
Introduction
This guide covers the installation and configuration of Nginx on Fedora 40 using the 5W1H approach. We will explore the What, Who, Where, When, Why, How, Consequences, and Conclusion of setting up an Nginx server.
Overview
What
Nginx (pronounced "engine-x") is a high-performance, lightweight web server and reverse proxy server used for serving static content, load balancing, and handling concurrent connections efficiently.
Who
This guide is intended for system administrators and IT professionals responsible for setting up and managing web servers, looking for a high-performance solution on Fedora 40.
Where
The setup process can be carried out on any server running Fedora 40, whether it's a physical machine, virtual machine, or cloud instance.
When
Setting up Nginx should be done during a planned maintenance window to avoid potential disruptions to existing services.
Why
Implementing Nginx on your server offers several advantages:
| Pros | Cons |
|---|---|
| High performance and low resource usage | Configuration complexity for beginners |
| Handles concurrent connections efficiently | Less extensive module support compared to Apache |
| Scalable and flexible architecture | Potential learning curve for advanced features |
How
Follow these steps to set up Nginx on Fedora 40:
| Step 1 | Update your system: sudo dnf update -y |
| Step 2 | Install the Nginx package: sudo dnf install -y nginx |
| Step 3 | Start and enable the Nginx service: sudo systemctl start nginx sudo systemctl enable nginx |
| Step 4 | Open the firewall for HTTP and HTTPS traffic: sudo firewall-cmd --permanent --add-service=http sudo firewall-cmd --permanent --add-service=https sudo firewall-cmd --reload |
| Step 5 | Verify Nginx is running by accessing http://your_server_ip in a web |
Consequences
Setting up Nginx on Fedora 40 can have the following consequences:
| Positive |
|
| Negative |
|
Conclusion
Setting up Nginx on Fedora 40 is essential for achieving high performance and efficiency in serving web content. While the initial setup can be complex and requires ongoing maintenance, the benefits of a scalable and flexible architecture make Nginx a valuable addition to any web infrastructure. By following this guide, system administrators can ensure their servers are ready to deliver high-quality web services effectively.
Install : Nginx
Install fast HTTP Server [Nginx] and configure HTTP/Proxy Server with it.
Step [1]Install Nginx.
[root@bizantum ~]# dnf -y install nginx
Step [2]Confgure Nginx.
[root@bizantum ~]# vi /etc/nginx/nginx.conf
# line 40 : change to your hostname
server_name www.bizantum.lab;
[root@bizantum ~]# systemctl enable --now nginx
Step [3]If Firewalld is running, allow HTTP service. HTTP uses [80/TCP].
[root@bizantum ~]# firewall-cmd --add-service=http
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [4]Access to the default page of Nginx from a Client with Web browser and it's OK if the following page are shown.
Virtual Hostings
This is the Virtual Hostings setting for Nginx. For example, configure additional domainame [virtual.host].
Step [1]Configure Nginx.
[root@bizantum ~]# vi /etc/nginx/conf.d/virtual.host.conf
# create new
server {
listen 80;
server_name www.virtual.host;
location / {
root /usr/share/nginx/virtual.host;
index index.html index.htm;
}
}
[root@bizantum ~]# mkdir /usr/share/nginx/virtual.host
[root@bizantum ~]# systemctl reload nginx
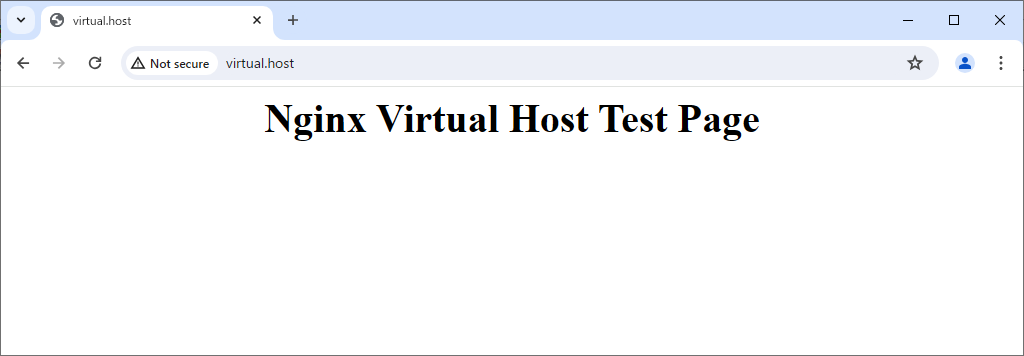
Step [2]Create a test page to verify it works normally.
