
Introduction
In this article, we will explore the what, who, where, when, why, and how of File Transfer Protocol (FTP) functionality on the Windows Server 2019 platform, so let's get started.
Overview
FTP (File Transfer Protocol) is a standard network protocol used to transfer files from one host to another over a TCP-based network, such as the Internet.
What
FTP is a protocol used for transferring files between a client and a server on a computer network. It allows users to upload, download, delete, rename, move, and copy files on a server.
Who
FTP is used by a variety of users, including web developers, system administrators, and individuals who need to transfer files over the internet. It is also used by businesses to exchange files securely with clients and partners.
Where
FTP is commonly used in web hosting environments, cloud storage services, and enterprise networks. It can be accessed via FTP clients, web browsers, or command-line interfaces.
When
FTP has been in use since the early 1970s, making it one of the oldest protocols still in use today. It has evolved over the years to include various security enhancements, such as FTPS (FTP Secure) and SFTP (SSH File Transfer Protocol).
Why
Understanding the pros and cons of FTP can provide insight into its suitability for various use cases.
| Pros | Cons |
|---|---|
| Widely supported and used | Lacks encryption in standard FTP |
| Simple to set up and use | Can be insecure if not properly configured |
| Supports large file transfers | Not suitable for transferring sensitive data without additional security measures |
How
Here is a basic workflow to use FTP:
| Step 1 | Install an FTP client or use a command-line interface with FTP capabilities |
| Step 2 | Connect to the FTP server using the server address, username, and password |
| Step 3 | Transfer files by uploading or downloading them to/from the server |
Consequences
The use of FTP brings various positive and negative consequences:
| Positive |
|
| Negative |
|
Conclusion
FTP remains a widely used and supported protocol for file transfers, offering simplicity and efficiency. However, it also presents security challenges, particularly in its standard, non-encrypted form. To mitigate risks, users should consider using secure versions like FTPS or SFTP and ensure proper configurations. Overall, FTP is a valuable tool for many file transfer needs, but caution is advised when handling sensitive data.
Install and Pre-Configure
Install FTP Server to transfer files.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Install FTP Server.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# install FTP Server with admin tools
PS C:\Users\Administrator> Install-WindowsFeature Web-FTP-Server -IncludeManagementTools
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {FTP Server, FTP Service, IIS Management C...
Using Graphical User Interface (GUI)
Step [2]Run Server Manager and Click [Add roles and features].
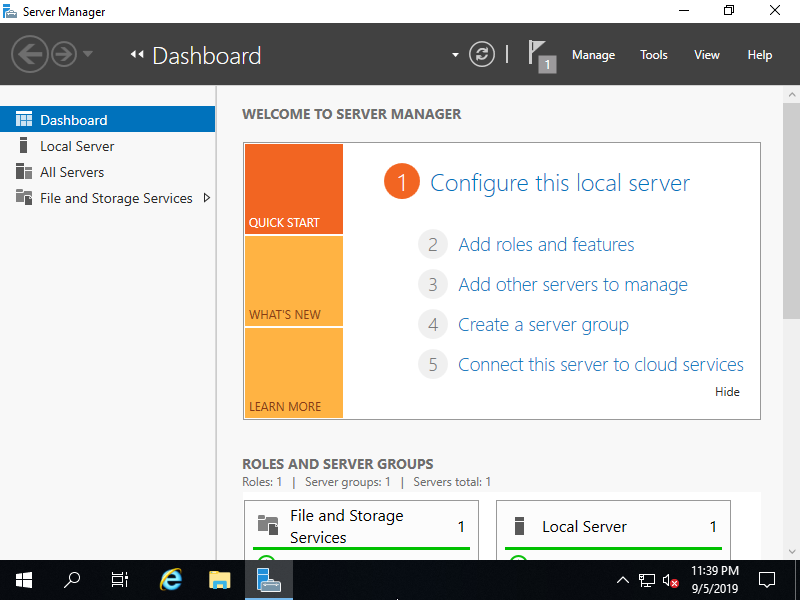
Step [3]Click [Next] button.
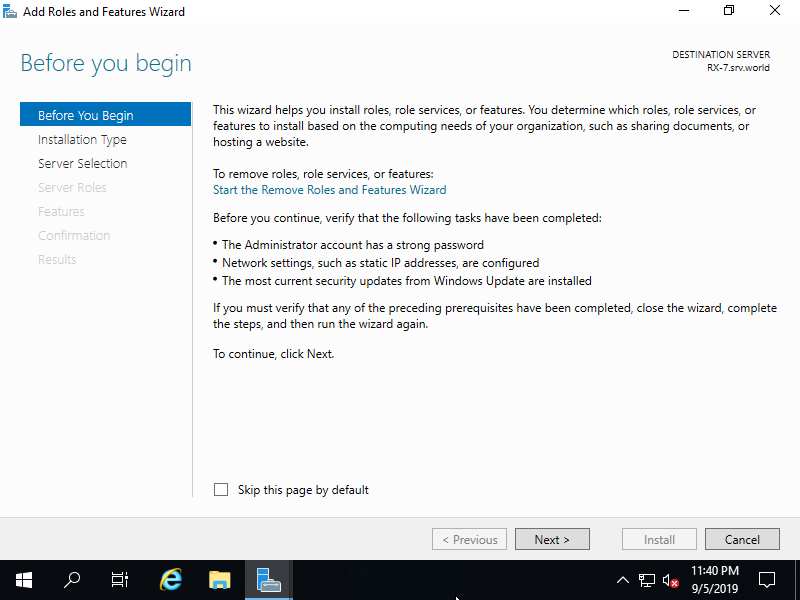
Step [4]Select [Role-based or feature-based installation].
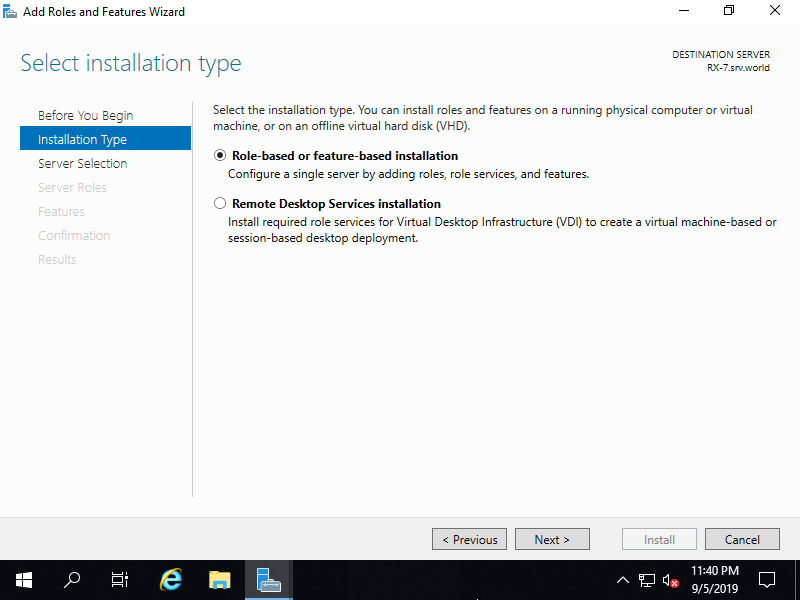
Step [5]Select a Host which you'd like to add services.
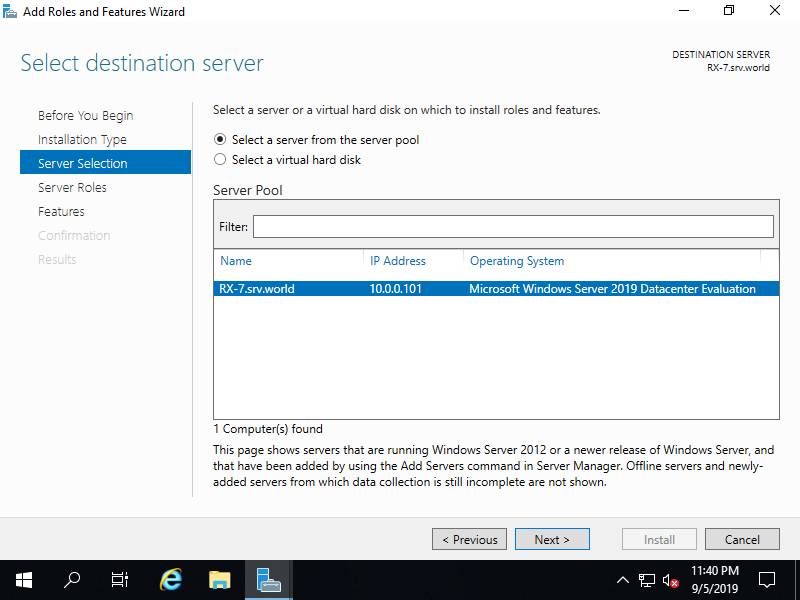
Step [6]Check a box [Web Server (IIS)]. (FTP Server feature is included in Web Server (IIS) features).
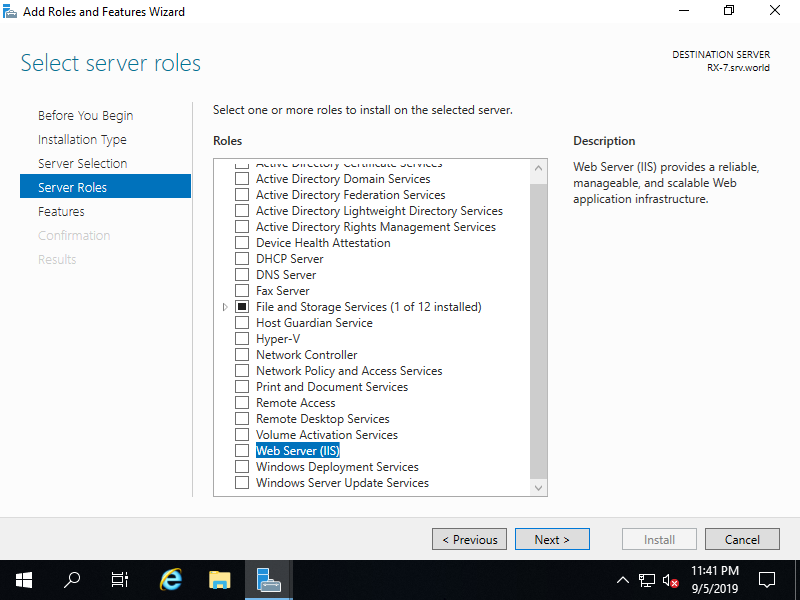
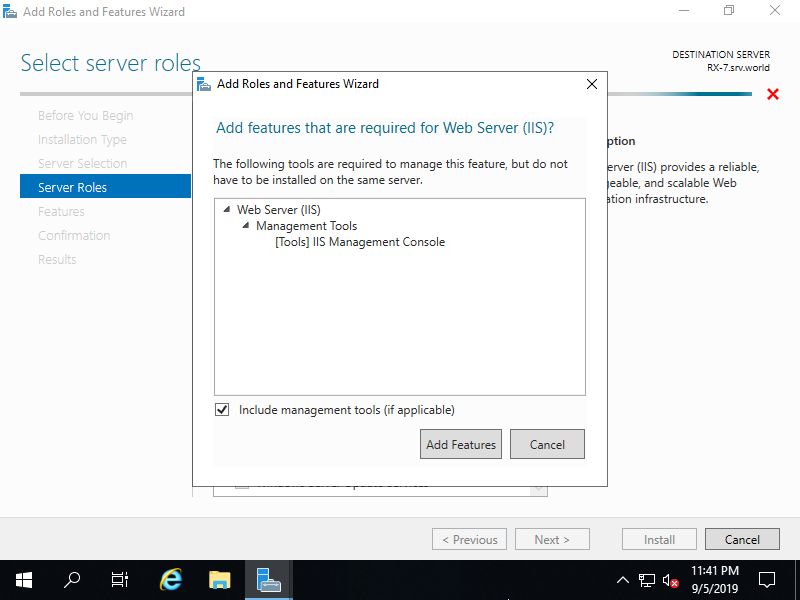
Step [7]Addtional features are required to add IIS Server. Click [Add Features] button and then Click [Next] button.
