
Introduction
Debian 12 "Bookworm" is the latest stable release of the Debian operating system, known for its reliability, security, and extensive software repository. Configuring the basic settings of Debian 12 is essential to ensure a smooth and optimized experience. This guide will walk you through the initial setup and basic configurations to get your system up and running efficiently.
User Accounts
If you'd like to add new user accounts, configure like follows.
Step [1]For example, Add a [bookworm] user.
root@bizantum:~# adduser bookworm
Adding user `bookworm' ...
Adding new group `bookworm' (1001) ...
Adding new user `bookworm' (1001) with group `bookworm' ...
Creating home directory `/home/bookworm' ...
Copying files from `/etc/skel' ...
New password: # set user password
Retype new password: # confirm
passwd: password updated successfully
Changing the user information for bookworm
Enter the new value, or press ENTER for the default
Full Name []: # input user info (OK with empty all if you do not need)
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n] y
root@bizantum:~#
Step [2]If you'd like to limit users to switch to root user account, configure like follows. For example, Configure that only [bookworm] user can switch to root account with [su] command.
root@bizantum:~# usermod -aG adm bookworm
root@bizantum:~# vi /etc/pam.d/su
# line 15 : uncomment and add the group
auth required pam_wheel.so group=adm
Step [3]If you'd like to remove user accounts, configure like follows.
# remove a user [bookworm] (only removed user account)
root@bizantum:~# deluser bookworm
# remove a user [bookworm] (removed user account and his home directory)
root@bizantum:~# deluser bookworm --remove-home
Command Alias
Set Command Alias for some commands that are often used.
Step [1] Apply to all users as defaults.
root@bizantum:~# vi /etc/profile.d/command_alias.sh
# create new file
# add alias you'd like to set
alias ll='ls $LS_OPTIONS -l'
alias l='ls $LS_OPTIONS -lA'
alias rm='rm -i'
alias cp='cp -i'
alias mv='mv -i'
# reload
root@bizantum:~# source /etc/profile.d/command_alias.sh
Step [2]Apply to a user. For example, a user [bookworm] applies alias for itself.
bookworm@bizantum:~$ vi ~/.bashrc
# add to the end : add alias you'd like to set
alias ll='ls $LS_OPTIONS -l'
alias l='ls $LS_OPTIONS -lA'
alias rm='rm -i'
alias cp='cp -i'
alias mv='mv -i'
bookworm@bizantum:~$ source ~/.bashrc
Manage Network
Change to static IP addres if you use Debian as a server.
Step [1]The interface name [enp1s0] is different on each environment, replace it to your own one.
root@bizantum:~# vi /etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
allow-hotplug enp1s0
# comment out
#iface enp1s0 inet dhcp
# add static settings
iface enp1s0 inet static
# IP address
address 10.0.0.30
# network address
network 10.0.0.0
# subnet mask
netmask 255.255.255.0
# broadcast address
broadcast 10.0.0.255
# default gateway
gateway 10.0.0.1
# name server
dns-nameservers 10.0.0.10
root@bizantum:~# systemctl restart ifup@enp1s0
root@bizantum:~# ip address
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:43:5b:f5 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.30/24 brd 10.0.0.255 scope global enp1s0
valid_lft forever preferred_lft forever
inet6 fe80::5054:ff:fe43:5bf5/64 scope link
valid_lft forever preferred_lft forever
# For nameservers,
# if resolvconf or Networkmanager programs have not been installed and also
# you set static IP address, it needs to edit [/etc/resolv.conf] by hand
# if you installed OS with only [Standard system utilties], they have not been installed like follows
root@bizantum:~# systemctl status resolvconf.service NetworkManager.service
Unit resolvconf.service could not be found.
Unit NetworkManager.service could not be found.
root@bizantum:~# vi /etc/resolv.conf
# set your domainame and nameserver
domain dns.bizantum.local
search dns.bizantum.local
nameserver 10.0.0.10
Step [2]Disable IPv6 if you do not need it.
root@bizantum:~# echo "net.ipv6.conf.all.disable_ipv6 = 1" >> /etc/sysctl.conf
root@bizantum:~# sysctl -p
net.ipv6.conf.all.disable_ipv6 = 1
root@bizantum:~# ip address
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:43:5b:f5 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.30/24 brd 10.0.0.255 scope global enp1s0
valid_lft forever preferred_lft forever
Manage Services
To see services status or enable/disable services, Configure like follows.
Step [1]Display services.
