
Overview
What
Active Directory Domain Services (ADDS) is a directory service developed by Microsoft for Windows domain networks. It is an essential component of the Windows Server operating system, enabling administrators to manage and store information about network resources and application data in a centralized, organized, and secure manner.
Who
ADDS is primarily used by network administrators, IT professionals, and system engineers who are responsible for managing and maintaining the network infrastructure within an organization. It is also utilized by businesses of all sizes, educational institutions, government agencies, and other entities that require centralized network management and security.
Where
ADDS is used in a variety of environments, including corporate networks, educational institutions, and government agencies. It is commonly deployed in on-premises data centers and can also be integrated with cloud-based services for hybrid network configurations.
When
ADDS should be used when there is a need for centralized management of user accounts, permissions, and network resources. It is particularly useful in environments with a large number of users and devices, where manual management would be inefficient and prone to errors. ADDS is also essential for organizations that require enhanced security and compliance with regulatory standards.
Why
Using Active Directory Domain Services (ADDS) offers several advantages and some costs. Here’s a detailed comparison:
| Pros | Costs |
|---|---|
| Centralized Management: Simplifies the administration of user accounts, permissions, and policies. | Initial Setup Cost: Requires investment in hardware, software, and skilled personnel for setup and maintenance. |
| Improved Security: Enhances security through centralized authentication and access control. | Ongoing Maintenance: Regular updates and maintenance are needed to ensure optimal performance and security. |
| Scalability: Easily scales to accommodate growing business needs. | Training: Staff may need training to effectively manage and utilize ADDS. |
| Integration: Seamlessly integrates with other Microsoft products and services. | Hardware Requirements: Requires robust hardware to handle the load of directory services. |
How
ADDS works by storing directory data and making this data available to network users and administrators. It uses a structured data store as the basis for a logical, hierarchical organization of directory information. This data store contains information about Active Directory objects, such as user accounts, computers, and other resources. The main components of ADDS include:
| Domains | Logical groupings of network resources. |
| Organizational Units (OUs) | Containers within a domain that help organize and manage objects. |
| Forest | A collection of one or more domains that share a common schema. |
| Global Catalog | A distributed data repository that contains a searchable, partial representation of every object in every domain within a forest. |
Consequences
Implementing ADDS can lead to several positive and negative consequences:
| Positive |
|
| Negative |
|
Conclusion
Active Directory Domain Services (ADDS) is a vital component for managing network resources and user accounts in Windows Server 2019. While it offers numerous benefits, including centralized management, improved security, and scalability, it also requires careful consideration of costs, initial setup, ongoing maintenance, and training. Proper implementation and maintenance of ADDS can greatly enhance the efficiency and security of an organization's IT infrastructure.
Install ADDS
Installing Active Directory Domain Service (ADDS).
Using Command Line Interface (CLI)
Run PowerShell with Admin Privilege and Configure like follows.
Step [1]Installing ADDS
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# install AD DS with admin tools
PS C:\Users\Administrator> Install-WindowsFeature -name AD-Domain-Services -IncludeManagementTools
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True Yes SuccessRest... {Active Directory ,...
WARNING: You must restart this server to finish the installation process.
# restart computer to apply changes
PS C:\Users\Administrator> Restart-Computer -Force
Using Graphical User Interface (GUI)
On GUI configuration, set like follows.
Step [2]Run [Server Manager] and click [Add roles and features].
Step [3]Click [Next] button.
Step [4]Select [Role-based or feature-based installation].
Step [5]Select a Host which you'd like to add services.
Step [6]Check a box [Active Directory Domain Services].
Step [7]Addtional features are required to add AD DS. Click [Add Features] button.
Step [8]Click [Next] button.
Step [9]Click [Next] button.
Step [10]Click [Install] button.
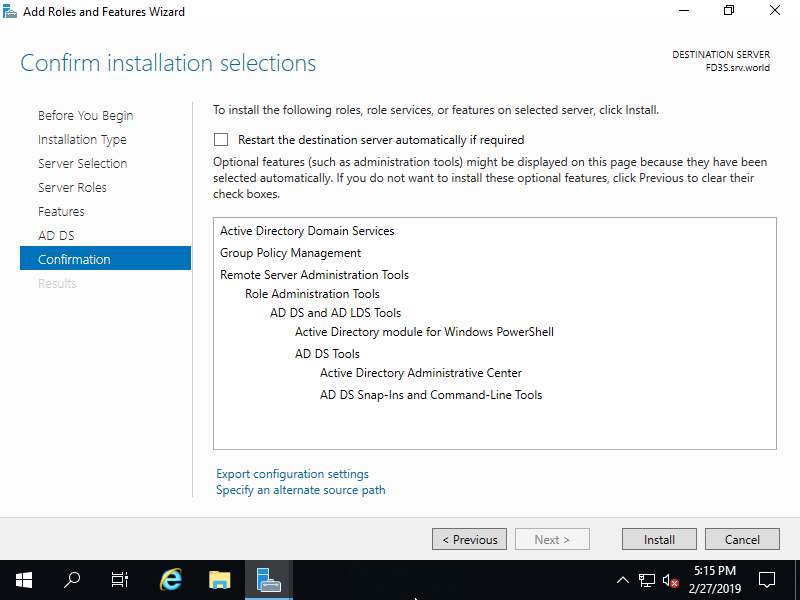
Step [11]After finishing Installation, click [Close] button.
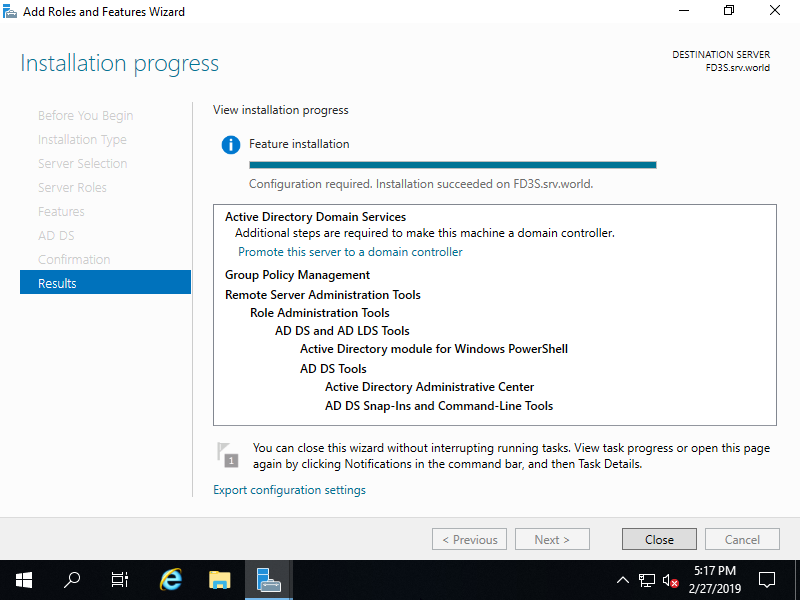
Configure New DC
Configure New DC (Domain Controler).
Using Command Line Interface (CLI)
Run PowerShell with Admin Privilege and Configure like follows.
Step [1]For example, Configure new DC with Root Domain name as [bizantum.local]. After finishing commands, Computer will restart automatically.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
# set forest/domain functional level as Windows Server 2016 = [WinThreshold]
# for [-DomainNetbiosName], set any NetBIOS name
# for [-SafeModeAdministratorPassword], set any password for SafeMode
PS C:\Users\Administrator> Install-ADDSForest -DomainName "bizantum.local" `
-ForestMode WinThreshold `
-DomainMode WinThreshold `
-DomainNetbiosName FD3S01 `
-SafeModeAdministratorPassword (ConvertTo-SecureString -AsPlainText "P@ssw0rd01" -Force) `
-InstallDNS
The target server will be configured as a domain controller and restarted when this operation is complete.
Do you want to continue with this operation?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): Y
.....
.....
Using Graphical User Interface (GUI)
On GUI configuration, set like follows.
Step [2]Run [Server Manager] and click [AD DS], next, on the screen below, Click [More...] link which is upper-right on the left pane.
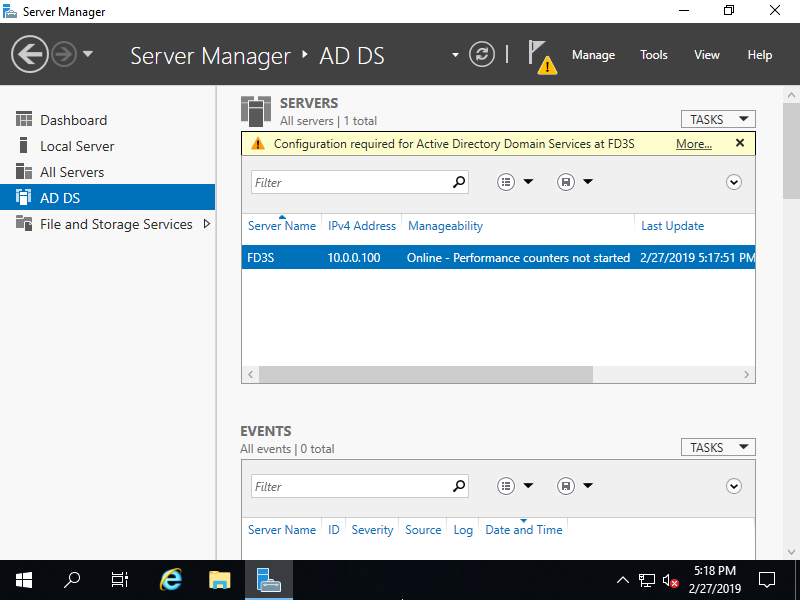
Step [3] Click [Promote this server to domain...] link.
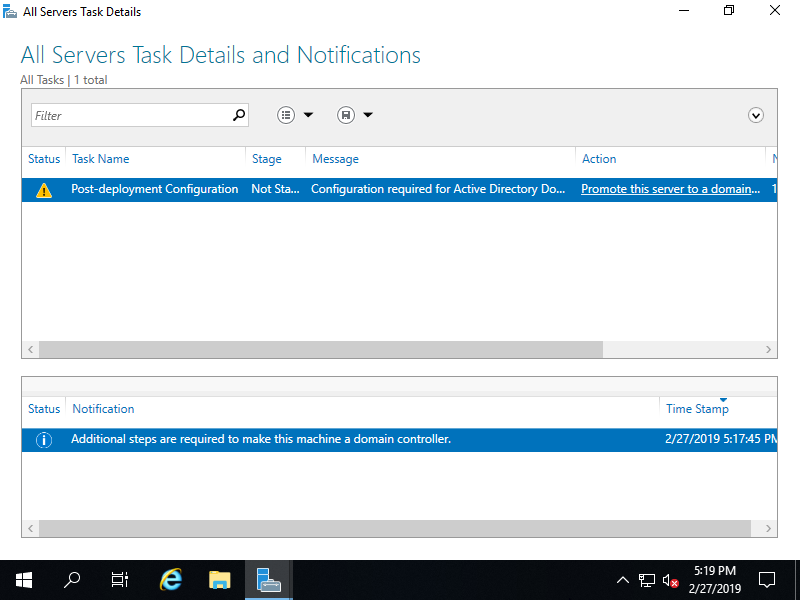
Step [4]Check a box [Add a new forest] and input any Domain name you'd like to set for [Root domain name] field.
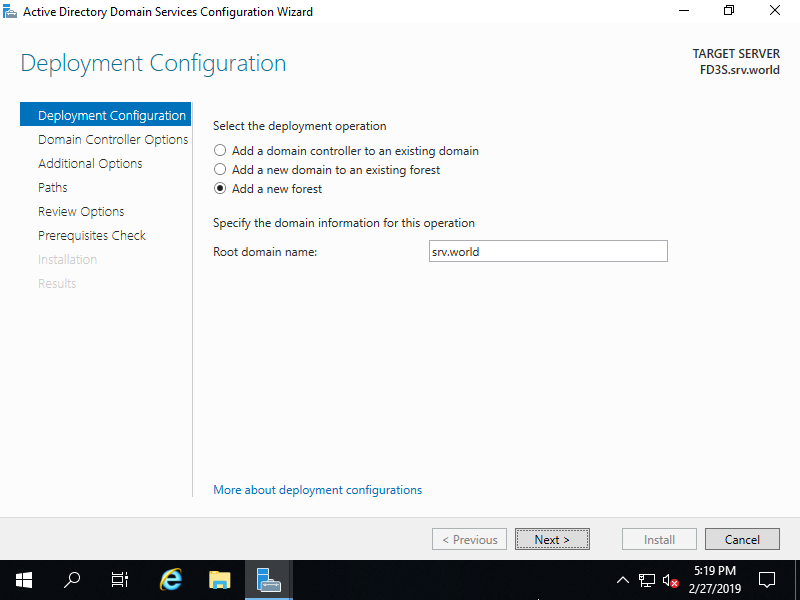
Step [5]Select [Forest functional level] and [Domain functional level]. This example shows to select [Windows Server 2016] both. Furthermore, Set any password for Directory Services Restore Mode.
Step [6]Click [Next] button.
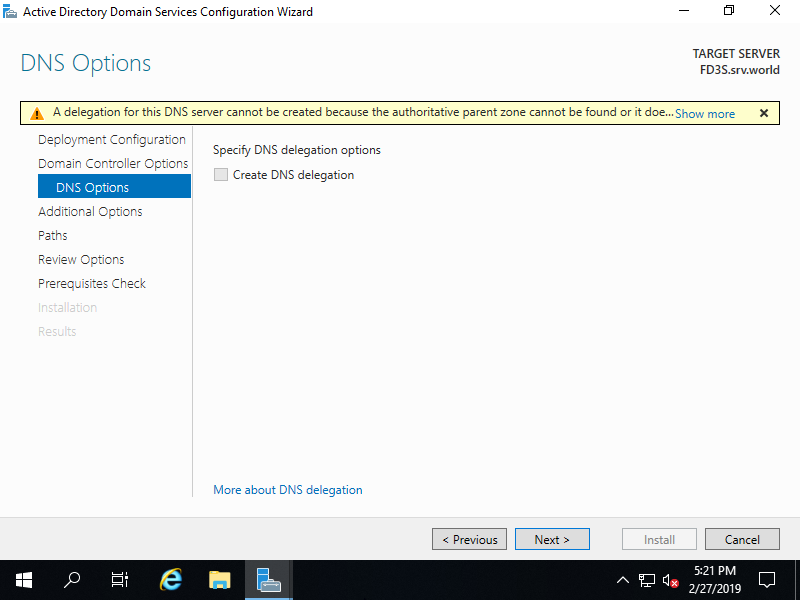
Step [7]Input NetBIOS name you'd like to set.