Step [8]Click [Next] button.
Step [9]Click [Next] button.
Step [10]This is the section to select Web Server features. Check a box [FTP Server] like follows.
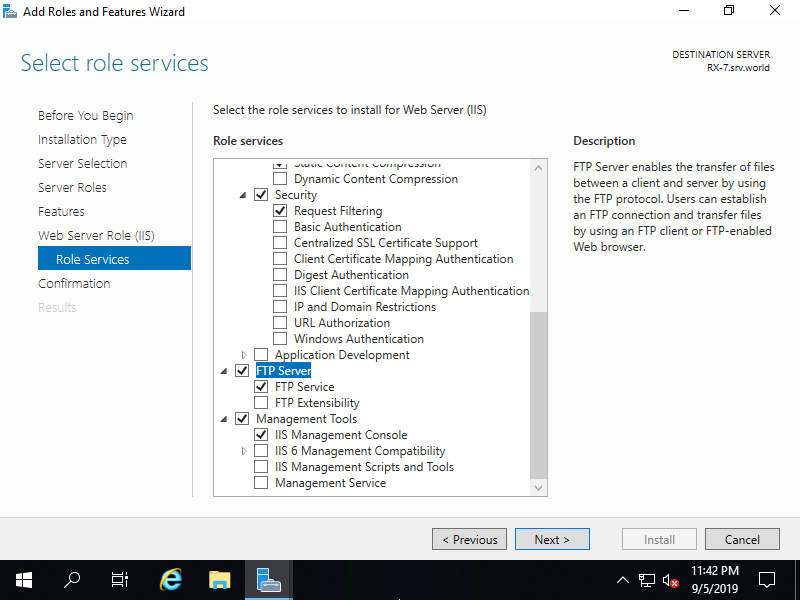
Step [11]Click [Install] button.
Step [12]After finishing Installation, click [Close] button.
Configure Passive Mode
On this example, it shows to configure FTP Server with Passive Mode.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure FTP Service.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# set the port range you use for passive mode
# specify any range that FTP Server Host does not use
# example below sets 60000 - 60100 range
PS C:\Users\Administrator> Set-WebConfiguration "/system.ftpServer/firewallSupport" -PSPath "IIS:\" -Value @{lowDataChannelPort="60000";highDataChannelPort="60100";}
# confirm
PS C:\Users\Administrator> Get-IISConfigSection -SectionPath "system.ftpServer/firewallSupport"
IsLocked : False
OverrideMode : Inherit
OverrideModeEffective : Deny
SectionPath : system.ftpServer/firewallSupport
Attributes : {lowDataChannelPort, highDataChannelPort}
ChildElements : {}
ElementTagName : system.ftpServer/firewallSupport
IsLocallyStored : True
Methods :
RawAttributes : {[lowDataChannelPort, 60000], [highDataChannelPort, 60100]}
Schema : Microsoft.Web.Administration.ConfigurationElementSchema
#restart FTP Service
PS C:\Users\Administrator> Restart-Service ftpsvc
# allow passive ports you set and also 21 port FTP Server uses on Windows firewall
PS C:\Users\Administrator> New-NetFirewallRule `
-Name "FTP Server Port" `
-DisplayName "FTP Server Port" `
-Description 'Allow FTP Server Ports' `
-Profile Any `
-Direction Inbound `
-Action Allow `
-Protocol TCP `
-Program Any `
-LocalAddress Any `
-LocalPort 21,60000-60100
Name : FTP Server Port
DisplayName : FTP Server Port
Description : Allow FTP Server Ports
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Inbound
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : NotApplicable
PolicyStoreSource : PersistentStore
PolicyStoreSourceType : Local
Using Graphical User Interface (GUI)
Step [2]Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager].
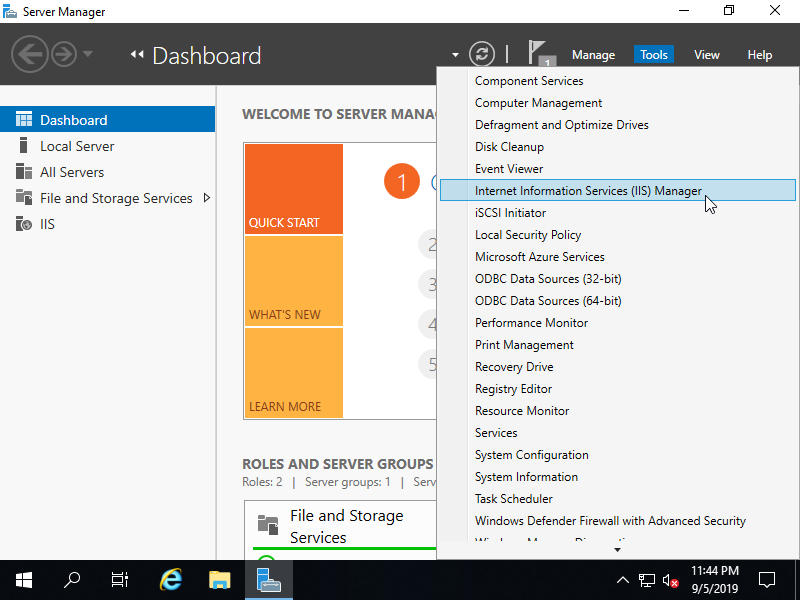
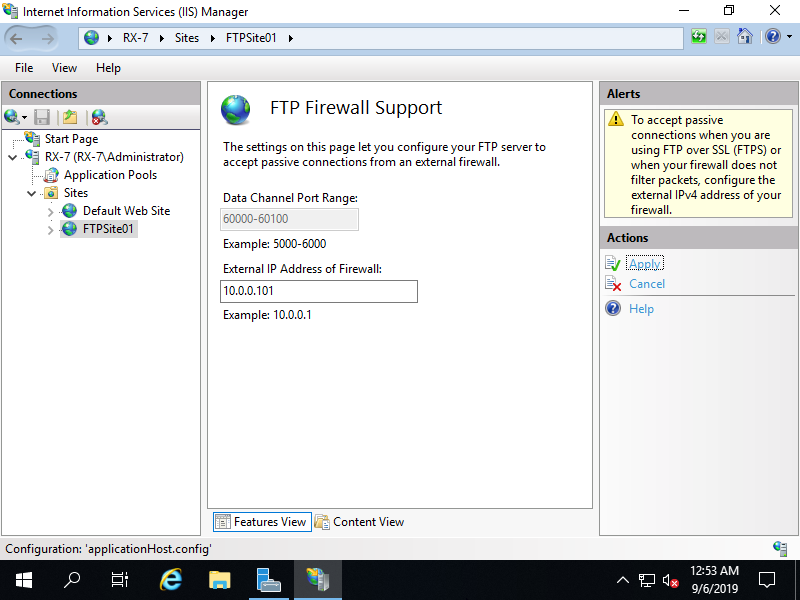
Step [3]Select Hostname on the left pane and Click [FTP Firewall Support] on the center pane.
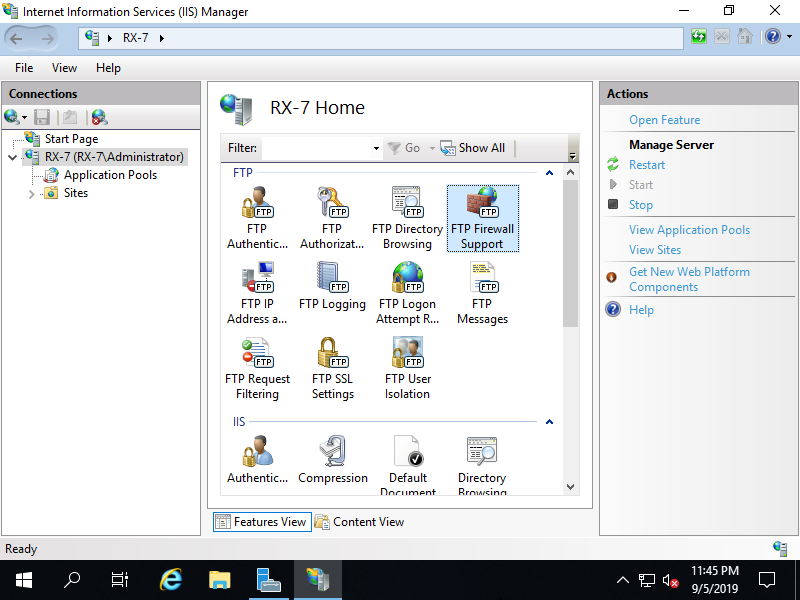
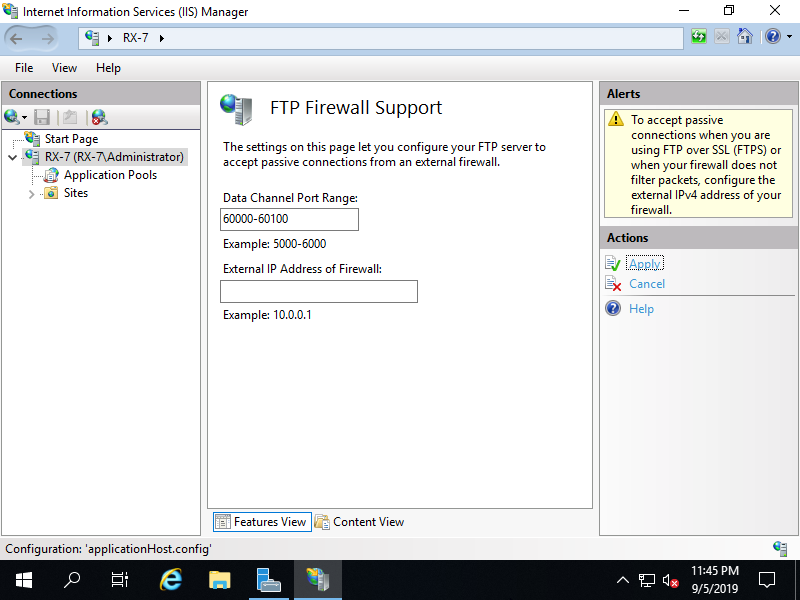
Step [4]Input port range for [Data Channel Port Range] section. Specify any range that FTP Server Host does not use. (example below sets 60000 - 60100 range).
