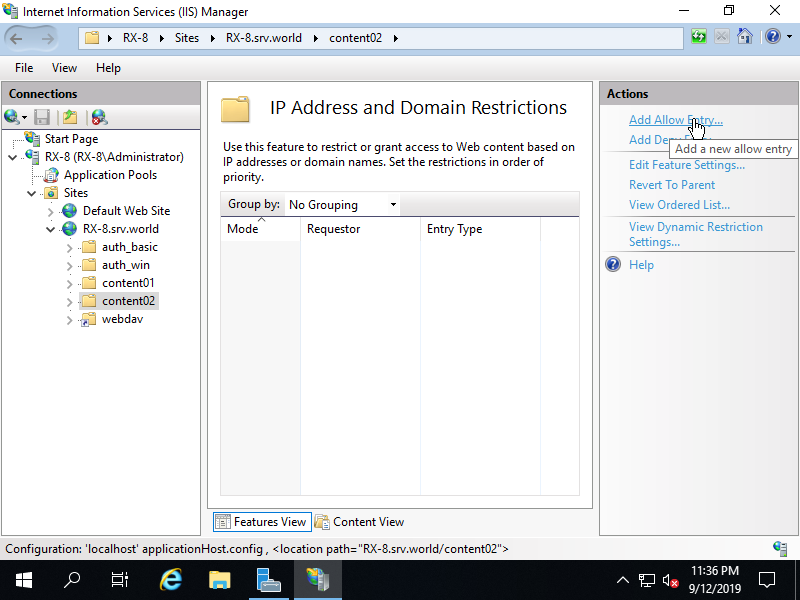
Step [12]Input an IP address on [Specific IP address] field, or IP address range on [IP address range]. On this example, set [10.0.0.240/255.255.255.240] range to allow from them.
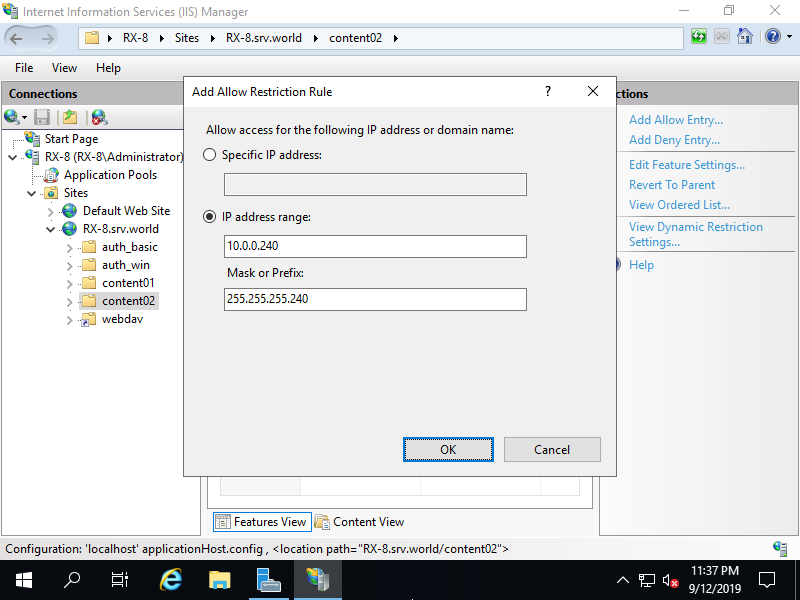
Step [13]After setting, entries are displayed. If you'd like to add more, possible to add with the same operation.
