
Introduction
In this article, we will explore the what, who, where, when, why, and how of Domain Name System (DNS) Server and Client functionality on the Fedora 40 Server platform, so let's get started.
Overview
What
A Domain Name System (DNS) server is a crucial component of network infrastructure that translates human-readable domain names (like www.example.com) into IP addresses (such as 192.168.1.1), allowing users to access websites and services easily.
Who
DNS servers are used by everyone who accesses the internet. They are managed by network administrators, IT professionals, and internet service providers (ISPs) to ensure smooth and efficient operation of network services.
Where
DNS servers are deployed in data centers, offices, and within cloud environments. They serve both local networks (intranet) and the broader internet (extranet).
When
DNS servers are constantly in use, every time a user types a web address or uses an internet service. The setup and configuration typically occur during network infrastructure deployment and maintenance.
Why
DNS servers simplify the user experience by allowing the use of memorable domain names instead of complex IP addresses. They ensure efficient routing of internet traffic and play a crucial role in maintaining network security and performance.
| Pros | Cons |
|---|---|
| Simplifies internet navigation. | Misconfigurations can lead to downtime or security vulnerabilities. |
| Enhances user experience. | Requires ongoing maintenance and monitoring. |
| Improves network efficiency and performance. |
How
| Setup | Install the DNS server software on a dedicated server or use a managed DNS service. |
| Configuration | Define the DNS zones, create records for domain names, and set up forwarders for external DNS resolution. |
| Maintenance | Regularly update and monitor the DNS server to ensure its reliability and security. |
Consequences
| Positive | Simplifies internet navigation, enhances user experience, and improves network efficiency and performance. |
| Negative | Misconfigurations can lead to downtime or security vulnerabilities, and it requires ongoing maintenance and monitoring. |
Conclusion
A DNS server is essential for translating domain names into IP addresses, making internet navigation seamless. Proper setup, configuration, and maintenance are critical to leveraging its full benefits and ensuring network reliability.
Configure Internal Network
Install BIND to Configure DNS (Domain Name System) Server to provide Name or Address Resolution service for Clients.
Step [1]Install BIND.
root@dlp:~# apt -y install bind9 bind9utils
Step [2]On this example, Configure BIND for Internal Network. The example follows is for the case that Local network is [10.0.0.0/24], Domain name is [bizantum.local], Replace them to your own environment.
root@dlp:~# vi /etc/bind/named.conf
include "/etc/bind/named.conf.options";
include "/etc/bind/named.conf.local";
include "/etc/bind/named.conf.default-zones";
# add
include "/etc/bind/named.conf.internal-zones";
root@dlp:~# vi /etc/bind/named.conf.options
# add : set ACL entry for local network
acl internal-network {
10.0.0.0/24;
};
options {
directory "/var/cache/bind";
.....
.....
# add local network set on [acl] section above
# network range you allow to recieve queries from hosts
allow-query { localhost; internal-network; };
# network range you allow to transfer zone files to clients
# add secondary DNS servers if it exist
allow-transfer { localhost; };
# add : allow recursion
recursion yes;
//=======================================================================
// If BIND logs error messages about the root key being expired,
// you will need to update your keys. See https://www.isc.org/bind-keys
//=======================================================================
dnssec-validation auto;
# if not listen IPV6, change [any] to [none]
listen-on-v6 { any; };
};
root@dlp:~# vi /etc/bind/named.conf.internal-zones
# create new
# add zones for your network and domain name
zone "bizantum.local" IN {
type master;
file "/etc/bind/bizantum.local.lan";
allow-update { none; };
};
zone "0.0.10.in-addr.arpa" IN {
type master;
file "/etc/bind/0.0.10.db";
allow-update { none; };
};
# if you don't use IPv6 and also suppress logs for IPv6 related, possible to change
# set BIND to use only IPv4
root@dlp:~# vi /etc/default/named
# add
OPTIONS="-u bind -4"
# For how to write the section [*.*.*.*.in-addr.arpa], write your network address reversely like follows
# case of 10.0.0.0/24
# network address ⇒ 10.0.0.0
# network range ⇒ 10.0.0.0 - 10.0.0.255
# how to write ⇒ 0.0.10.in-addr.arpa
# case of 192.168.1.0/24
# network address ⇒ 192.168.1.0
# network range ⇒ 192.168.1.0 - 192.168.1.255
# how to write ⇒ 1.168.192.in-addr.arpa
Step [3]Next, Configure Zone Files for each Zone you set in [named.conf] above. To Configure Zone Files, refer to here.
