
Introduction
In this article, we will explore the what, who, where, when, why, and how of DNS Server (BIND) functionality on the Fedora 40 platform, so let's get started.
Overview
What
BIND (Berkeley Internet Name Domain) is an open-source software that implements the Domain Name System (DNS) protocols for the Internet. It allows you to manage and resolve domain names to IP addresses and vice versa.
Who
BIND is developed and maintained by the Internet Systems Consortium (ISC). It is widely used by Internet Service Providers (ISPs), corporations, and educational institutions for managing DNS services.
Where
BIND can be installed on various Unix-like operating systems, including Linux, FreeBSD, and Solaris, as well as on Windows platforms.
When
BIND has been in development since the early 1980s. It is typically used whenever there is a need to resolve domain names into IP addresses, such as in web hosting, email delivery, and network services.
Why
Using BIND as a DNS server offers several advantages and some disadvantages:
| Pros | Cons |
|---|---|
| Flexibility - Highly configurable and can be tailored to different needs. | Complexity - Can be complex to set up and manage for beginners. |
| Open Source - Free to use and modify. | Resource Intensive - Requires significant system resources. |
| Widely Supported - Extensive community support and documentation. | Security - Being widely used, it can be a target for attacks; requires regular updates and patches. |
How
Setting up BIND involves several steps:
- Install BIND software using package manager (e.g., `apt-get install bind9` on Ubuntu).
- Configure the named.conf file to define DNS zones and options.
- Create zone files for forward and reverse DNS lookups.
- Start and test the BIND service to ensure it is resolving DNS queries correctly.
Consequences
Using BIND as your DNS server can significantly enhance network efficiency and reliability, but it also requires diligent management to ensure security and performance. Misconfigurations can lead to downtime or vulnerabilities.
Conclusion
BIND is a robust and flexible solution for managing DNS services. It offers extensive features and is backed by a strong community, making it a preferred choice for many organizations. However, it requires careful configuration and maintenance to leverage its full potential effectively.
Configure Internal Network
Install BIND to Configure DNS (Domain Name System) Server to provide Name or Address Resolution service for Clients.
Step [1]Install BIND.
[root@bizantum ~]# dnf -y install bind bind-utils
Step [2]On this example, Configure BIND for Internal Network. The example follows is for the case that Local network is [10.0.0.0/24], Domain name is [srv.bizantum], Replace them to your own environment.
[root@bizantum ~]# vi /etc/named.conf
.....
.....
// add : set ACL entry for local network
acl internal-network {
10.0.0.0/24;
};
options {
// change ( listen all )
listen-on port 53 { any; };
// change if need ( if not listen IPv6, set [none] )
listen-on-v6 { any; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
// add local network set on [acl] section above
// network range you allow to receive queries from hosts
allow-query { localhost; internal-network; };
// network range you allow to transfer zone files to clients
// add secondary DNS servers if it exist
allow-transfer { localhost; };
.....
.....
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
/* https://fedoraproject.org/wiki/Changes/CryptoPolicy */
include "/etc/crypto-policies/back-ends/bind.config";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
// add zones for your network and domain name
zone "srv.bizantum" IN {
type primary;
file "srv.bizantum.lan";
allow-update { none; };
};
zone "0.0.10.in-addr.arpa" IN {
type primary;
file "0.0.10.db";
allow-update { none; };
};
# if you don't use IPv6 and also suppress logs for IPv6 related, possible to change
# set BIND to use only IPv4
[root@bizantum ~]# vi /etc/sysconfig/named
# add to last line
OPTIONS="-4"
# For how to write the section [*.*.*.*.in-addr.arpa], write your network address reversely like follows
# case of 10.0.0.0/24
# network address ⇒ 10.0.0.0
# network range ⇒ 10.0.0.0 - 10.0.0.255
# how to write ⇒ 0.0.10.in-addr.arpa
# case of 192.168.1.0/24
# network address ⇒ 192.168.1.0
# network range ⇒ 192.168.1.0 - 192.168.1.255
# how to write ⇒ 1.168.192.in-addr.arpa
Step [3]Next, Configure Zone Files for each Zone you set in [named.conf] above. To Configure Zone Files, refer to here.