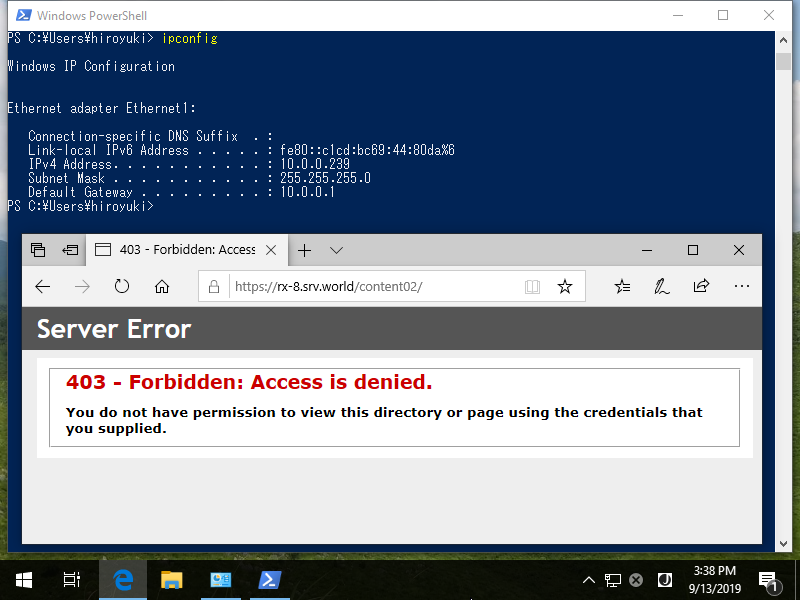
Step [14]After setting, verify working normally to access from denied computer and allowed computer. The example below shows that source computer that has [10.0.0.239] accessed to IIS site and he was denied as settings.
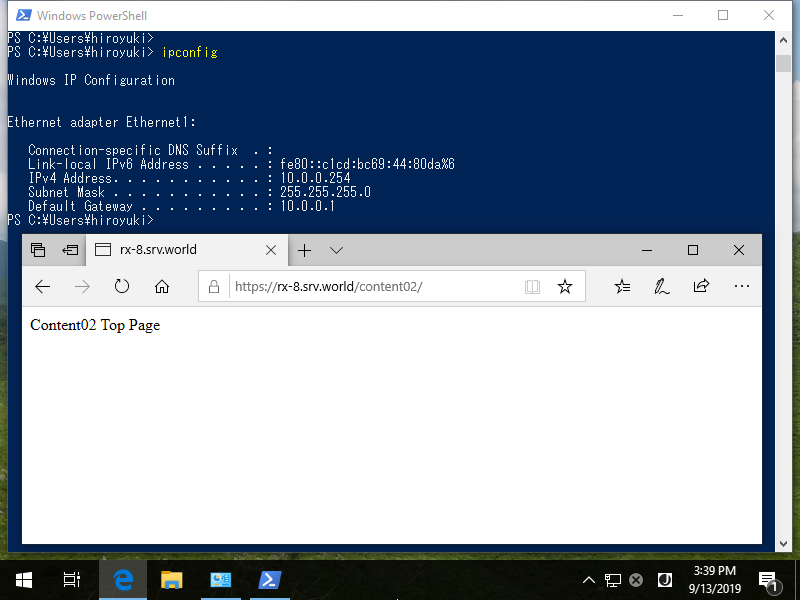
Step [15]The example below shows that source computer that has [10.0.0.254] accessed to IIS site and he could access to it as allow settings.