# display services which are running
# to add [--all], display all included inactive servises
# to add [--no-pager], do not use pagers like [less/more]
root@bizantum:~# systemctl -t service
UNIT
apparmor.service
blk-availability.service
console-setup.service
cron.service
dbus.service
.....
.....
systemd-user-sessions.service
user-runtime-dir@0.service
user@0.service
LOAD = Reflects whether the unit definition was properly loaded.
ACTIVE = The high-level unit activation state, i.e. generalization of SUB.
SUB = The low-level unit activation state, values depend on unit type.
33 loaded units listed. Pass --all to see loaded but inactive units, too.
To show all installed unit files use 'systemctl list-unit-files'.
# display list of all services' setting
root@bizantum:~# systemctl list-unit-files -t service
UNIT FILE STATE VENDOR PRESET
apparmor.service enabled enabled
apt-daily-upgrade.service static -
apt-daily.service static -
autovt@.service alias -
blk-availability.service enabled enabled
console-getty.service disabled disabled
console-setup.service enabled enabled
.....
.....
systemd-volatile-root.service static -
udev.service alias -
user-runtime-dir@.service static -
user@.service static -
x11-common.service masked enabled
117 unit files listed.
Step [2]If there are some unnecessary services, it's possible to Stop and turn OFF auto-start setting like follows. (possible to omit [.service] words).
root@bizantum:~# systemctl stop apparmor
root@bizantum:~# systemctl disable apparmor
Manage Sudo
Configure Sudo to separate users' duty if some people share privileges.
Step [1]Install Sudo.
root@bizantum:~# apt -y install sudo
Step [2]Transfer root privilege to a user all.
root@bizantum:~# visudo
# add to the end : user [bookworm] can use all root privilege
# how to write ⇒ destination host=(owner) command
bookworm ALL=(ALL:ALL) ALL
# push [Ctrl + x] key to quit visudo
# verify with user [bookworm]
bookworm@bizantum:~$ cat /etc/shadow
cat: /etc/shadow: Permission denied
# denied
bookworm@bizantum:~$ sudo cat /etc/shadow
[sudo] password for bookworm: # bookworm's password
root:xxxxxxxxxx:19520:0:99999:7:::
daemon:*:19520:0:99999:7:::
bin:*:19520:0:99999:7:::
sys:*:19520:0:99999:7:::
sync:*:19520:0:99999:7:::
.....
.....
# possible executed
Step [3]In addition to the setting [1], set that some commands are not allowed.
root@bizantum:~# visudo
# add alias for the kind of shutdown commands
# Cmnd alias specification
Cmnd_Alias SHUTDOWN = /usr/sbin/halt, /usr/sbin/shutdown, \
/usr/sbin/poweroff, /usr/sbin/reboot, /usr/sbin/init, /usr/bin/systemctl
# add ( commands in alias [SHUTDOWN] are not allowed )
bookworm ALL=(ALL:ALL) ALL, !SHUTDOWN
# verify with user [bookworm]
bookworm@bizantum:~$ sudo /usr/sbin/reboot
[sudo] password for bookworm:
Sorry, user bookworm is not allowed to execute '/usr/sbin/reboot' as root on bizantum.
# denied as setting
Step [4]Transfer some commands with root privilege to users in a group.
root@bizantum:~# visudo
# add alias for the kind of user management commands
# Cmnd alias specification
Cmnd_Alias USERMGR = /usr/sbin/adduser, /usr/sbin/useradd, /usr/sbin/newusers, \
/usr/sbin/deluser, /usr/sbin/userdel, /usr/sbin/usermod, /usr/bin/passwd
# add to the end
%usermgr ALL=(ALL:ALL) USERMGR
root@bizantum:~# groupadd usermgr
root@bizantum:~# usermod -aG usermgr bookworm
# verify with user [bookworm]
bookworm@bizantum:~$ sudo /usr/sbin/useradd testuser
bookworm@bizantum:~$
bookworm@bizantum:~$ sudo /usr/bin/passwd testuser
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
# possible execute
Step [5]Transfer some specific commands with root privilege to a user.