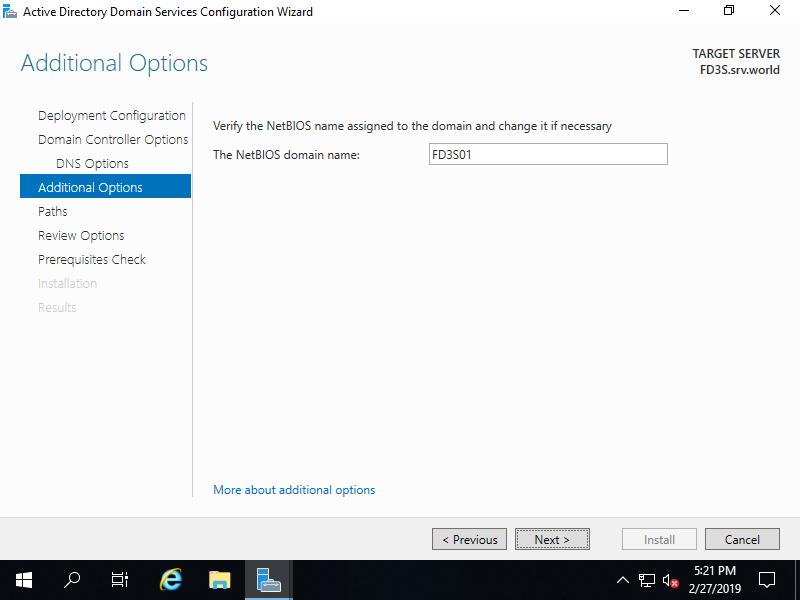
Step [8]Specify Database folder or Log folder and so on. It's Ok to keep default if you don't have specific requirements.
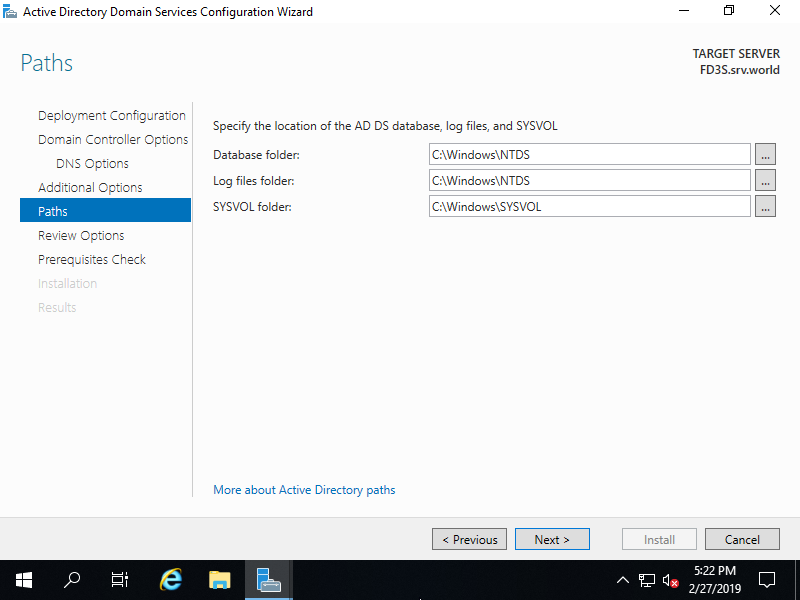
Step [9]Check the contents you configured and click [Next] button.
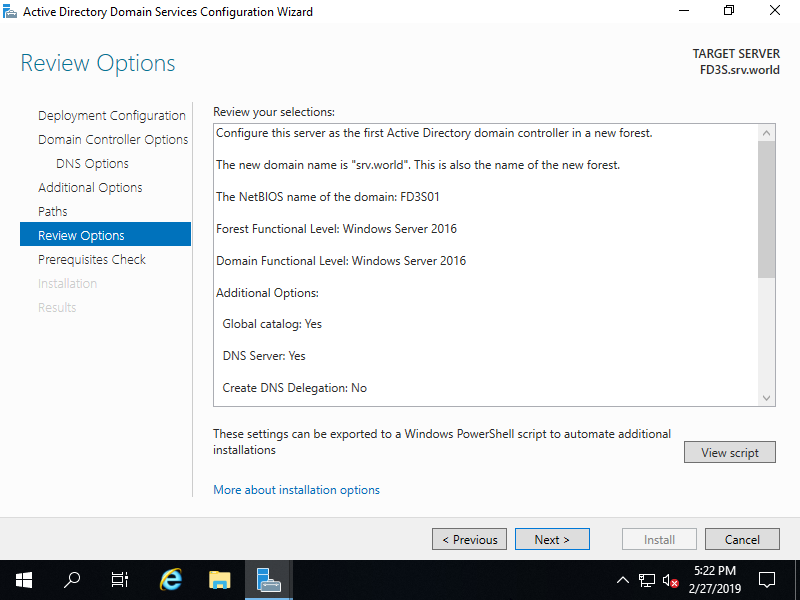
Step [10]Click [Install] button. After finishing it, System will restart automatically.
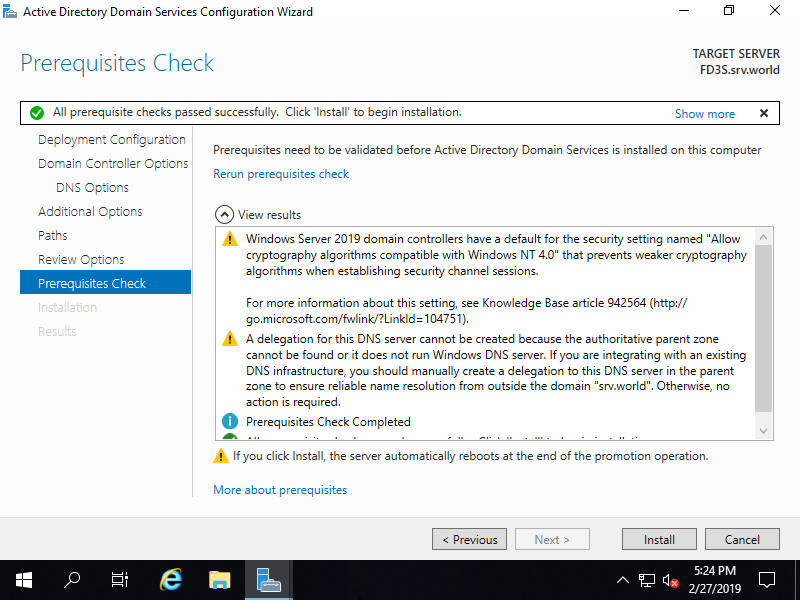
Step [11]After restarting System, logon name is changed as [Domain name][User name].
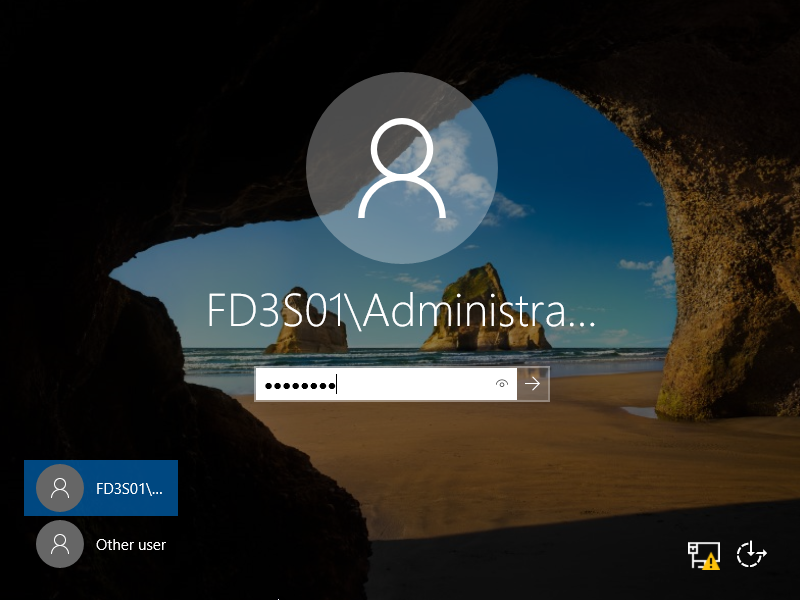
Step [12]It's OK if logined normally.
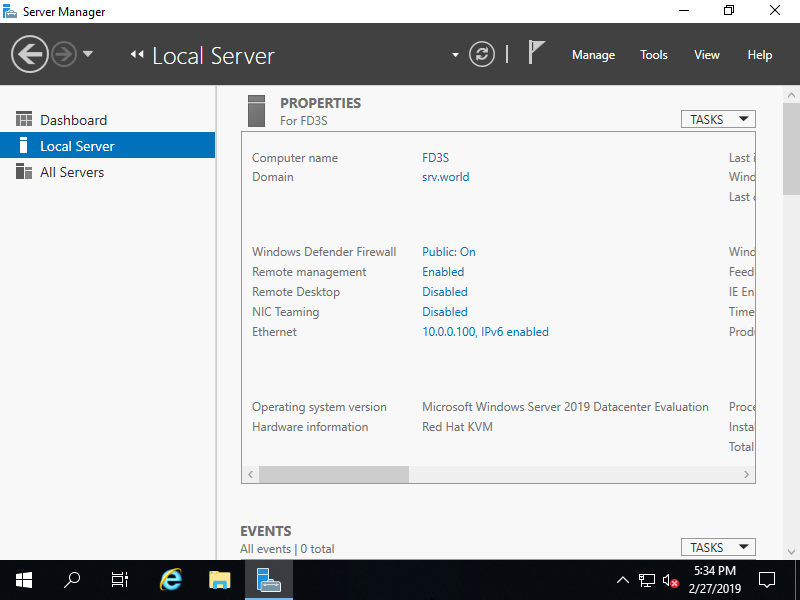
Join Domain Client Host
Join in Active Directory Domain from Other Windows Client Hosts. This example is based on Windows 10 (1809).
Step [1]Before setting, change to DNS settings to refer Active Directory Host.
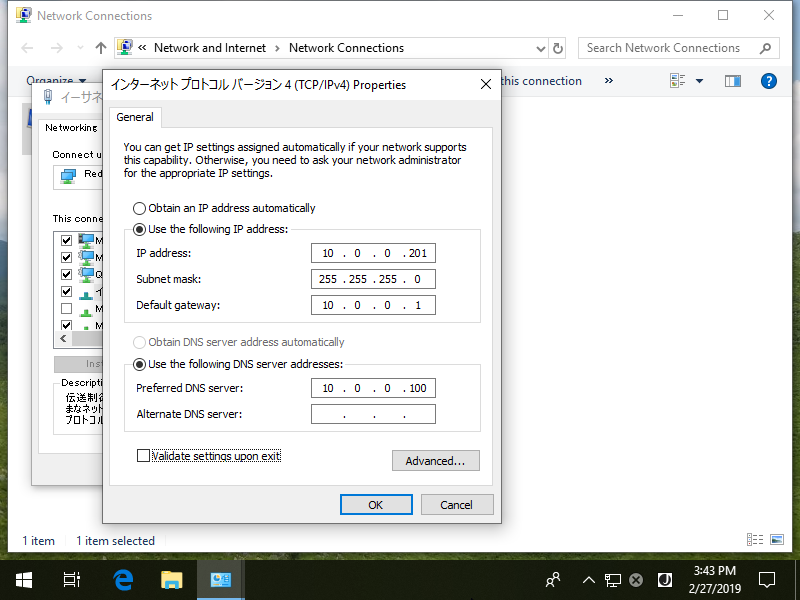
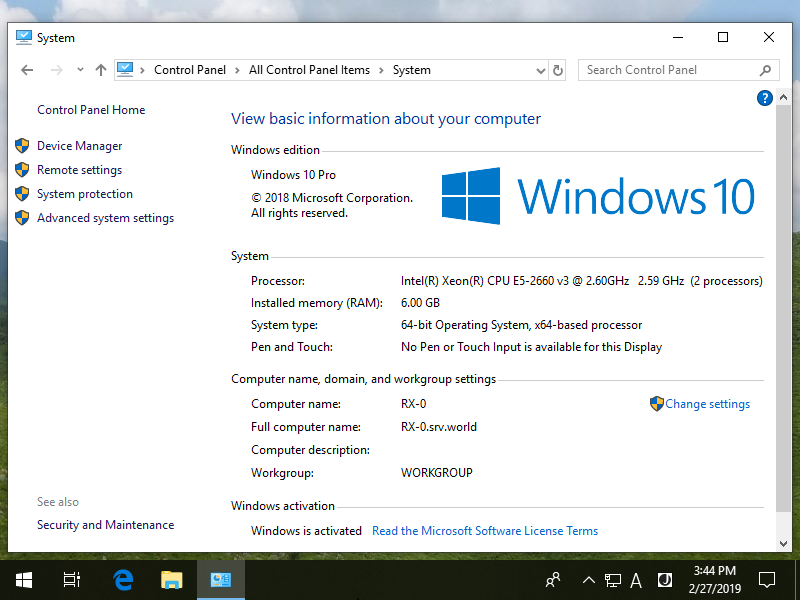
Step [2]Open [System] and click [Change settings] link which is lower-right.