Configure External Network
Install BIND to Configure DNS (Domain Name System) Server to provide Name or Address Resolution service for Clients.
Step [1]Install BIND.
[root@bizantum ~]# dnf -y install bind bind-utils
Step [2]On this example, Configure BIND for External Network. The example follows is for the case that External network is [172.16.0.80/29], Domain name is [srv.bizantum], Replace them to your own environment. ( Actually, [172.16.0.80/29] is for private IP addresses, though. )
[root@bizantum ~]# vi /etc/named.conf
.....
.....
options {
// change ( listen all )
listen-on port 53 { any; };
// change if need ( if not listen IPv6, set [none] )
listen-on-v6 { any; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
// change : receive queries from all hosts
allow-query { any; };
// network range you allow to transfer zone files to clients
// add secondary DNS servers if it exist
allow-transfer { localhost; };
.....
.....
// change : not allow recursive queries
// answer to zones only this server has their entries
recursion no;
dnssec-enable yes;
dnssec-validation yes;
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
/* https://fedoraproject.org/wiki/Changes/CryptoPolicy */
include "/etc/crypto-policies/back-ends/bind.config";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
// add zones for your network and domain name
zone "srv.bizantum" IN {
type primary;
file "srv.bizantum.wan";
allow-update { none; };
};
zone "80.0.16.172.in-addr.arpa" IN {
type primary;
file "80.0.16.172.db";
allow-update { none; };
};
# if you don't use IPv6 and also suppress logs for IPv6 related, possible to change
# set BIND to use only IPv4
[root@bizantum ~]# vi /etc/sysconfig/named
# add to last line
OPTIONS="-4"
Step [3]Next, Configure Zone Files for each Zone you set in [named.conf] above. To Configure Zone Files, refer to here.
Configure Zone Files
Configure Zone Files for each Zone set in [named.conf]. Replace Network or Domain name on the example below to your own environment.
Step [1]Create zone files that servers resolve IP address from Domain name. The example below uses Internal network [10.0.0.0/24], Domain name [srv.bizantum]. Replace to your own environment.
[root@bizantum ~]# vi /var/named/srv.bizantum.lan
$TTL 86400
@ IN SOA doh.bizantum.local. root.srv.bizantum. (
;; any numerical values are OK for serial number but
;; recommendation is [YYYYMMDDnn] (update date + number)
2024042501 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
;; define Name Server
IN NS doh.bizantum.local.
;; define Name Server's IP address
IN A 10.0.0.30
;; define Mail Exchanger Server
IN MX 10 doh.bizantum.local.
;; define each IP address of a hostname
bizantum IN A 10.0.0.30
www IN A 10.0.0.31
Step [2]Create zone files that servers resolve Domain name from IP address. The example below uses Internal network [10.0.0.0/24], Domain name [srv.bizantum]. Replace to your own environment.
[root@bizantum ~]# vi /var/named/0.0.10.db
$TTL 86400
@ IN SOA doh.bizantum.local. root.srv.bizantum. (
2024042501 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
;; define Name Server
IN NS doh.bizantum.local.
;; define each hostname of an IP address
30 IN PTR doh.bizantum.local.
31 IN PTR www.bizantum.local.
Step [3]Next, Start BIND and Verify Name or Address Resolution, refer to here.
Enable BIND Service
Step [1]Start and Enable BIND Service.
[root@bizantum ~]# systemctl enable --now named
Step [2]If Firewalld is running, allow DNS service. DNS uses [53/TCP,UDP].
[root@bizantum ~]# firewall-cmd --add-service=dns
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [3] Change DNS setting to refer to own DNS if need. (replace [enp1s0] to your own environment).
[root@bizantum ~]# nmcli connection modify enp1s0 ipv4.dns 10.0.0.30
[root@bizantum ~]# nmcli connection up enp1s0
Step [4]Verify Name and Address Resolution. If [ANSWER SECTION] is shown, that's OK.
[root@bizantum ~]# dig doh.bizantum.local.