root@bizantum:~# visudo
# add to the end : set specific commands to each user
fedora ALL=(ALL:ALL) /usr/sbin/visudo
debian ALL=(ALL:ALL) /usr/sbin/adduser, /usr/sbin/useradd, /usr/sbin/newusers, \
/usr/sbin/deluser, /usr/sbin/userdel, /usr/sbin/usermod, /usr/bin/passwd
ubuntu ALL=(ALL:ALL) /usr/bin/vim
# verify with user [fedora]
fedora@bizantum:~$ sudo /usr/sbin/visudo
# possible open and edit
## Sudoers allows particular users to run various commands as
## the root user, without needing the root password.
##
# verify with user [debian]
debian@bizantum:~$ sudo /usr/sbin/userdel -r testuser
debian@bizantum:~$ # possible execute
# verify with user [ubuntu]
ubuntu@bizantum:~$ sudo /usr/bin/vim /root/.profile
# possible open and edit
# ~/.profile: executed by Bourne-compatible login shells.
Step [6]It's possible to display Sudo logs on Journald like follows.
root@bizantum:~# journalctl -t sudo
Jun 14 00:03:05 debian sudo[1656]: bookworm : TTY=ttyS0 ; PWD=/home/bookworm ; USER=root ; COMMAND=/usr/bin/cat /etc/shadow
Jun 14 00:03:05 debian sudo[1656]: pam_unix(sudo:session): session opened for user root(uid=0) by root(uid=1001)
Jun 14 00:03:05 debian sudo[1656]: pam_unix(sudo:session): session closed for user root
Jun 14 00:09:41 debian sudo[1687]: bookworm : TTY=ttyS0 ; PWD=/home/bookworm ; USER=root ; COMMAND=/usr/bin/ls -l /root
Jun 14 00:09:41 debian sudo[1687]: pam_unix(sudo:session): session opened for user root(uid=0) by root(uid=1001)
Jun 14 00:09:41 debian sudo[1687]: pam_unix(sudo:session): session closed for user root
APT Sources
Configure APT Sources that are used when running [apt] command.
Step [1]If you installed Debian from DVD media, DVD was set as main source, however if it's not necessary anymore, change APT source settings.
root@bizantum:~# vi /etc/apt/sources.list
# comment out DVD source and add network source
#deb cdrom:[Debian GNU/Linux 11.0.0 _Bullseye_ - Official amd64 DVD Binary-1 20210814-10:04]/ bullseye contrib main
deb http://deb.debian.org/debian/ bookworm main non-free-firmware
# if comment outed
# uncomment it to enable [security] source
deb http://security.debian.org/debian-security bookworm-security main non-free-firmware
# if comment outed
# uncomment it to enable [updates] source
deb http://deb.debian.org/debian/ bookworm-updates main non-free-firmware
Step [2]Add Backports source with: https://backports.debian.org/Instructions/
root@bizantum:~# vi /etc/apt/sources.list
# add to the end
deb http://deb.debian.org/debian/ bookworm-backports main non-free-firmware
Step [3]After changing APT source settings, update source lists.
root@bizantum:~# apt update
Hit:1 http://deb.debian.org/debian bookworm InRelease
Hit:2 http://deb.debian.org/debian bookworm-updates InRelease
Hit:3 http://security.debian.org/debian-security bookworm-security InRelease
Get:4 http://deb.debian.org/debian bookworm-backports InRelease [49.7 kB]
Fetched 49.7 kB in 0s (101 kB/s)
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
All packages are up to date.
Update System
After it has been a production System, maybe it's difficult to update System, but at least after installing, Update Debian Server to the latest.
Step [1]Update your Debian Server.
root@bizantum:~# apt update
Hit:1 http://security.debian.org/debian-security bookworm-security InRelease
Hit:2 http://deb.debian.org/debian bookworm InRelease
Hit:3 http://deb.debian.org/debian bookworm-updates InRelease
Hit:4 http://deb.debian.org/debian bookworm-backports InRelease
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
All packages are up to date.
Step [2]Upgrade your Debian Server.
root@bizantum:~# apt -y upgrade
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
Calculating upgrade... Done
The following packages will be upgraded:
.....
.....
.....
Configure SSH
SSH Server
Configure SSH Server to manage a server from the remote computer. SSH uses 22/TCP.
Step [1]Password Authentication for OpenSSH Server on Debian is enabled by default, so it's possible to login without changing any settings. Furthermore, root account is prohibited Password Authentication by default with [PermitRootLogin prohibit-password], so default setting is good for use. But if you prohibit root login all, change like follows.
root@server:~# apt -y install openssh-server
root@server:~# vi /etc/ssh/sshd_config
# line 33 : uncomment and change to [no]
PermitRootLogin no
root@server:~# systemctl restart ssh
SSH Client on Debian Host
Configure SSH Client on Debian or Linux Host
Step [2]Install SSH Client.
root@client:~# apt -y install openssh-client
Step [3]Connect to the SSH server with a common user.