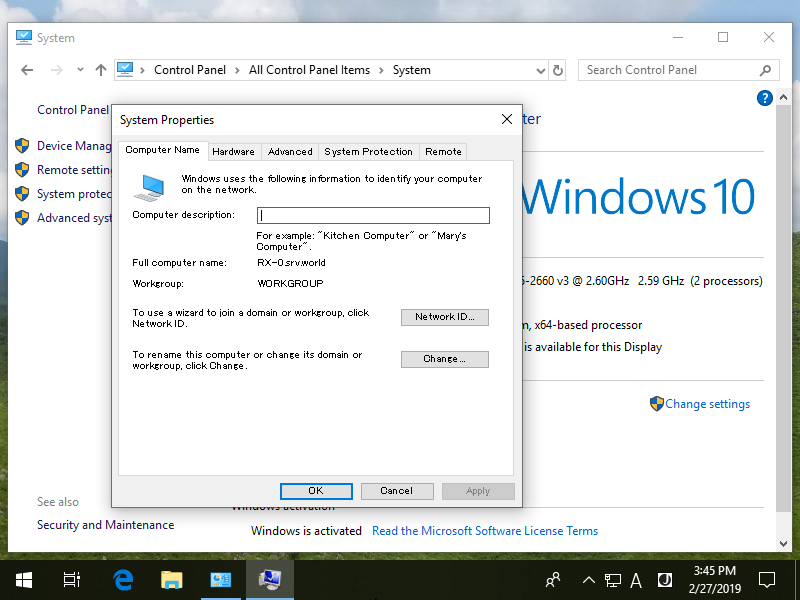
Step [3]Move to [Computer Name] tab and click [Change] button.
Step [4]Check a box [Domain] and input domain name and next, click [OK] button.
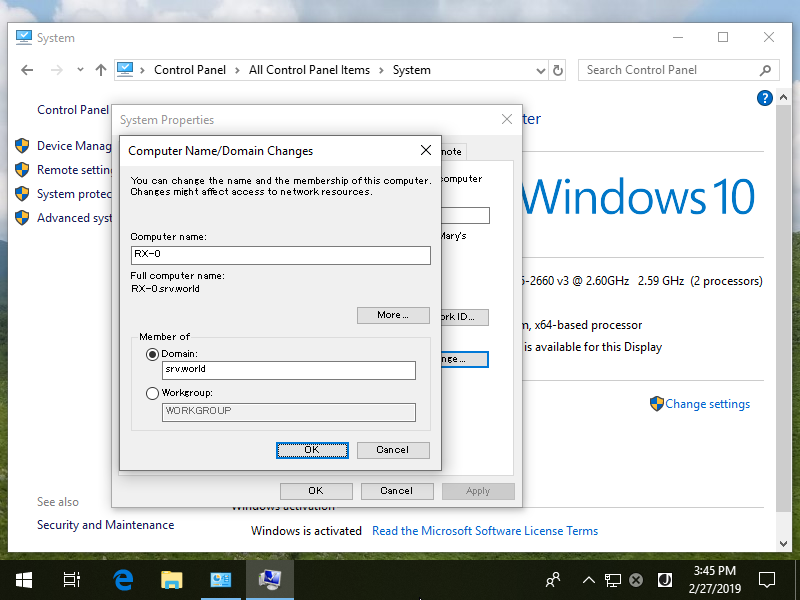
Step [5] Authentication is required, authenticate with a domain User in Active Directory.
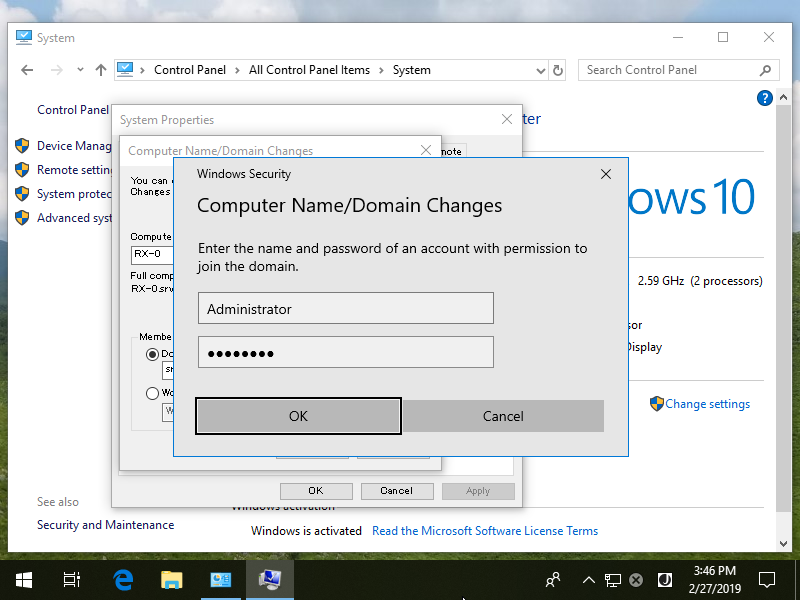
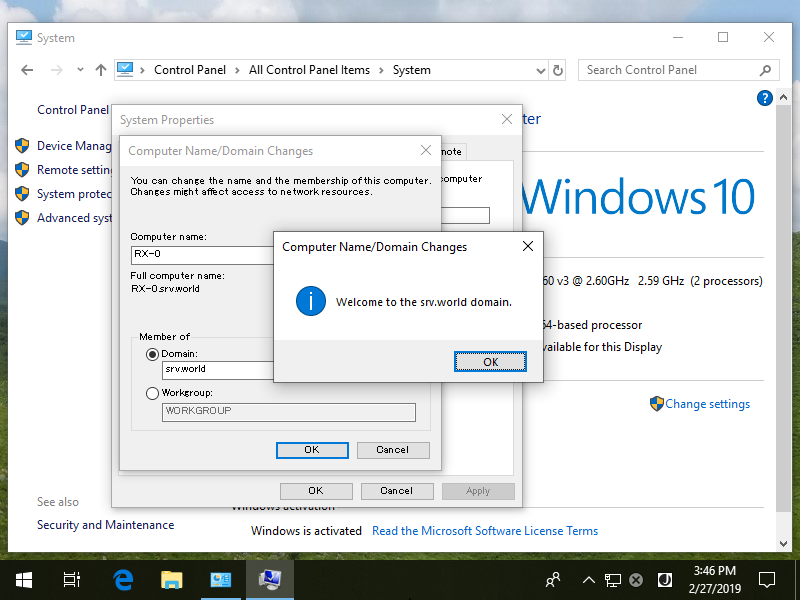
Step [6]After successing authentication, Welcome message is shown like follows. Restart the Computer once.
Step [7]On the logon screen after restarting Computer, click [another user] to switch Domain user to logon and Authenticate with a Domain user you added.
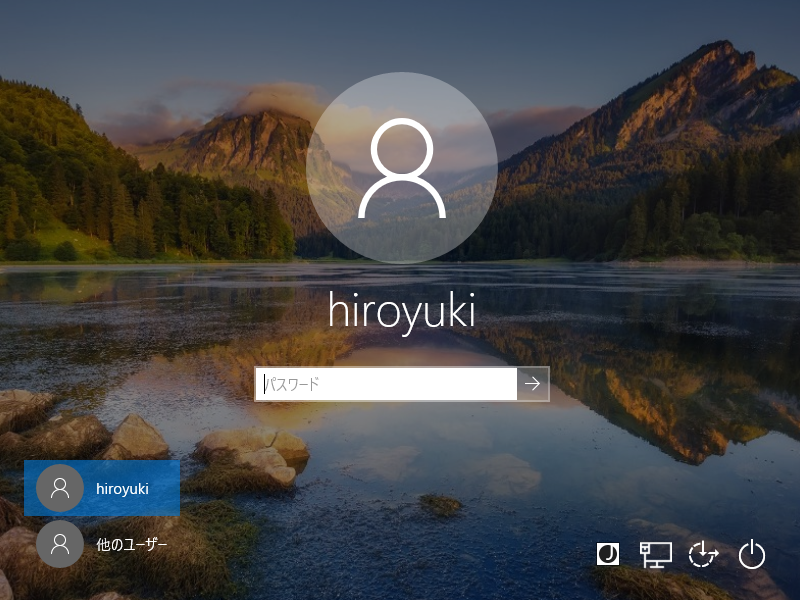
Step [8]Just Logon to Active Directory Domain.
Add UNIX Attributes
Add UNIX attributes to existing User Accounts. User Accounts that have UNIX attributes can authenticate to UNIX/Linux Hosts that have LDAP Client role.
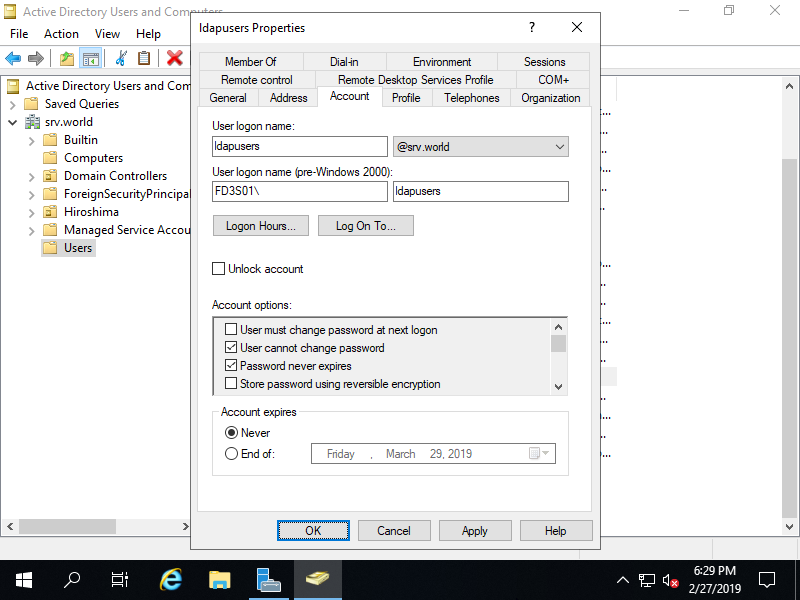
Step [1]Run [Server Manager] and click [Tools] - [Active Directory Users and Conputers], and Add a user for authentication from UNIX/Linux Hosts. Any name is OK for username, it's OK with minimum rights, it's not necessarry to join in Administrators group. On this example, proceed with [ldapusers] like follows
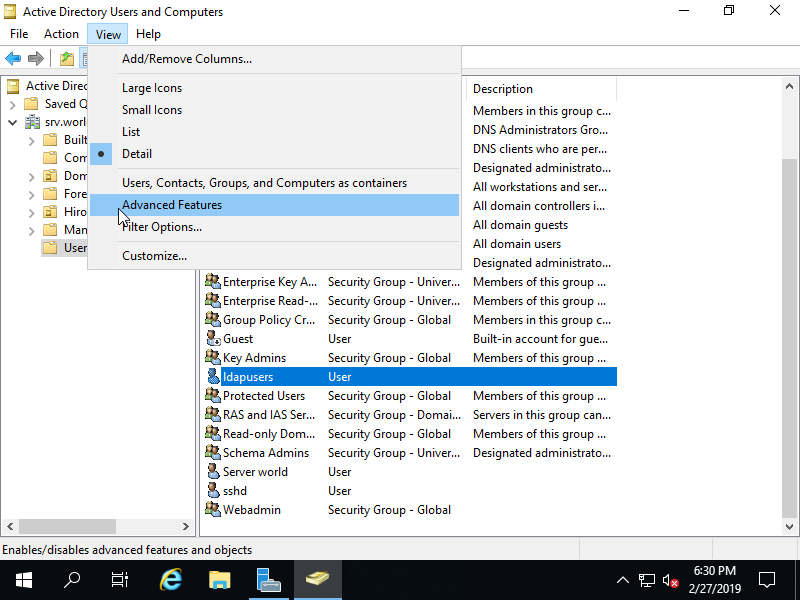
Step [2] Add UNIX attrubutes to an existing user. Select [Advanced Features] on [View] menu on [Active Directory Users and Conputers] window.
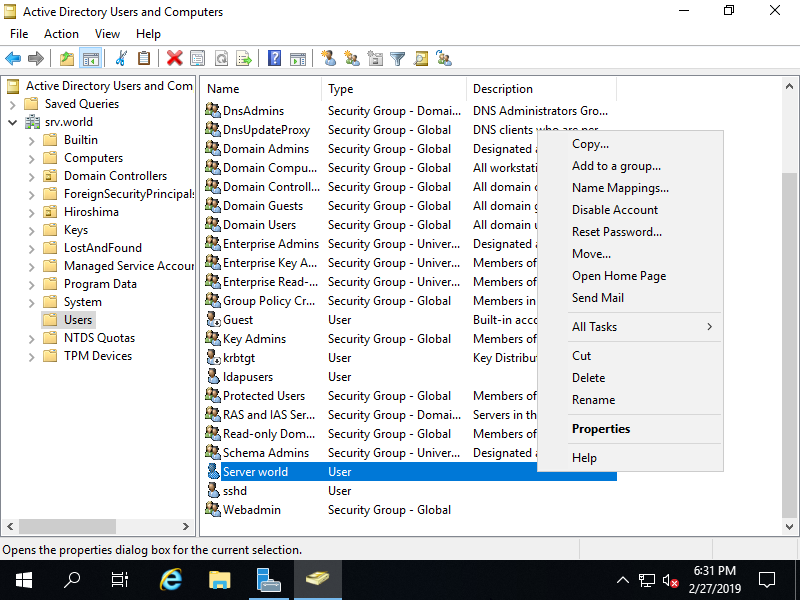
Step [3]Open [Property] for a user you'd like to add UNIX attributes.
Step [4]Move to [Attribute Editor] tab and open [uidNumber] attribute.