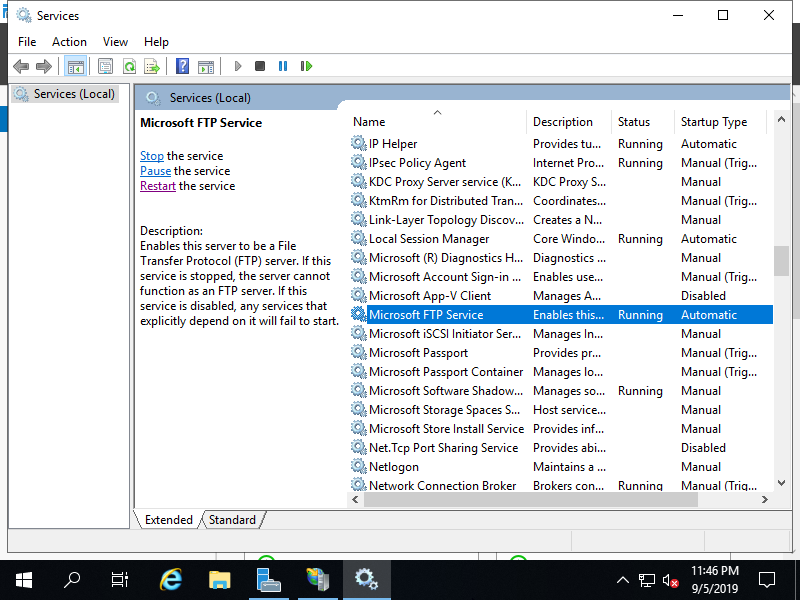
Step [5]Open [Server Manager] - [Tools] - [Services] and restart FTP Service to apply changes.
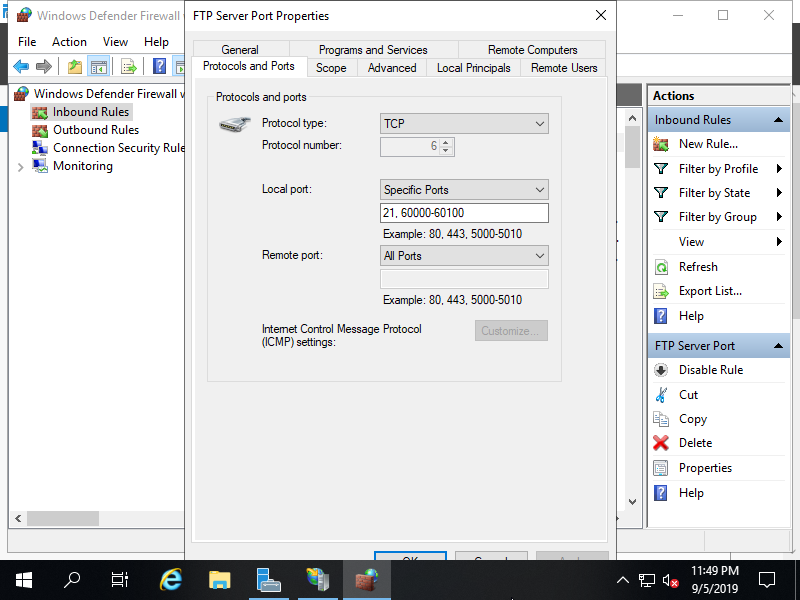
Step [6]Open [Server Manager] - [Tools] - [Windows Defender Firewall with Advanced Security] and add inbound rule to allow passibe ports you set and also 21 port FTP Service uses like follows.
Configure FTP Site
Setup on FTP Server
Add FTP Site to use FTP file transfer from Client computers. For example, Configure FTP site to create a local group [FTPGroup] and add local users you allow to use FTP to the group, and also grant read and write authority to the group.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure FTP Service.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# add a group [FTPGroup] for FTP
PS C:\Users\Administrator> New-LocalGroup -Name "FTPGroup"
Name Description
---- -----------
FTPGroup
# add users to the [FTPGroup] you allow to use FTP
# add [Bizantum] user to [FTPGroup] as an example below
PS C:\Users\Administrator> Add-LocalGroupMember -Group "FTPGroup" -Member "Bizantum"
# confirm
PS C:\Users\Administrator> Get-LocalGroupMember -Name "FTPGroup"
ObjectClass Name PrincipalSource
----------- ---- ---------------
User FTP07\Bizantum Local
# add FTP site
# -Name [any name you like]
# -IPAddress [listening IP address] (below is 0.0.0.0 (all))
# -Port [listening port]
PS C:\Users\Administrator> New-WebFtpSite -Name "FTPSite01" -IPAddress "*" -Port 21
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
FTPSite01 2 Started ftp *:21:
# set physical folder that is used for FTP site
# example below, create a [FTPSite01] folder under the [C:\inetpub\ftproot] that is created by default and set it
PS C:\Users\Administrator> mkdir 'C:\inetpub\ftproot\FTPSite01'
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name physicalPath -Value 'C:\inetpub\ftproot\FTPSite01'
# allow no SSL/TLS connection
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.security.ssl.controlChannelPolicy -Value "SslAllow"
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.security.ssl.dataChannelPolicy -Value "SslAllow"
# set basic authentication
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.security.authentication.basicAuthentication.enabled -Value $true
# set read and write authority to [FTPGroup] group
PS C:\Users\Administrator> Add-WebConfiguration "/system.ftpServer/security/authorization" -Location FTPSite01 -PSPath IIS:\ -Value @{accessType="Allow";roles="FTPGroup";permissions="Read,Write"}
# set external IP address (the one client computers can connect)
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.firewallSupport.externalIp4Address -Value "10.0.0.101"
# set NTFS access authority to the physical folder
# example below, add full control
PS C:\Users\Administrator> icacls "C:\inetpub\ftproot\FTPSite01" /grant "FTPGroup:(OI)(CI)(F)"
processed file: C:\inetpub\ftproot\FTPSite01
Successfully processed 1 files; Failed processing 0 files
# restart FTP site
PS C:\Users\Administrator> Restart-WebItem -PSPath 'IIS:\Sites\FTPSite01'
Using Graphical User Interface (GUI)
Step [2]Add a local group and add local users to the group you allow to use FTP site. On this example, Create a [FTPGroup] group and add [Bizantum] user to the group to allow to use FTP site. For creating local user and others, refer to here.
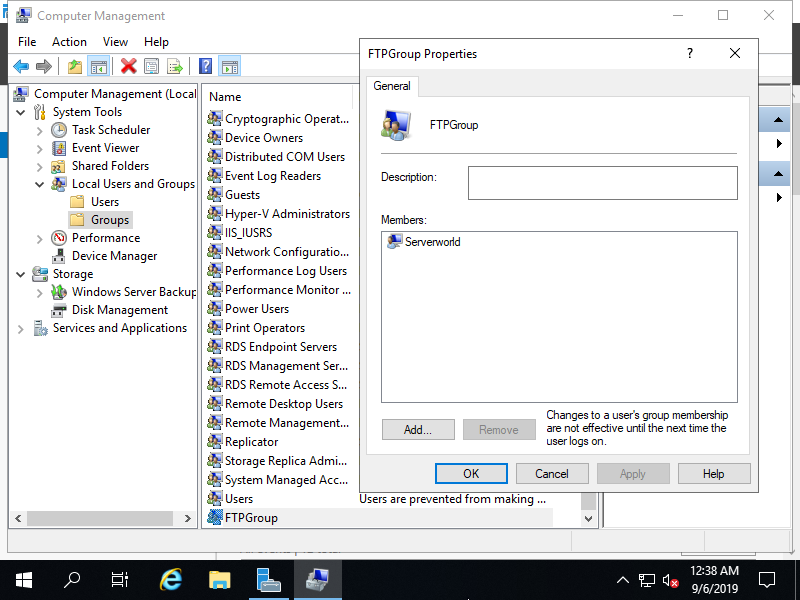
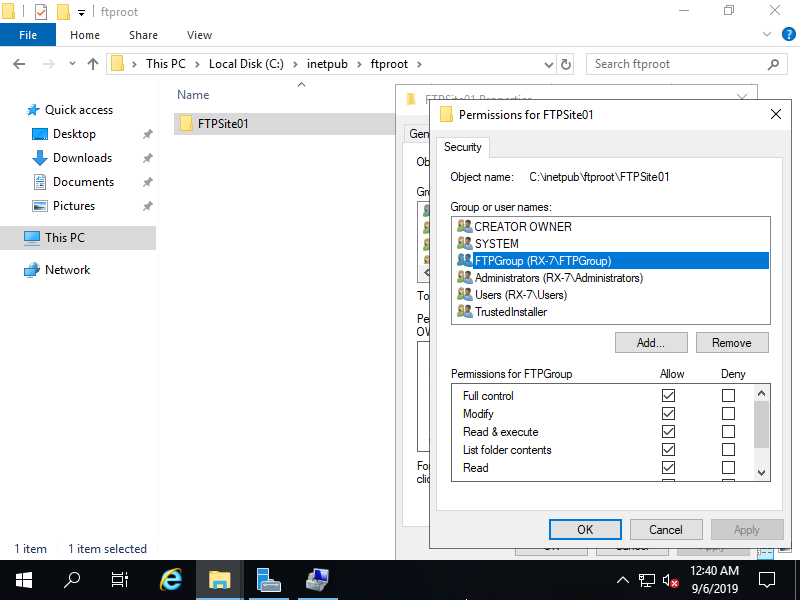
Step [3]Create a physical folder for FTP site's root path and add access authority for the group added on [2] to the folder. On this example, create a [FTPSite01] folder under the [C:\inetpub\ftproot] that is created by default and set it.