# ssh [username@hostname or IP address]
debian@client:~$ ssh debian@server.bizantum.local
The authenticity of host 'server.bizantum.local (10.0.0.30)' can't be established.
ED25519 key fingerprint is SHA256:yKjR2T5206zIca4pz1cDMzh4axt9X6RmkrFKwD4dbg0.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'server.bizantum.local' (ED25519) to the list of known hosts.
debian@server.bizantum.local's password:
Linux server.bizantum.local 6.1.0-9-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.27-1 (2023-05-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
debian@server:~$ # just logined
Step [4]It's possible to execute commands on remote Host with adding commands to ssh command.
# for example, open [/etc/passwd] on remote host
debian@client:~$ ssh debian@server.bizantum.local "cat /etc/passwd"
debian@server.bizantum.local's password:
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
.....
.....
SSH Client on Windows Host
Configure SSH Client on Windows Host
Step [5]Get a SSH Client for Windows. This example shows to use Putty like follows. Input your server's IP address and Click [Open] button.
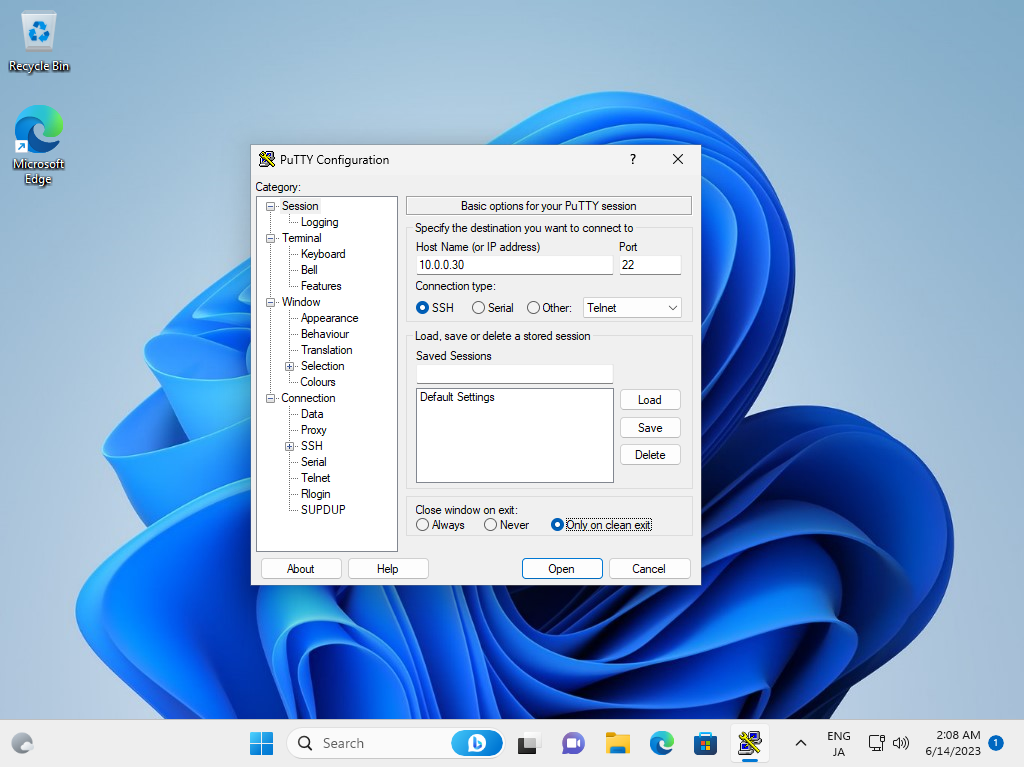
Step [6]After authentication on SSH server, it's possible to login remotely with SSH.