[root@bizantum ~]# vi /usr/share/nginx/virtual.host/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
Nginx Virtual Host Test Page
</div>
</body>
</html>
SSL/TLS Setting
Enable SSL/TLS setting to use secure encrypted connection.
Step [1]Get SSL certificates, refer to here.
Step [2]Configure Nginx. For example, enable SSL/TLS on default site.
[root@bizantum ~]# vi /etc/nginx/conf.d/ssl.conf
# create new
# replace servername and path of certificates to your own one
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
server_name www.bizantum.lab;
root /usr/share/nginx/html;
ssl_certificate "/etc/letsencrypt/live/www.bizantum.lab/fullchain.pem";
ssl_certificate_key "/etc/letsencrypt/live/www.bizantum.lab/privkey.pem";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers PROFILE=SYSTEM;
ssl_prefer_server_ciphers on;
include /etc/nginx/default.d/*.conf;
location / {
}
error_page 404 /404.html;
location = /40x.html
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
[root@bizantum ~]# systemctl reload nginx
Step [3]If you'd like to set HTTP connection to redirect to HTTPS (Always on SSL/TLS), configure like follows.
[root@bizantum ~]# vi /etc/nginx/nginx.conf
# add into the section of listening 80 port
server {
listen 80 default_server;
listen [::]:80 default_server;
return 301 https://$host$request_uri;
server_name www.bizantum.lab;
root /usr/share/nginx/html;
[root@bizantum ~]# systemctl reload nginx
Step [4]If Firewalld is running, allow HTTPS service. HTTPS uses [443/TCP].
[root@bizantum ~]# firewall-cmd --add-service=https
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [5]Verify to access to the test page from any client computer with web browser via HTTPS. If you set Always On SSL/TLS, access with HTTP to verify the connection is redirected to HTTPS normally, too.
Enable Userdir
Enable Userdir for common users to open their site in the home directories.
Step [1]Configure Nginx. Add settings into the [server] section of a site definition you'd like to set.
[root@bizantum ~]# vi /etc/nginx/conf.d/ssl.conf
# add into the [server] section
server {
.....
.....
location ~ ^/~(.+?)(/.*)?$ {
alias /home/$1/public_html$2;
index index.html index.htm;
}
[root@bizantum ~]# systemctl reload nginx
Step [2]If SELinux is enabled, change boolean setting.
[root@bizantum ~]# setsebool -P httpd_enable_homedirs on
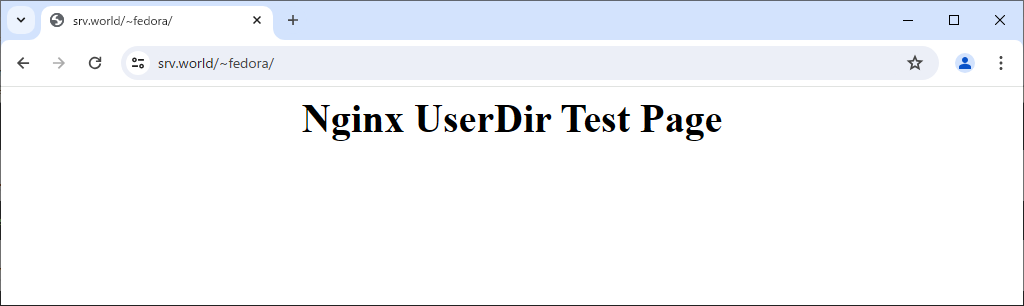
Step [3]Create a test page as a common user to verify it works normally.