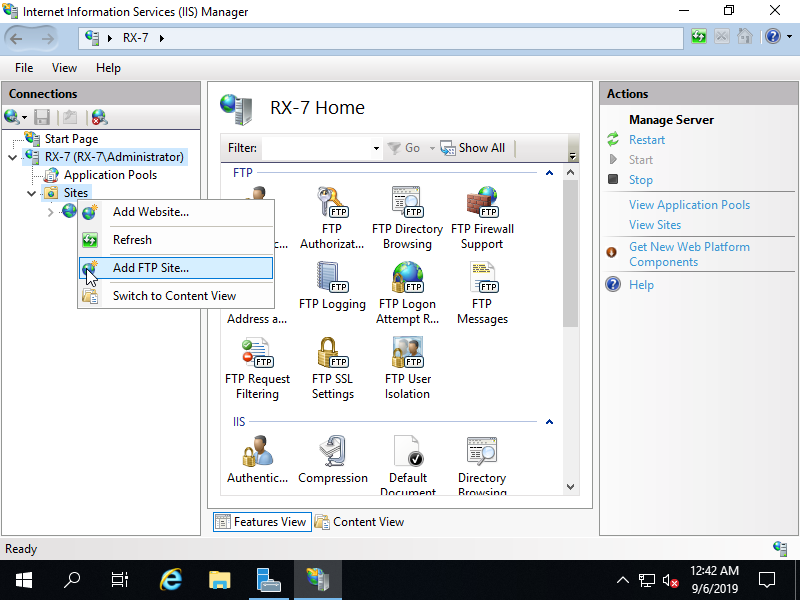
Step [4]Add FTP Site. Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager]. Next, Select the [Site] and right click it, then Open [Add FTP Site].
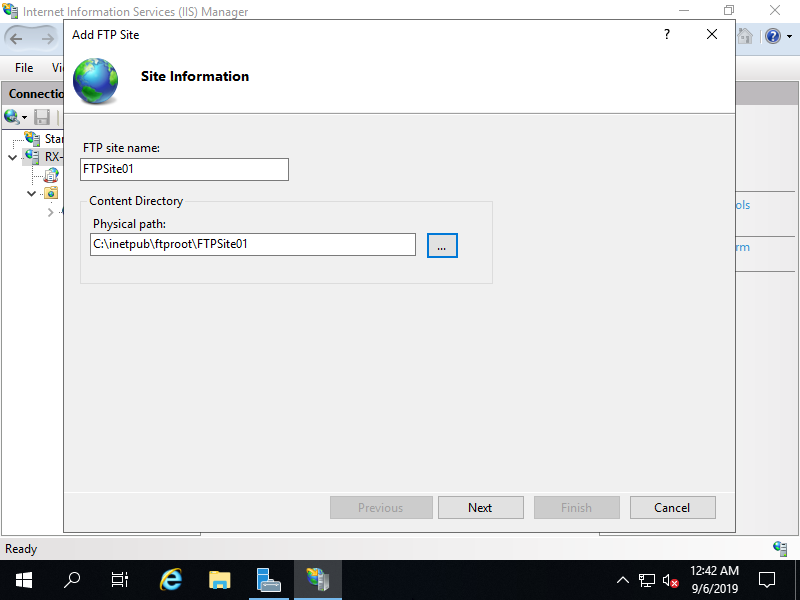
Step [5]Input any name for [FTP site name], specify physical Path for [Physical path] that you added on [3] section.
Step [6]This is Binding setting section. It's OK to keep default for IP Address and Port. For the case of this default setting, FTP service listens on 0.0.0.0:21. For [SSL] section, Select [No SSL] on this example. If you'd like to configure with SSL, refer to here.
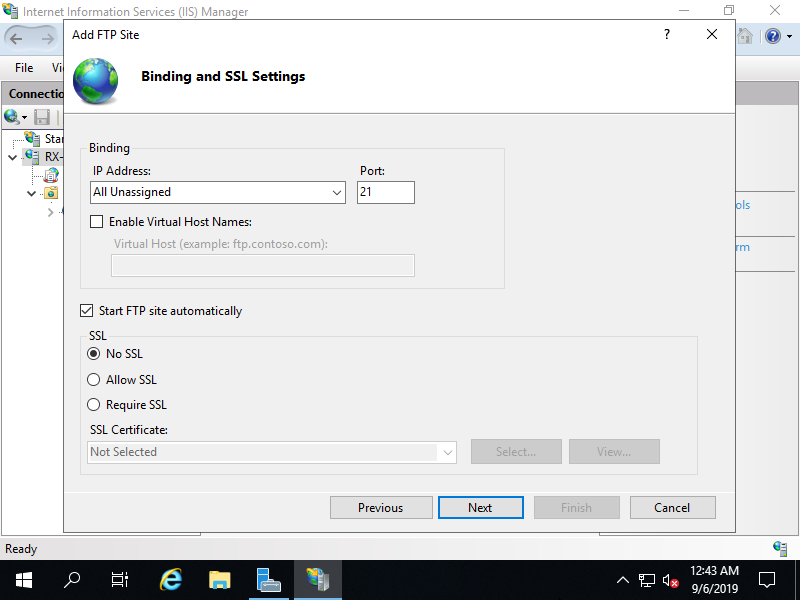
Step [7]This is Authentication and Authorization settings section. On this example, set [Basic] for authentication and [Specified roles or user groups] for Authorization.
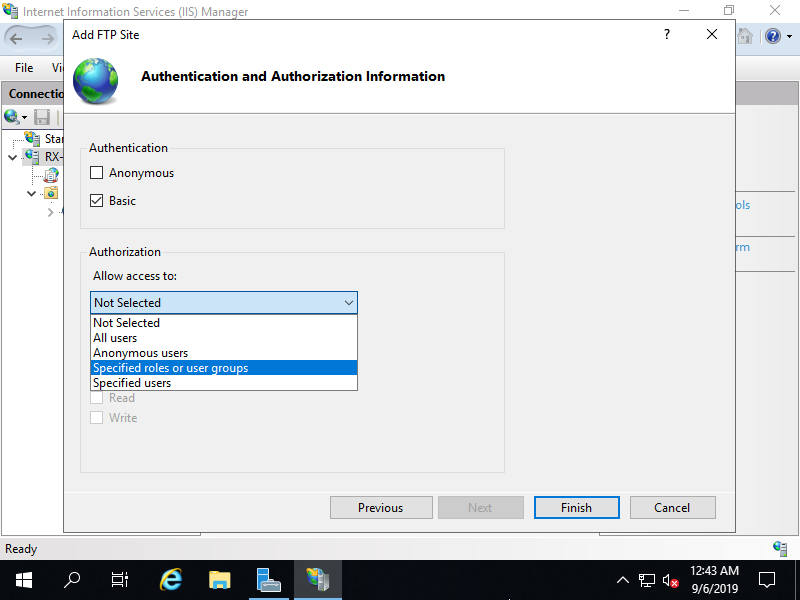
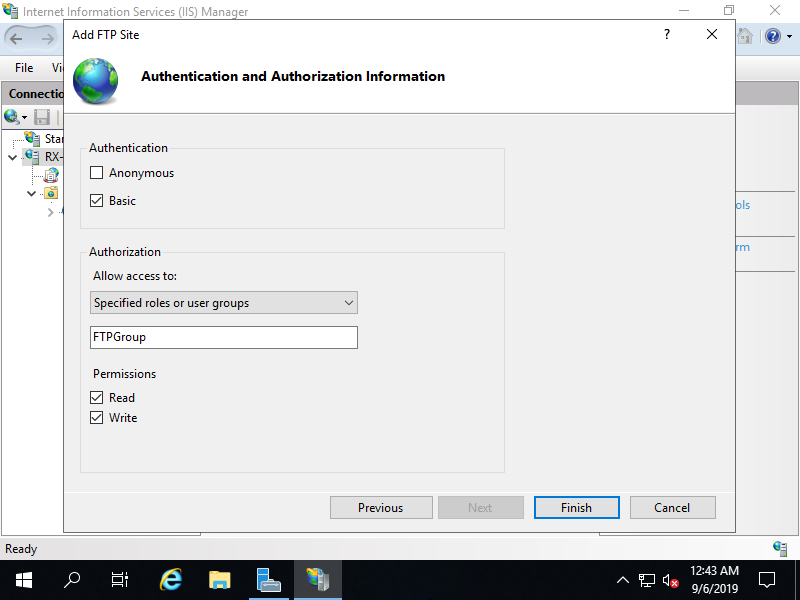
Step [8]For Authorization setting, if selected [Specified roles or user groups], it needs to specify group you allow to access. On this example, set the group created on [2] section.
Step [9]FTP site has been added. Select the new FTP site on the left pane and click [FTP Firewall Support] on center pane.
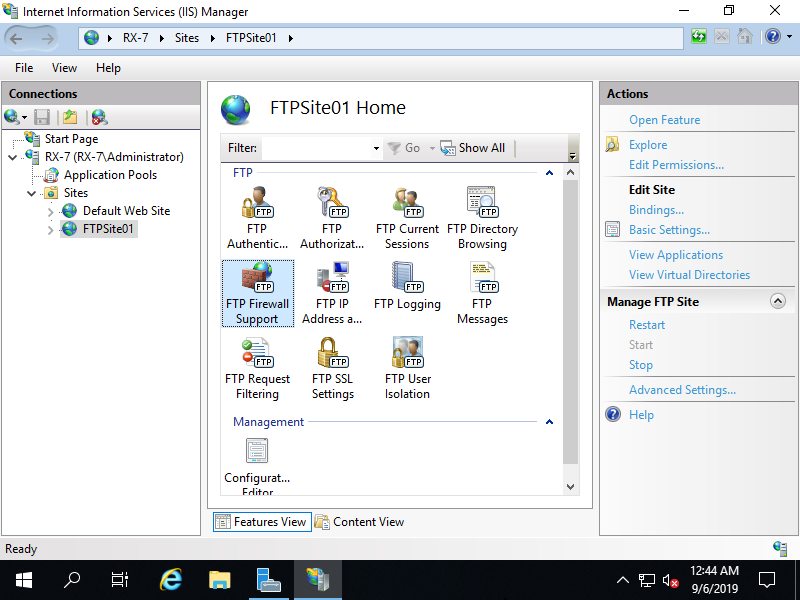
Step [10]Set IP address that client computers can connect to. That's OK to configure FTP site.