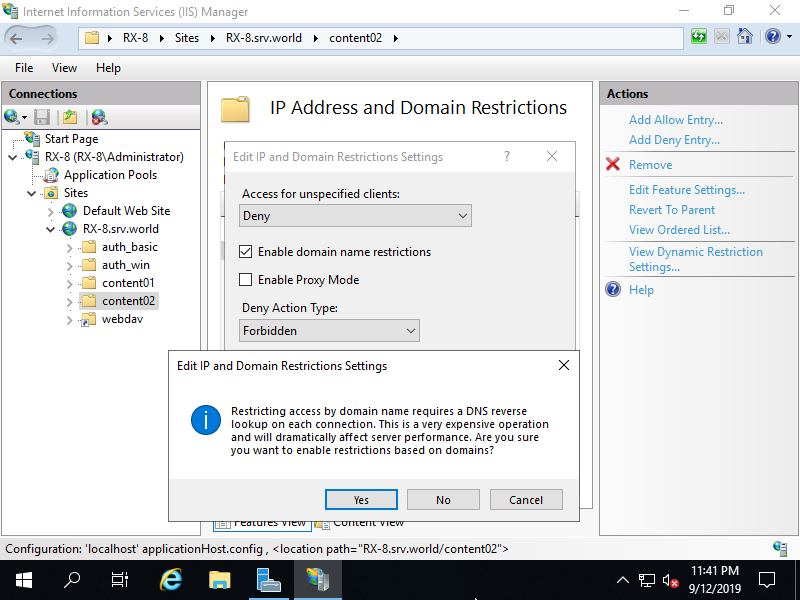
Step [16]By the way, it's possbile to set domain name based restrictions, too. However, for the screen like below, it is not recommended.
Use Python scripts
Configure IIS to be able to use Python scripts.
Step [1]Install Python, refer to here.
Using Command Line Interface (CLI)
Step [2]Run PowerShell with Admin Privilege and Configure.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# Install CGI and ISAPI extension feature
PS C:\Users\Administrator> Install-WindowsFeature Web-CGI,Web-ISAPI-Ext
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {Application Development, CGI, ISAPI Exten...
# restart IIS
PS C:\Users\Administrator> Restart-Service W3SVC
PS C:\Users\Administrator> Get-Website
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
Default Web Site 1 Started %SystemDrive%\inetpub\wwwroot http *:80:
RX-7.bizantum.lab 2 Started C:\inetpub\newsite http *:80:RX-7.bizantum.lab
https *:443:rx-7.bizantum.lab sslFlags=0
PS C:\Users\Administrator> Get-ChildItem C:\inetpub\newsite
Directory: C:\inetpub\newsite
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/11/2019 7:09 PM content01
d----- 9/11/2019 7:09 PM content02
-a---- 9/9/2019 1:27 AM 28 index.html
# add Python to ISAPI/CGI extension
PS C:\Users\Administrator> Add-WebConfiguration -Filter '/system.webServer/security/isapiCgiRestriction' -Value @{description="Python";path="C:\Program Files\Python37\python.exe %s %s";allowed="true"}
# for example, set [*.py] scripts as executable under [content01] folder on [RX-7.bizantum.lab] site
PS C:\Users\Administrator> Set-WebConfigurationProperty -Filter '/system.webServer/handlers' -Location "RX-7.bizantum.lab/content01" -Name accessPolicy -Value "Read, Script"
PS C:\Users\Administrator> Add-WebConfiguration -Filter '/system.webServer/handlers' -Location "RX-7.bizantum.lab/content01" -Value @{name="Python Interpreter";path="*.py";verb="*";modules="CgiModule";scriptProcessor="C:\Program Files\Python37\python.exe %s %s";resourceType="File"}
# restart Web site
PS C:\Users\Administrator> Restart-WebItem -PSPath 'IIS:\Sites\RX-7.bizantum.lab'
# create test script
PS C:\Users\Administrator> $str_document = @'
print("Content-type: text/html\n\n")
print("Python Script Test Page on IIS")
'@
PS C:\Users\Administrator> Write-Output $str_document | Out-File C:\inetpub\newsite\content01\test.py -Encoding Default
# verify to access
PS C:\Users\Administrator> curl.exe https://rx-7.bizantum.lab/content01/test.py
Python Script Test Page on IIS
Using Graphical User Interface (GUI)
Step [3]Run [Start] - [Server Manager] and enter [Add roles and features], then check a box [CGI] and [ISAPI Extensions] and install them.