; <<>> DiG 9.18.26 <<>> doh.bizantum.local.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 54419
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;doh.bizantum.local. IN A
;; ANSWER SECTION:
doh.bizantum.local. 86400 IN A 10.0.0.30
;; Query time: 0 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Thu Apr 25 12:46:41 JST 2024
;; MSG SIZE rcvd: 58
[root@bizantum ~]# dig -x 10.0.0.30
; <<>> DiG 9.18.26 <<>> -x 10.0.0.30
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58002
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;30.0.0.10.in-addr.arpa. IN PTR
;; ANSWER SECTION:
30.0.0.10.in-addr.arpa. 86400 IN PTR doh.bizantum.local.
;; Query time: 0 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Thu Apr 25 12:47:16 JST 2024
;; MSG SIZE rcvd: 78
Use View Statement
This is an example to use View Statement in [named.conf]. On this example, Configure both settings for Internal Network like here and settings for External Network like here with View Statement in [named.conf].
Step [1]This example uses internal network [10.0.0.0/24], external network [172.16.0.80/29], domain name [srv.bizantum], Replace them for your own environment. ( Actually, [172.16.0.80/29] is for private IP addresses, though. )
[root@bizantum ~]# vi /etc/named.conf
.....
.....
// add : set ACL entry for local network
acl internal-network {
10.0.0.0/24;
};
options {
// change ( listen all )
listen-on port 53 { any; };
// change if need ( if not listen IPv6, set [none] )
listen-on-v6 { any; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
// add local network set on [acl] section above
// network range you allow to receive queries from hosts
allow-query { localhost; internal-network; };
// network range you allow to transfer zone files to clients
// add secondary DNS servers if it exist
allow-transfer { localhost; };
.....
.....
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
/* https://fedoraproject.org/wiki/Changes/CryptoPolicy */
include "/etc/crypto-policies/back-ends/bind.config";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
// change all lines follows
// set internal network zones
view "internal" {
match-clients {
localhost;
internal-network;
};
zone "." IN {
type hint;
file "named.ca";
};
zone "srv.bizantum" IN {
type primary;
file "srv.bizantum.lan";
allow-update { none; };
};
zone "0.0.10.in-addr.arpa" IN {
type primary;
file "0.0.10.db";
allow-update { none; };
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
};
// set external network zones
view "external" {
// match all except targets defined on [match-clients] on internal section
match-clients { any; };
allow-query { any; };
// not allow recursive queries
recursion no;
zone "srv.bizantum" IN {
type primary;
file "srv.bizantum.wan";
allow-update { none; };
};
zone "80.0.16.172.in-addr.arpa" IN {
type primary;
file "80.0.16.172.db";
allow-update { none; };
};
};
Step [2]For configuration of each Zone files set in [named.conf] above, refer to here.
Set Alias (CNAME)
If you'd like to set Alias (Another Name) to a Host, set CNAME record in a zone file.
Step [1]Set CNAME record in a zone file.
[root@bizantum ~]# vi /var/named/srv.bizantum.lan
$TTL 86400
@ IN SOA doh.bizantum.local. root.srv.bizantum. (
;; update serial number
2024042502 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
IN NS doh.bizantum.local.
IN A 10.0.0.30
IN MX 10 doh.bizantum.local.
bizantum IN A 10.0.0.30
www IN A 10.0.0.31
;; [Alias] IN CNAME [Original Name]
ftp IN CNAME doh.bizantum.local.
[root@bizantum ~]# rndc reload
server reload successful
# verify resolution
[root@bizantum ~]# dig ftp.srv.bizantum.
; <<>> DiG 9.18.26 <<>> ftp.srv.bizantum.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 25007
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;ftp.srv.bizantum. IN A
;; ANSWER SECTION:
ftp.srv.bizantum. 86400 IN CNAME doh.bizantum.local.
doh.bizantum.local. 86400 IN A 10.0.0.30
;; Query time: 0 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Thu Apr 25 12:55:39 JST 2024
;; MSG SIZE rcvd: 76
Configure Chroot Environment
If you'd like to configure Chroot Environment for named, Set like follows.
Step [1]After setting Chroot environment, configuration files are placed under [/var/named/chroot]. [named.conf] is placed under [/var/named/chroot/etc/named.conf], zone files are placed [/var/named/chroot/var/named/***]. When modify settings, Change them under [/var/named/chroot] files.