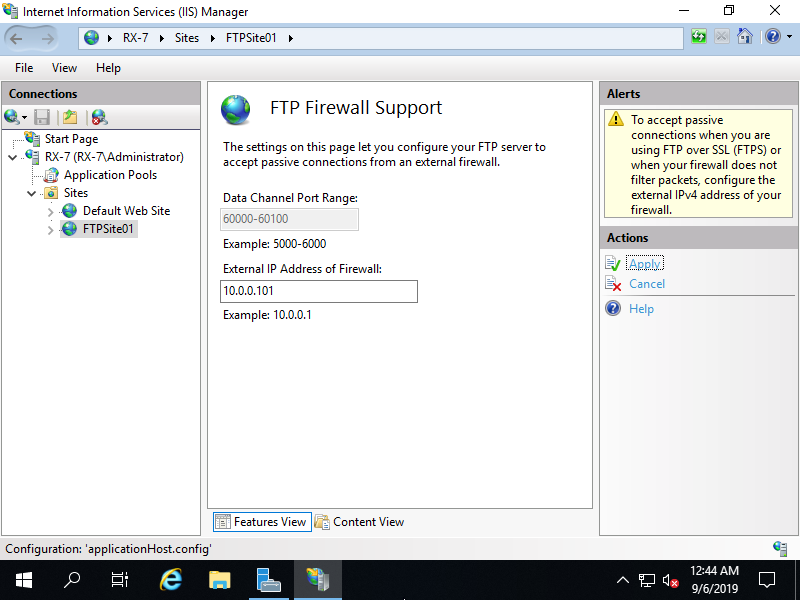
Configure SSL/TLS
Setup on FTP Server
Add FTP Site with enable SSL setting. For example, Configure FTP site with SSL setting to create a local group [FTPGroup] and add local users you allow to use FTP to the group, and also grant read and write authority to the group.
Step [1]Buy or Get or Create SSL certificate first. On this example, create self-signed certificate and use it. for self-signed one. refer to here.
Using Command Line Interface (CLI)
Step [2]Run PowerShell with Admin Privilege and Configure FTP Service.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# add a group [FTPGroup] for FTP
PS C:\Users\Administrator> New-LocalGroup -Name "FTPGroup"
Name Description
---- -----------
FTPGroup
# add users to the [FTPGroup] you allow to use FTP
# add [Bizantum] user to [FTPGroup] as an example below
PS C:\Users\Administrator> Add-LocalGroupMember -Group "FTPGroup" -Member "Bizantum"
# confirm
PS C:\Users\Administrator> Get-LocalGroupMember -Name "FTPGroup"
ObjectClass Name PrincipalSource
----------- ---- ---------------
User FTP07\Bizantum Local
# add FTP site
# -Name [any name you like]
# -IPAddress [listening IP address] (below is 0.0.0.0 (all))
# -Port [listening port]
PS C:\Users\Administrator> New-WebFtpSite -Name "FTPSite01" -IPAddress "*" -Port 21
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
FTPSite01 2 Started ftp *:21:
# set physical folder that is used for FTP site
# example below, create a [FTPSite01] folder under the [C:\inetpub\ftproot] that is created by default and set it
PS C:\Users\Administrator> mkdir 'C:\inetpub\ftproot\FTPSite01'
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name physicalPath -Value 'C:\inetpub\ftproot\FTPSite01'
# set SSL/TLS required
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.security.ssl.controlChannelPolicy -Value "SslRequire"
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.security.ssl.dataChannelPolicy -Value "SslRequire"
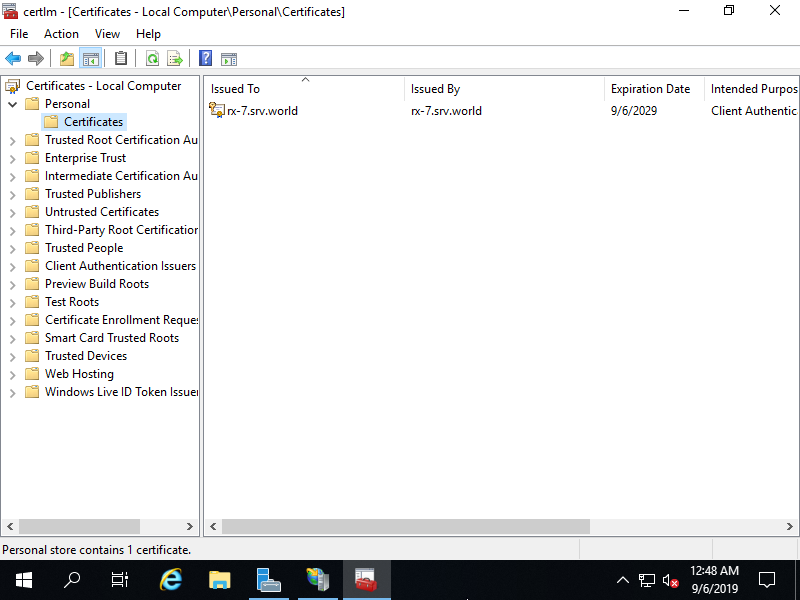
# confirm Thumbprint of certificate
PS C:\Users\Administrator> Get-ChildItem Cert:\LocalMachine\My
PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\My
Thumbprint Subject
---------- -------
560F4FE5B89D70A8CAC5F65B1869C4F8A9274C15 CN=rx-8.bizantum.lab
# add cert store and Thumbprint
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.security.ssl.serverCertStoreName -Value "My"
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.security.ssl.serverCertHash -Value "560F4FE5B89D70A8CAC5F65B1869C4F8A9274C15"
# set basic authentication
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.security.authentication.basicAuthentication.enabled -Value $true
# set read and write authority to [FTPGroup] group
PS C:\Users\Administrator> Add-WebConfiguration "/system.ftpServer/security/authorization" -Location FTPSite01 -PSPath IIS:\ -Value @{accessType="Allow";roles="FTPGroup";permissions="Read,Write"}
# set external IP address (the one client computers can connect)
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPSite01" -Name ftpServer.firewallSupport.externalIp4Address -Value "10.0.0.101"
# set NTFS access authority to the physical folder
# example below, add full control
PS C:\Users\Administrator> icacls "C:\inetpub\ftproot\FTPSite01" /grant "FTPGroup:(OI)(CI)(F)"
processed file: C:\inetpub\ftproot\FTPSite01
Successfully processed 1 files; Failed processing 0 files
# restart FTP site
PS C:\Users\Administrator> Restart-WebItem -PSPath 'IIS:\Sites\FTPSite01'
Using Graphical User Interface (GUI)
Step [3]Add a local group and add local users to the group you allow to use FTP site. On this example, Create a [FTPGroup] group and add [Bizantum] user to the group to allow to use FTP site. For creating local user and others, refer to here.

Step [4]Create a physical folder for FTP site's root path and add access authority for the group added on [2] to the folder. On this example, create a [FTPSite01] folder under the [C:\inetpub\ftproot] that is created by default and set it.

Step [5]Buy ot Get or Create SSL certificate first. On this example, create self-signed certificate and use it. for self-signed one. refer to here.
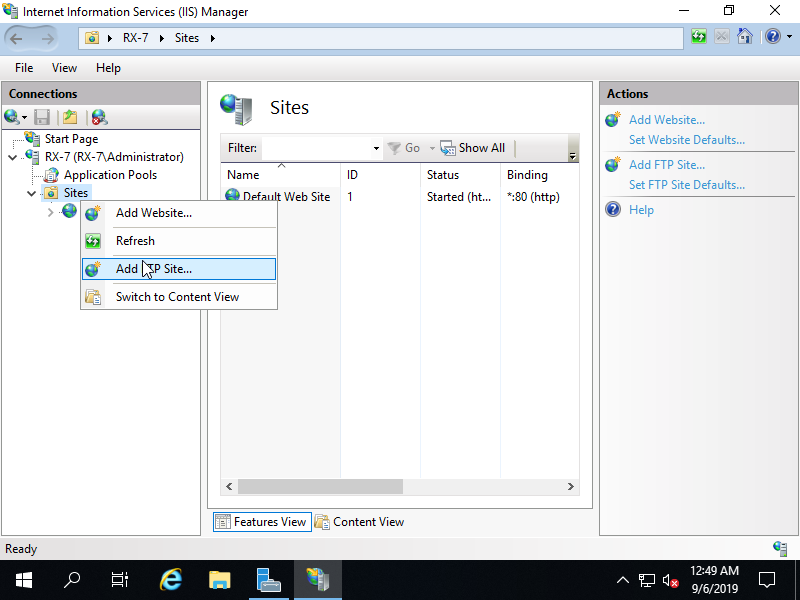
Step [6]Add FTP Site. Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager]. Next, Select the [Site] and right click it, then Open [Add FTP Site].
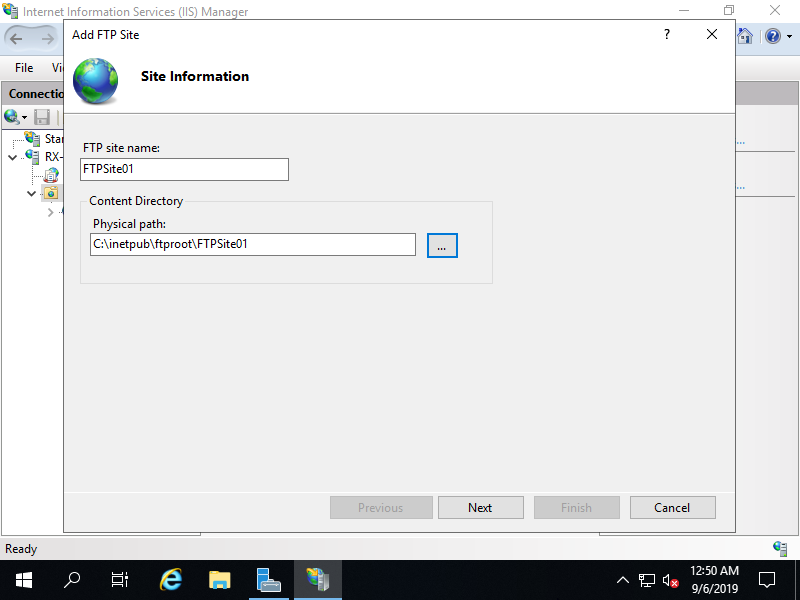
Step [7]Input any name for [FTP site name], specify physical Path for [Physical path] that you added on [3] section.
Step [8]This is Binding and SSL settings section. It's OK to keep default for IP Address and Port. For the case of this default setting, FTP service listens on 0.0.0.0:21. For [SSL] section, Select [Require SSL] and also select your certificate on [SSL Certificate] field.