Configure External Network
Install BIND to Configure DNS (Domain Name System) Server to provide Name or Address Resolution service for Clients.
Step [1]Install BIND.
root@dlp:~# apt -y install bind9 bind9utils
Step [2]On this example, Configure BIND for External Network. The example follows is for the case that External network is [172.16.0.80/29], Domain name is [bizantum.local], Replace them to your own environment. (Actually, [172.16.0.80/29] is for private IP addresses, though.)
root@dlp:~# vi /etc/bind/named.conf
include "/etc/bind/named.conf.options";
include "/etc/bind/named.conf.local";
include "/etc/bind/named.conf.default-zones";
# add
include "/etc/bind/named.conf.external-zones";
root@dlp:~# vi /etc/bind/named.conf.options
options {
directory "/var/cache/bind";
.....
.....
# add : receive queries from all hosts
allow-query { any; };
# network range you allow to transfer zone files to clients
# add secondary DNS servers if it exist
allow-transfer { localhost; };
# add : not allow recursion
recursion no;
//=======================================================================
// If BIND logs error messages about the root key being expired,
// you will need to update your keys. See https://www.isc.org/bind-keys
//=======================================================================
dnssec-validation auto;
# if not listen IPV6, change [any] to [none]
listen-on-v6 { any; };
};
root@dlp:~# vi /etc/bind/named.conf.external-zones
# create new
# add zones for your network and domain name
zone "bizantum.local" IN {
type master;
file "/etc/bind/dlp.bizantum.wan";
allow-update { none; };
};
zone "80.0.16.172.in-addr.arpa" IN {
type master;
file "/etc/bind/80.0.16.172.db";
allow-update { none; };
};
# if you don't use IPv6 and also suppress logs for IPv6 related, possible to change
# set BIND to use only IPv4
root@dlp:~# vi /etc/default/named
# add
OPTIONS="-u bind -4"
Step [3]Next, Configure Zone Files for each Zone you set in [named.conf] above. To Configure Zone Files, refer to here.
Configure Zone Files
Replace Network or Domain name on the example below to your own environment.
Step [1]Create zone files that servers resolve IP address from Domain name. The example below uses Internal network [10.0.0.0/24], Domain name [bizantum.local]. Replace to your own environment.
root@dlp:~# vi /etc/bind/bizantum.local.lan
$TTL 86400
@ IN SOA dlp.bizantum.local. root.bizantum.local. (
# any numerical values are OK for serial number
# recommended : [YYYYMMDDnn] (update date + number)
2023061501 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
# define Name Server
IN NS dlp.bizantum.local.
# define Name Server's IP address
IN A 10.0.0.30
# define Mail Exchanger Server
IN MX 10 dlp.bizantum.local.
# define each IP address of a hostname
dlp IN A 10.0.0.30
www IN A 10.0.0.31
Step [2]Create zone files that servers resolve Domain name from IP address. The example below uses Internal network [10.0.0.0/24], Domain name [bizantum.local]. Replace to your own environment.
root@dlp:~# vi /etc/bind/0.0.10.db
$TTL 86400
@ IN SOA dlp.bizantum.local. root.bizantum.local. (
2023061501 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
# define Name Server
IN NS dlp.bizantum.local.
# define each hostname of an IP address
30 IN PTR dlp.bizantum.local.
31 IN PTR www.bizantum.local.
Step [3]Next, Start BIND and Verify Name or Address Resolution, refer to here.
Verify Resolution
Step [1]Restart BIND to apply changes.
root@dlp:~# systemctl restart named
Step [2]Change DNS setting to refer to own DNS if need.
root@dlp:~# vi /etc/resolv.conf
# change nameserver
nameserver 10.0.0.30
# * if you are using resolvconf or Networkmanager programs,
# change nameserver setting on a file for their requirements
Step [3]Verify Name and Address Resolution. If [ANSWER SECTION] is shown, that's OK.
root@dlp:~# dig dlp.bizantum.local.