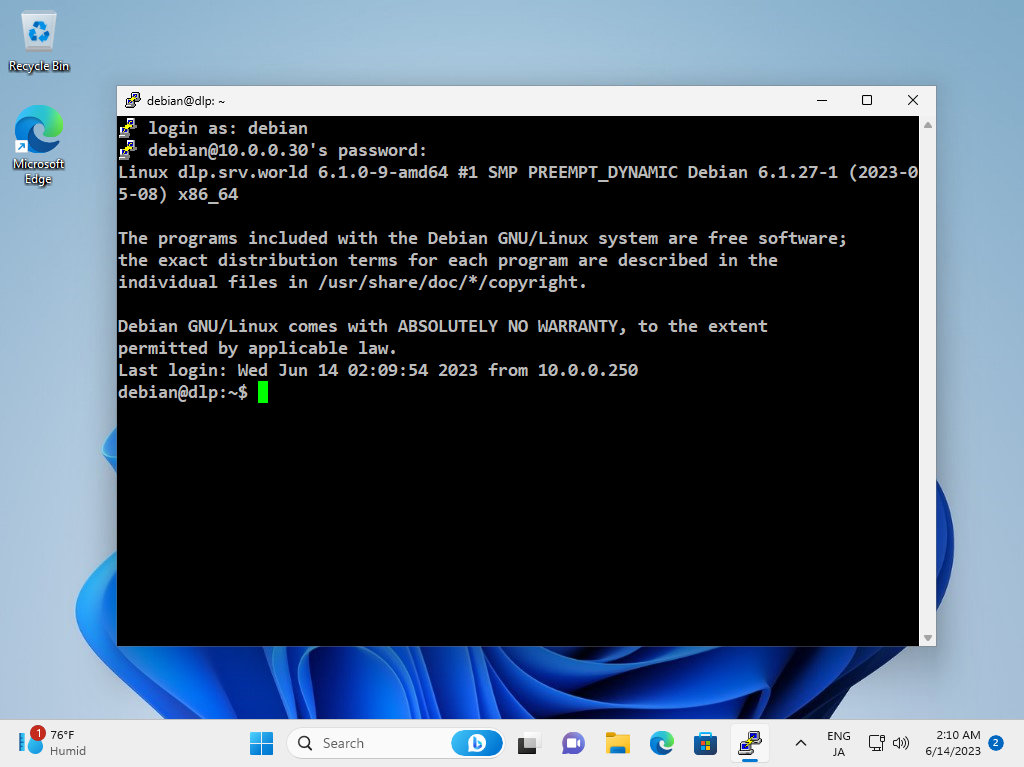
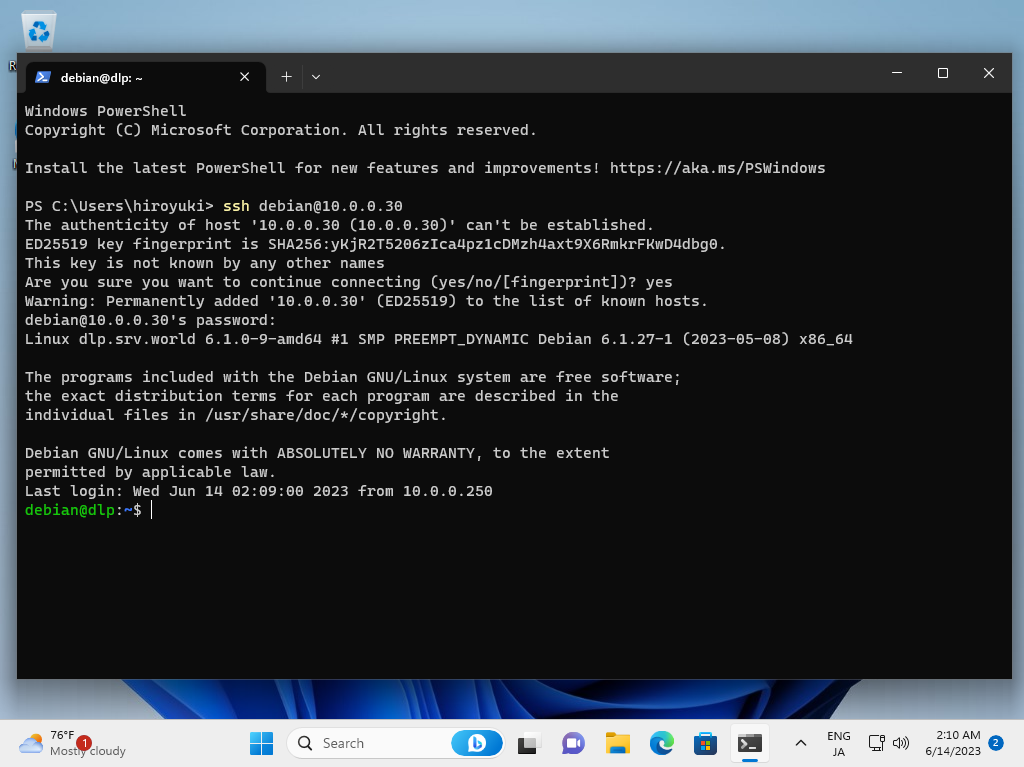
Step [7]OpenSSH Client has been implemented as an Windows feature, so it's possible to use ssh command on PowerShell or Command Prompt without Putty and other SSH software.
