
Introduction
This guide provides a comprehensive overview of installing FreeIPA on Fedora 40 using the 5W1H approach. We will cover the key aspects including the What, Who, Where, When, Why, How, Consequences, and Conclusion of the installation process.
Overview
What
FreeIPA is an integrated security information management solution. It combines Linux (Fedora), 389 Directory Server, MIT Kerberos, NTP, DNS, and Dogtag (Certificate System) to form a one-stop solution for managing security information, including user identities and providing centralized authentication and authorization.
Who
This guide is intended for system administrators and IT professionals who manage Linux servers and are looking to implement a centralized identity management system using FreeIPA on Fedora 40.
Where
This installation can be performed on any compatible hardware or virtual machine running Fedora 40. It is particularly useful in environments where multiple Linux servers are managed and a centralized authentication system is needed.
When
The installation should be performed during a planned maintenance window to minimize disruption, as it involves significant changes to the system’s security and authentication infrastructure.
Why
Implementing FreeIPA offers numerous benefits:
| Pros | Cons |
|---|---|
| Centralized identity management | Initial setup complexity |
| Improved security | Learning curve for administrators |
| Scalability | Resource consumption |
How
Follow these steps to install FreeIPA on Fedora 40:
| Step 1 | Update your system: sudo dnf update -y |
| Step 2 | Install FreeIPA server: sudo dnf install -y freeipa-server |
| Step 3 | Run the FreeIPA installation script: sudo ipa-server-install |
| Step 4 | Follow the prompts to configure your FreeIPA server including setting up DNS and Kerberos configurations. |
| Step 5 | Verify the installation by accessing the FreeIPA web UI and ensuring all services are running correctly. |
Consequences
The successful installation and configuration of FreeIPA on Fedora 40 will provide a robust identity management solution. However, there are both positive and negative consequences toconsider.
| Positive |
|
| Negative |
|
Conclusion
FreeIPA is a powerful tool for managing security information and centralizing authentication on Fedora 40. While the initial setup can be complex and resource-intensive, the long-term benefits of enhanced security, centralized management, and improved user experience make it a valuable addition to any IT infrastructure. By following this guide, system administrators can successfully install and configure FreeIPA, leveraging its capabilities to streamline their identity management processes.
Configure Server
Configure FreeIPA Server that is an integrated security information management System. ( called [Red Hat Identity Management] on RHEL )
Step [1]Install FreeIPA Packages.
[root@bizantum ~]# dnf -y install freeipa-server freeipa-server-dns freeipa-client
Step [2]Setup FreeIPA Server with integrated DNS feature.
# add own hostname
[root@bizantum ~]# echo '10.0.0.40 dlp.ipa.bizantum.lab dlp' >> /etc/hosts
[root@bizantum ~]# ipa-server-install --setup-dns
The log file for this installation can be found in /var/log/ipaserver-install.log
==============================================================================
This program will set up the IPA Server.
Version 4.11.1
This includes:
* Configure a stand-alone CA (dogtag) for certificate management
* Configure the NTP client (chronyd)
* Create and configure an instance of Directory Server
* Create and configure a Kerberos Key Distribution Center (KDC)
* Configure Apache (httpd)
* Configure DNS (bind)
* Configure SID generation
* Configure the KDC to enable PKINIT
To accept the default shown in brackets, press the Enter key.
Enter the fully qualified domain name of the computer
on which you're setting up server software. Using the form
<hostname>.<domainname>
Example: master.example.com.
# confirm hostname and Enter
Server host name [dlp.ipa.bizantum.lab]:
Warning: skipping DNS resolution of host dlp.ipa.bizantum.lab
The domain name has been determined based on the host name.
# confirm domain name and Enter
Please confirm the domain name [ipa.bizantum.lab]:
The kerberos protocol requires a Realm name to be defined.
This is typically the domain name converted to uppercase.
# confirm realm name and Enter
Please provide a realm name [IPA.bizantum.lab]:
Certain directory server operations require an administrative user.
This user is referred to as the Directory Manager and has full access
to the Directory for system management tasks and will be added to the
instance of directory server created for IPA.
The password must be at least 8 characters long.
# set Directory Manager password
Directory Manager password:
Password (confirm):
The IPA server requires an administrative user, named 'admin'.
This user is a regular system account used for IPA server administration.
# set IPA admin password
IPA admin password:
Password (confirm):
Checking DNS domain ipa.bizantum.lab., please wait ...