[fedora@www ~]$ chmod 711 /home/fedora
[fedora@www ~]$ mkdir ~/public_html
[fedora@www ~]$ chmod 755 ~/public_html
[fedora@www ~]$ vi ~/public_html/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
Nginx UserDir Test Page
</div>
</body>
</html>
Basic Authentication
Set Basic Authentication to limit access on specific web pages.
Step [1]Username and password are sent with plain text on Basic Authentication, so Use secure connection with SSL/TLS setting, refer to here.
Step [2]Add setting on a site config you'd like to set. For example, set Basic Auth under the [/auth-basic] directory.
[root@bizantum ~]# dnf -y install httpd-tools
[root@bizantum ~]# vi /etc/nginx/conf.d/ssl.conf
# add into the [server] section
server {
.....
.....
location /auth-basic/ {
auth_basic "Basic Auth";
auth_basic_user_file "/etc/nginx/.htpasswd";
}
[root@bizantum ~]# mkdir /usr/share/nginx/html/auth-basic
[root@bizantum ~]# systemctl reload nginx
# add user for Basic authentication
[root@bizantum ~]# htpasswd -5 -c /etc/nginx/.htpasswd fedora
New password: # set any password
Re-type new password:
Adding password for user fedora
# create a test page
[root@bizantum ~]# vi /usr/share/nginx/html/auth-basic/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
Test Page for Basic Authentication
</div>
</body>
</html>
Step [3]Access to the test page from any client computer with web browser. Then authentication is required as settings, answer with a user added in [2].
Step [4]That's OK if authentication is successfully passed and test page is displayed normally.
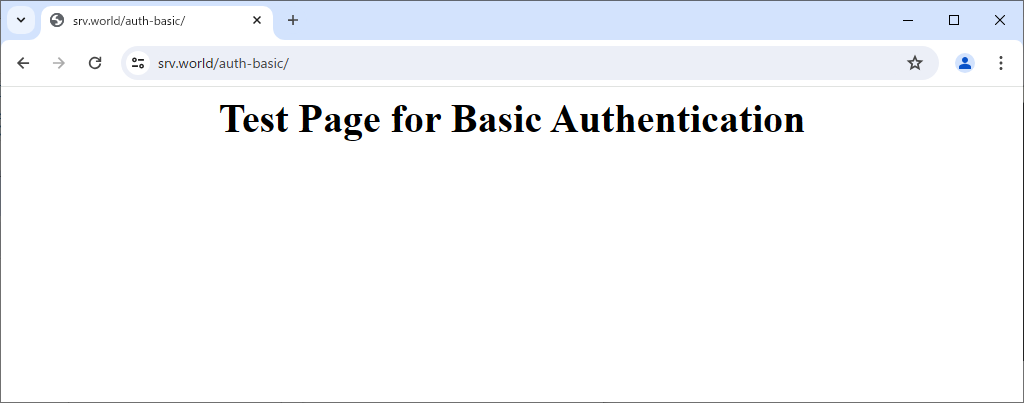
Use CGI Scripts
Configure CGI executable Environment on Nginx.
Step [1]Install FastCGI Wrap and Configure Nginx for it.
[root@bizantum ~]# dnf -y install fcgiwrap
[root@bizantum ~]# vi /etc/nginx/fcgiwrap.conf
# create new
# for example, enable CGI under [/cgi-bin]
location /cgi-bin/ {
gzip off;
root /usr/share/nginx;
fastcgi_pass unix:/var/run/fcgiwrap.socket;
include /etc/nginx/fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
[root@bizantum ~]# mkdir /usr/share/nginx/cgi-bin
[root@bizantum ~]# chmod 755 /usr/share/nginx/cgi-bin
[root@bizantum ~]# vi /etc/nginx/conf.d/ssl.conf
# add settings into [server] section of a site definition
server {
.....
.....
include fcgiwrap.conf;
}
[root@bizantum ~]# systemctl reload nginx
Step [2]Create Systemd file for FastCGI Wrap service and Start them.