; <<>> DiG 9.18.12-1-Debian <<>> dlp.bizantum.local.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34251
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 399a23023b136d3901000000648a68aaab63310525a6459f (good)
;; QUESTION SECTION:
;dlp.bizantum.local. IN A
;; ANSWER SECTION:
dlp.bizantum.local. 86400 IN A 10.0.0.30
;; Query time: 0 msec
;; SERVER: 10.0.0.30#53(10.0.0.30) (UDP)
;; WHEN: Wed Jun 14 20:26:02 CDT 2023
;; MSG SIZE rcvd: 86
root@dlp:~# dig -x 10.0.0.30
; <<>> DiG 9.18.12-1-Debian <<>> -x 10.0.0.30
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44135
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 1091197ede0eca9001000000648a68cf698db831ee837680 (good)
;; QUESTION SECTION:
;30.0.0.10.in-addr.arpa. IN PTR
;; ANSWER SECTION:
30.0.0.10.in-addr.arpa. 86400 IN PTR dlp.bizantum.local.
;; Query time: 0 msec
;; SERVER: 10.0.0.30#53(10.0.0.30) (UDP)
;; WHEN: Wed Jun 14 20:26:39 CDT 2023
;; MSG SIZE rcvd: 106
Use View Statement
This is an example to use View Statement in [named.conf]. On this example, Configure both settings for Internal Network like here and settings for External Network like here with View Statement in [named.conf].
Step [1]This example uses internal network [10.0.0.0/24], external network [172.16.0.80/29], domain name [bizantum.local], Replace them for your own environment. ( Actually, [172.16.0.80/29] is for private IP addresses, though. )
root@dlp:~# vi /etc/bind/named.conf
include "/etc/bind/named.conf.options";
include "/etc/bind/named.conf.local";
# comment out
#include "/etc/bind/named.conf.default-zones";
# add
include "/etc/bind/named.conf.internal-zones";
include "/etc/bind/named.conf.external-zones";
root@dlp:~# vi /etc/bind/named.conf.options
# add : set ACL entry for local network
acl internal-network {
10.0.0.0/24;
};
options {
directory "/var/cache/bind";
.....
.....
# add local network set on [acl] section above
# network range you allow to recieve queries from hosts
allow-query { localhost; internal-network; };
# network range you allow to transfer zone files to clients
# add secondary DNS servers if it exist
allow-transfer { localhost; };
# add recursion range your allow recursive query
allow-recursion { localhost; internal-network; };
//=======================================================================
// If BIND logs error messages about the root key being expired,
// you will need to update your keys. See https://www.isc.org/bind-keys
//=======================================================================
dnssec-validation auto;
# if not listen IPV6, change [any] to [none]
listen-on-v6 { any; };
};
root@dlp:~# vi /etc/bind/named.conf.internal-zones
view "internal" {
# set internal network zones
match-clients {
localhost;
internal-network;
};
zone "bizantum.local" {
type master;
file "/etc/bind/bizantum.local.lan";
allow-update { none; };
};
zone "0.0.10.in-addr.arpa" {
type master;
file "/etc/bind/0.0.10.db";
allow-update { none; };
};
include "/etc/bind/named.conf.default-zones";
};
root@dlp:~# vi /etc/bind/named.conf.external-zones
view "external" {
# match all except targets defined on [match-clients] on internal section
match-clients { any; };
# allow all queries
allow-query { any; };
# not allow recursive queries
recursion no;
zone "bizantum.local" {
type master;
file "/etc/bind/dlp.bizantum.wan";
allow-update { none; };
};
zone "80.0.16.172.in-addr.arpa" {
type master;
file "/etc/bind/80.0.16.172.db";
allow-update { none; };
};
};
Step [2]For configuration of each Zone files set in [named.conf] above, refer to here.
Set Alias (CNAME)
If you'd like to set Alias (Another Name) to a Host, set CNAME record in a zone file.
Step [1]Set [CNAME] record in a zone file.
root@dlp:~# vi /etc/bind/bizantum.local.lan
$TTL 86400
@ IN SOA dlp.bizantum.local. root.bizantum.local. (
# update serial number
2023061502 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
IN NS dlp.bizantum.local.
IN A 10.0.0.30
IN MX 10 dlp.bizantum.local.
dlp IN A 10.0.0.30
www IN A 10.0.0.31
# [Alias] IN CNAME [Original Name]
ftp IN CNAME dlp.bizantum.local.
root@dlp:~# rndc reload
server reload successful
# verify resolution
root@dlp:~# dig ftp.bizantum.local.