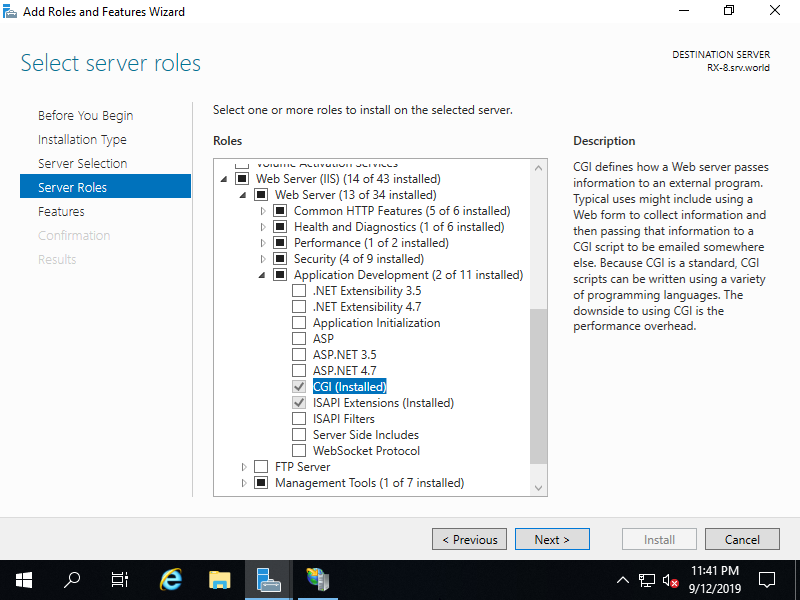
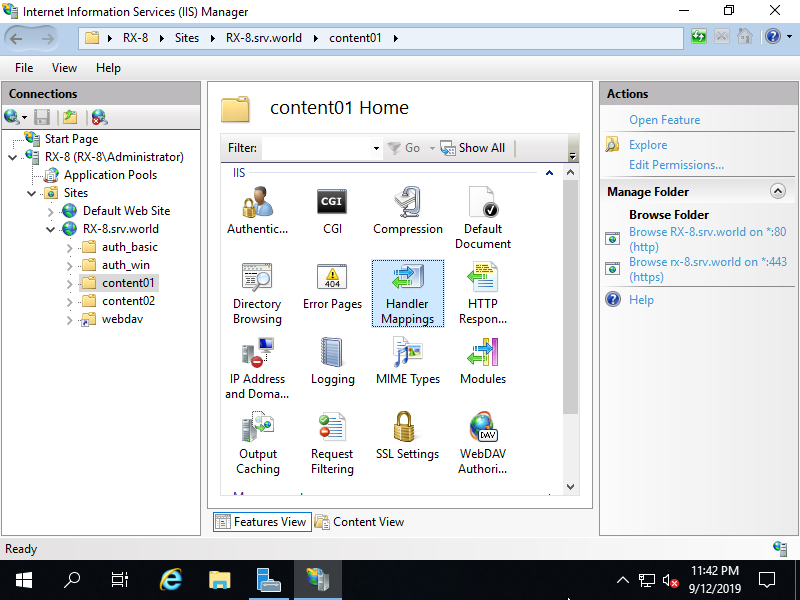
Step [4]For example, set [*.py] scripts as executable under [content01] folder on [RX-7.bizantum.lab] site. Select target folder on the left pane and Open [Handler Mappings] on the center pane.