Security UFW
UFW Basic Usage
This is the basis of UFW (Uncomplicated Firewall) for securing server.
Step [1]Install UFW.
root@bizantum:~# apt -y install ufw
Step [2]UFW is the frontend tool of nftables/iptables. On Debian 12, default backend of UFW is nftables.
root@bizantum:~# update-alternatives --config iptables
There are 2 choices for the alternative iptables (providing /usr/sbin/iptables).
Selection Path Priority Status
------------------------------------------------------------
* 0 /usr/sbin/iptables-nft 20 auto mode
1 /usr/sbin/iptables-legacy 10 manual mode
2 /usr/sbin/iptables-nft 20 manual mode
Press <enter> to keep the current choice[*], or type selection number:
Step [3]To use UFW, it needs to run UFW service. Furthermore, even if service is running, UFW is disabled by default, so it needs to enable it manually.
root@bizantum:~# systemctl enable --now ufw
Synchronizing state of ufw.service with SysV service script with /lib/systemd/systemd-sysv-install.
Executing: /lib/systemd/systemd-sysv-install enable ufw
root@bizantum:~# systemctl status ufw
* ufw.service - Uncomplicated firewall
Loaded: loaded (/lib/systemd/system/ufw.service; enabled; preset: enabled)
Active: active (exited) since Wed 2023-07-12 18:50:17 CDT; 1min 23s ago
Docs: man:ufw(8)
Process: 1254 ExecStart=/lib/ufw/ufw-init start quiet (code=exited, status=>
Main PID: 1254 (code=exited, status=0/SUCCESS)
CPU: 775us
# current status
root@bizantum:~# ufw status
Status: inactive
# enable ufw
root@bizantum:~# ufw enable
Firewall is active and enabled on system startup
root@bizantum:~# ufw status
Status: active
# disable ufw
root@bizantum:~# ufw disable
Firewall stopped and disabled on system startup
Step [4]This is the basis to allow services or port by UFW.
# incoming connections are all denied by default
root@bizantum:~# ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
# for example, allow SSH
root@bizantum:~# ufw allow ssh
Rule added
Rule added (v6)
# for example, allow HTTP
root@bizantum:~# ufw allow http
Rule added
Rule added (v6)
# for example, allow 2049/tcp
root@bizantum:~# ufw allow 2049/tcp
Rule added
Rule added (v6)
root@bizantum:~# ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
22/tcp ALLOW IN Anywhere
80/tcp ALLOW IN Anywhere
2049/tcp ALLOW IN Anywhere
22/tcp (v6) ALLOW IN Anywhere (v6)
80/tcp (v6) ALLOW IN Anywhere (v6)
2049/tcp (v6) ALLOW IN Anywhere (v6)
# * when running [ufw allow (service name)], the port set in [/etc/services] is allowed
Step [5]This is the basis to delete rules by UFW.
root@bizantum:~# ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
22/tcp ALLOW IN Anywhere
80/tcp ALLOW IN Anywhere
2049/tcp ALLOW IN Anywhere
22/tcp (v6) ALLOW IN Anywhere (v6)
80/tcp (v6) ALLOW IN Anywhere (v6)
2049/tcp (v6) ALLOW IN Anywhere (v6)
# for example, delete the SSH allowing rule
root@bizantum:~# ufw delete allow ssh
Rule deleted
Rule deleted (v6)
# for example, delete the 80/tcp allowing rule
root@bizantum:~# ufw delete allow 80/tcp
Rule deleted
Rule deleted (v6)
# show status with rule number
root@bizantum:~# ufw status numbered
Status: active
To Action From
-- ------ ----
[ 1] 2049/tcp ALLOW IN Anywhere
[ 2] 2049/tcp (v6) ALLOW IN Anywhere (v6)
# delete a rule with specifying rule number
root@bizantum:~# ufw delete 2
Deleting:
allow 2049/tcp
Proceed with operation (y|n)? y
Rule deleted (v6)
# to delete all rules and disable UFW, run like follows
root@bizantum:~# ufw reset
Resetting all rules to installed defaults. Proceed with operation (y|n)? y
Backing up 'user.rules' to '/etc/ufw/user.rules.20230712_185512'
Backing up 'before.rules' to '/etc/ufw/before.rules.20230712_185512'
Backing up 'after.rules' to '/etc/ufw/after.rules.20230712_185512'
Backing up 'user6.rules' to '/etc/ufw/user6.rules.20230712_185512'
Backing up 'before6.rules' to '/etc/ufw/before6.rules.20230712_185512'
Backing up 'after6.rules' to '/etc/ufw/after6.rules.20230712_185512'
root@bizantum:~# ufw status
Status: inactive
Step [6]This is the basis to allow services or ports with specific source or destination hosts.