[root@bizantum ~]# vi /usr/lib/systemd/system/fcgiwrap.service
# create new
[Unit]
Description=Simple CGI Server
After=nss-user-lookup.target
Requires=fcgiwrap.socket
[Service]
EnvironmentFile=/etc/sysconfig/fcgiwrap
ExecStart=/usr/sbin/fcgiwrap ${DAEMON_OPTS} -c ${DAEMON_PROCS}
User=nginx
Group=nginx
[Install]
Also=fcgiwrap.socket
[root@bizantum ~]# vi /usr/lib/systemd/system/fcgiwrap.socket
# create new
[Unit]
Description=fcgiwrap Socket
[Socket]
ListenStream=/run/fcgiwrap.socket
[Install]
WantedBy=sockets.target
[root@bizantum ~]# systemctl enable --now fcgiwrap
Step [3]If SELinux is enabled, change policy.
[root@bizantum ~]# vi nginx-server.te
# create new
module nginx-server 1.0;
require {
type unconfined_service_t;
type var_run_t;
type httpd_t;
class sock_file write;
class unix_stream_socket connectto;
}
#============= httpd_t ==============
allow httpd_t unconfined_service_t:unix_stream_socket connectto;
allow httpd_t var_run_t:sock_file write;
[root@bizantum ~]# checkmodule -m -M -o nginx-server.mod nginx-server.te
[root@bizantum ~]# semodule_package --outfile nginx-server.pp --module nginx-server.mod
[root@bizantum ~]# semodule -i nginx-server.pp
Step [4]Create a test scripts with a language (example below is Python3) under the directory you set CGI executable ([/usr/share/nginx/cgi-bin] on this example) and Access to it to verify CGI works normally.
[root@bizantum ~]# vi /usr/share/nginx/cgi-bin/index.cgi
#!/usr/bin/python3
print("Content-type: text/html\n")
print("<html>\n<body>")
print("<div style=\"width: 100%; font-size: 40px; font-weight: bold; text-align: center;\">")
print("CGI Script Test Page")
print("</div>")
print("</body>\n</html>")
[root@bizantum ~]# chmod 755 /usr/share/nginx/cgi-bin/index.cgi
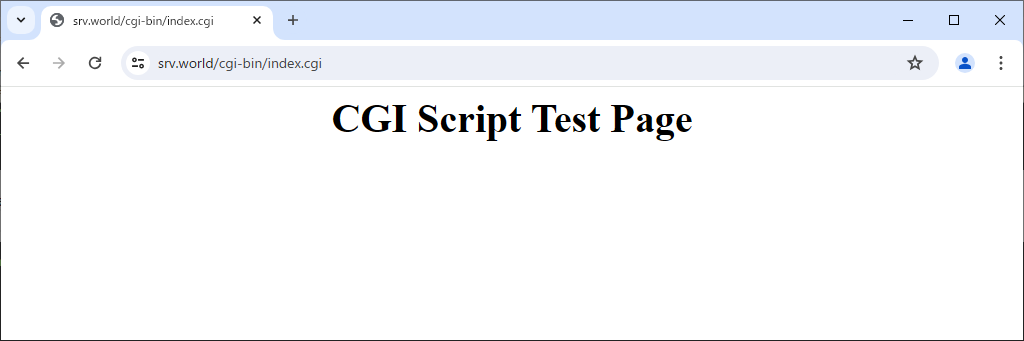
Use PHP Scripts
Configure httpd to use PHP scripts.
Step [1]Install PHP.
[root@bizantum ~]# dnf -y install php php-mbstring php-pear
Step [2]After installing PHP, Restart httpd, it's OK to do it only. PHP-FPM (FPM : FastCGI Process Manager) is configured by default. When [nginx] starts, [php-fpm] also starts for dependency by setting file [/usr/lib/systemd/system/nginx.service.d/php-fpm.conf].