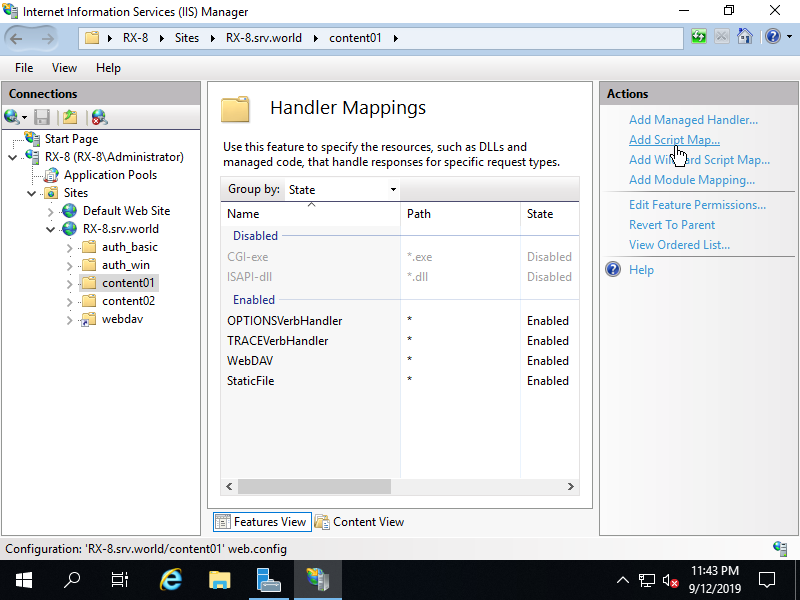
Step [5]Click [Add Script Map] on th right pane.
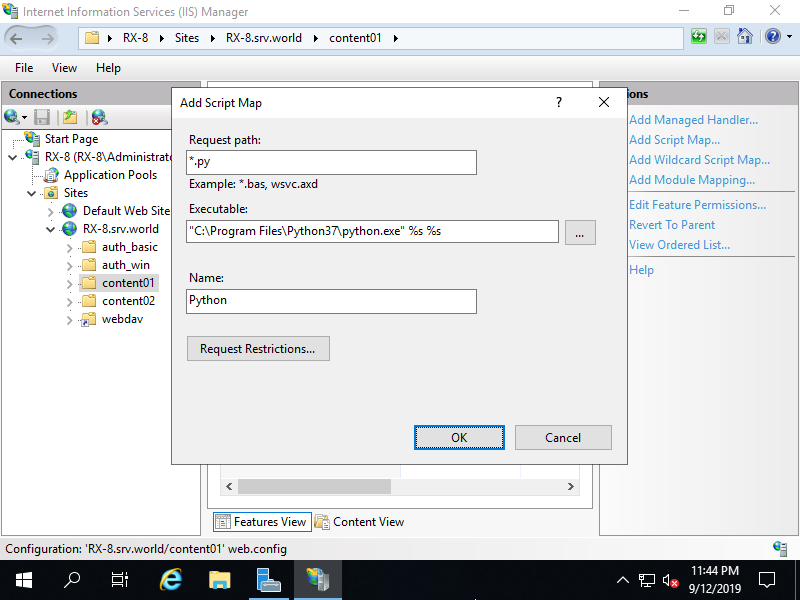
Step [6]For the [Name] field, input any name you like, for other fields, input like follows. (but your Python path is different, replace to your path)
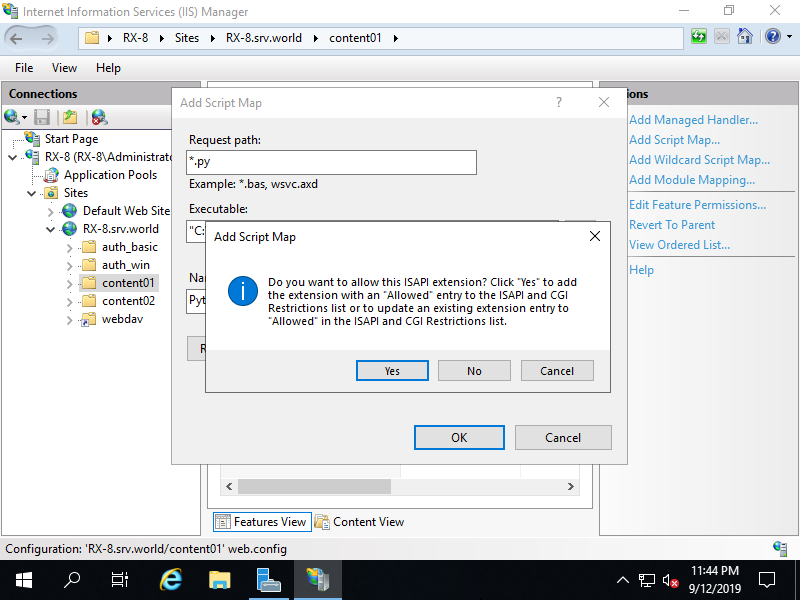
Step [7]Click [Yes].