# for example, allow SSH only from [10.0.0.215]
root@bizantum:~# ufw allow from 10.0.0.215 to any port ssh
Rule added
# for example, allow [80/tcp] only from [10.0.0.215] to [10.0.0.30]
root@bizantum:~# ufw allow from 10.0.0.215 to 10.0.0.30 port 80 proto tcp
Rule added
# for example, limit SSH from [10.0.0.220]
# * over 6 consecutive SSH trial within 30 seconds are denided
root@bizantum:~# ufw limit from 10.0.0.220 to any port ssh
Rule added
root@bizantum:~# ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
22/tcp ALLOW IN 10.0.0.215
10.0.0.30 80/tcp ALLOW IN 10.0.0.215
22/tcp LIMIT IN 10.0.0.220
# when using limit, following ruleset are configured
root@bizantum:~# nft list ruleset | grep 'dport 22'
# Warning: table ip filter is managed by iptables-nft, do not touch!
ip saddr 10.0.0.215 tcp dport 22 counter packets 0 bytes 0 accept
# Warning: table ip6 filter is managed by iptables-nft, do not touch!
ip saddr 10.0.0.220 tcp dport 22 ct state new xt match recent counter packets 0 bytes 0
ip saddr 10.0.0.220 tcp dport 22 ct state new xt match recent counter packets 0 bytes 0 jump ufw-user-limit
ip saddr 10.0.0.220 tcp dport 22 counter packets 0 bytes 0 jump ufw-user-limit-accept
Step [7]To configure ICMP related settings, edit the configuration file below. Incoming connections are denied all by default but ICMP related connections are allowed.
root@bizantum:~# vi /etc/ufw/before.rules
# ICMP related connections are allowed by the settings below
# if you'd like to deny them, simply comment out all like follows
# ok icmp codes for INPUT
# -A ufw-before-input -p icmp --icmp-type destination-unreachable -j ACCEPT
# -A ufw-before-input -p icmp --icmp-type time-exceeded -j ACCEPT
# -A ufw-before-input -p icmp --icmp-type parameter-problem -j ACCEPT
# -A ufw-before-input -p icmp --icmp-type echo-request -j ACCEPT
# ok icmp code for FORWARD
# -A ufw-before-forward -p icmp --icmp-type destination-unreachable -j ACCEPT
# -A ufw-before-forward -p icmp --icmp-type time-exceeded -j ACCEPT
# -A ufw-before-forward -p icmp --icmp-type parameter-problem -j ACCEPT
# -A ufw-before-forward -p icmp --icmp-type echo-request -j ACCEPT
# reload settings
root@bizantum:~# ufw reload
Firewall reloaded
# to allow [echo-request] from the specific IP address or network, set like follows
# * answer to Ping from remote hosts
root@bizantum:~# vi /etc/ufw/before.rules
# for example, allow [echo-request] from [10.0.0.0/24]
# ok icmp codes for INPUT
# -A ufw-before-input -p icmp --icmp-type destination-unreachable -j ACCEPT
# -A ufw-before-input -p icmp --icmp-type time-exceeded -j ACCEPT
# -A ufw-before-input -p icmp --icmp-type parameter-problem -j ACCEPT
# -A ufw-before-input -p icmp --icmp-type echo-request -j ACCEPT
-A ufw-before-input -p icmp --icmp-type echo-request -s 10.0.0.0/24 -j ACCEPT
# ok icmp code for FORWARD
# -A ufw-before-forward -p icmp --icmp-type destination-unreachable -j ACCEPT
# -A ufw-before-forward -p icmp --icmp-type time-exceeded -j ACCEPT
# -A ufw-before-forward -p icmp --icmp-type parameter-problem -j ACCEPT
# -A ufw-before-forward -p icmp --icmp-type echo-request -j ACCEPT
root@bizantum:~# ufw reload
Firewall reloaded
UFW IP Masquerade
This is how to configure IP Masquerading on UFW. This example is based on the environment like follows.