[root@bizantum ~]# dnf -y install bind-chroot
[root@bizantum ~]# mkdir /var/named/chroot/usr/lib64/named
[root@bizantum ~]# /usr/libexec/setup-named-chroot.sh /var/named/chroot on
[root@bizantum ~]# systemctl disable --now named
[root@bizantum ~]# systemctl enable --now named-chroot
Created symlink /etc/systemd/system/multi-user.target.wants/named-chroot.service → /usr/lib/systemd/system/named-chroot.service.
[root@bizantum ~]# ll /var/named/chroot/etc
total 716
drwxr-x---. 3 root named 23 Apr 25 12:57 crypto-policies
-rw-r--r--. 2 root root 309 Apr 4 09:00 localtime
drwxr-x---. 2 root named 6 Apr 22 09:00 named
-rw-r-----. 1 root named 2259 Apr 25 12:51 named.conf
-rw-r-----. 1 root named 1034 Apr 22 09:00 named.rfc1912.zones
-rw-r--r--. 1 root named 686 Apr 22 09:00 named.root.key
drwxr-x---. 3 root named 25 Apr 25 12:57 pki
-rw-r--r--. 1 root root 6714 Nov 29 19:34 protocols
-rw-r-----. 1 root named 100 Apr 25 12:46 rndc.key
-rw-r--r--. 1 root root 701707 Nov 29 19:34 services
[root@bizantum ~]# ll /var/named/chroot/var/named
total 24
-rw-r--r--. 1 root root 313 Apr 25 12:33 0.0.10.db
drwxr-x---. 8 root named 73 Apr 25 12:57 chroot
drwxrwx---. 2 named named 23 Apr 25 12:46 data
drwxrwx---. 2 named named 108 Apr 25 12:55 dynamic
-rw-r-----. 1 root named 3314 Apr 22 09:00 named.ca
-rw-r-----. 1 root named 152 Apr 22 09:00 named.empty
-rw-r-----. 1 root named 152 Apr 22 09:00 named.localhost
-rw-r-----. 1 root named 168 Apr 22 09:00 named.loopback
drwxrwx---. 2 named named 6 Apr 22 09:00 slaves
-rw-r--r--. 1 root root 404 Apr 25 12:55 srv.bizantum.lan
Configure Secondary Server
Configure DNS Secondary Server (Slave Server). On this example, it shows to configure DNS Secondary Server [ns.server.education] (192.168.100.85) that DNS Master Server is [bizantum.srv.bizantum] (172.16.0.82) configured like here. Replace IP address and Hostname to your own environment.
Step [1]Configure on DNS Master Server Host.
[root@bizantum ~]# vi /etc/named.conf
.....
.....
options {
listen-on port 53 { any; };
listen-on-v6 { any; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
allow-query { localhost; internal-network; };
// add secondary server to allow to transfer zone files
allow-transfer { localhost; 192.168.100.85; };
.....
.....
[root@bizantum ~]# vi /var/named/srv.bizantum.wan
$TTL 86400
@ IN SOA doh.bizantum.local. root.srv.bizantum. (
;; update serial number
2024042503 ;Serial
3600 ;Refresh
1800 ;Retry
604800 ;Expire
86400 ;Minimum TTL
)
IN NS doh.bizantum.local.
;; add secondary server
IN NS ns.server.education.
IN A 172.16.0.82
IN MX 10 doh.bizantum.local.
bizantum IN A 172.16.0.82
www IN A 172.16.0.83
[root@bizantum ~]# systemctl restart named
Step [2]Configure on DNS Secondary Server Host.
[root@ns ~]# vi /etc/named.conf
// add target zone info
// IP address is the primary server's one
zone "srv.bizantum" IN {
type secondary;
primaries { 172.16.0.82; };
file "slaves/srv.bizantum.wan";
notify no;
};
[root@ns ~]# systemctl restart named
[root@ns ~]# ls /var/named/slaves
srv.bizantum.wan # zone file transferred
DNS Server Settings over HTTPS
Configure DNS over HTTPS Server on BIND. Get SSL/TLS certificate, refer to here.
Step [1]Configure BIND.