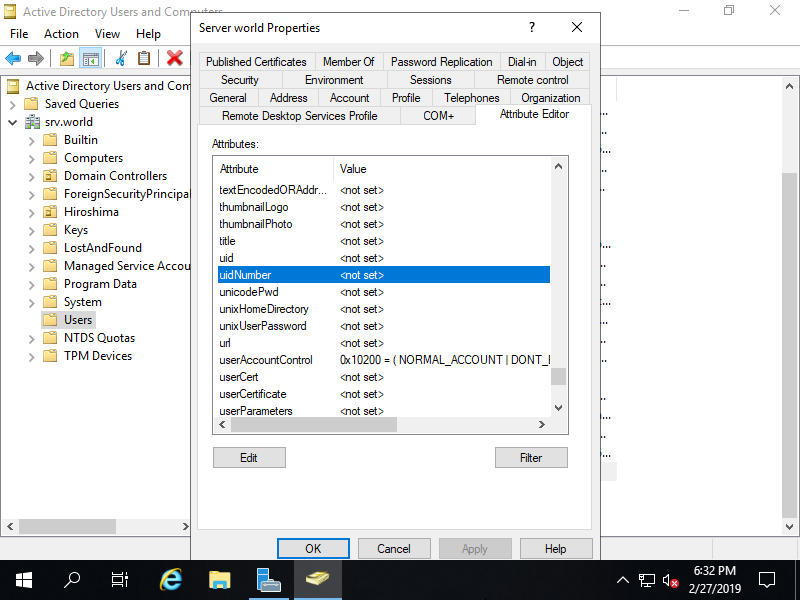
Step [5]Input UID number that is used on Linux. Specify uniq number which does not exist on Linux Localhost.
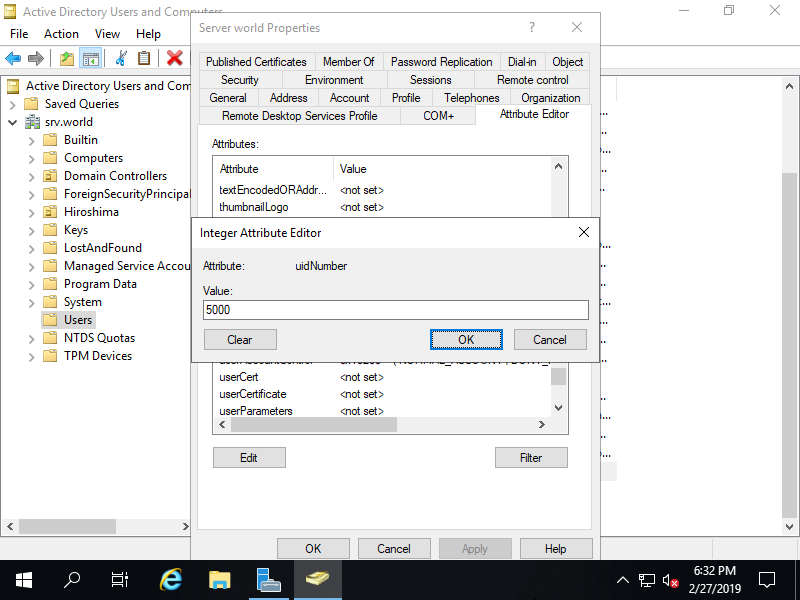
Step [6]Open [gidNumber] attribute and input GID number. Specify uniq number which already exists on Linux Localhost, or Specify GID number which exists on Active Directory groups. For GID number which exists on Active Directory groups, it means the GID which is added to an AD group with the same procedure on here.
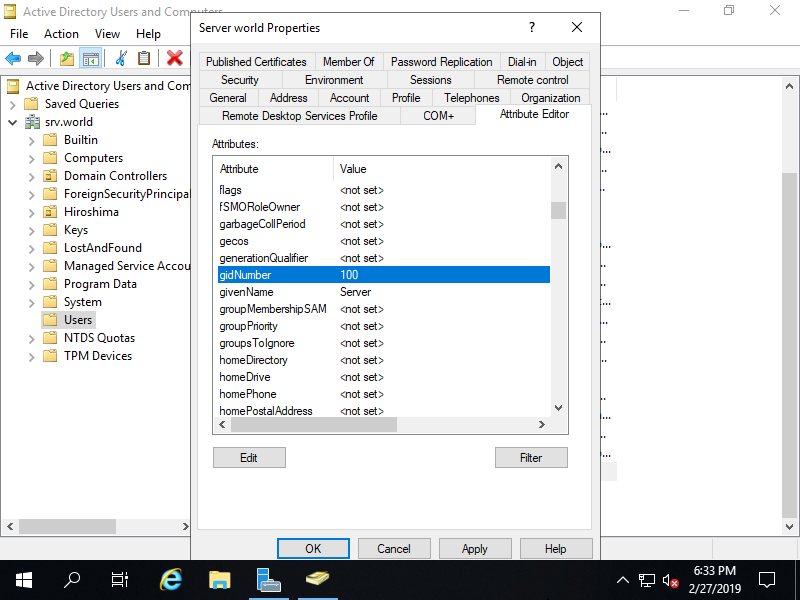
Step [7]Open [loginShell] attribute and input the Path of Login Shell on Linux. Specify it that exists on Linux Host.
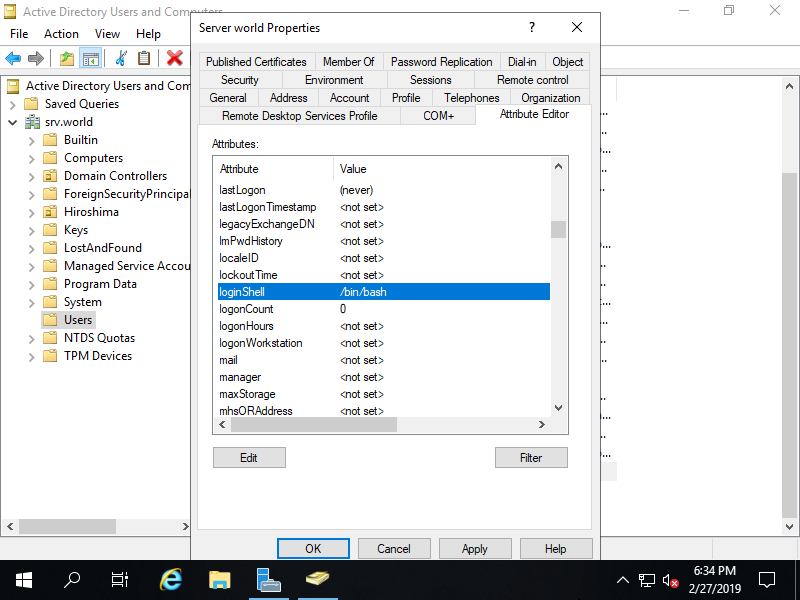
Step [8]Open [unixHomeDirectory] attribute and input the Path of Home Directory. It's possbile to login to Linux Host if the Path of Home Directory does not exist, If not exist, it will be created for initial login (if configured as so) or move to / (if not configured automatical mkhomedir).
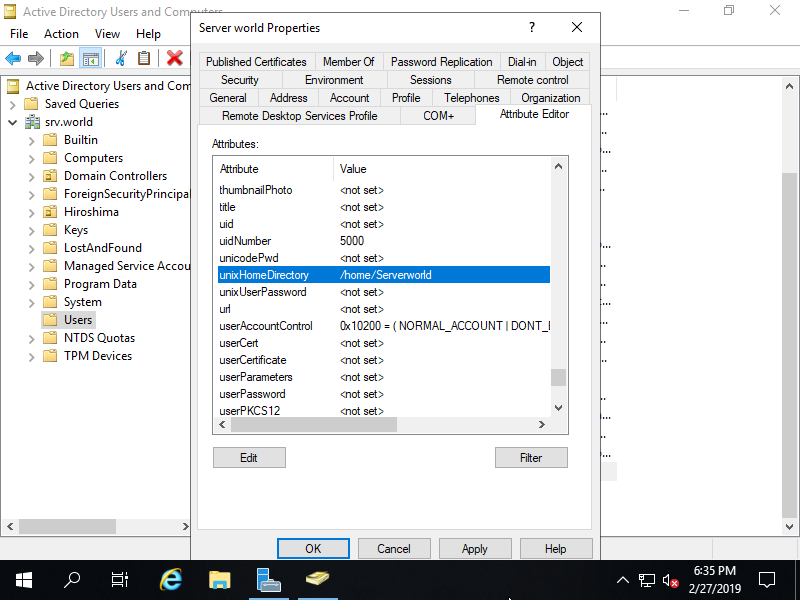
All done, to configure on Linux LDAP Client we will expalin on next section.
Add User Account
Using Command Line Interface (CLI)
Run PowerShell with Admin Privilege and Configure like follows.
Step [1]Run PowerShell or Command Prompt and use [dsadd user] command.
# show current user list
PS C:\Users\Administrator> dsquery user -name *
"CN=Administrator,CN=Users,DC=bizantum,DC=local"
"CN=Guest,CN=Users,DC=bizantum,DC=local"
"CN=Bizantum,CN=Users,DC=bizantum,DC=local"
"CN=sshd,CN=Users,DC=bizantum,DC=local"
"CN=krbtgt,CN=Users,DC=bizantum,DC=local"
# for example, add [Redstone] user
PS C:\Users\Administrator> dsadd user CN=Redstone,CN=Users,DC=bizantum,DC=local `
-pwd P@ssw0rd01 `
-mustchpwd yes `
-ln Redstone `
-fn R5 `
-email Redstone@bizantum.local `
-display "Redstone R5"
dsadd succeeded:CN=Redstone,CN=Users,DC=bizantum,DC=local
PS C:\Users\Administrator> dsquery user -name Redstone
"CN=Redstone,CN=Users,DC=bizantum,DC=local"
# options for [dsadd user]
PS C:\Users\Administrator> dsadd user /?
Description: Adds a user to the directory.
Syntax: dsadd user <UserDN> [-samid <SAMName>] [-upn <UPN>] [-fn <FirstName>]
[-mi <Initial>] [-ln <LastName>] [-display <DisplayName>]
[-empid <EmployeeID>] [-pwd {<Password> | *}] [-desc <Description>]
[-memberof <Group ...>] [-office <Office>] [-tel <Phone#>]
[-email <Email>] [-hometel <HomePhone#>] [-pager <Pager#>]
[-mobile <CellPhone#>] [-fax <Fax#>] [-iptel <IPPhone#>]
[-webpg <WebPage>] [-title <Title>] [-dept <Department>]
[-company <Company>] [-mgr <Manager>] [-hmdir <HomeDir>]
[-hmdrv <DriveLtr:>] [-profile <ProfilePath>] [-loscr <ScriptPath>]
[-mustchpwd {yes | no}] [-canchpwd {yes | no}]
[-reversiblepwd {yes | no}] [-pwdneverexpires {yes | no}]
[-acctexpires <NumDays>] [-disabled {yes | no}]
[{-s <Server> | -d <Domain>}] [-u <UserName>]
[-p {<Password> | *}] [-q] [{-uc | -uco | -uci}]
[-fnp <FirstNamePhonetic>] [-lnp <LastNamePhonetic>]
[-displayp <DisplayNamePhonetic>]
.....
.....
Step [2]If you'd like to delete users, use [dsrm] command.
# for example, delete [Redstone] user
PS C:\Users\Administrator> dsrm "CN=Redstone,CN=Users,DC=bizantum,DC=local"
Are you sure you wish to delete CN=Redstone,CN=Users,DC=bizantum,DC=local (Y/N)? y
dsrm succeeded:CN=Redstone,CN=Users,DC=bizantum,DC=local
Step [3]If you use PowerShell, It's possible to use Cmdlet for PowerShell.
# show current user list
PS C:\Users\Administrator> Get-ADUser -Filter * | Format-Table DistinguishedName
DistinguishedName
-----------------
CN=Administrator,CN=Users,DC=bizantum,DC=local
CN=Guest,CN=Users,DC=bizantum,DC=local
CN=Bizantum,CN=Users,DC=bizantum,DC=local
CN=sshd,CN=Users,DC=bizantum,DC=local
CN=krbtgt,CN=Users,DC=bizantum,DC=local
# for example, add [Redstone] user
PS C:\Users\Administrator> New-ADUser Redstone `
-Surname Redstone `
-GivenName R5 `
-DisplayName "Redstone R5" `
-EmailAddress "Redstone@bizantum.local" `
-AccountPassword (ConvertTo-SecureString -AsPlainText "P@ssw0rd01" -Force) `
-ChangePasswordAtLogon $true `
-Enabled $true
# verify
PS C:\Users\Administrator> Get-ADUser -Identity Redstone
DistinguishedName : CN=Redstone,CN=Users,DC=bizantum,DC=local
Enabled : True
GivenName : R5
Name : Redstone
ObjectClass : user
ObjectGUID : 0c65ad43-9cb2-4808-a2b3-72b731377a8f
SamAccountName : Redstone
SID : S-1-5-21-1938244123-2570910143-1886879425-1107
Surname : Redstone
UserPrincipalName :
# if delete, do like follows
PS C:\Users\Administrator> Remove-ADUser -Identity "CN=Redstone,CN=Users,DC=bizantum,DC=local"
Confirm
Are you sure you want to perform this action?
Performing the operation "Remove" on target "CN=Redstone,CN=Users,DC=bizantum,DC=local".
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): Y
# options for [New-ADUser] command
PS C:\Users\Administrator> Get-Help New-ADUser
NAME
New-ADUser
Description
Creates a new Active Directory user.