# if you set DNS forwarder, answer [yes]
Do you want to configure DNS forwarders? [yes]:
The following DNS servers are configured in systemd-resolved: 10.0.0.10
Do you want to configure these servers as DNS forwarders? [yes]:
All detected DNS servers were added. You can enter additional addresses now:
Enter an IP address for a DNS forwarder, or press Enter to skip:
DNS forwarders: 10.0.0.10
Checking DNS forwarders, please wait ...
DNS server 10.0.0.10 does not support DNSSEC: answer to query '. SOA' is missing DNSSEC signatures (no RRSIG data)
Please fix forwarder configuration to enable DNSSEC support.
DNS server 10.0.0.10: answer to query '. SOA' is missing DNSSEC signatures (no RRSIG data)
Please fix forwarder configuration to enable DNSSEC support.
WARNING: DNSSEC validation will be disabled
# if you search reverse zone of DNS forwarder, answer [yes]
Do you want to search for missing reverse zones? [yes]: no
Trust is configured but no NetBIOS domain name found, setting it now.
Enter the NetBIOS name for the IPA domain.
Only up to 15 uppercase ASCII letters, digits and dashes are allowed.
Example: EXAMPLE.
# set any NetBIOS name
NetBIOS domain name [IPA]: IPA01
# if you set Chrony as NTP server, answer [yes]
Do you want to configure chrony with NTP server or pool address? [no]:
The IPA Master Server will be configured with:
Hostname: dlp.ipa.bizantum.lab
IP address(es): 10.0.0.40
Domain name: ipa.bizantum.lab
Realm name: IPA.bizantum.lab
The CA will be configured with:
Subject DN: CN=Certificate Authority,O=IPA.bizantum.lab
Subject base: O=IPA.bizantum.lab
Chaining: self-signed
BIND DNS server will be configured to serve IPA domain with:
Forwarders: 10.0.0.10
Forward policy: only
Reverse zone(s): No reverse zone
# confirm settings and proceed with [yes]
Continue to configure the system with these values? [no]: yes
The following operations may take some minutes to complete.
Please wait until the prompt is returned.
Disabled p11-kit-proxy
Synchronizing time
No SRV records of NTP servers found and no NTP server or pool address was provided.
Using default chrony configuration.
Attempting to sync time with chronyc.
Time synchronization was successful.
Configuring directory server (dirsrv). Estimated time: 30 seconds
[1/42]: creating directory server instance
Validate installation settings ...
Create file system structures ...
Perform SELinux labeling ...
.....
.....
Setup complete
Next steps:
1. You must make sure these network ports are open:
TCP Ports:
* 80, 443: HTTP/HTTPS
* 389, 636: LDAP/LDAPS
* 88, 464: kerberos
* 53: bind
UDP Ports:
* 88, 464: kerberos
* 53: bind
* 123: ntp
2. You can now obtain a kerberos ticket using the command: 'kinit admin'
This ticket will allow you to use the IPA tools (e.g., ipa user-add)
and the web user interface.
Be sure to back up the CA certificates stored in /root/cacert.p12
These files are required to create replicas. The password for these
files is the Directory Manager password
The ipa-server-install command was successful
Step [3]Get Kerberos Ticket.
[root@bizantum ~]# kinit admin
Password for admin@IPA.bizantum.lab: # IPA admin password
[root@bizantum ~]# klist
Ticket cache: KCM:0
Default principal: admin@IPA.bizantum.lab
Valid starting Expires Service principal
05/14/2024 09:05:00 05/15/2024 08:08:27 krbtgt/IPA.bizantum.lab@IPA.bizantum.lab
# change default shell to Bash
[root@bizantum ~]# ipa config-mod --defaultshell=/bin/bash
Maximum username length: 32
Maximum hostname length: 64
Home directory base: /home
Default shell: /bin/bash
Default users group: ipausers
Default e-mail domain: ipa.bizantum.lab
Search time limit: 2
Search size limit: 100
User search fields: uid,givenname,sn,telephonenumber,ou,title
Group search fields: cn,description
Enable migration mode: False
Certificate Subject base: O=IPA.bizantum.lab
Password Expiration Notification (days): 4
Password plugin features: AllowNThash, KDC:Disable Last Success
SELinux user map order: guest_u:s0$xguest_u:s0$user_u:s0$staff_u:s0-s0:c0.c1023$sysadm_u:s0-s0:c0.c1023$unconfined_u:s0-s0:c0.c1023
Default SELinux user: unconfined_u:s0-s0:c0.c1023
Default PAC types: MS-PAC, nfs:NONE
IPA masters: dlp.ipa.bizantum.lab
IPA master capable of PKINIT: dlp.ipa.bizantum.lab
IPA CA servers: dlp.ipa.bizantum.lab
IPA CA renewal master: dlp.ipa.bizantum.lab
IPA DNS servers: dlp.ipa.bizantum.lab
Step [4]If Firewalld is running, allow services.