[root@bizantum ~]# openssl dhparam -out /var/named/dhparam.pem 3072
[root@bizantum ~]# cp /etc/letsencrypt/live/bizantum.srv.bizantum/{fullchain.pem,privkey.pem} /var/named/
[root@bizantum ~]# chown named:named /var/named/{fullchain.pem,privkey.pem,dhparam.pem}
[root@bizantum ~]# vi /etc/named.conf
// add settings for certificate
tls local-tls {
key-file "/var/named/privkey.pem";
cert-file "/var/named/fullchain.pem";
dhparam-file "/var/named/dhparam.pem";
ciphers "HIGH:!kRSA:!aNULL:!eNULL:!RC4:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS:!SHA1:!SHA256:!SHA384";
prefer-server-ciphers yes;
session-tickets no;
};
http local {
endpoints { "/dns-query"; };
};
options {
// change like follows
listen-on tls local-tls http local { any; };
listen-on-v6 tls local-tls http local { any; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
.....
.....
[root@bizantum ~]# systemctl restart named
Step [2]If SELinux is enabled, change policy.
[root@bizantum ~]# setsebool -P named_tcp_bind_http_port on
Step [3]If Firewalld is running, allow service ports.
[root@bizantum ~]# firewall-cmd --add-service={http,https}
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [4]Verify Name Resolution with HTTPS on localhost.
[root@bizantum ~]# dig +https @localhost doh.bizantum.local.
; <<>> DiG 9.18.26 <<>> +https @localhost doh.bizantum.local.
; (2 servers found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 37917
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 506c388df8078843010000006629d8b64880247e6d39fdda (good)
;; QUESTION SECTION:
;doh.bizantum.local. IN A
;; ANSWER SECTION:
doh.bizantum.local. 86400 IN A 10.0.0.30
;; Query time: 0 msec
;; SERVER: ::1#443(localhost) (HTTPS)
;; WHEN: Thu Apr 25 13:14:46 JST 2024
;; MSG SIZE rcvd: 86
Configure Chroot Environment
Configure Fedora Client to refer to your DNS over HTTPS Server.
Step [1] Install dnscrypt-proxy. Before it, make sure the DNS Stamp on the following site, it needs on dnscrypt-proxy settings. ⇒ https://dnscrypt.info/stamps/ Select or Input like follows. Then note the value [sdns://***] on [Stamp] section. * Protocol : DNS-over-HTTPS (DoH) * IP Address : your DNS-over-HTTPS server's IP address * Host Name : your DNS-over-HTTPS server's hostname * Path : the value for [endpoints] that you set on your DNS-over-HTTPS server settings
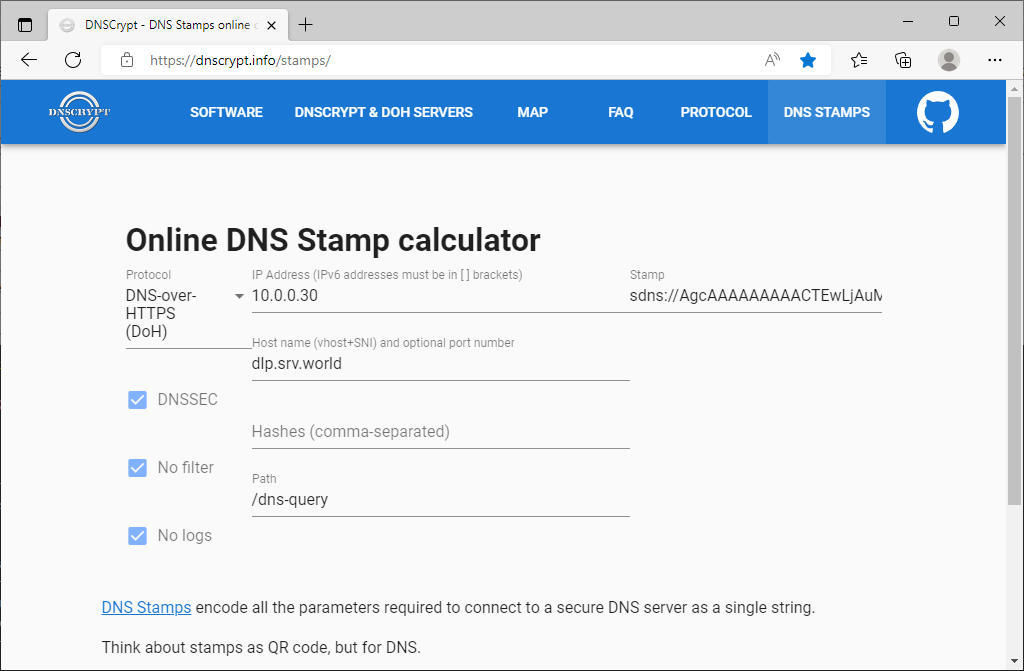
Step [2]Configure Fedora Client to refer to your DoH server.