Syntax
New-ADUser [-Name] <String> [-AccountExpirationDate <DateTime>] [-AccountNotDelegated <Boolean>] [-AccountPassword
<SecureString>] [-AllowReversiblePasswordEncryption <Boolean>] [-AuthenticationPolicy <ADAuthenticationPolicy>] [-A
uthenticationPolicySilo <ADAuthenticationPolicySilo>] [-AuthType {Negotiate | Basic}] [-CannotChangePassword <Boole
an>] [-Certificates <X509Certificate[]>] [-ChangePasswordAtLogon <Boolean>] [-City <String>] [-Company <String>] [-
CompoundIdentitySupported <Boolean>] [-Country <String>] [-Credential <PSCredential>] [-Department <String>] [-Desc
ription <String>] [-DisplayName <String>] [-Division <String>] [-EmailAddress <String>] [-EmployeeID <String>] [-Em
ployeeNumber <String>] [-Enabled <Boolean>] [-Fax <String>] [-GivenName <String>] [-HomeDirectory <String>] [-HomeD
rive <String>] [-HomePage <String>] [-HomePhone <String>] [-Initials <String>] [-Instance <ADUser>] [-KerberosEncry
ptionType {None | DES | RC4 | AES128 | AES256}] [-LogonWorkstations <String>] [-Manager <ADUser>] [-MobilePhone <St
ring>] [-Office <String>] [-OfficePhone <String>] [-Organization <String>] [-OtherAttributes <Hashtable>] [-OtherNa
me <String>] [-PassThru] [-PasswordNeverExpires <Boolean>] [-PasswordNotRequired <Boolean>] [-Path <String>] [-POBo
x <String>] [-PostalCode <String>] [-PrincipalsAllowedToDelegateToAccount <ADPrincipal[]>] [-ProfilePath <String>]
[-SamAccountName <String>] [-ScriptPath <String>] [-Server <String>] [-ServicePrincipalNames <String[]>] [-Smartcar
dLogonRequired <Boolean>] [-State <String>] [-StreetAddress <String>] [-Surname <String>] [-Title <String>] [-Trust
edForDelegation <Boolean>] [-Type <String>] [-UserPrincipalName <String>] [-Confirm] [-WhatIf] [<CommonParameters>]
.....
.....
Step [4]If you'd lie to add UNIX attributes for existing users on PowerShell, Use [Set-ADUser] command.
# for example, add atrributes to [Redstone] user
PS C:\Users\Administrator> Get-ADUser -Identity Redstone
DistinguishedName : CN=Redstone,CN=Users,DC=bizantum,DC=local
Enabled : True
GivenName : R5
Name : Redstone
ObjectClass : user
ObjectGUID : 62e8a6bd-feec-4700-830b-eafdbf5b8faa
SamAccountName : Redstone
SID : S-1-5-21-1938244123-2570910143-1886879425-1121
Surname : Redstone
UserPrincipalName :
# soecify minimum required attributes for UNIX/Linux users with hash table
PS C:\Users\Administrator> Set-ADUser -identity "CN=Redstone,CN=Users,DC=bizantum,DC=local" `
-Add @{uidNumber="5001"; gidNumber="100"; loginShell="/bin/bash"; unixHomeDirectory="/home/Redstone"}
# verify
PS C:\Users\Administrator> Get-ADUser -Identity Redstone -Properties * | Out-String -Stream | Select-String "uidNumber","gidNumber","loginShell","unixHomeDirectory"
gidNumber : 100
loginShell : /bin/bash
uidNumber : 5001
unixHomeDirectory : /home/Redstone
Using Graphical User Interface (GUI)
On GUI configuration, set like follows.
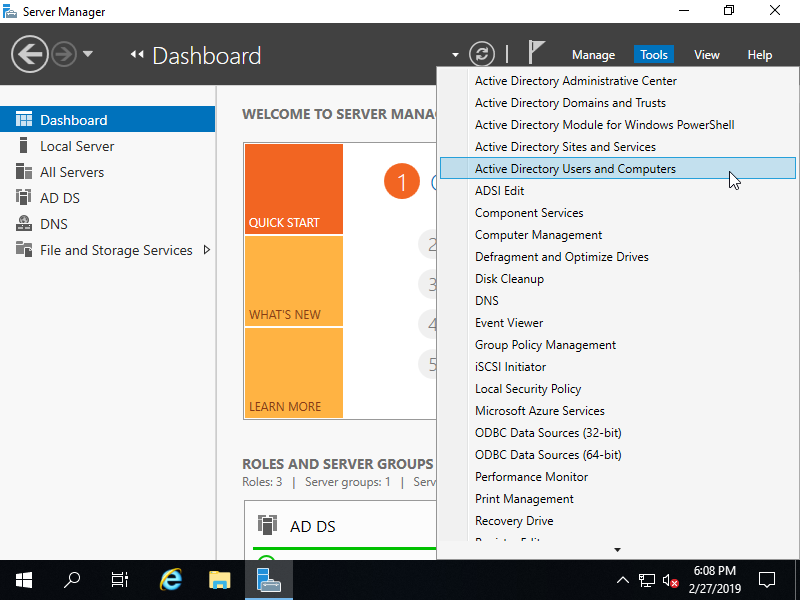
Step [5]Run [Server Manager] and click [Tools] - [Active Directory Users and Conputers].
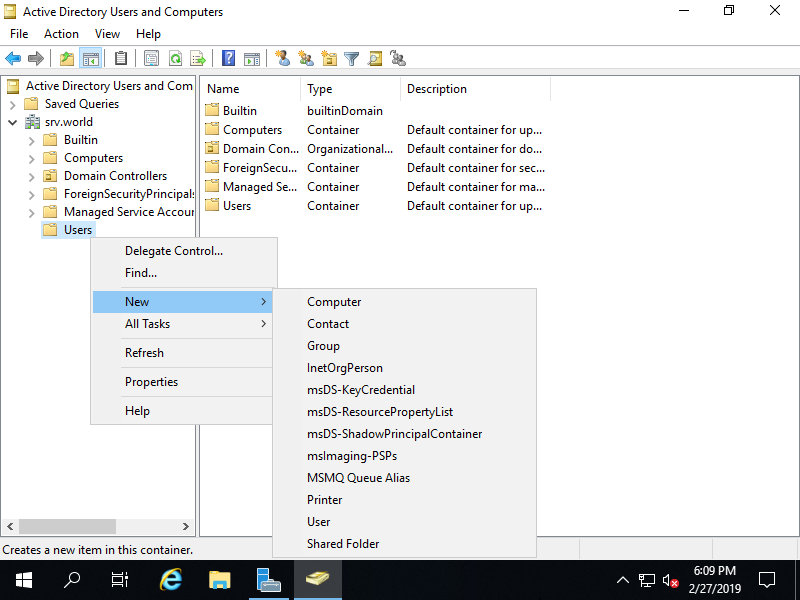
Step [6]Right-Click [Users] on left tree and select [New] - [User].
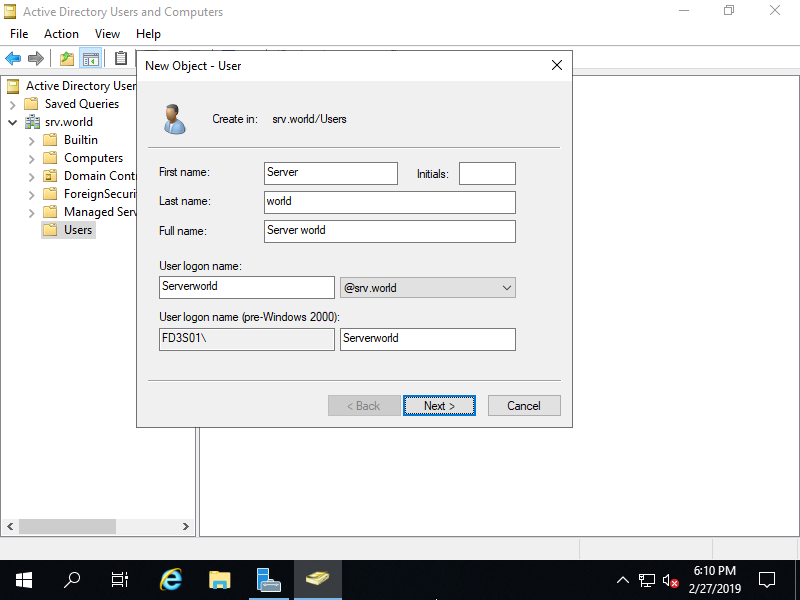
Step [7]Input Username and Logon name for a new user.
Step [8]Set initial password for a new User.
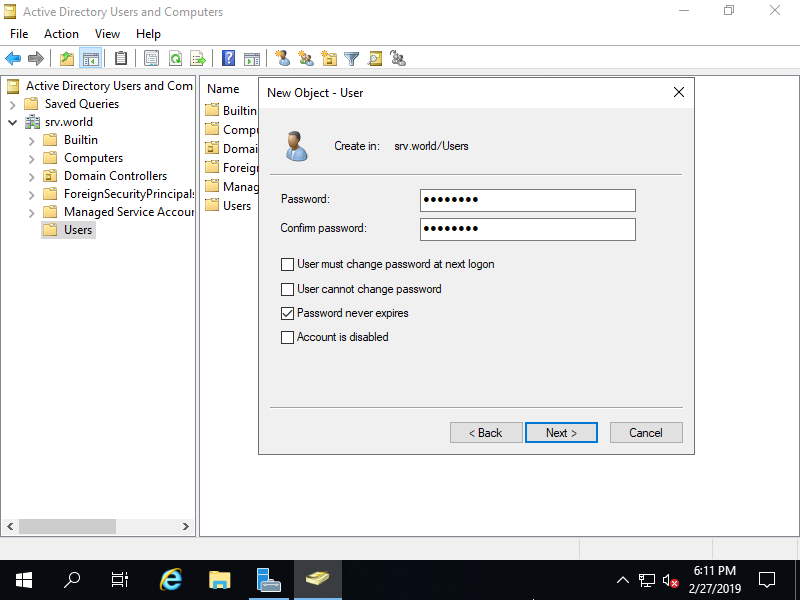
Step [9]Check contents you set and click [Finish] button.
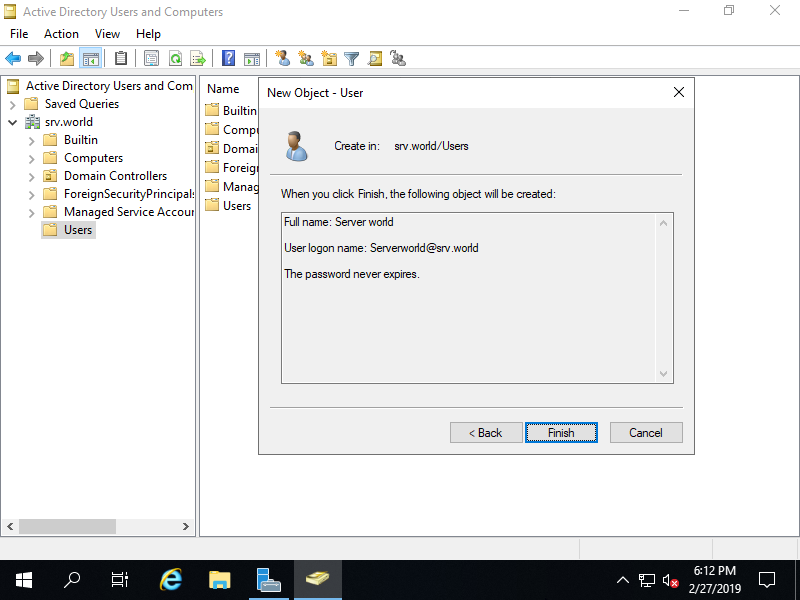
Step [10]A new user is just added.
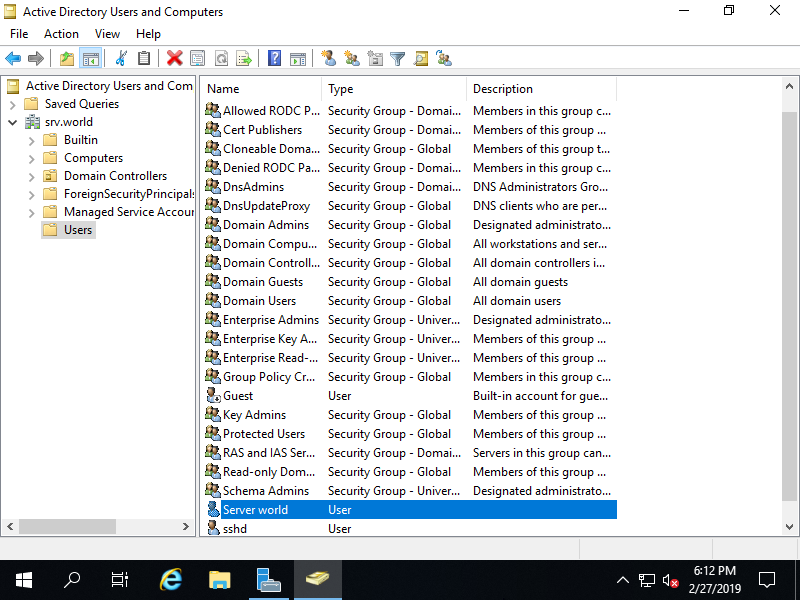
Add Group Account
Using Command Line Interface (CLI)
Run PowerShell with Admin Privilege and Configure like follows.
Step [1]Use [dsadd group] command.
# show current group list
PS C:\Users\Administrator> dsquery group -name *
"CN=Administrators,CN=Builtin,DC=bizantum,DC=local"
"CN=Users,CN=Builtin,DC=bizantum,DC=local"
"CN=Guests,CN=Builtin,DC=bizantum,DC=local"
"CN=Print Operators,CN=Builtin,DC=bizantum,DC=local"
"CN=Backup Operators,CN=Builtin,DC=bizantum,DC=local"
.....
.....
# for example, add [DBAdmin] group
PS C:\Users\Administrator> dsadd group CN=DBAdmin,CN=Users,DC=bizantum,DC=local `
-secgrp yes `
-scope g `
-desc "Database Admin Group"
dsadd succeeded:CN=DBAdmin,CN=Users,DC=bizantum,DC=local
PS C:\Users\Administrator> dsquery group -name DBAdmin
"CN=DBAdmin,CN=Users,DC=bizantum,DC=local"
# options for [dsadd group]
PS C:\Users\Administrator> dsadd group /?
Description: Adds a group to the directory.
Syntax: dsadd group <GroupDN> [-secgrp {yes | no}] [-scope {l | g | u}]
[-samid <SAMName>] [-desc <Description>] [-memberof <Group ...>]
[-members <Member ...>] [{-s <Server> | -d <Domain>}] [-u <UserName>]
[-p {<Password> | *}] [-q] [{-uc | -uco | -uci}]
.....
.....
Step [2]For adding members to a Group, Use [dsmod group] command.