[root@bizantum ~]# firewall-cmd --add-service={freeipa-ldap,freeipa-ldaps,dns,ntp}
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Add User Accounts
Add User Accounts on FreeIPA Server.
Step [1]Add a user. The password set on here is required to change at initial login.
[root@bizantum ~]# ipa user-add fedora --first=Fedora --last=Linux --password
Password: # set password
Enter Password again to verify:
-------------------
Added user "fedora"
-------------------
User login: fedora
First name: Fedora
Last name: Linux
Full name: Fedora Linux
Display name: Fedora Linux
Initials: FL
Home directory: /home/fedora
GECOS: Fedora Linux
Login shell: /bin/bash
Principal name: fedora@IPA.bizantum.lab
Principal alias: fedora@IPA.bizantum.lab
User password expiration: 20240514000727Z
Email address: fedora@ipa.bizantum.lab
UID: 446800003
GID: 446800003
Password: True
Member of groups: ipausers
Kerberos keys available: True
# confirm
[root@bizantum ~]# ipa user-find fedora
--------------
1 user matched
--------------
User login: fedora
First name: Fedora
Last name: Linux
Home directory: /home/fedora
Login shell: /bin/bash
Principal name: fedora@IPA.bizantum.lab
Principal alias: fedora@IPA.bizantum.lab
Email address: fedora@ipa.bizantum.lab
UID: 446800003
GID: 446800003
Account disabled: False
----------------------------
Number of entries returned 1
----------------------------
Step [2] Add Existing local Users to FreeIPA Directory. (set the same password with the username on this example, but it is required to change at initial login)
[root@bizantum ~]# vi ipauser.sh
# extract local users who have [1000-9999] digit UID
# this is an example
#!/bin/bash
for line in `grep "x:[1-9][0-9][0-9][0-9]:" /etc/passwd`
do
USER=`echo $line | cut -d: -f1`
FIRST=`echo $line | cut -d: -f5 | awk {'print $1'}`
LAST=`echo $line | cut -d: -f5 | awk {'print $2'}`
[ ! "$FIRST" ] && FIRST=$USER
[ ! "$LAST" ] && LAST=$USER
echo $USER | ipa user-add $USER --first=$FIRST --last=$LAST --password
done
[root@bizantum ~]# sh ipauser.sh
-------------------
Added user "redhat"
-------------------
User login: redhat
First name: redhat
Last name: redhat
Full name: redhat redhat
Display name: redhat redhat
Initials: rr
Home directory: /home/redhat
GECOS: redhat redhat
Login shell: /bin/bash
Principal name: redhat@IPA.bizantum.lab
Principal alias: redhat@IPA.bizantum.lab
User password expiration: 20240514000901Z
Email address: redhat@ipa.bizantum.lab
UID: 446800004
GID: 446800004
Password: True
Member of groups: ipausers
Kerberos keys available: True
.....
.....
Configure Client
Configure FreeIPA Client.
Step [1]Add DNS entry for FreeIPA Client in integrated DNS on FreeIPA Server. (if not using FreeIPA integrated DNS, skip this step)
# ipa dnsrecord-add [domain name] [record name] [record type] [record]
[root@bizantum ~]# ipa dnsrecord-add ipa.bizantum.lab node01 --a-rec 10.0.0.61
Record name: node01
A record: 10.0.0.61
Step [2]Setup NTP Client on FreeIPA Client to sync time with FreeIPA Server, refer to here.
Step [3]
[root@node01 ~]# dnf -y install freeipa-client
Step [4]Setup FreeIPA Client.
# set DNS to FreeIPA server host
[root@node01 ~]# nmcli connection modify enp1s0 ipv4.dns 10.0.0.40
[root@node01 ~]# nmcli connection up enp1s0
# setup client with specifying FreeIPA server and domain name
[root@node01 ~]# ipa-client-install --server=dlp.ipa.bizantum.lab --domain ipa.bizantum.lab
This program will set up IPA client.
Version 4.11.1
Autodiscovery of servers for failover cannot work with this configuration.
If you proceed with the installation, services will be configured to always access the discovered server for all operations and will not fail over to other servers in case of failure.