[root@bizantum ~]# systemctl restart nginx
[root@bizantum ~]# systemctl status php-fpm
* php-fpm.service - The PHP FastCGI Process Manager
Loaded: loaded (/usr/lib/systemd/system/php-fpm.service; disabled; preset:>
Drop-In: /usr/lib/systemd/system/service.d
+-- 10-timeout-abort.conf
Active: active (running) since Tue 2024-05-14 13:50:38 JST; 4s ago
Main PID: 2229 (php-fpm)
Status: "Ready to handle connections"
Tasks: 6 (limit: 4638)
Memory: 12.2M (peak: 12.4M)
CPU: 30ms
CGroup: /system.slice/php-fpm.service
.....
.....
# create PHPInfo test page
[root@bizantum ~]# echo '' > /usr/share/nginx/html/info.php
Step [3]Verify to access to PHPInfo test page from any client computer.
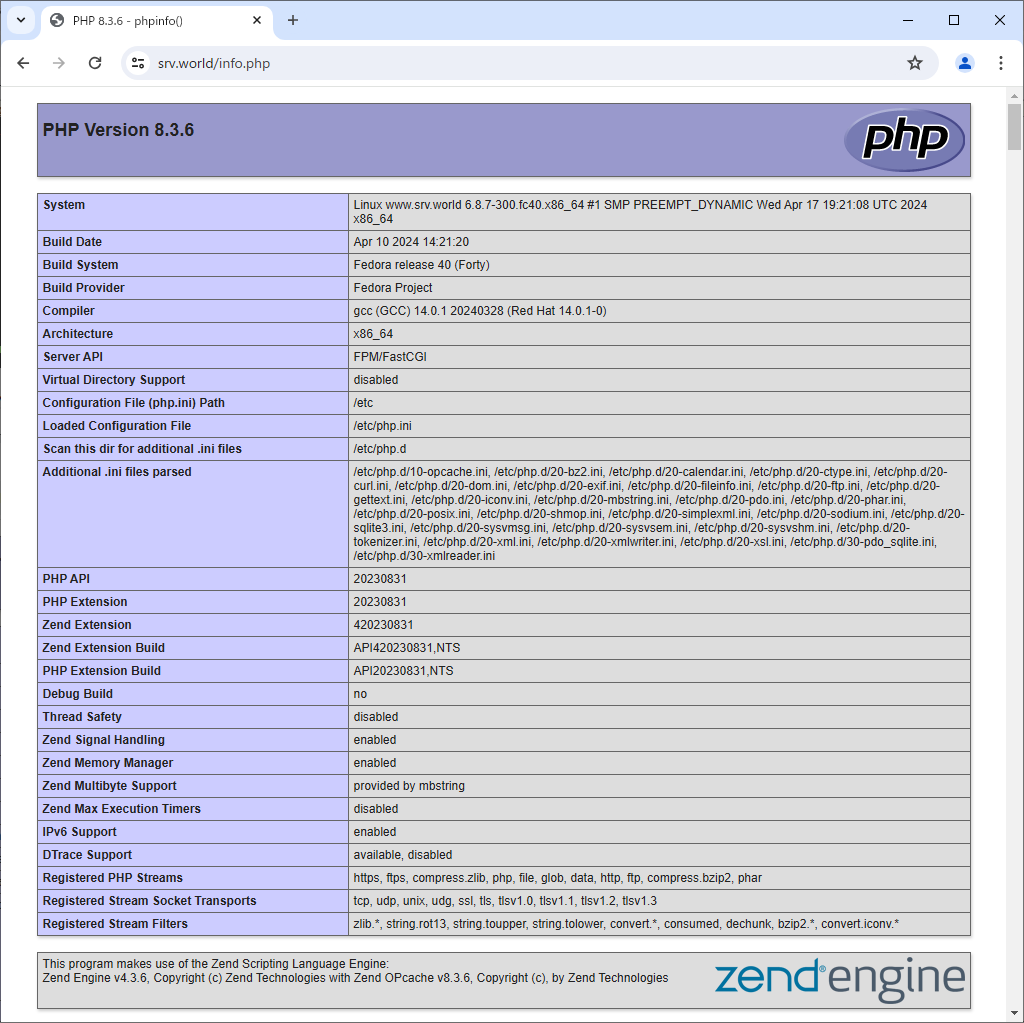
Reverse Proxy
Configure Nginx as a Reverse Proxy Server. For example, Configure Nginx that HTTP/HTTPS accesses to [www.bizantum.lab] are forwarded to [node01.bizantum.lab].