# for example, add [Redstone] user to [DBAdmin] group
PS C:\Users\Administrator> dsmod group CN=DBAdmin,CN=Users,DC=bizantum,DC=local `
-addmbr CN=Redstone,CN=Users,DC=bizantum,DC=local
dsmod succeeded:CN=DBAdmin,CN=Users,DC=bizantum,DC=local
# verify
PS C:\Users\Administrator> dsget group CN=DBAdmin,CN=Users,DC=bizantum,DC=local -members
"CN=Redstone,CN=Users,DC=bizantum,DC=local"
# if delete a member from a group, do like follows
PS C:\Users\Administrator> dsmod group CN=DBAdmin,CN=Users,DC=bizantum,DC=local `
-rmmbr CN=Redstone,CN=Users,DC=bizantum,DC=local
dsmod succeeded:CN=DBAdmin,CN=Users,DC=bizantum,DC=local
Step [3] If you'd like to delete groups, use [dsrm] command.
# for example, delete [DBAdmin] group
PS C:\Users\Administrator> dsrm "CN=DBAdmin,CN=Users,DC=bizantum,DC=local"
Are you sure you wish to delete CN=DBAdmin,CN=Users,DC=bizantum,DC=local (Y/N)? y
dsrm succeeded:CN=DBAdmin,CN=Users,DC=bizantum,DC=local
Step [4]If you use PowerShell, It's possible to use Cmdlet for PowerShell.
# show current group list
PS C:\Users\Administrator> Get-ADGroup -Filter * | Format-Table DistinguishedName
DistinguishedName
-----------------
CN=Administrators,CN=Builtin,DC=bizantum,DC=local
CN=Users,CN=Builtin,DC=bizantum,DC=local
CN=Guests,CN=Builtin,DC=bizantum,DC=local
CN=Print Operators,CN=Builtin,DC=bizantum,DC=local
CN=Backup Operators,CN=Builtin,DC=bizantum,DC=local
.....
.....
# for example, add [DBAdmin] group
PS C:\Users\Administrator> New-ADGroup DBAdmin `
-GroupScope Global `
-GroupCategory Security `
-Description "Database Admin Group"
# verify
PS C:\Users\Administrator> Get-ADGroup -Identity DBAdmin
DistinguishedName : CN=DBAdmin,CN=Users,DC=bizantum,DC=local
GroupCategory : Security
GroupScope : Global
Name : DBAdmin
ObjectClass : group
ObjectGUID : 401cf330-57a3-4352-bb00-8e1932b47036
SamAccountName : DBAdmin
SID : S-1-5-21-1938244123-2570910143-1886879425-1110
# if delete, do like follows
PS C:\Users\Administrator> Remove-ADGroup -Identity "CN=DBAdmin,CN=Users,DC=bizantum,DC=local"
Confirm
Are you sure you want to perform this action?
Performing the operation "Remove" on target "CN=DBAdmin,CN=Users,DC=bizantum,DC=local".
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): Y
# options for [New-ADGroup]
PS C:\Users\Administrator> Get-Help New-ADGroup
NAME
New-ADGroup
SYNOPSIS
Creates an Active Directory group.
SYNTAX
New-ADGroup [-Name] <String> [-GroupScope] {DomainLocal | Global | Universal} [-AuthType {Negotiate | Basic}] [-Cre
dential <PSCredential>] [-Description <String>] [-DisplayName <String>] [-GroupCategory {Distribution | Security}]
[-HomePage <String>] [-Instance <ADGroup>] [-ManagedBy <ADPrincipal>] [-OtherAttributes <Hashtable>] [-PassThru] [-
Path <String>] [-SamAccountName <String>] [-Server <String>] [-Confirm] [-WhatIf] [<CommonParameters>]
.....
.....
Using Graphical User Interface (GUI)
On GUI configuration, set like follows.
Step [5]Run [Server Manager] and open [Tools] - [Active Directory Users and Conputers], next, Click with right button [Users] on left tree and select [New] - [Group].
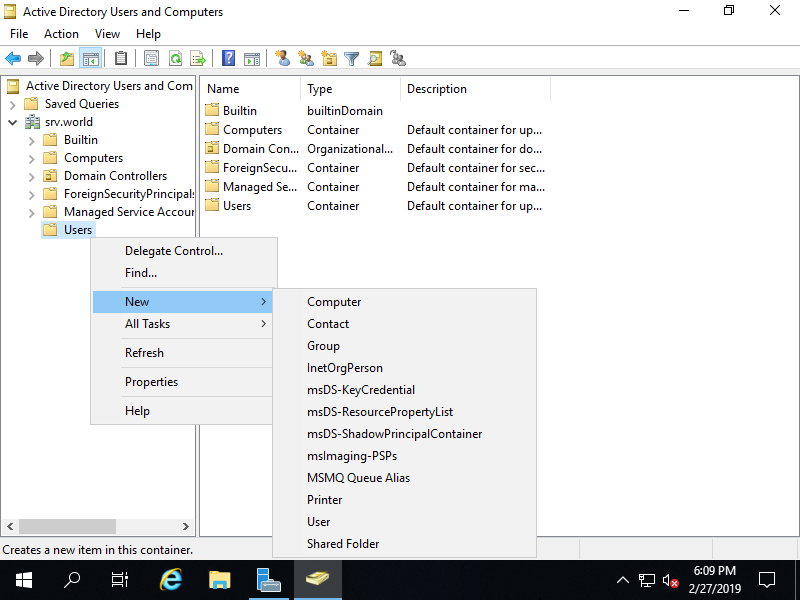
Step [6]Input a Group name you'd like to add.
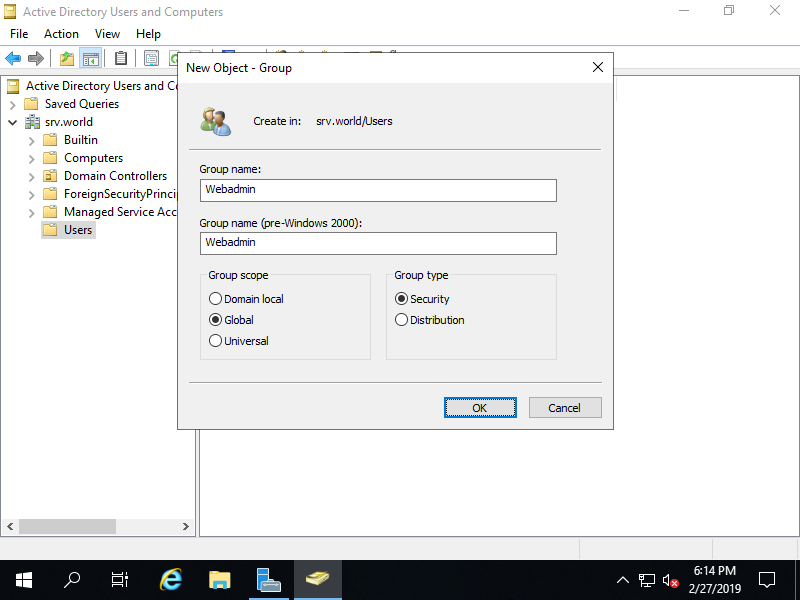
Step [7]A new Group is just added.
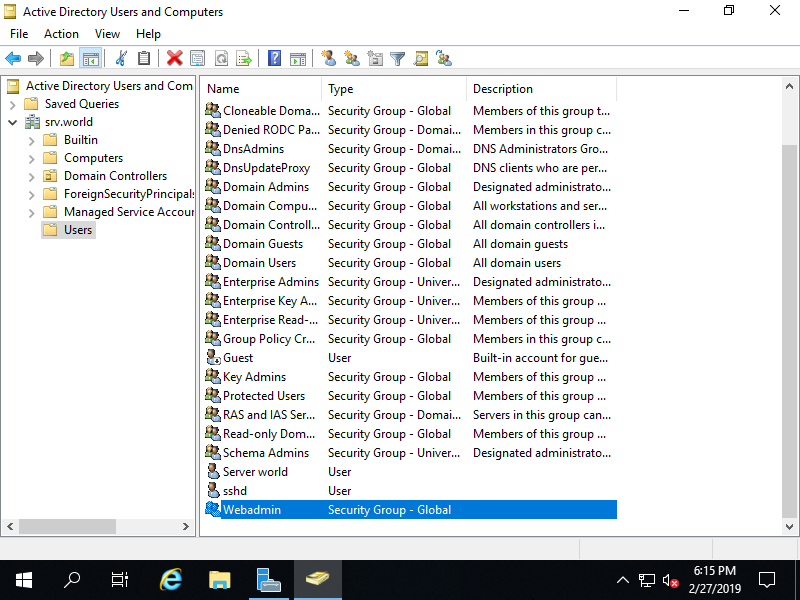
Step [8]For adding users in a Group, Right Click the Group and Open [Properties].
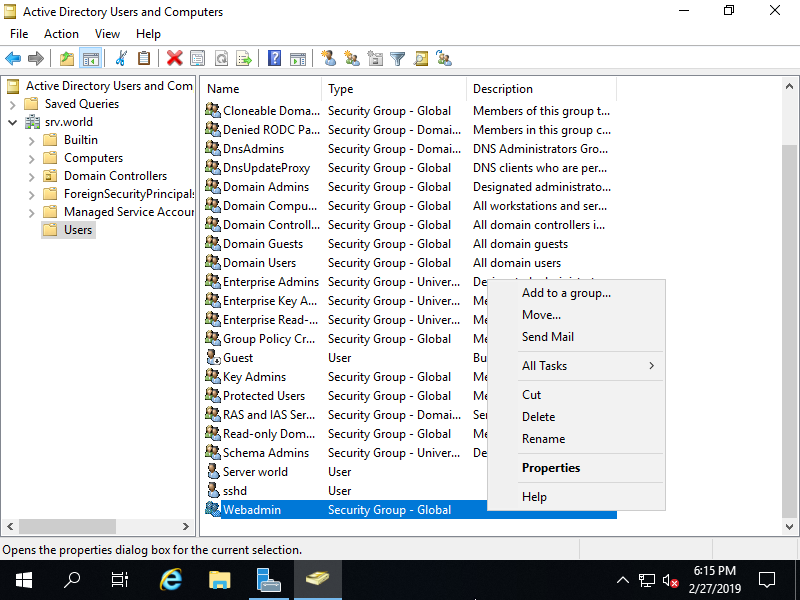
Step [9]Move to [Member] tab and Click [Add] button.
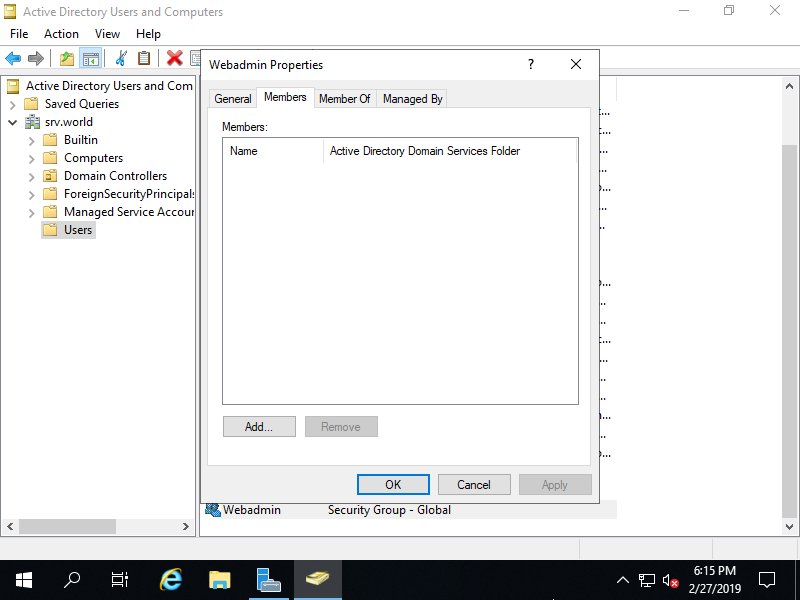
Step [10]Input a user you'd like to add to this Group and Click [OK].
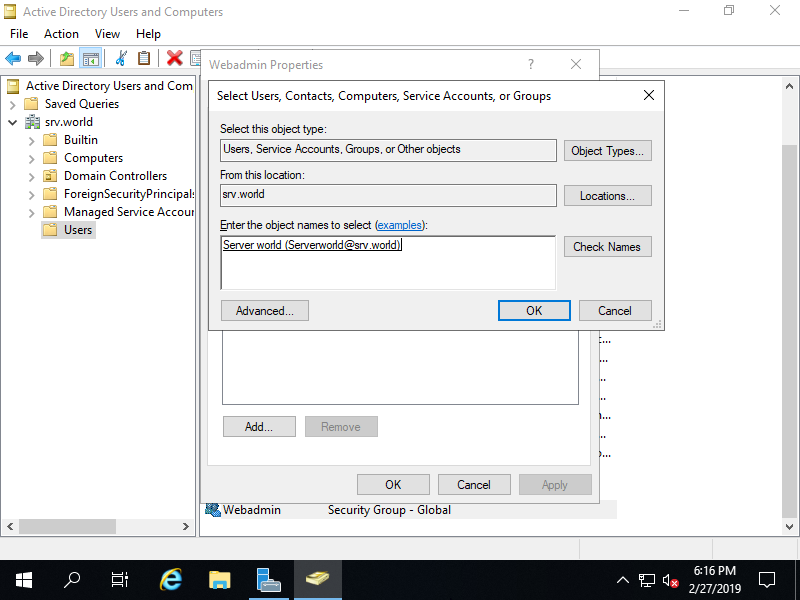
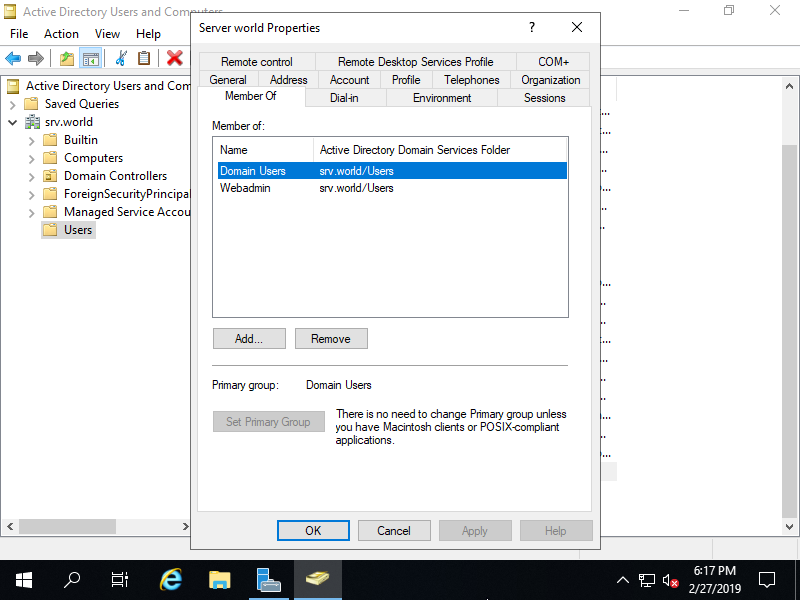
Step [11]Confirm the Properties of the user you added to the Group.