Proceed with fixed values and no DNS discovery? [no]: yes
Do you want to configure chrony with NTP server or pool address? [no]:
Client hostname: node01.ipa.bizantum.lab
Realm: IPA.bizantum.lab
DNS Domain: ipa.bizantum.lab
IPA Server: dlp.ipa.bizantum.lab
BaseDN: dc=ipa,dc=srv,dc=world
# confirm settings and answer [yes]
Continue to configure the system with these values? [no]: yes
Synchronizing time
No SRV records of NTP servers found and no NTP server or pool address was provided.
Using default chrony configuration.
Attempting to sync time with chronyc.
Time synchronization was successful.
# authenticate with admin user
User authorized to enroll computers: admin
Password for admin@IPA.bizantum.lab:
Successfully retrieved CA cert
Subject: CN=Certificate Authority,O=IPA.bizantum.lab
Issuer: CN=Certificate Authority,O=IPA.bizantum.lab
Valid From: 2024-05-14 00:01:09+00:00
Valid Until: 2044-05-14 00:01:09+00:00
Enrolled in IPA realm IPA.bizantum.lab
Created /etc/ipa/default.conf
Configured /etc/sssd/sssd.conf
Systemwide CA database updated.
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
Could not update DNS SSHFP records.
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config.d/04-ipa.conf
Configuring ipa.bizantum.lab as NIS domain.
Configured /etc/krb5.conf for IPA realm IPA.bizantum.lab
Client configuration complete.
The ipa-client-install command was successful
# set it below if you need (create home directory at initial login)
[root@node01 ~]# authselect enable-feature with-mkhomedir
[root@node01 ~]# systemctl enable --now oddjobd
[root@node01 ~]# exit
logout
Fedora Linux 40 (Server Edition)
Kernel 6.8.7-300.fc40.x86_64 on an x86_64 (ttyS0)
Activate the web console with: systemctl enable --now cockpit.socket
node01 login: redhat # FreeIPA user
Password: # password
Password expired. Change your password now. # required to change password at initial login
Current Password: # current password
New password: # new password
Retype new password:
[redhat@node01 ~]$ # logined
User Accounts Management
This is the Basic Operation of User Accounts Management.
Step [1]Add FreeIPA user accounts.
[root@bizantum ~]# ipa user-add fedora --first=Fedora --last=Linux --password
Password: # set password
Enter Password again to verify:
-------------------
Added user "fedora"
-------------------
User login: fedora
First name: Fedora
Last name: Linux
Full name: Fedora Linux
Display name: Fedora Linux
Initials: FL
Home directory: /home/fedora
GECOS: Fedora Linux
Login shell: /bin/bash
Principal name: fedora@IPA.bizantum.lab
Principal alias: fedora@IPA.bizantum.lab
User password expiration: 20240514000727Z
Email address: fedora@ipa.bizantum.lab
UID: 446800003
GID: 446800003
Password: True
Member of groups: ipausers
Kerberos keys available: True
Step [2]Change password of FreeIPA user account.
[root@bizantum ~]# ipa passwd fedora
New Password:
Enter New Password again to verify:
-------------------------------------------
Changed password for "fedora@IPA.bizantum.lab"
-------------------------------------------
Step [3]Lock or Unlock FreeIPA user accounts.
[root@bizantum ~]# ipa user-disable fedora
------------------------------
Disabled user account "fedora"
------------------------------
[root@bizantum ~]# ipa user-enable fedora
-----------------------------
Enabled user account "fedora"
-----------------------------
Step [4]Search FreeIPA user accounts.
[root@bizantum ~]# ipa user-find fedora
--------------
1 user matched
--------------
User login: fedora
First name: Fedora
Last name: Linux
Home directory: /home/fedora
Login shell: /bin/bash
Principal name: fedora@IPA.bizantum.lab
Principal alias: fedora@IPA.bizantum.lab
Email address: fedora@ipa.bizantum.lab
UID: 446800003
GID: 446800003
Account disabled: False
----------------------------
Number of entries returned 1
----------------------------
[root@bizantum ~]# ipa user-show --raw fedora
uid: fedora
givenname: Fedora
sn: Linux
homedirectory: /home/fedora
loginshell: /bin/bash
krbcanonicalname: fedora@IPA.bizantum.lab
krbprincipalname: fedora@IPA.bizantum.lab
mail: fedora@ipa.bizantum.lab
uidnumber: 446800003
gidnumber: 446800003
nsaccountlock: FALSE
has_password: TRUE
has_keytab: TRUE
Step [5]Remove FreeIPA user accounts.