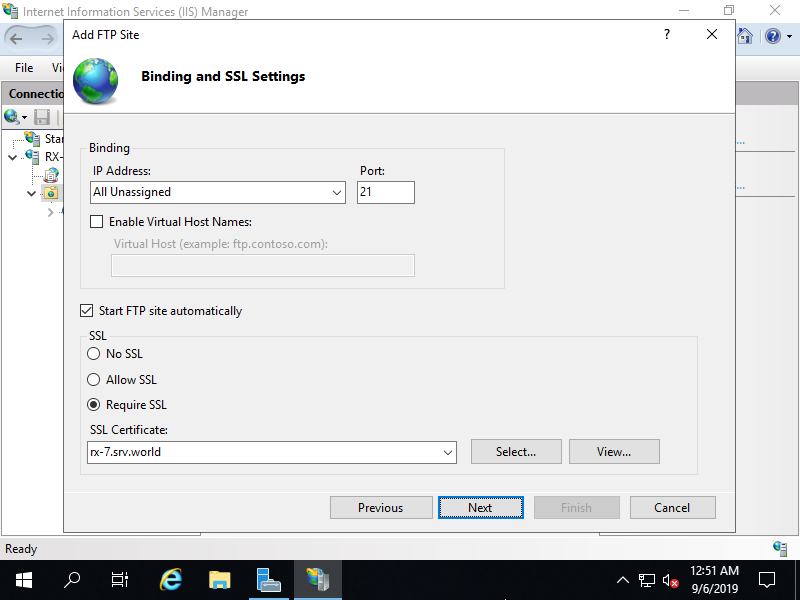
Step [9]This is Authentication and Authorization settings section. On this example, set [Basic] for authentication and [Specified roles or user groups] for Authorization.
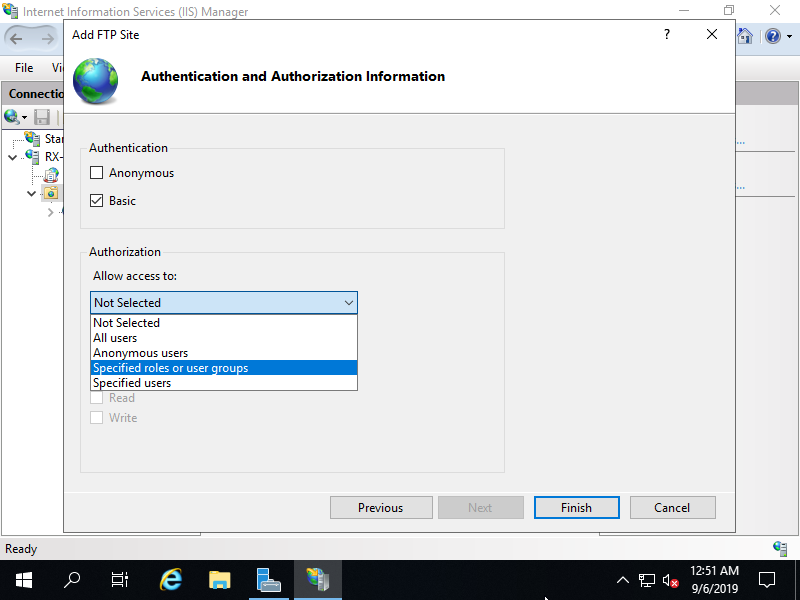
Step [10]For Authorization setting, if selected [Specified roles or user groups], it needs to specify group you allow to access. On this example, set the group created on [2] section.
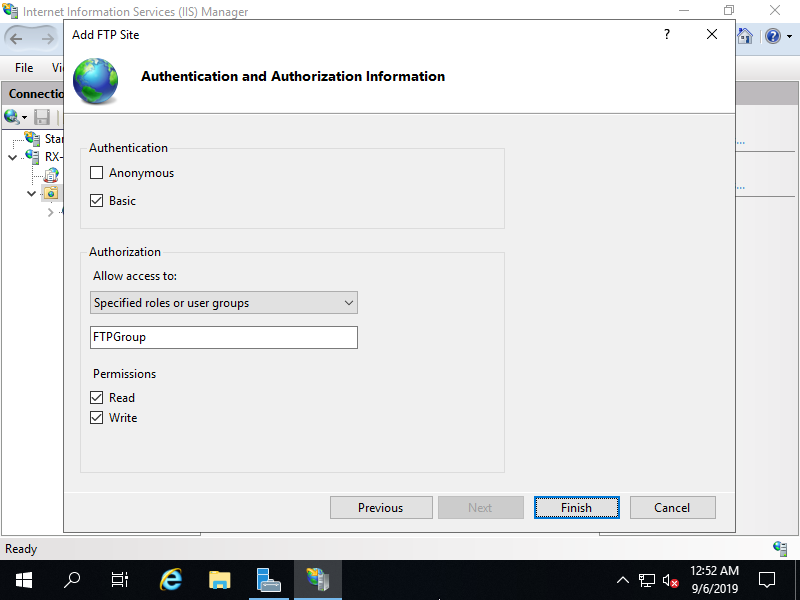
Step [11]FTP site has been added. Select the new FTP site on the left pane and click [FTP Firewall Support] on center pane.
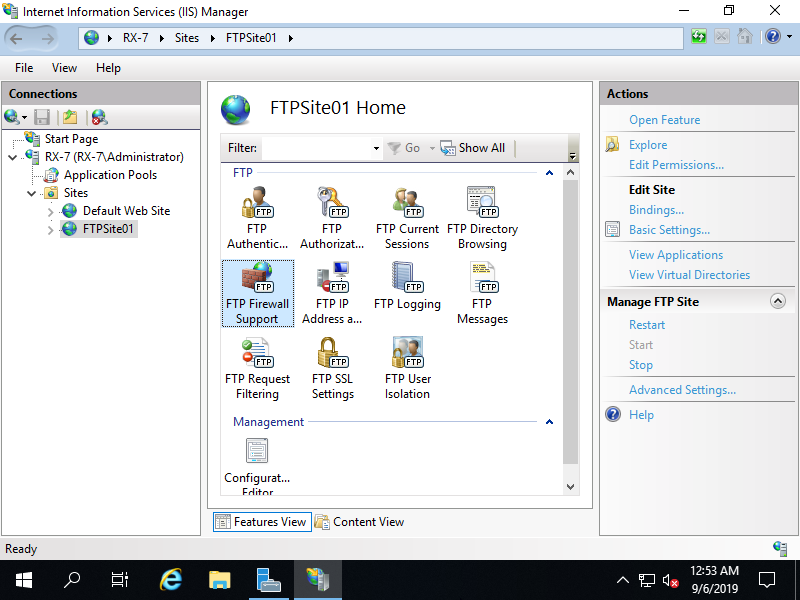
Step [12]Set IP address that client computers can connect to. That's OK to configure FTP site.
Configure FTP Client
Connect to the FTP server from Client Computers. this example is based on the settings FTP Client connects to FTP Server with passive mode. On passive mode connection, client program [ftp] command bundled in Windows 10 or Windows Server 2019 (or old versions) can not use passive mode (even if with [quote pasv]), so it needs to use other FTP Client program. On this example, Use FileZilla.
Step [1]Install FileZilla and run it, then Open [File] - [Site Manager].
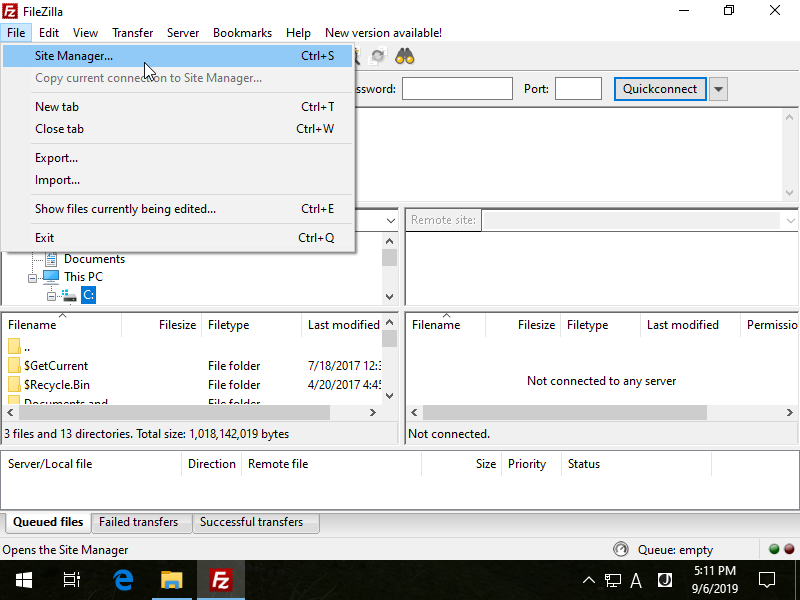
Step [2]Click [New Site] button and input information for FTP connection. For [Host] field, input Hostname or IP address of FTP server. For [Logon Type] filed, select [Ask for password] or other type except [Anonymous].
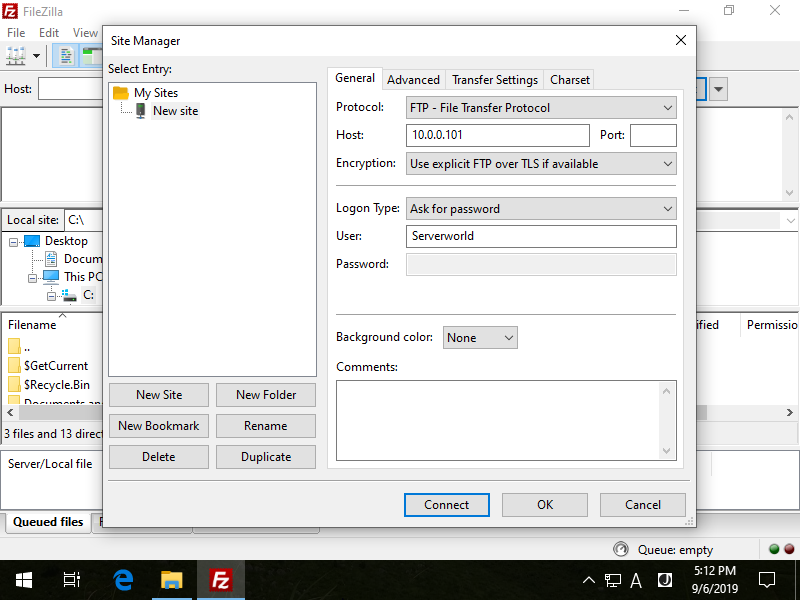
Step [3]Password is required, input it of the connected user.
Step [4]If you use self-signed certificate, following warning is shown because it is self-signed one. Click [OK] to proceed.