Step [1] Get SSL certificates, refer to here.
Step [2]Configure Nginx.
# for HTTP setting
[root@bizantum ~]# vi /etc/nginx/nginx.conf
# change [server] section like follows
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name www.bizantum.lab;
proxy_redirect off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
location / {
proxy_pass http://node01.bizantum.lab/;
}
}
# for HTTPS setting
[root@bizantum ~]# vi /etc/nginx/conf.d/proxy-ssl.conf
# create new
# replace certificates to your own one
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
server_name www.bizantum.lab;
ssl_certificate "/etc/letsencrypt/live/www.bizantum.lab/fullchain.pem";
ssl_certificate_key "/etc/letsencrypt/live/www.bizantum.lab/privkey.pem";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers PROFILE=SYSTEM;
ssl_prefer_server_ciphers on;
proxy_redirect off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
location / {
proxy_pass http://node01.bizantum.lab/;
}
}
[root@bizantum ~]# systemctl reload nginx
Step [3]If SELinux is enabled, change boolean setting.
[root@bizantum ~]# setsebool -P httpd_can_network_connect on
Step [4]Configure backend Nginx server to log X-Forwarded-For header.
[root@node01 ~]# vi /etc/nginx/nginx.conf
# make sure settings [log_format] in [http] section
# OK if set [http_x_forwarded_for]
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
# add into [server] section
# specify your local network for [set_real_ip_from]
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name node01.bizantum.lab;
root /usr/share/nginx/html;
set_real_ip_from 10.0.0.0/24;
real_ip_header X-Forwarded-For;
[root@node01 ~]# systemctl reload nginx
Step [5]Verify it works fine to access to frontend Nginx Server from any Client Computer.
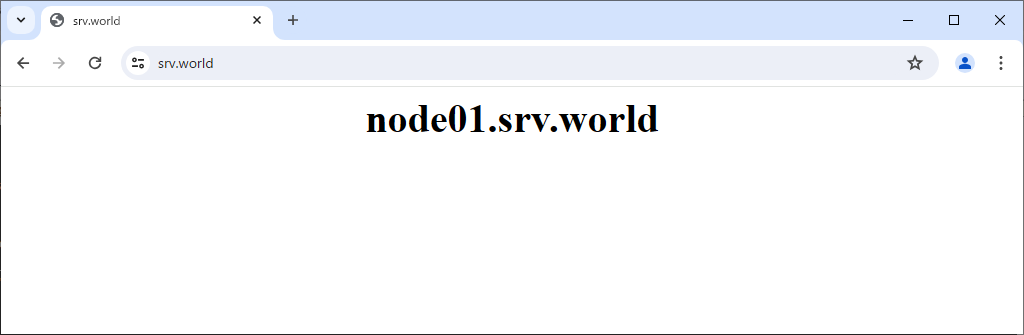
Load Balancing
Configure Nginx as a Load Balancing Server. This example is based on the environment like follows.
-----------+---------------------------+-----
| |
|10.0.0.30 |
+----------+-----------+ |
| [ www.bizantum.lab ] | |
| Nginx | |
+----------------------+ |
|
------------+--------------------------+--------------------------+------------
| | |
|10.0.0.51 |10.0.0.52 |10.0.0.53
+-----------+----------+ +-----------+----------+ +-----------+----------+
| [ node01.bizantum.lab ] | | [ node02.bizantum.lab ] | | [ node03.bizantum.lab ] |
| Web Server#1 | | Web Server#2 | | Web Server#3 |
+----------------------+ +----------------------+ +----------------------+
Step [1]Get SSL certificates, refer to here.
Step [2]Configure Nginx.