; <<>> DiG 9.18.12-1-Debian <<>> ftp.bizantum.local.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 5455
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 39f956d9ceb54a1b01000000648a70f88d272ec28418b94f (good)
;; QUESTION SECTION:
;ftp.bizantum.local. IN A
;; ANSWER SECTION:
ftp.bizantum.local. 86400 IN CNAME dlp.bizantum.local.
dlp.bizantum.local. 86400 IN A 10.0.0.30
;; Query time: 0 msec
;; SERVER: 10.0.0.30#53(10.0.0.30) (UDP)
;; WHEN: Wed Jun 14 21:01:28 CDT 2023
;; MSG SIZE rcvd: 104
Configure Secondary Server
Configure DNS Secondary Server. On this example, it shows to configure DNS Secondary Server [ns.server.education] (192.168.100.85) that DNS Primary Server is [dlp.bizantum.local] (172.16.0.82) configured like here. Replace IP address and Hostname to your own environment.
Step [1]Configure on DNS Primary Server Host.
root@dlp:~# vi /etc/bind/named.conf.options
.....
.....
options {
directory "/var/cache/bind";
.....
.....
allow-query { localhost; internal-network; };
# add secondary server to allow to transfer zone files
allow-transfer { localhost; 192.168.100.85; };
allow-recursion { localhost; internal-network; };
.....
.....
root@dlp:~# vi /etc/bind/dlp.bizantum.wan
$TTL 86400
@ IN SOA dlp.bizantum.local. root.bizantum.local. (
# update serial numbere
2023061503 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
IN NS dlp.bizantum.local.
# add secondary server
IN NS ns.server.lab.
IN A 172.16.0.82
IN MX 10 dlp.bizantum.local.
dlp IN A 172.16.0.82
www IN A 172.16.0.83
root@dlp:~# systemctl restart named
Step [2]Configure on DNS Secondary Server Host.
root@ns:~# vi /etc/bind/named.conf.external-zones
# add target zone info
# for IP address, it's the Primary server's IP address
zone "bizantum.local" IN {
type slave;
masters { 172.16.0.82; };
file "/etc/bind/slaves/dlp.bizantum.wan";
};
root@ns:~# systemctl restart named
root@ns:~# ls /etc/bind/slaves
dlp.bizantum.wan # zone file has been transferred
Set SPF record
Set up a Sender Policy Framework (SPF) record to verify the validity of the domain from which the email is sent. This example is based on the environment that the [bizantum.local] domain uses the network range [172.16.0.80/29]. Replace the domain name to yours, and also replace [172.16.0.80/29] to the global IP address of yours.
Step [1]Add a TXT record to the zone file that contains the target domain name and set SPF there.
root@dlp:~# vi /etc/bind/dlp.bizantum.wan
$TTL 86400
@ IN SOA dlp.bizantum.local. root.bizantum.local. (
;; when updating a zone file, update the serial number as well
2024071001 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
IN NS dlp.bizantum.local.
IN A 172.16.0.82
IN MX 10 dlp.bizantum.local.
;; add SPF settings to a TXT record
;; specify the host to use as the mail server
IN TXT "v=spf1 +ip4:172.16.0.82 -all"
dlp IN A 172.16.0.82
www IN A 172.16.0.83
root@dlp:~# rndc reload
Step [2]This is the basic description of SPF.
;; the TXT record itself can have multiple lines,
;; but in SPF settings, only one TXT record can be set for one domain name
;; [v=spf1] ⇒ it means SPF version
;; [+ip4] ⇒ specify IPv4 addresses
;; [+ip6] ⇒ specify IPv6 addresses
;; [+] ⇒ verify your domain's mail server
;; * [+] is optional
;; * if there is no [+] or [-], the [+] is considered to be omitted
;; [-] ⇒ do not authenticate as a mail server for the domain
;; [~] ⇒ deemed to be potentially fake but delivered anyway
;; if there are multiple mail servers, specify them with a space separator
IN TXT "v=spf1 +ip4:172.16.0.82 +ip4:172.16.0.83 -all"
;; for the case of specifying the host name of the mail server
;; * host name must be specified as a Fully Qualified Domain Name (FQDN)
IN TXT "v=spf1 +a:dlp.bizantum.local +a:www.bizantum.local -all"
;; for the case of setting only the specified host in the MX record
IN TXT "v=spf1 +mx -all"
;; for the case of describing the network containing hosts that may send email using the CIDR method
;; * be careful, if you specify too broad a range, the SPF record will be meaningless
IN TXT "v=spf1 +ip4:172.16.0.80/29 -all"
;; for example, if you use a subdomain such as [severdev@dlp.bizantum.local] as an email address,
;; set it for the subdomain
dlp IN TXT "v=spf1 +ip4:172.16.0.82 -all"
;; for example, if your domain is only used as a web server and does not send email at all,
;; you can declare this with the following settings
IN TXT "v=spf1 -all"
;; for example, if you want to include the same SPF record as the one set for another domain [server.education],
;; set it like follows
IN TXT "v=spf1 +include:server.education -all"
Step [3]The following website allows you to check the contents of the SPF record you have set, so we recommend that you check it. ⇒ https://mxtoolbox.com/spf.aspx, If there are no problems with the SPF record settings, when you send an email to Gmail or others from the mail server of the configured domain, [SPF: PASS] will be displayed in the header.