[root@bizantum ~]# ipa user-del fedora
---------------------
Deleted user "fedora"
---------------------
Step [6]Add FreeIPA group accounts.
[root@bizantum ~]# ipa group-add --desc='Development Group' development
-------------------------
Added group "development"
------------------------
Group name: development
Description: Development Group
GID: 446800007
Step [7]Add members to a FreeIPA group account.
[root@bizantum ~]# ipa group-add-member --users=redhat development
Group name: development
Description: Development Group
GID: 446800007
Member users: redhat
-------------------------
Number of members added
-------------------------
Step [8]Add FreeIPA group to FreeIPA group nested.
[root@bizantum ~]# ipa group-add-member --groups=development hiroshima
Group name: hiroshima
Description: Development Group
GID: 446800008
Member groups: development
Indirect Member users: redhat
-------------------------
Number of members added 1
-------------------------
Step [9]Search FreeIPA group accounts.
[root@bizantum ~]# ipa group-find development
----------------
2 groups matched
----------------
Group name: development
Description: Development Group
GID: 446800007
Group name: hiroshima
Description: Development Group
GID: 446800008
----------------------------
Number of entries returned 2
----------------------------
Step [10]Remove FreeIPA group accounts.
[root@bizantum ~]# ipa group-del hiroshima
-------------------------
Deleted group "hiroshima"
-------------------------
Web Admin Console
It's possible to operate FreeIPA Server on Web Admin Console.
Step [1]Start Web browser on any Client Computer and Access to [https://(FreeIPA server's hostname or IP address)/]. Then, login form of FreeIPA server is shown like follows, Login with any FreeIPA user.
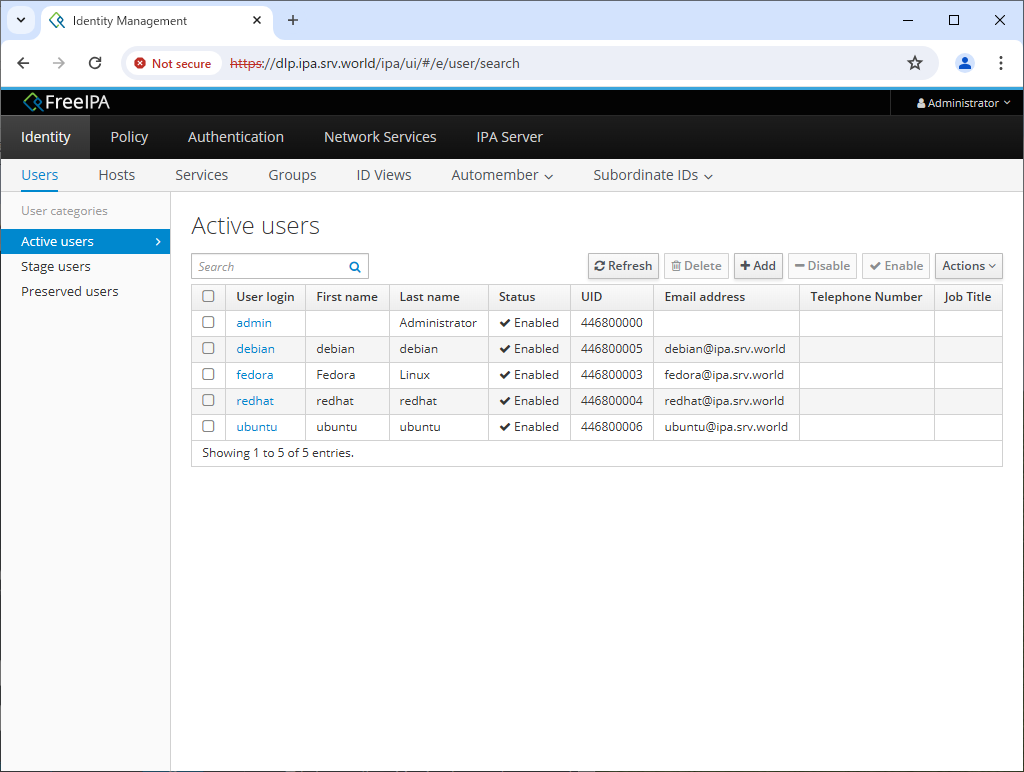
Step [2]If you log in as a general user, you can check and edit your own user information, and if you log in as [admin], you can perform general FreeIPA server management operations visually.
- Get link
- X
- Other Apps










Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.