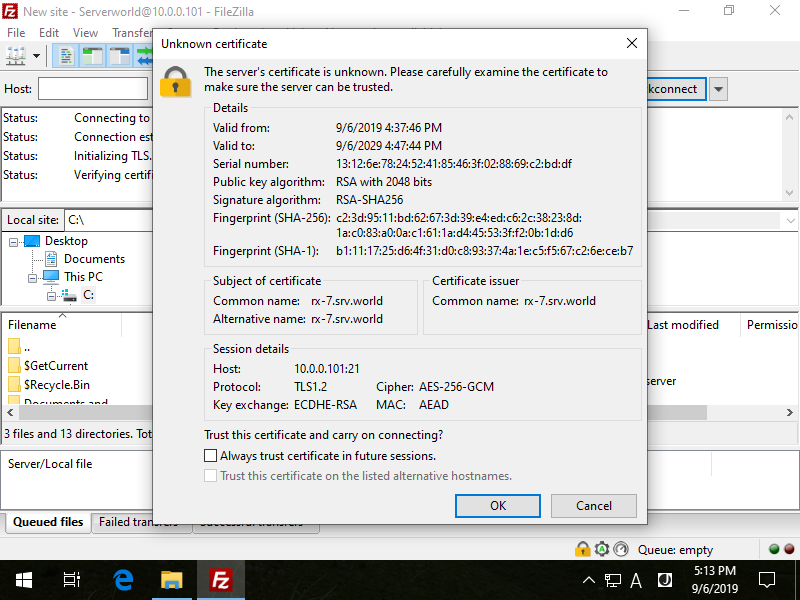
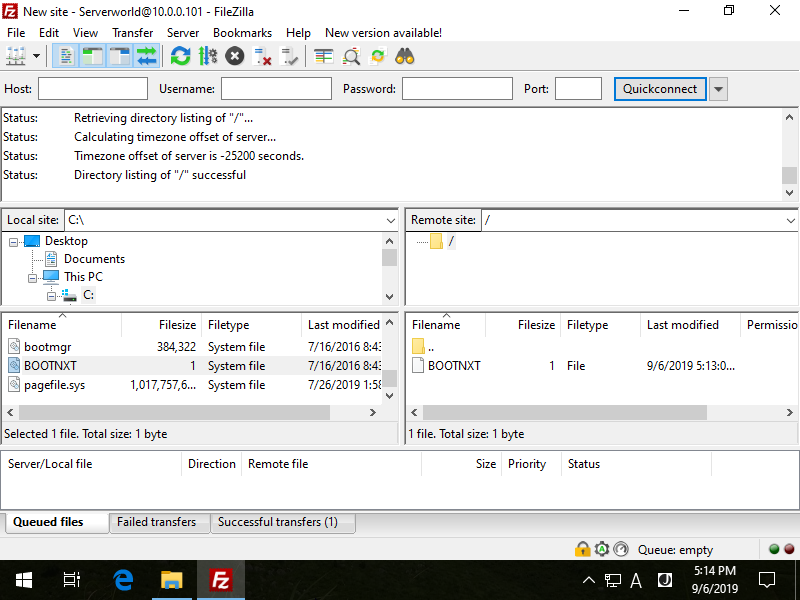
Step [5]Just connected to FTP site. Try to transfer files.
Configure FTP Isolation
Configure FTP User Isolation Setting. For this setting, each user can access only to their own named folder. If thete is no file share requirements among users, this setting is useful.
Using Command Line Interface (CLI)
Step [1]Run PowerShell with Admin Privilege and Configure FTP Service.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# add FTP site
# -Name [any name you like]
# -IPAddress [listening IP address] (below is 0.0.0.0 (all))
# -Port [listening port]
PS C:\Users\Administrator> New-WebFtpSite -Name "FTPRoot" -IPAddress "*" -Port 21
Name ID State Physical Path Bindings
---- -- ----- ------------- --------
FTPRoot 2 Started ftp *:21:
# set physical folder that is used for FTP site
# example below, create a [FTPSite01] folder under the [C:\inetpub\ftproot] that is created by default and set it
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPRoot" -Name physicalPath -Value 'C:\inetpub\ftproot'
# set SSL/TLS setting (example below is allowing No SSL)
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPRoot" -Name ftpServer.security.ssl.controlChannelPolicy -Value "SslAllow"
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPRoot" -Name ftpServer.security.ssl.dataChannelPolicy -Value "SslAllow"
# set basic authentication
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPRoot" -Name ftpServer.security.authentication.basicAuthentication.enabled -Value $true
# set read and write authority to all local users
PS C:\Users\Administrator> Add-WebConfiguration "/system.ftpServer/security/authorization" -Location FTPRoot -PSPath IIS:\ -Value @{accessType="Allow";users="*";permissions="Read,Write"}
# set user isolation
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPRoot" -Name ftpServer.userIsolation.mode -Value "IsolateRootDirectoryOnly"
# set external IP address (the one client computers can connect)
PS C:\Users\Administrator> Set-ItemProperty "IIS:\Sites\FTPRoot" -Name ftpServer.firewallSupport.externalIp4Address -Value "10.0.0.101"
# create the [LocalUser] folder under the Path you set as physical path of FTP site (it is needed on this setting)
# if Domain users, create [(FTP root)\(%UserDomain%)]
PS C:\Users\Administrator> mkdir C:\inetpub\ftproot\LocalUser
Directory: C:\inetpub\ftproot
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/5/2019 10:19 PM LocalUser
# restart FTP site
PS C:\Users\Administrator> Restart-WebItem -PSPath 'IIS:\Sites\FTPRoot'
# create folders for each local user that each folder name is the same with thier username
# naming rule ⇒ [(FTP root)\LocalUser\(Username)] (example below is for [Bizantum] user)
PS C:\Users\Administrator> mkdir C:\inetpub\ftproot\LocalUser\Bizantum
PS C:\Users\Administrator> icacls "C:\inetpub\ftproot\LocalUser\Bizantum" /grant "Bizantum:(OI)(CI)(F)"
processed file: C:\inetpub\ftproot\LocalUser\Bizantum
Successfully processed 1 files; Failed processing 0 files
Using Graphical User Interface (GUI)
Step [2]Add FTP Site. Run [Start] - [Server Manager] and Click [Tools] - [Internet Information Services (IIS) Manager]. Next, Select the [Site] and right click it, then Open [Add FTP Site].
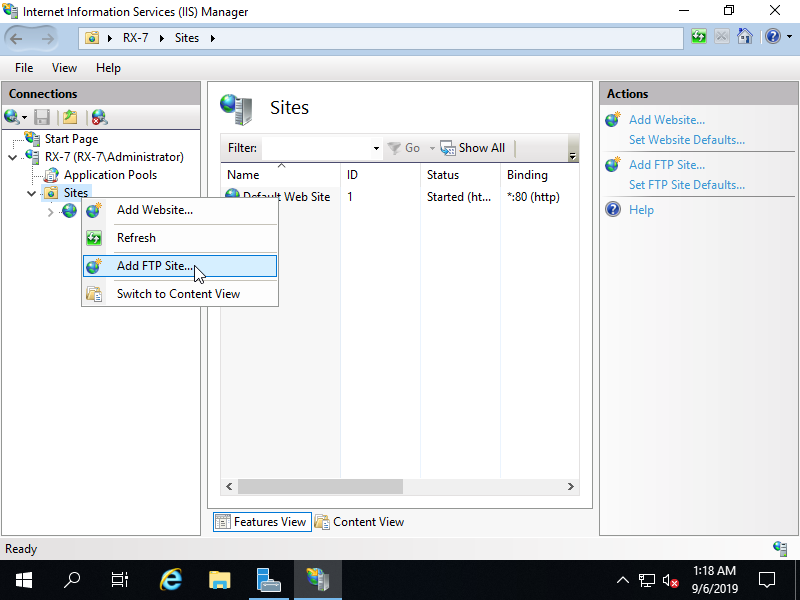
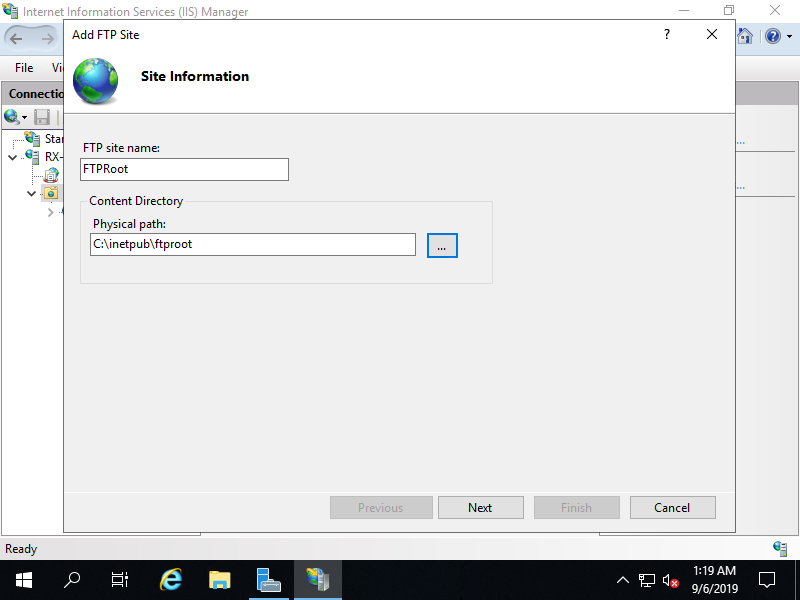
Step [3]Input any name for [FTP site name], specify physical Path for [Physical path]. On this example, set the default root [C:\inetpub\ftproot] to [Physical path].
Step [4]This is Binding setting section. It's OK to keep default for IP Address and Port. For the case of this default setting, FTP service listens on 0.0.0.0:21. For [SSL] section, Select [No SSL] on this example. If you'd like to configure with SSL, refer to here.
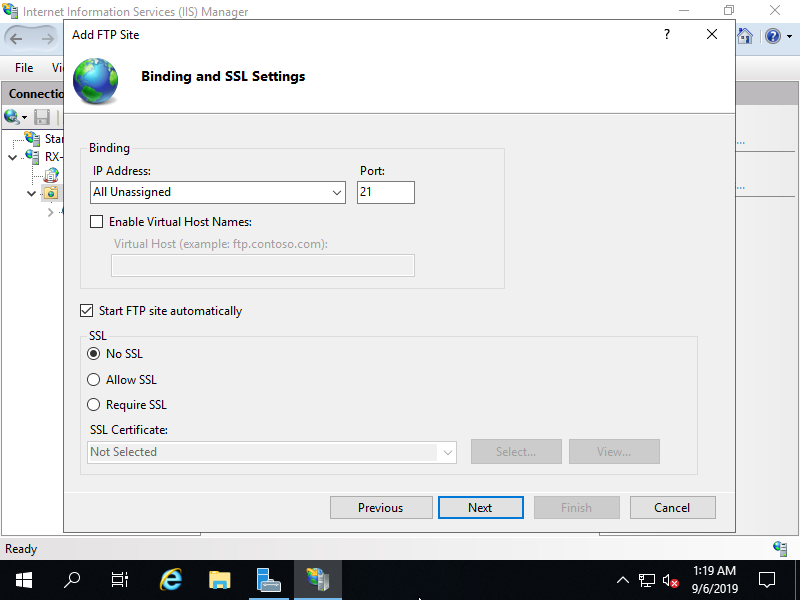
Step [5]This is Authentication and Authorization settings section. Set [Basic] for authentication and [All users] for Authorization.