Set DMARC record
Configure a DMARC (Domain-based Message Authentication, Reporting, and Conformance) record to indicate that your mail server is protected by SPF/DKIM.
Step [1]DMARC is a setting that registers in your DNS record what to do when SPF or DKIM authentication fails, and instructs the recipient of the email. Therefore, configure SPF record setting and DKIM setting on Mail server side in advance.
Step [2]Configure a DMARC record in the zone file that contains the target domain name.
root@dlp:~# vi /etc/bind/dlp.bizantum.wan
$TTL 86400
@ IN SOA dlp.bizantum.local. root.bizantum.local. (
;; update serial number
2024071501 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
IN NS dlp.bizantum.local.
IN A 172.16.0.82
IN MX 10 dlp.bizantum.local.
IN TXT "v=spf1 +ip4:172.16.0.82 -all"
dlp IN A 172.16.0.82
www IN A 172.16.0.83
20240712._domainkey IN TXT "v=DKIM1; h=sha256; k=rsa; ""p=MIIBIjANBgkqh....."
;; add to last line
_dmarc IN TXT "v=DMARC1; p=none;"
root@dlp:~# rndc reload
Step [3]Other options for your DMARC record.
;; [v=DMARC1] ⇒ DMARC version
;; [p=***] : action policy when authentication fails
;; - [none] ⇒ do nothing
;; - [quarantine] ⇒ quarantined in junk mail folder
;; - [reject] ⇒ reject email
;; [rua=mailto:***] : the address to which aggregate reports will be sent
;; * if not specified, no aggregate report will be sent
;; * if specify multiple addresses, separate them with commas (,)
_dmarc IN TXT "v=DMARC1; p=none; rua=mailto:admin@bizantum.local,webmaster@bizantum.local"
;; [ruf=mailto:***] : the address to which failure reports will be sent
;; * if not specified, no failure report will be sent
;; * if specify multiple addresses, separate them with commas (,)
_dmarc IN TXT "v=DMARC1; p=none; ruf=mailto:admin@bizantum.local,webmaster@bizantum.local"
;; [sp=***] : action policy when authentication of subdomain fails
;; * if not specified, the setting of [p=***] will be inherited
;; - [none] ⇒ do nothing
;; - [quarantine] ⇒ quarantined in junk mail folder
;; - [reject] ⇒ reject email
_dmarc IN TXT "v=DMARC1; p=none; sp=reject; rua=mailto:admin@bizantum.local"
;; [pct=***] : percentage of emails that the policy covers
;; * specify with [1-100]
;; * if not specified, it is set to [pct=100]
_dmarc IN TXT "v=DMARC1; p=none; pct=50; rua=mailto:admin@bizantum.local"
;; [fo=***] : action options for sending failure reports (when ruf=*** is enabled)
;; - [0] ⇒ both DKIM and SPF authentication fails (default if not specified)
;; - [1] ⇒ either DKIM or SPF authentication failed
;; - [d] ⇒ DKIM authentication failed
;; - [s] ⇒ SPF authentication failed
;; [aspf=***] : SPF authentication alignment mode
;; - [s] ⇒ strict mode : exact domain match (default if not specified)
;; - [r] ⇒ relaxed mode : partial domain match
;; [adkim=***] : DKIM authentication alignment mode
;; - [s] ⇒ strict mode : exact domain match (default if not specified)
;; - [r] ⇒ relaxed mode : partial domain match
;; [rf=afrf] : DMARC authentication failure report format
;; * currently only [rf=afrf] (default if not specified)
;; [ri=***] : aggregate report sending interval (in seconds)
;; * if not specified, the default value is [ri=86400] (24 hours)
Step [4]The following website allows you to check the description of the DMARC record you have set, so it is a good idea to check it out. ⇒ https://mxtoolbox.com/dmarc.aspx, If there are no problems with the DMARC record settings, when you send an email from the mail server of the configured domain to Gmail etc., the header will show [DMARC: 'PASS'].