Add Organization Unit
Using Command Line Interface (CLI)
Run PowerShell with Admin Privilege and Configure like follows.
Step [1]Use [dsadd ou] command. The command does not have an option to enable [Protect container from accidental deletion], but if you'd like to enable it, Use PowerShell Cmdlet refer to the Step [3].
# show current Organizational Unit list
PS C:\Users\Administrator> dsquery ou -name *
"OU=Domain Controllers,DC=bizantum,DC=local"
# for example, add an Organizational Unit [Hiroshima]
PS C:\Users\Administrator> dsadd ou OU=Hiroshima,DC=bizantum,DC=local
dsadd succeeded:OU=Hiroshima,DC=bizantum,DC=local
PS C:\Users\Administrator> dsquery ou -name Hiroshima
"OU=Hiroshima,DC=bizantum,DC=local"
# for adding OU under the existing OU, specifu the Path like follows
# add an OU [Development01] under the OU [Hiroshima]
PS C:\Users\Administrator> dsadd ou OU=Development01,OU=Hiroshima,DC=bizantum,DC=local
dsadd succeeded:OU=Development01,OU=Hiroshima,DC=bizantum,DC=local
# options for [dsadd ou]
PS C:\Users\Administrator> dsadd ou /?
Description: Adds an organizational unit to the directory
Syntax: dsadd ou <OrganizationalUnitDN> [-desc <Description>]
[{-s <Server> | -d <Domain>}] [-u <UserName>]
[-p {<Password> | *}] [-q] [{-uc | -uco | -uci}]
.....
.....
Step [2]If you'd like to delete Organizational Units, use [dsrm] command. This command is based on the case the option [Protect container from accidental deletion] is not enabled for Organizational Unit, if enabled, Use PowerShell Cmdlet refer to the Step [3].
# for example, delete an OU [Development01]
PS C:\Users\Administrator> dsquery ou -name Development01
"OU=Development01,OU=Hiroshima,DC=bizantum,DC=local"
PS C:\Users\Administrator> dsrm "OU=Development01,OU=Hiroshima,DC=bizantum,DC=local"
Are you sure you wish to delete OU=Development01,OU=Hiroshima,DC=bizantum,DC=local (Y/N)? y
dsrm succeeded:OU=Development01,OU=Hiroshima,DC=bizantum,DC=local
Step [3]If you use PowerShell, It's possible to use Cmdlet for PowerShell.
# show current Organizational Unit list
PS C:\Users\Administrator> Get-ADOrganizationalUnit -Filter * | Format-Table DistinguishedName
DistinguishedName
-----------------
OU=Domain Controllers,DC=bizantum,DC=local
OU=Hiroshima,DC=bizantum,DC=local
# for example, add [Development01] under the [Hiroshima]
PS C:\Users\Administrator> New-ADOrganizationalUnit Development01 `
-Path "OU=Hiroshima,DC=bizantum,DC=local" `
-ProtectedFromAccidentalDeletion $True
# verify
PS C:\Users\Administrator> Get-ADOrganizationalUnit -Filter * | Format-Table DistinguishedName
DistinguishedName
-----------------
OU=Domain Controllers,DC=bizantum,DC=local
OU=Hiroshima,DC=bizantum,DC=local
OU=Development01,OU=Hiroshima,DC=bizantum,DC=local
# if the option [ProtectedFromAccidentalDeletion] is enabled,
# disable it first and delete it
PS C:\Users\Administrator> Set-ADOrganizationalUnit `
-Identity "OU=Development01,OU=Hiroshima,DC=bizantum,DC=local" `
-ProtectedFromAccidentalDeletion $false
PS C:\Users\Administrator> Remove-ADOrganizationalUnit -Identity "OU=Development01,OU=Hiroshima,DC=bizantum,DC=local"
Confirm
Are you sure you want to perform this action?
Performing the operation "Remove" on target "OU=Development01,OU=Hiroshima,DC=bizantum,DC=local".
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): Y
# options for [New-ADOrganizationalUnit]
PS C:\Users\Administrator> Get-Help New-ADOrganizationalUnit
NAME
New-ADOrganizationalUnit
SYNOPSIS
Creates a new Active Directory organizational unit.
SYNTAX
New-ADOrganizationalUnit [-Name] <String> [-AuthType {Negotiate | Basic}] [-City <String>] [-Country <String>] [-Cr
edential <PSCredential>] [-Description <String>] [-DisplayName <String>] [-Instance <ADOrganizationalUnit>] [-Manag
edBy <ADPrincipal>] [-OtherAttributes <Hashtable>] [-PassThru] [-Path <String>] [-PostalCode <String>] [-ProtectedF
romAccidentalDeletion <Boolean>] [-Server <String>] [-State <String>] [-StreetAddress <String>] [-Confirm] [-WhatIf
] [<CommonParameters>]
.....
.....
Using Graphical User Interface (GUI)
On GUI configuration, set like follows.
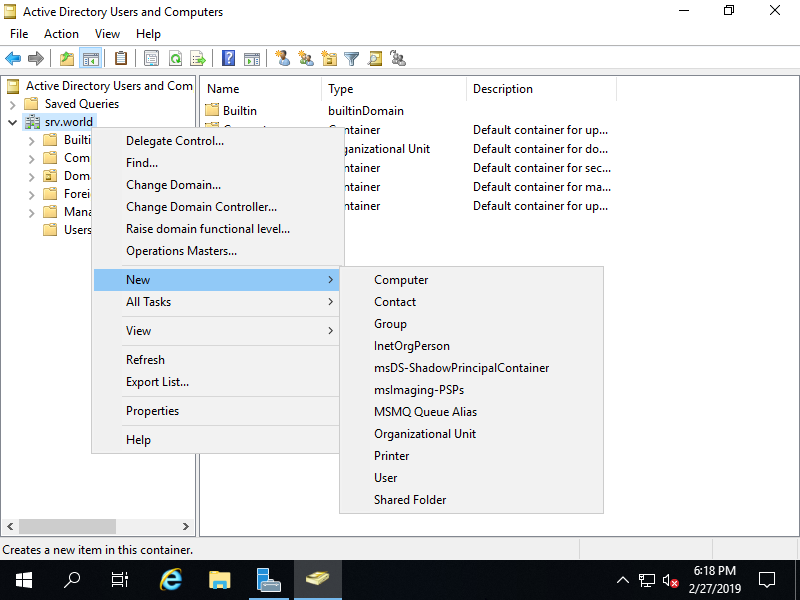
Step [4]Run [Server Manager] and open [Tools] - [Active Directory Users and Conputers], next, right-Click your domain name on the left tree and select [New] - [Organizational Unit].
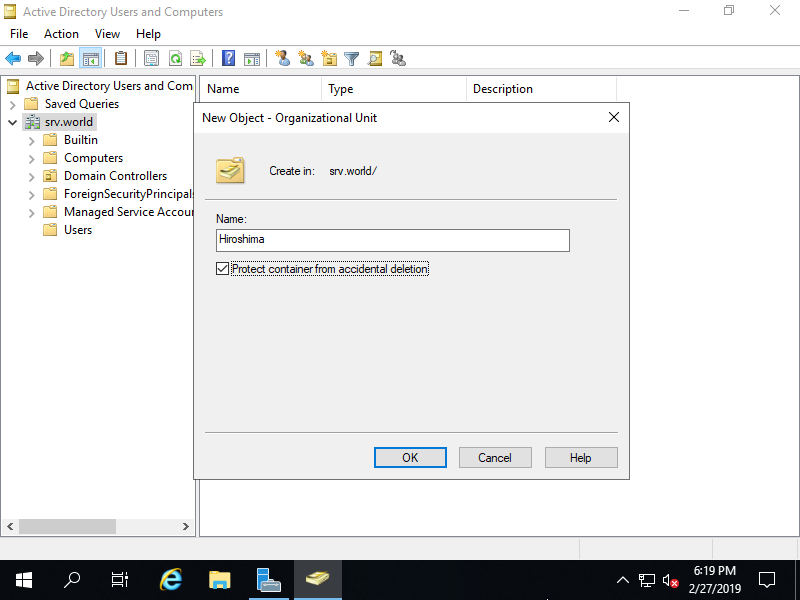
Step [5]Set any name you like.
Step [6] A new Organizational Unit is just created.
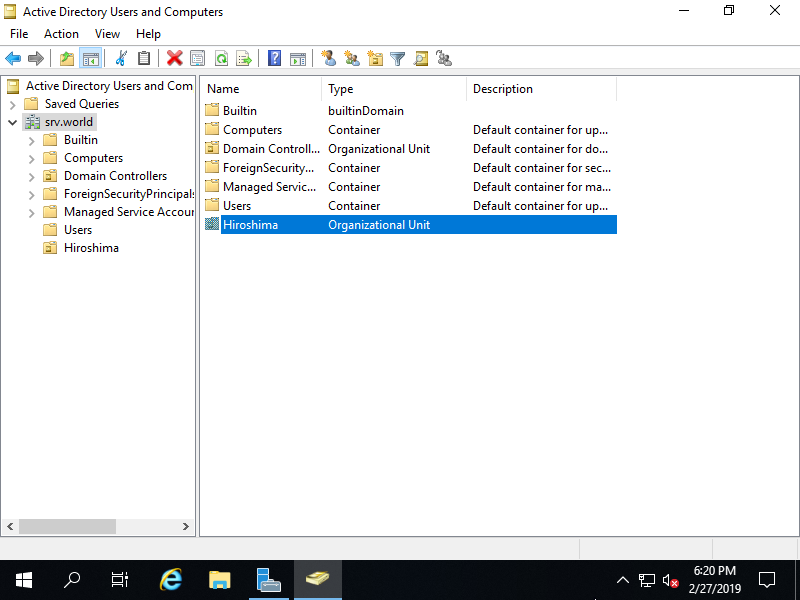
Step [7]It's possible to configure hierarchical design for Organizational Unit.
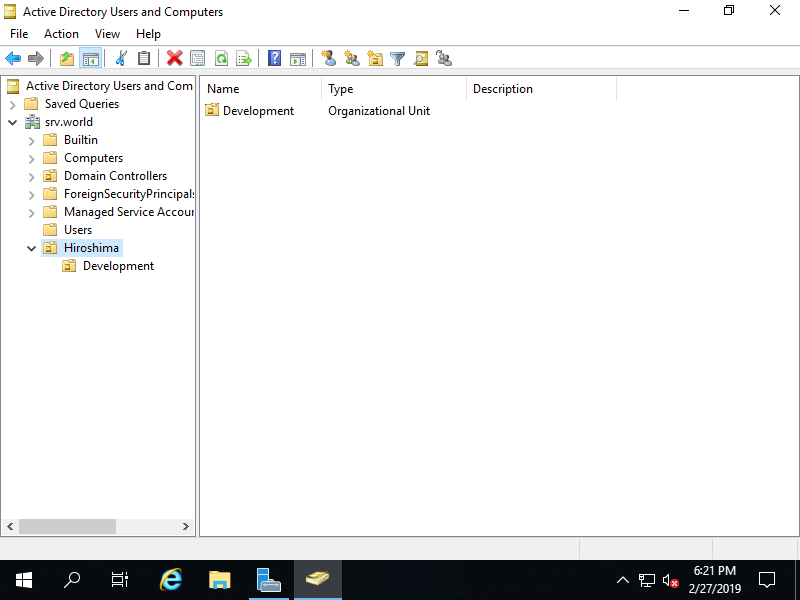
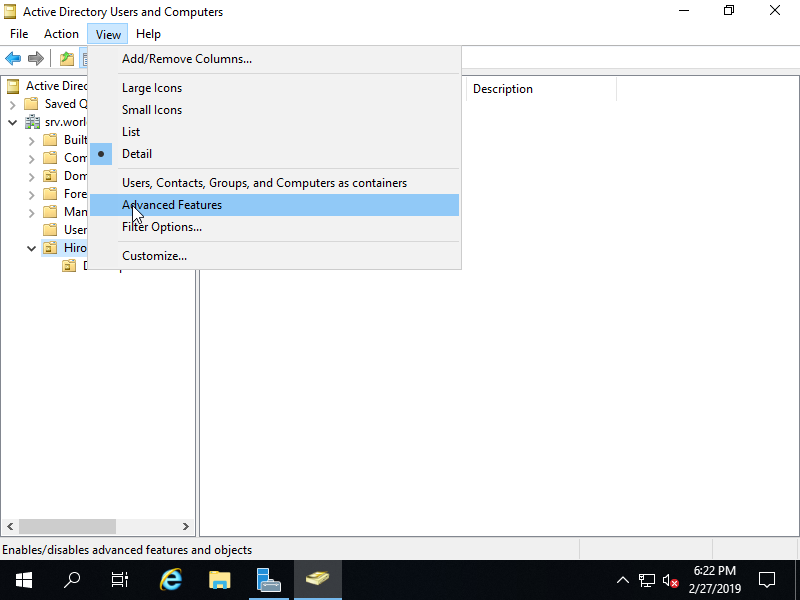
Step [8]By default, the option [Protect container from accidental deletion] is enabled for Organizational Units, so it's impossible to delete them. If you'd like to delete them, disable the option first like follows. Select [View] - [Advanced Features].