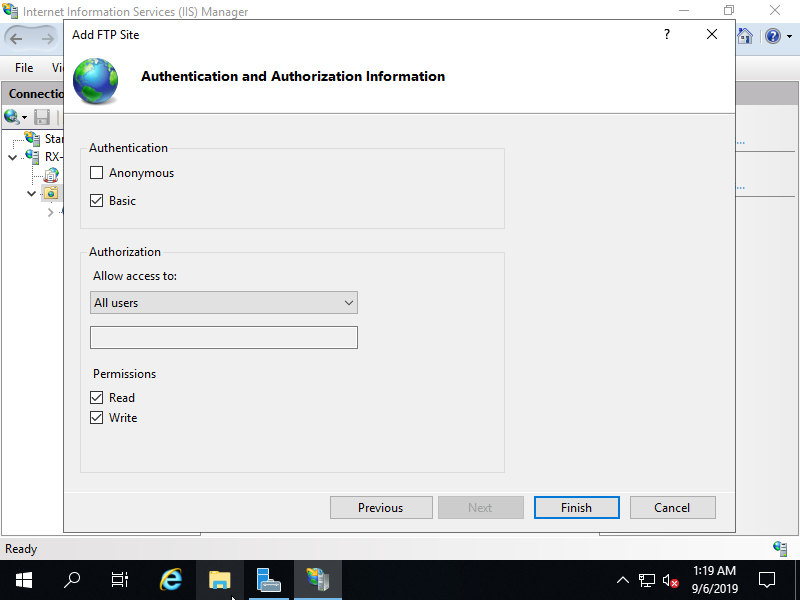
Step [6]FTP site has been added. Select the new FTP site on the left pane and click [FTP Firewall Support] on center pane.
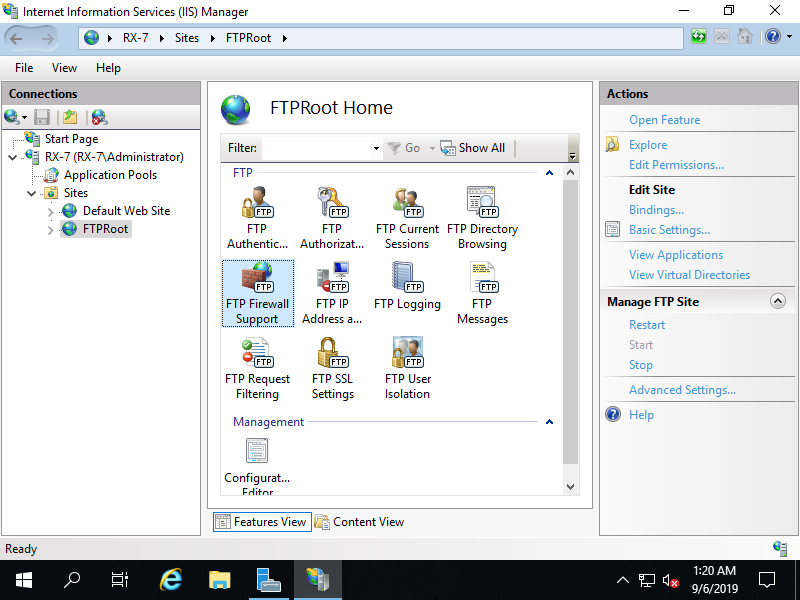
Step [7]Set IP address that client computers can connect to.
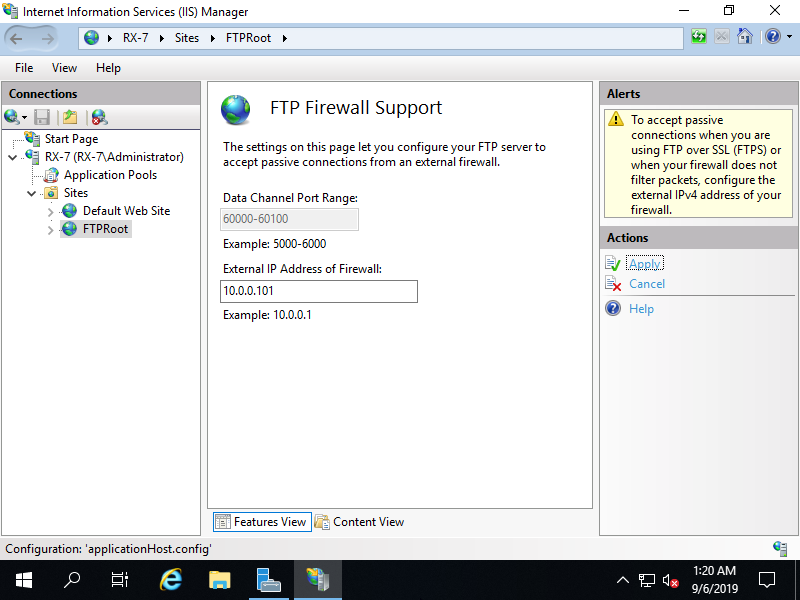
Step [8]Back to FTP site index and Click [FTP User Isolation] on the center pane.
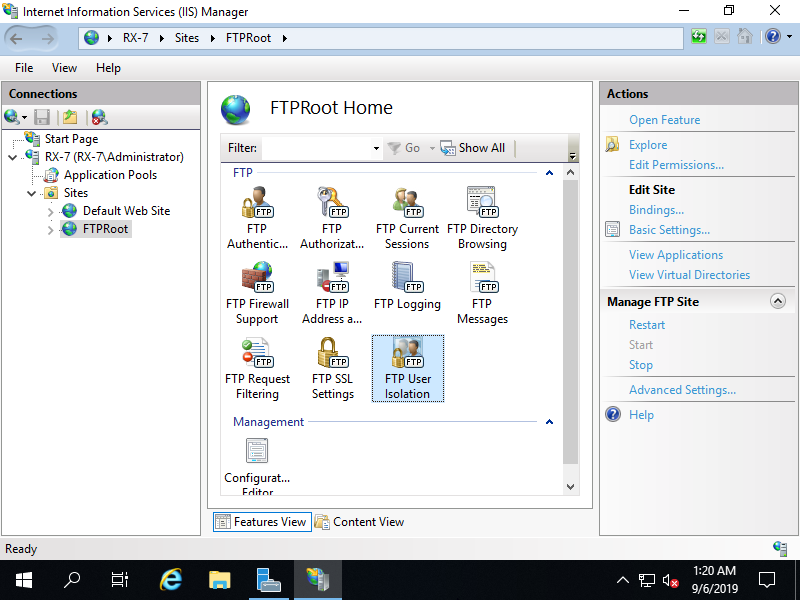
Step [9]Check a box [User name physical directory] and apply setting.
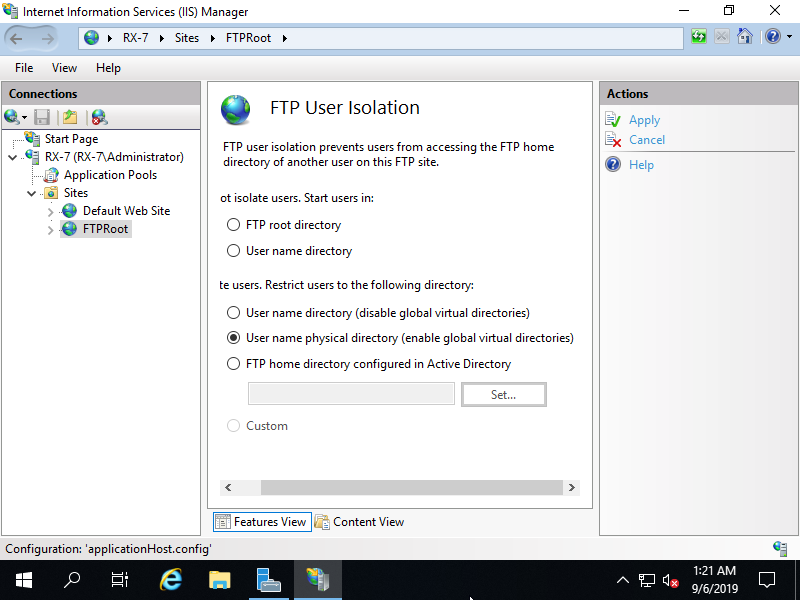
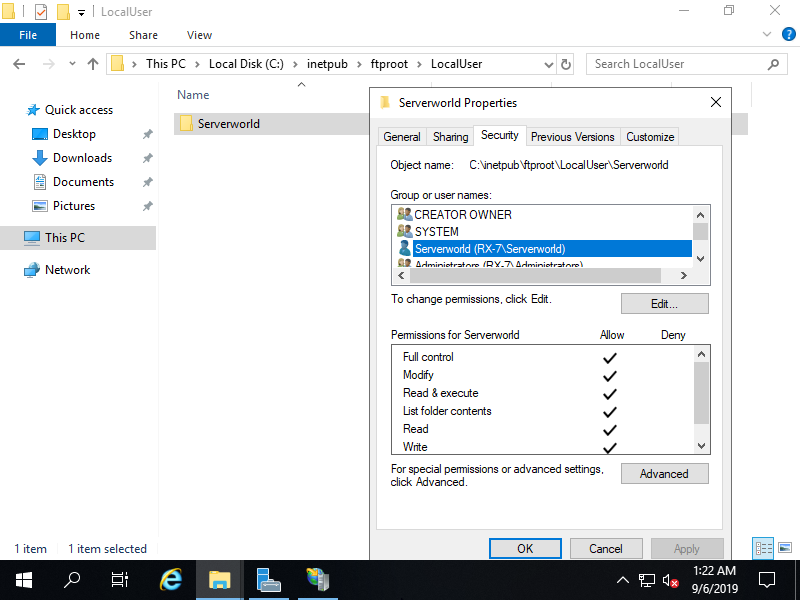
Step [10]On FTP User Isolation setting, FTP root folder is needed for each user. Create a [LocalUser] folder under the FTP root of the FTP site. (on this example, FTP root is [C:\inetpub\ftproot]) Next, create user folders that folder name is the same with each username and add read and write authority to their folders. (example below is for [Bizantum] user) That's OK, FTP User Isolation setting has done. Try to access to FTP site from Client Computer.
- Get link
- X
- Other Apps








Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.