Server Settings DNS over HTTPS
Configure DNS over HTTPS Server on BIND.
Step [1]Get SSL/TLS certificate, refer to here.
Step [2]Configure BIND.
root@dlp:~# openssl dhparam -out /etc/bind/dhparam.pem 3072
root@dlp:~# cp /etc/letsencrypt/live/dlp.bizantum.local/{fullchain.pem,privkey.pem} /etc/bind/
root@dlp:~# chown bind:bind /etc/bind/{fullchain.pem,privkey.pem,dhparam.pem}
root@dlp:~# vi /etc/bind/named.conf.options
# add settings for certificate
tls local-tls {
key-file "/etc/bind/privkey.pem";
cert-file "/etc/bind/fullchain.pem";
dhparam-file "/etc/bind/dhparam.pem";
};
http local {
endpoints { "/dns-query"; };
};
options {
.....
.....
dnssec-validation auto;
# add and change like follows
listen-on tls local-tls http local { any; };
listen-on-v6 tls local-tls http local { any; };
};
root@dlp:~# systemctl restart named
Step [3]Verify Name Resolution with HTTPS on localhost.
root@dlp:~# dig +https @127.0.0.1 dlp.bizantum.local.
; <<>> DiG 9.18.12-1-Debian <<>> +https @127.0.0.1 dlp.bizantum.local.
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43458
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 069f8ca33e4add1e01000000648a72bab31b02f6e2ae9fc4 (good)
;; QUESTION SECTION:
;dlp.bizantum.local. IN A
;; ANSWER SECTION:
dlp.bizantum.local. 86400 IN A 10.0.0.30
;; Query time: 0 msec
;; SERVER: 127.0.0.1#443(127.0.0.1) (HTTPS)
;; WHEN: Wed Jun 14 21:08:58 CDT 2023
;; MSG SIZE rcvd: 86
Client Settings DNS over HTTPS
Configure Debian Client to refer to your DNS over HTTPS Server.
Configure on Debian Client Host
Step [1]Install dnscrypt-proxy. Before it, make sure the DNS Stamp on the following site, it needs on dnscrypt-proxy settings. ⇒ https://dnscrypt.info/stamps/, Select or Input like follows. Then note the value [sdns://***] on [Stamp] section.
- Protocol: DNS-over-HTTPS (DoH)
- IP Address: your DNS-over-HTTPS server's IP address
- Host Name: your DNS-over-HTTPS server's hostname
- Path: the value for [endpoints] that you set on your DNS-over-HTTPS server settings
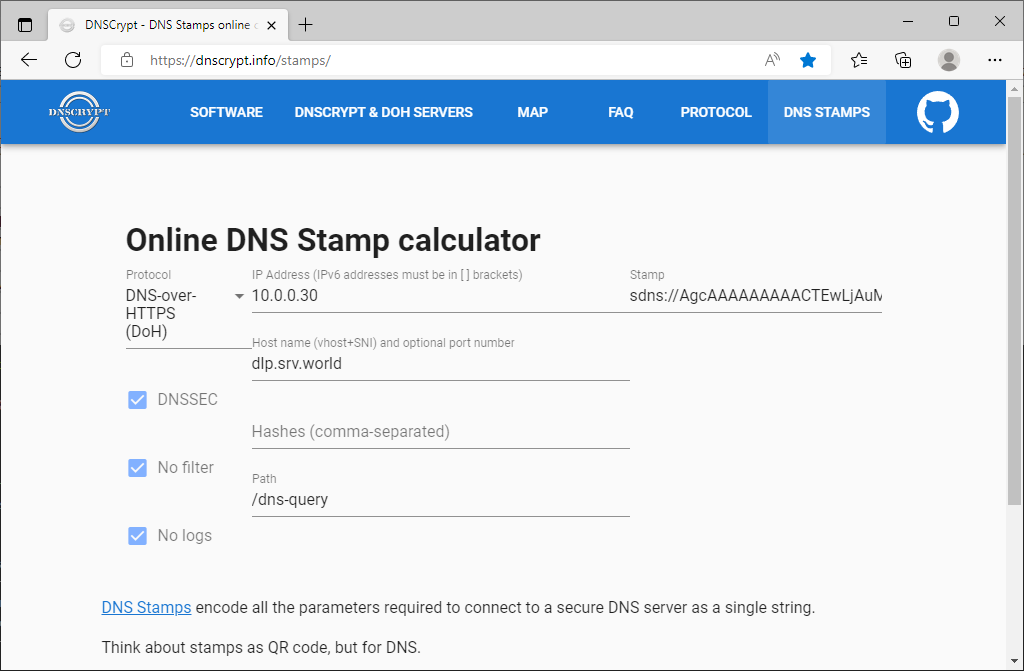
Step [2]Configure Debian Client to refer to your DoH server.