[root@bizantum ~]# vi /etc/nginx/nginx.conf
# add into [http] section
# [backup] means this server is balanced only when other servers are down
# [weight=*] means balancing weight
http {
upstream backends {
server node01.bizantum.lab:80 weight=2;
server node02.bizantum.lab:80;
server node03.bizantum.lab:80 backup;
}
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# for HTTP
# change like follows in [server] section
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name www.bizantum.lab;
proxy_redirect off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
location / {
proxy_pass http://backends;
}
}
# for HTTPS
[root@bizantum ~]# vi /etc/nginx/conf.d/lb-ssl.conf
# create new
# replace certificates to your own one
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
server_name www.bizantum.lab;
ssl_certificate "/etc/letsencrypt/live/www.bizantum.lab/fullchain.pem";
ssl_certificate_key "/etc/letsencrypt/live/www.bizantum.lab/privkey.pem";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers PROFILE=SYSTEM;
ssl_prefer_server_ciphers on;
proxy_redirect off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
location / {
proxy_pass http://backends;
}
}
[root@bizantum ~]# systemctl reload nginx
Step [3]If SELinux is enabled, change boolean setting.
[root@bizantum ~]# setsebool -P httpd_can_network_connect on
Step [4]Configure backend Nginx server to log X-Forwarded-For header.
[root@node01 ~]# vi /etc/nginx/nginx.conf
# make sure settings [log_format] in [http] section
# OK if set [http_x_forwarded_for]
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
# add into [server] section
# specify your local network for [set_real_ip_from]
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name node01.bizantum.lab;
root /usr/share/nginx/html;
set_real_ip_from 10.0.0.0/24;
real_ip_header X-Forwarded-For;
[root@node01 ~]# systemctl reload nginx
Step [5]Verify it works fine to access to frontend Nginx Server from any Client Computer.
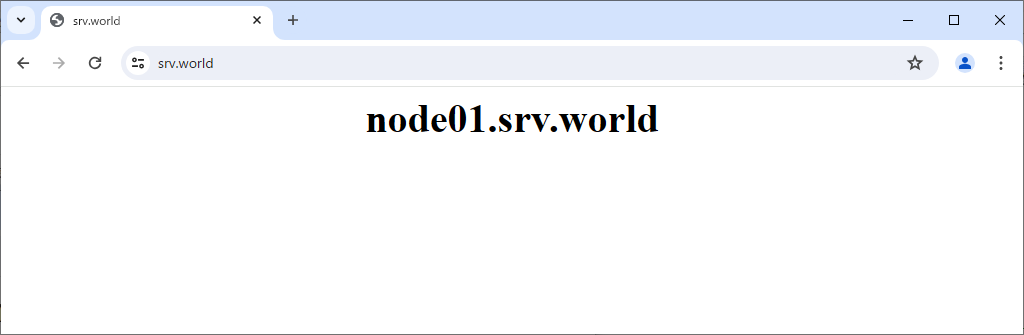
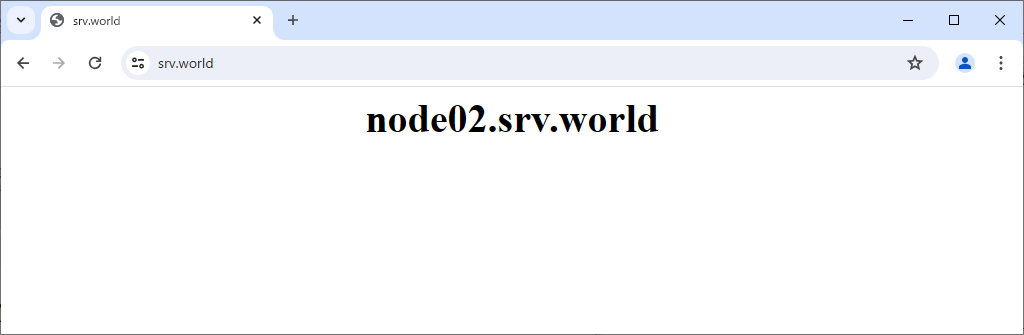
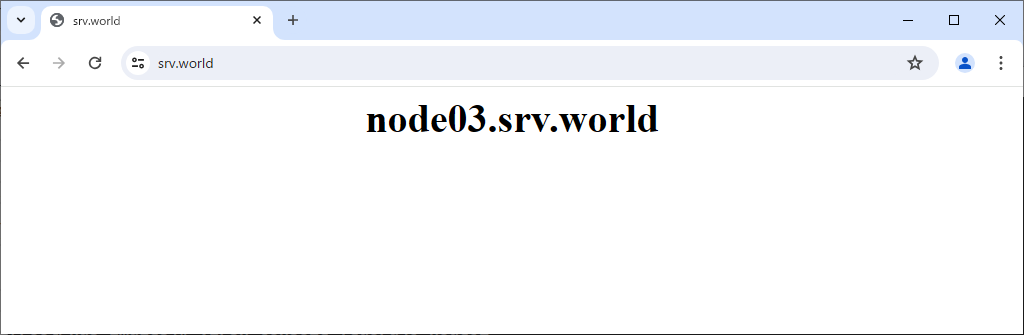
Use Stream module
Configure Nginx to use Stream module. It's possible to proxy TCP, UDP (1.9.13 or later), UNIX-domain sockets requests. This example is based on the environment like follows to proxy MariaDB requests to backend servers.