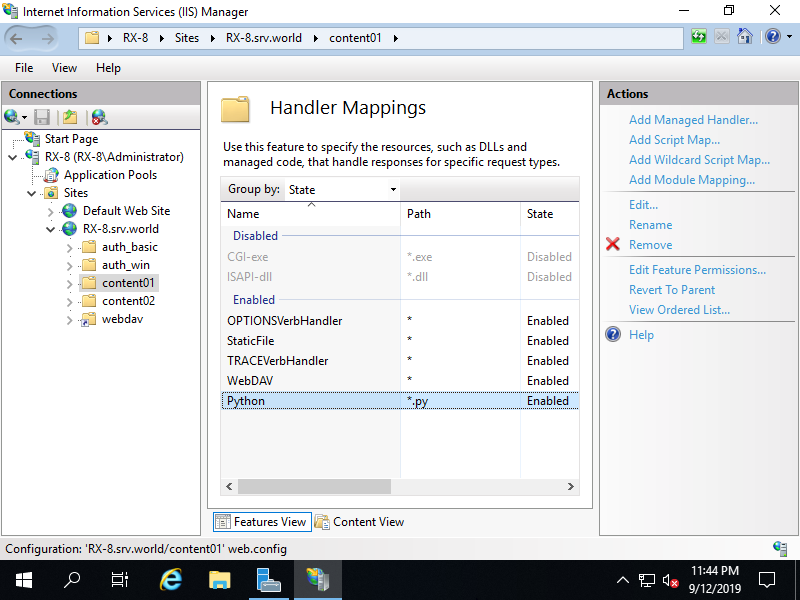
Step [8][*.py] handler mapping has been added.
Step [9]Create a Python test script to verify setting.

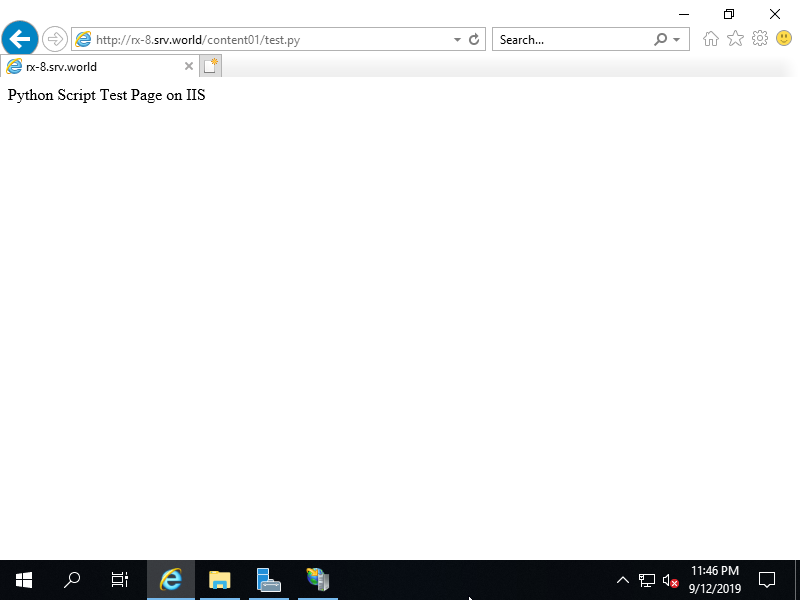
Step [10]Access to the test script to verify working.
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.