root@node01:~# echo 'deb https://deb.debian.org/debian/ testing main' >> /etc/apt/sources.list
root@node01:~# apt update
root@node01:~# apt -y install dnscrypt-proxy
root@node01:~# vi /etc/dnscrypt-proxy/dnscrypt-proxy.toml
# Empty listen_addresses to use systemd socket activation
listen_addresses = []
# change to your DoH server
server_names = ['dlp.bizantum.local']
[query_log]
file = '/var/log/dnscrypt-proxy/query.log'
[nx_log]
file = '/var/log/dnscrypt-proxy/nx.log'
# comment out all
#[sources]
# [sources.'public-resolvers']
# url = 'https://download.dnscrypt.info/resolvers-list/v2/public-resolvers.md'
# cache_file = '/var/cache/dnscrypt-proxy/public-resolvers.md'
# minisign_key = 'RWQf6LRCGA9i53mlYecO4IzT51TGPpvWucNSCh1CBM0QTaLn73Y7GFO3'
# refresh_delay = 72
# prefix = ''
# add follows
# set the Stamp value on [stamp] section that you made sure on [1]
[static]
[static.'dlp.bizantum.local']
stamp = 'sdns://AgcAAAAAAAAACTEwLjAuMC4zMAANZGxwLnNydi53b3JsZAovZG5zLXF1ZXJ5'
root@node01:~# systemctl restart dnscrypt-proxy
root@node01:~# vi /etc/resolv.conf
# change to the IP address that dnscrypt-proxy listens
nameserver 127.0.2.1