[root@node01 ~]# dnf -y install dnscrypt-proxy
[root@node01 ~]# mv /etc/dnscrypt-proxy/dnscrypt-proxy.toml /etc/dnscrypt-proxy/dnscrypt-proxy.toml.org
[root@node01 ~]# vi /etc/dnscrypt-proxy/dnscrypt-proxy.toml
# create new
listen_addresses = ['127.0.0.1:53']
ipv4_servers = true
ipv6_servers = false
dnscrypt_servers = false
doh_servers = true
odoh_servers = false
require_dnssec = false
max_clients = 250
keepalive = 30
use_syslog = true
log_files_max_size = 10
log_files_max_age = 7
log_files_max_backups = 1
reject_ttl = 10
cache = true
cache_size = 4096
cache_min_ttl = 2400
cache_max_ttl = 86400
cache_neg_min_ttl = 60
cache_neg_max_ttl = 600
# your DoH server
server_names = ['bizantum.srv.bizantum']
[query_log]
file = '/var/log/dnscrypt-proxy/query.log'
[nx_log]
file = '/var/log/dnscrypt-proxy/nx.log'
# set the Stamp value on [stamp] section that you made sure on [1]
[static]
[static.'bizantum.srv.bizantum']
stamp = 'sdns://AgcAAAAAAAAACTEwLjAuMC4zMAANZGxwLnNydi53b3JsZAovZG5zLXF1ZXJ5'
[root@node01 ~]# mkdir /var/log/dnscrypt-proxy
[root@node01 ~]# systemctl enable --now dnscrypt-proxy
# change DNS to the IP address that dnscrypt-proxy listens
[root@node01 ~]# nmcli connection modify enp1s0 ipv4.dns 127.0.0.1