Internet
-------------+-------------
Gateway|192.168.0.1
|
External |
enp9s0|192.168.0.30
+------------+------------+
| |
| debian.bizantum.local |
| |
+------------+------------+
enp1s0|10.0.0.30
Internal |
|
Step [1]Enable Forward policy first.
root@bizantum:~# vi /etc/default/ufw
# line 19 : change
DEFAULT_FORWARD_POLICY="ACCEPT"
root@bizantum:~# vi /etc/sysctl.conf
# line 28 : uncomment
net.ipv4.ip_forward=1
# reload settings
root@bizantum:~# sysctl -p
root@bizantum:~# ufw reload
Step [2]In addition to the UFW default setting, add rules that computers in Internal network can connect to external network or internet via [10.0.0.30] as a gateway.
root@bizantum:~# ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), allow (routed)
New profiles: skip
root@bizantum:~# vi /etc/ufw/before.rules
.....
.....
# don't delete the 'COMMIT' line or these rules won't be processed
COMMIT
# add to the end
# NAT
*nat
-F
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -s 10.0.0.0/24 -o enp9s0 -j MASQUERADE
COMMIT
root@bizantum:~# ufw reload
Step [3]In addition to the setting of [2] above, add rules like follows.
- requests to [enp9s0] with 22 or 80 port destination on External side are forwarded to the Host [10.0.0.51] with the same port on Internal side
- requests to [enp9s0] with 3306 port destination on External side are forwarded to the Host [10.0.0.52] with the same port on Internal side
root@bizantum:~# ufw allow ssh
Rule added
Rule added (v6)
root@bizantum:~# ufw allow http
Rule added
Rule added (v6)
root@bizantum:~# ufw allow mysql
Rule added
Rule added (v6)
root@bizantum:~# ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), allow (routed)
New profiles: skip
To Action From
-- ------ ----
22/tcp ALLOW IN Anywhere
80/tcp ALLOW IN Anywhere
3306/tcp ALLOW IN Anywhere
22/tcp (v6) ALLOW IN Anywhere (v6)
80/tcp (v6) ALLOW IN Anywhere (v6)
3306/tcp (v6) ALLOW IN Anywhere (v6)
root@bizantum:~# vi /etc/ufw/before.rules
.....
.....
# don't delete the 'COMMIT' line or these rules won't be processed
COMMIT
# NAT
*nat
-F
:POSTROUTING ACCEPT [0:0]
# add rules
:PREROUTING ACCEPT [0:0]
-A PREROUTING -p tcp --dst 192.168.0.30 -m multiport --dports 22,80 -j DNAT --to-destination 10.0.0.51
-A POSTROUTING -p tcp --dst 10.0.0.51 -m multiport --dports 22,80 -j SNAT --to-source 10.0.0.30
-A PREROUTING -p tcp --dst 192.168.0.30 --dport 3306 -j DNAT --to-destination 10.0.0.52:3306
-A POSTROUTING -p tcp --dst 10.0.0.52 --dport 3306 -j SNAT --to-source 10.0.0.30
-A POSTROUTING -s 10.0.0.0/24 -o enp9s0 -j MASQUERADE
COMMIT
root@bizantum:~# ufw reload
VIM Text Editor
Configure Vim that is more convenience than vi.
Step [1]Install Vim.
root@bizantum:~# apt -y install vim
Step [2]Configure Vim. On the example below, Apply to a user. If you like to applly settings to all users as the system wide, add settings in [/etc/vim/vimrc]. You may want to select and apply each parameter according to your own preferences.
debian@bizantum:~$ vi ~/.vimrc
" use extended feature of vim (no compatible with vi)
set nocompatible
" specify character encoding
set encoding=utf-8
" specify file encoding
" to specify multiple entries, write them with comma separated
set fileencodings=utf-8
" specify file formats
set fileformats=unix,dos
" take backup
" opposite is [ set nobackup ]
set backup
" specify backup directory
set backupdir=~/backup
" number of search histories
set history=50
" ignore Case
set ignorecase
" distinct Capital if you mix it in search words
set smartcase
" highlights matched words
" opposite is [ set nohlsearch ]
set hlsearch
" use incremental search
" opposite is [ set noincsearch ]
set incsearch
" show line number
" opposite is [ set nonumber ]
set number
" visualize break ( $ ) or tab ( ^I )
set list
" highlights parentheses
set showmatch
" not insert LF at the end of file
set binary noeol
" enable auto indent
" opposite is [ noautoindent ]
set autoindent
" show color display
" opposite is [ syntax off ]
syntax on
" change colors for comments if it's set [ syntax on ]
highlight Comment ctermfg=LightCyan
" wrap lines
" opposite is [ set nowrap ]
set wrap









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.