# * if you are using resolvconf or Networkmanager programs,
# change nameserver setting on a file for their requirements
# verify resolution
root@node01:~# dig www.bizantum.local.
; <<>> DiG 9.18.12-1-Debian <<>> www.bizantum.local.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 55046
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;www.bizantum.local. IN A
;; ANSWER SECTION:
www.bizantum.local. 86397 IN A 10.0.0.31
;; Query time: 0 msec
;; SERVER: 127.0.2.1#53(127.0.2.1) (UDP)
;; WHEN: Wed Jun 14 21:29:45 CDT 2023
;; MSG SIZE rcvd: 58
Configure on Windows Client Host
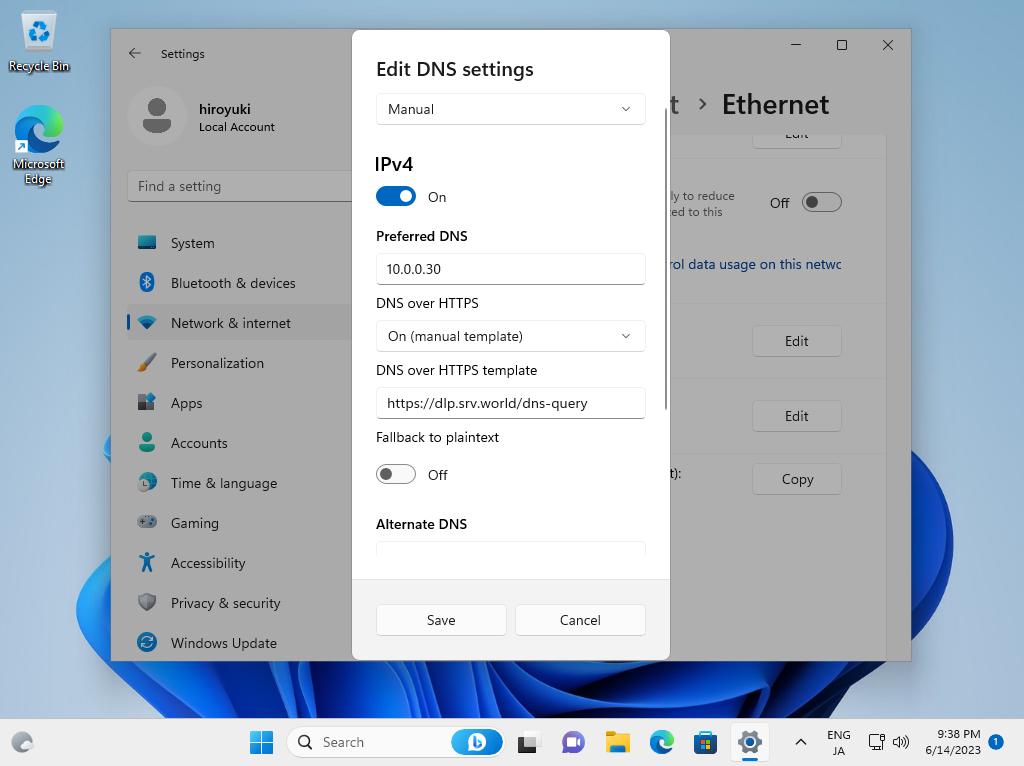
Configure Windows Client to refer to your DNS over HTTPS Server. This example is based on Windows 11.
Step [3]Open the Network setting and click the [Edit] button on [DNS server assignment] section. Next, Input your DoH Server address on the [Preferred DNS] section. For [DNS over HTTPS] section, select [On (manual template)] and For [DNS over HTTPS template] section, input the value of [endpoints] in named.conf you set.
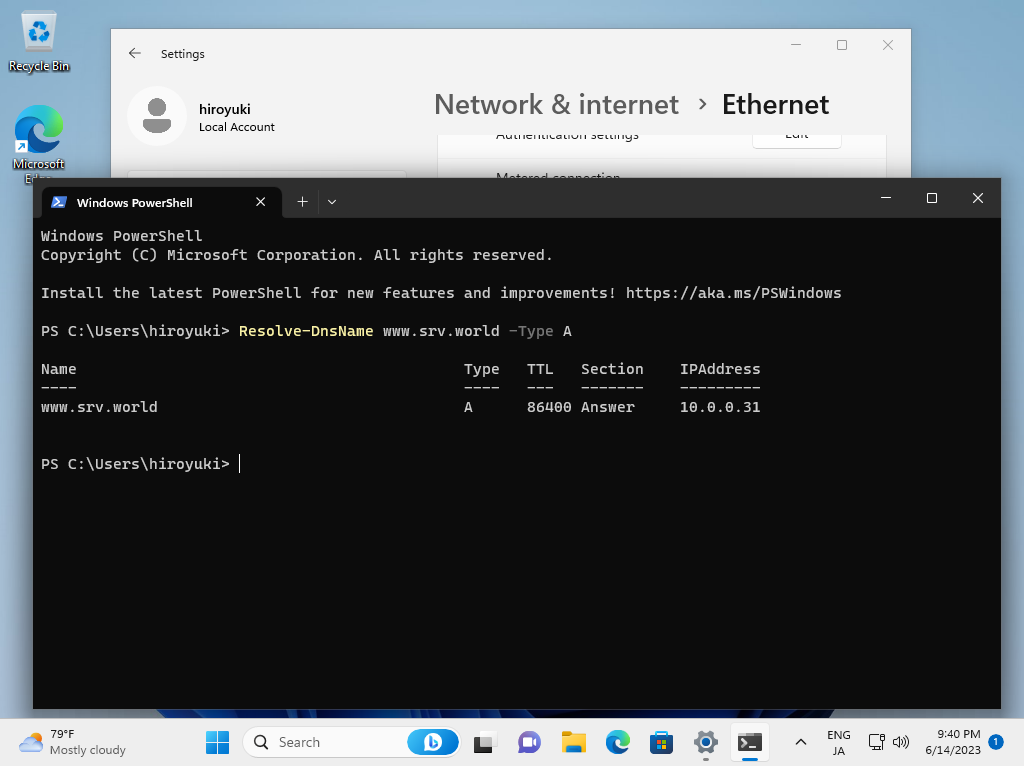
Step [4]After setting your DoH server, verify Name and Address Resolution.
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.