[root@node01 ~]# nmcli connection up enp1s0
# verify resolution
[root@node01 ~]# dig www.bizantum.local.
; <<>> DiG 9.18.24 <<>> www.bizantum.local.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 39342
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;www.bizantum.local. IN A
;; ANSWER SECTION:
www.bizantum.local. 86400 IN A 10.0.0.31
;; Query time: 2 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Thu Apr 25 13:22:44 JST 2024
;; MSG SIZE rcvd: 58
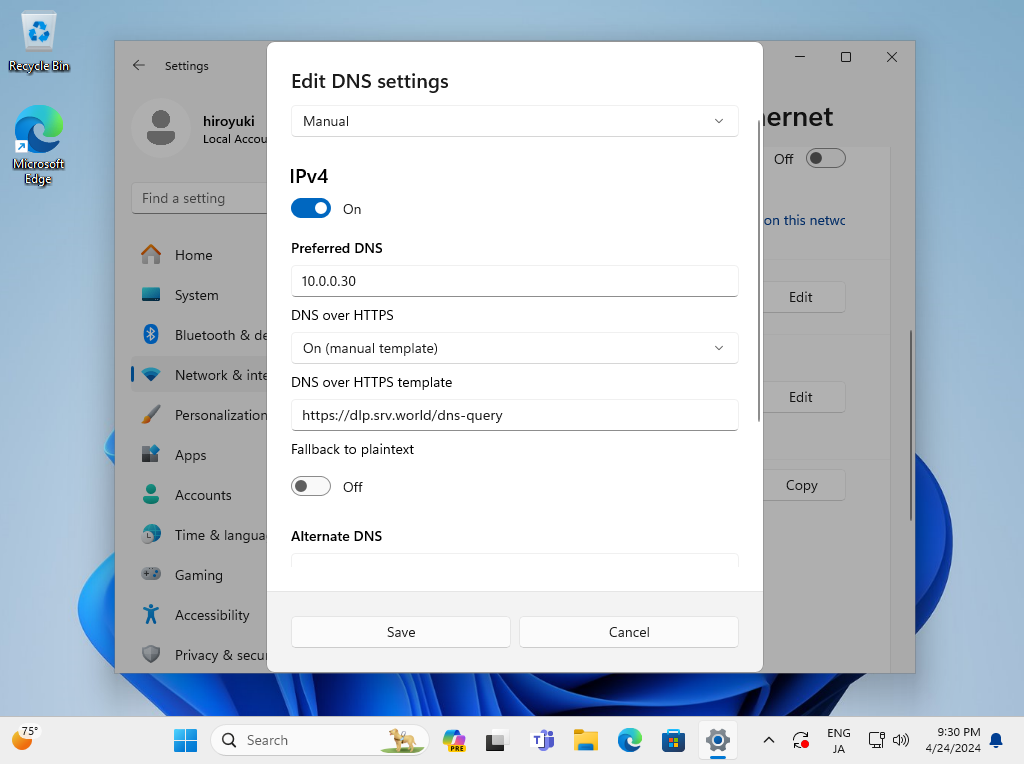
Step [3]Configure Windows Client to refer to your DNS over HTTPS Server. This example is based on Windows 11. Open the Network setting and click the [Edit] button on [DNS server assignment] section. Next, Input your DoH Server address on the [Preferred DNS] section. For [DNS over HTTPS] section, select [On (manual template)] and For [DNS over HTTPS template] section, input the value of [endpoints] in named.conf you set.
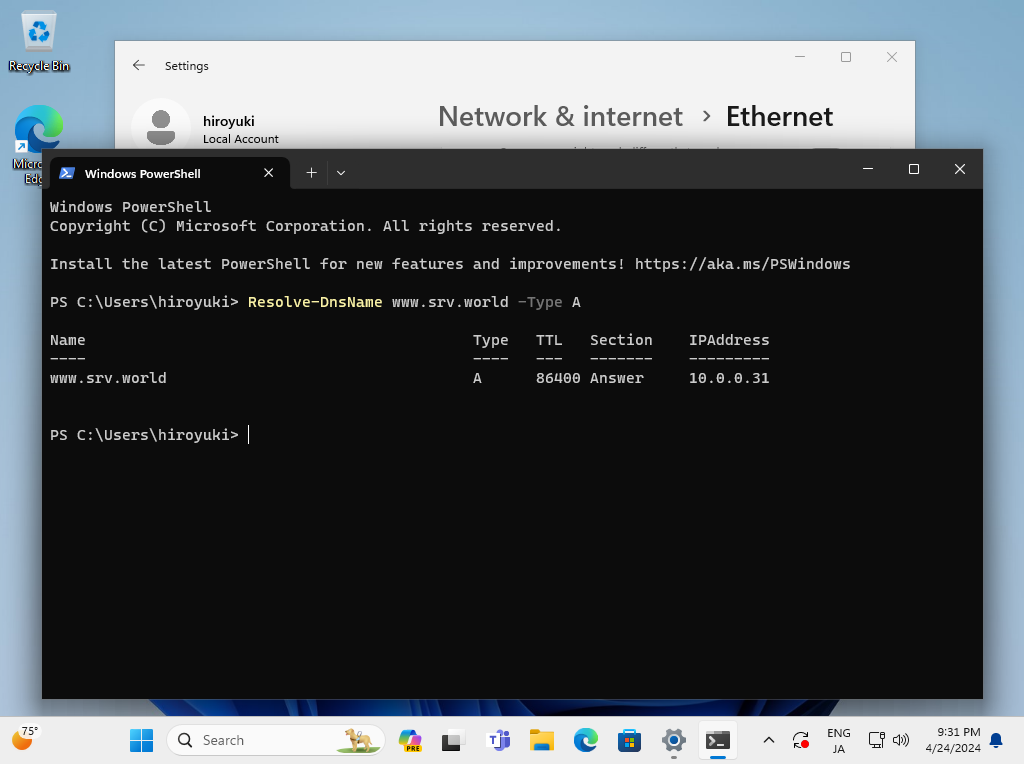
Step [4]Configure Windows Client to refer to your DNS over HTTPS Server. This example is based on Windows 11. After setting your DoH server, verify Name and Address Resolution.
- Get link
- X
- Other Apps










Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.