-----------+---------------------------+-----
| |
|10.0.0.31 |
+----------+-----------+ |
| [ www.bizantum.lab ] | |
| Nginx | |
+----------------------+ |
|
------------+--------------------------+-----------
| |
|10.0.0.51 |10.0.0.52
+-----------+----------+ +-----------+----------+
| [ node01.bizantum.lab ] | | [ node02.bizantum.lab ] |
| Mariadb#1 | | Mariadb#2 |
+----------------------+ +----------------------+
Step [1]Configure Nginx.
[root@bizantum ~]# dnf -y install nginx-mod-stream
[root@bizantum ~]# vi /etc/nginx/nginx.conf
# add to the end
# [weight=*] means balancing weight
stream {
upstream mariadb-backend {
server 10.0.0.51:3306 weight=2;
server 10.0.0.52:3306;
}
server {
listen 3306;
proxy_pass mariadb-backend;
}
}
[root@bizantum ~]# systemctl reload nginx
Step [2]If SELinux is enabled, change policy.
[root@bizantum ~]# setsebool -P httpd_can_network_connect on
[root@bizantum ~]# setsebool -P httpd_can_network_connect_db on
[root@bizantum ~]# vi nginx-stream.te
# create new
module nginx-stream 1.0;
require {
type mysqld_port_t;
type httpd_t;
class tcp_socket name_bind;
}
#============= httpd_t ==============
allow httpd_t mysqld_port_t:tcp_socket name_bind;
[root@bizantum ~]# checkmodule -m -M -o nginx-stream.mod nginx-stream.te
[root@bizantum ~]# semodule_package --outfile nginx-stream.pp --module nginx-stream.mod
[root@bizantum ~]# semodule -i nginx-stream.pp
Step [3]Verify it works fine to access to frontend Nginx server from any client computer.
[fedora@client ~]$ mysql -u bizantum -ppassword -h www.bizantum.lab -e "show variables like 'hostname';"
+---------------+------------------+
| Variable_name | Value |
+---------------+------------------+
| hostname | node01.bizantum.lab |
+---------------+------------------+
[fedora@client ~]$ mysql -u bizantum -ppassword -h www.bizantum.lab -e "show variables like 'hostname';"
+---------------+------------------+
| Variable_name | Value |
+---------------+------------------+
| hostname | node01.bizantum.lab |
+---------------+------------------+
[fedora@client ~]$ mysql -u bizantum -ppassword -h www.bizantum.lab -e "show variables like 'hostname';"
+---------------+------------------+
| Variable_name | Value |
+---------------+------------------+
| hostname | node02.bizantum.lab |
+---------------+------------------+
[fedora@client ~]$ mysql -u bizantum -ppassword -h www.bizantum.lab -e "show variables like 'hostname';"
+---------------+------------------+
| Variable_name | Value |
+---------------+------------------+
| hostname | node01.bizantum.lab |
+---------------+------------------+
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.