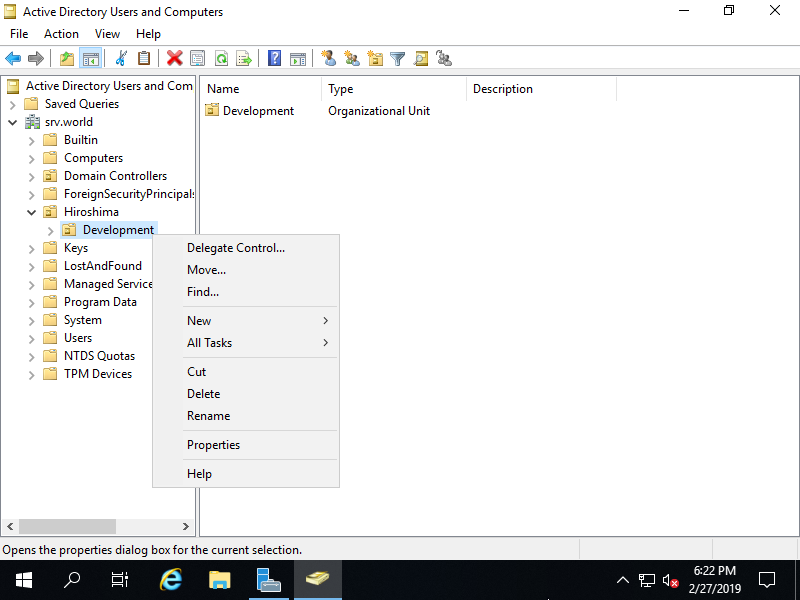
Step [9]Right Click the Organizational Unit you'd like to delete and open [Properties].
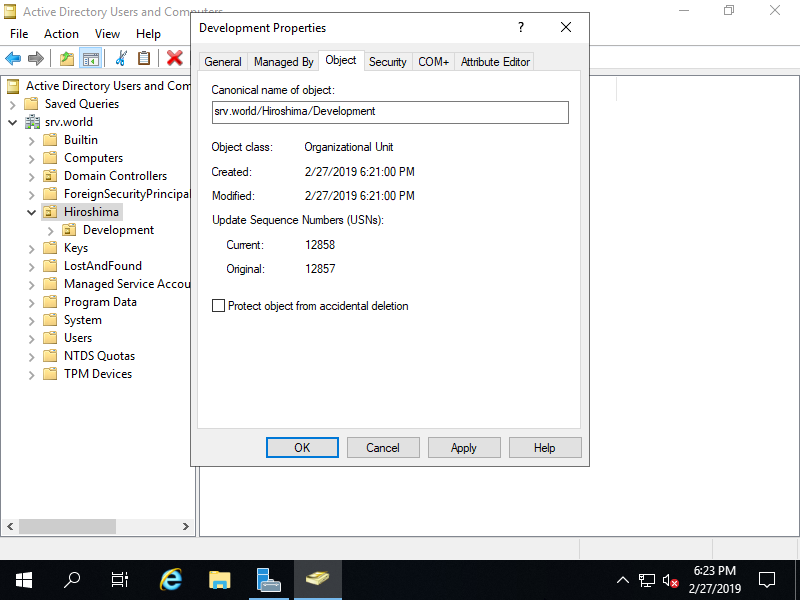
Step [10]Move to [Object] tab and un-check a box [Protect container from accidental deletion], then you can delete this Organizational Unit.
Add Computer Account
Using Command Line Interface (CLI)
Run PowerShell with Admin Privilege and Configure like follows.
Step [1]Use [dsadd computer] command.
# show current computer list
PS C:\Users\Administrator> dsquery computer -name *
"CN=FD3S,OU=Domain Controllers,DC=bizantum,DC=local"
"CN=RX-5,CN=Computers,DC=bizantum,DC=local"
# for example, add a computer [RX-7] under the [Computers]
PS C:\Users\Administrator> dsadd computer CN=RX-7,CN=Computers,DC=bizantum,DC=local
dsadd succeeded:CN=RX-7,CN=Computers,DC=bizantum,DC=local
PS C:\Users\Administrator> dsquery computer -name RX-7
"CN=RX-7,CN=Computers,DC=bizantum,DC=local"
# options for [dsadd computer]
PS C:\Users\Administrator> dsadd computer /?
Description: Adds a computer to the directory.
Syntax: dsadd computer <ComputerDN> [-samid <SAMName>] [-desc <Description>]
[-loc <Location>] [-memberof <Group ...>]
[{-s <Server> | -d <Domain>}] [-u <UserName>]
[-p {<Password> | *}] [-q] [{-uc | -uco | -uci}]
.....
.....
Step [2]If you'd like to delete Computer Accounts, use [dsrm] command.
# for example, delete a computer [RX-7]
PS C:\Users\Administrator> dsquery computer -name RX-7
"CN=RX-7,CN=Computers,DC=bizantum,DC=local"
PS C:\Users\Administrator> dsrm "CN=RX-7,CN=Computers,DC=bizantum,DC=local"
Are you sure you wish to delete CN=RX-7,CN=Computers,DC=bizantum,DC=local (Y/N)? y
dsrm succeeded:CN=RX-7,CN=Computers,DC=bizantum,DC=local
Step [3]If you use PowerShell, It's possible to use Cmdlet for PowerShell.
# show current computer list
PS C:\Users\Administrator> Get-ADComputer -Filter * | Format-Table DistinguishedName
DistinguishedName
-----------------
CN=FD3S,OU=Domain Controllers,DC=bizantum,DC=local
CN=RX-7,CN=Computers,DC=bizantum,DC=local
# for example, add a computer [RX-9]
PS C:\Users\Administrator> New-ADComputer -Name RX-9
# verify
PS C:\Users\Administrator> Get-ADComputer -Filter * | Format-Table DistinguishedName
DistinguishedName
-----------------
CN=FD3S,OU=Domain Controllers,DC=bizantum,DC=local
CN=RX-7,CN=Computers,DC=bizantum,DC=local
CN=RX-9,CN=Computers,DC=bizantum,DC=local
# for adding computer with some parameters like OU or admin account
PS C:\Users\Administrator> New-ADComputer -Name RX-8 `
-Path "OU=Computers,OU=Hiroshima,DC=bizantum,DC=local" `
-ManagedBy "CN=Bizantum,CN=Users,DC=bizantum,DC=local"
# if delete, do like follows
PS C:\Users\Administrator> Remove-ADComputer -Identity "CN=RX-9,CN=Computers,DC=bizantum,DC=local"
Confirm
Are you sure you want to perform this action?
Performing the operation "Remove" on target "CN=RX-9,CN=Computers,DC=bizantum,DC=local".
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): Y
# options for [New-ADComputer]
PS C:\Users\Administrator> Get-Help New-ADComputer
NAME
New-ADComputer
SYNOPSIS
Creates a new Active Directory computer.
SYNTAX
New-ADComputer [-Name] <String> [-AccountExpirationDate <DateTime>] [-AccountNotDelegated <Boolean>] [-AccountPassw
ord <SecureString>] [-AllowReversiblePasswordEncryption <Boolean>] [-AuthenticationPolicy <ADAuthenticationPolicy>]
[-AuthenticationPolicySilo <ADAuthenticationPolicySilo>] [-AuthType {Negotiate | Basic}] [-CannotChangePassword <B
oolean>] [-Certificates <X509Certificate[]>] [-ChangePasswordAtLogon <Boolean>] [-CompoundIdentitySupported <Boolea
n>] [-Credential <PSCredential>] [-Description <String>] [-DisplayName <String>] [-DNSHostName <String>] [-Enabled
<Boolean>] [-HomePage <String>] [-Instance <ADComputer>] [-KerberosEncryptionType {None | DES | RC4 | AES128 | AES2
56}] [-Location <String>] [-ManagedBy <ADPrincipal>] [-OperatingSystem <String>] [-OperatingSystemHotfix <String>]
[-OperatingSystemServicePack <String>] [-OperatingSystemVersion <String>] [-OtherAttributes <Hashtable>] [-PassThru
] [-PasswordNeverExpires <Boolean>] [-PasswordNotRequired <Boolean>] [-Path <String>] [-PrincipalsAllowedToDelegate
ToAccount <ADPrincipal[]>] [-SAMAccountName <String>] [-Server <String>] [-ServicePrincipalNames <String[]>] [-Trus
tedForDelegation <Boolean>] [-UserPrincipalName <String>] [-Confirm] [-WhatIf] [<CommonParameters>]
.....
.....
Using Graphical User Interface (GUI)
By default settings, if you don't add Computer Accounts by yourself, Computers can join in Domain with common users rights who don't have admin privileges. So if you'd like to limit authentication users when computers join to Domain, Add Computer Accounts beforehand.
On GUI configuration, set like follows.
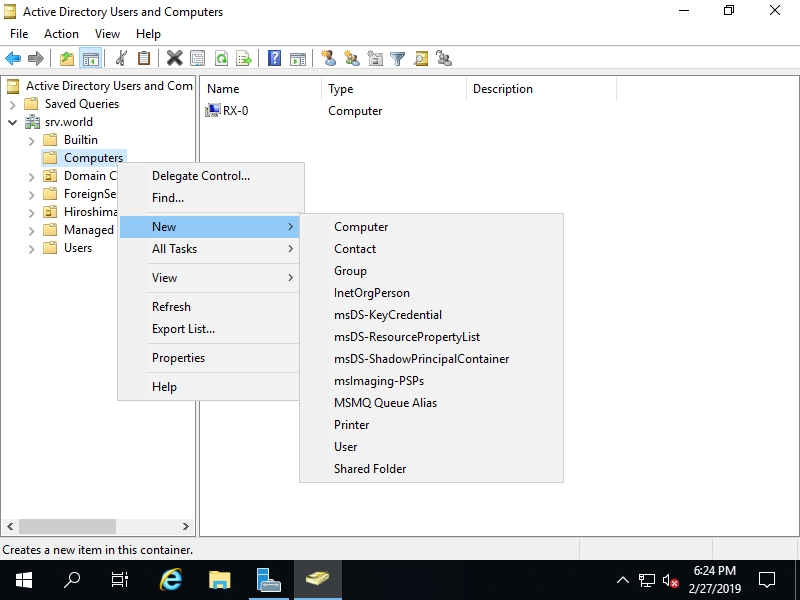
Step [4]Run [Server Manager] and open [Tools] - [Active Directory Users and Conputers], next, right-Click [Computers] on the left tree and select [New] - [Computer].
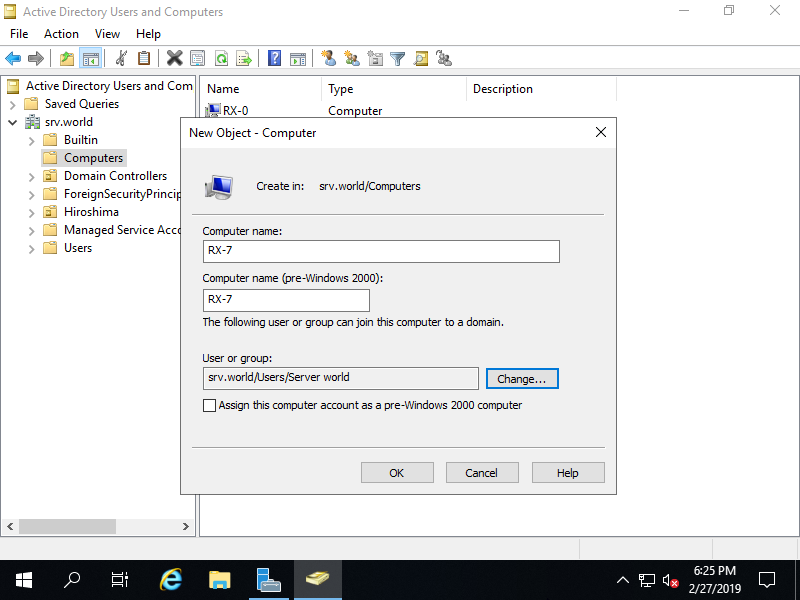
Step [5]Input a new Computer name. By default, the users when used for authentication to join in Domain are [Domain Admins] group users, but if yoy'd like to change it, it's possbile to change it on [User or group] field.
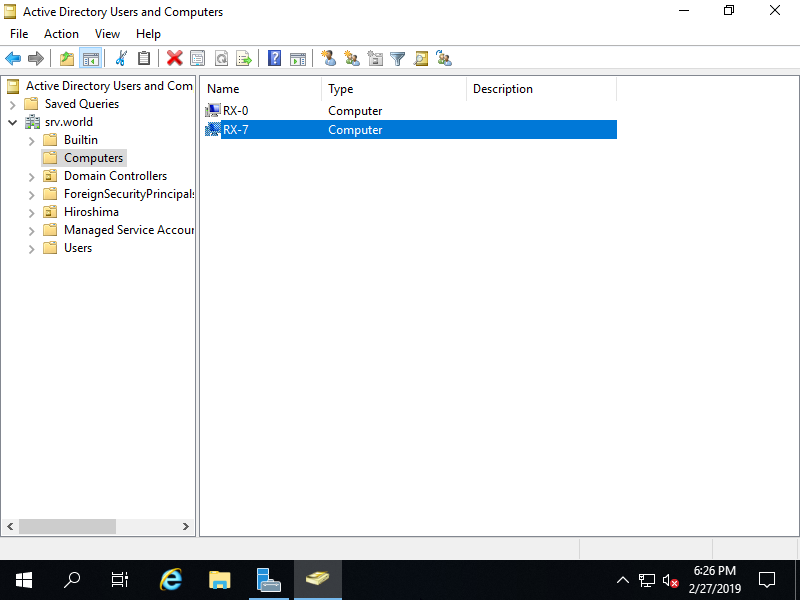
Step [6]A new Computer is just added.
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.