
Introduction
This guide covers the installation and configuration of Apache HTTPD on Fedora 40 using the 5W1H approach. We will explore the What, Who, Where, When, Why, How, Consequences, and Conclusion of setting up an Apache HTTPD server.
- Overview
- Apache httpd : Install
- Apache httpd : Virtual Hostings
- Apache httpd : SSL/TLS Setting
- Apache httpd : Enable Userdir
- Apache httpd : Use CGI Scripts
- Apache httpd : Use PHP Scripts
- Apache httpd : Basic Authentication
- Apache httpd : Configure WebDAV
- Apache httpd : Basic Auth + LDAP
- Apache httpd : Configure mod_md
Overview
What
Apache HTTPD is a highly popular open-source web server software used to serve websites and web applications. It supports a variety of features and modules, providing flexibility and power for web development.
Who
This guide is intended for system administrators and developers who need to set up a web server to host websites or web applications on Fedora 40.
Where
The setup process can be carried out on any server running Fedora 40, whether it's a physical machine, virtual machine, or cloud instance.
When
Setting up Apache HTTPD should be done during a planned maintenance window to avoid potential disruptions to existing services.
Why
Implementing Apache HTTPD on your server offers several advantages:
| Pros | Cons |
|---|---|
| Open-source and free to use | Configuration complexity for beginners |
| Flexible with many available modules | Resource-intensive under heavy load |
| Highly customizable | Requires regular updates and maintenance |
How
Follow these steps to set up Apache HTTPD on Fedora 40:
| Step 1 | Update your system: sudo dnf update -y |
| Step 2 | Install the Apache HTTPD package: sudo dnf install -y httpd |
| Step 3 | Start and enable the HTTPD service: sudo systemctl start httpd sudo systemctl enable httpd |
| Step 4 | Open the firewall for HTTP and HTTPS traffic: sudo firewall-cmd --permanent --add-service=http sudo firewall-cmd --permanent --add-service=https sudo firewall-cmd --reload |
| Step 5 | Verify Apache is running by accessing http://your_server_ip in a web browser. |
Consequences
Setting up Apache HTTPD on Fedora 40 can have the following consequences:
| Positive |
|
| Negative |
|
Conclusion
Setting up Apache HTTPD on Fedora 40 is crucial for hosting and managing web services. While the initial setup can be complex and demands regular maintenance, the flexibility, customization options, and powerful features of Apache HTTPD make it an excellent choice for web hosting. By following this guide, system administrators can ensure their servers are ready to deliver high-quality web services effectively.
Apache httpd : Install
Install Apache httpd to configure Web Server.
Step [1]Install Apache httpd.
[root@bizantum ~]# dnf -y install httpd
# rename or remove welcome page
[root@bizantum ~]# mv /etc/httpd/conf.d/welcome.conf /etc/httpd/conf.d/welcome.conf.org
Step [2]Configure httpd. Replace Server name to your own environment.
[root@bizantum ~]# vi /etc/httpd/conf/httpd.conf
# line 91 : change to admin's email address
ServerAdmin root@srv.world
# line 100 : change to your server's name
ServerName www.srv.world:80
# line 149 : change (remove [Indexes])
Options FollowSymLinks
# line 156 : change
AllowOverride All
# line 169 : add file name that it can access only with directory's name
DirectoryIndex index.html index.php index.cgi
# add follows to the end
# server's response header
ServerTokens Prod
[root@bizantum ~]# systemctl enable --now httpd
Step [3]If Firewalld is running, allow HTTP service. HTTP uses 80/TCP.
[root@bizantum ~]# firewall-cmd --add-service=http
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [4]Create a HTML test page and access to it from any client computer with web browser. It's OK if following page is shown.
[root@bizantum ~]# vi /var/www/html/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
Test Page
</div>
</body>
</html>
Apache httpd : Virtual Hostings
Configure Virtual Hostings to use multiple domain names.
Step [1]For example, Add a new Host setting that domain name is [virtual.host], document root is [/var/www/virtual.host].
[root@bizantum ~]# vi /etc/httpd/conf.d/vhost.conf
# create new
# settings for original domain
<VirtualHost *:80>
DocumentRoot /var/www/html
ServerName www.srv.world
</VirtualHost>
# settings for new domain
<VirtualHost *:80>
DocumentRoot /var/www/virtual.host
ServerName www.virtual.host
ServerAdmin webmaster@virtual.host
ErrorLog logs/virtual.host-error_log
CustomLog logs/virtual.host-access_log combined
</VirtualHost>
<Directory "/var/www/virtual.host">
Options FollowSymLinks
AllowOverride All
</Directory>
[root@bizantum ~]# mkdir /var/www/virtual.host
[root@bizantum ~]# systemctl reload httpd
Step [2]Create a test page and access to it from any client computer with web browser. It's OK if following page is shown.
[root@bizantum ~]# vi /var/www/virtual.host/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
Virtual Host Test Page
</div>
</body>
</html>
Apache httpd : SSL/TLS Setting
Configure SSL/TLS setting to use secure encrypt HTTPS connection.
Step [1] Get SSL Certificate, refer to here.
Step [2]Enable SSL/TLS settings.
[root@bizantum ~]# dnf -y install mod_ssl
[root@bizantum ~]# vi /etc/httpd/conf.d/ssl.conf
# line 59 : uncomment
DocumentRoot "/var/www/html"
# line 60 : uncomment and specify hostname
ServerName www.srv.world:443
# line 101 : change to the one got in [1]
SSLCertificateFile /etc/letsencrypt/live/www.srv.world/cert.pem
# line 109 : change to the one got in [1]
SSLCertificateKeyFile /etc/letsencrypt/live/www.srv.world/privkey.pem
# line 118 : change to the one got in [1]
SSLCertificateChainFile /etc/letsencrypt/live/www.srv.world/chain.pem
[root@bizantum ~]# systemctl restart httpd
Step [3]If you'd like to set HTTP connection to redirect to HTTPS (Always on SSL/TLS), Set RewriteRule to each Host settings. For example, if you set Virtual Hostings like the link here, Add RewriteRule like follows. Or It's possible to set RewriteRule in [.htaccess] not in [httpd.conf].
[root@bizantum ~]# vi /etc/httpd/conf.d/vhost.conf
<VirtualHost *:80>
DocumentRoot /var/www/html
ServerName www.srv.world
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
</VirtualHost>
[root@bizantum ~]# systemctl reload httpd
Step [4]If Firewalld is running, allow HTTPS service. HTTPS uses 443/TCP.
[root@bizantum ~]# firewall-cmd --add-service=https
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [5]Verify to access to the test page from any client computer with Web browser via HTTPS.
Apache httpd : Enable Userdir
Enable userdir. Users can create websites under their own home directory by this setting.
Step [1]Enable UserDir setting.
[root@bizantum ~]# vi /etc/httpd/conf.d/userdir.conf
# line 17 : comment out
#UserDir disabled
# line 24 : uncomment
UserDir public_html
# line 32-36
<Directory "/home/*/public_html">
AllowOverride All # change if you need
Options None # change if you need
Require method GET POST OPTIONS
</Directory>
[root@bizantum ~]# systemctl reload httpd
Step [2]If SELinux is enabled, change policy like follows.
[root@bizantum ~]# setsebool -P httpd_enable_homedirs on
[root@bizantum ~]# restorecon -R /home
Step [3]Create a test page with a user and access to it from any client computer with Web browser.
[fedora@www ~]$ mkdir public_html
[fedora@www ~]$ chmod 711 /home/fedora
[fedora@www ~]$ chmod 755 /home/fedora/public_html
[fedora@www ~]$ vi ./public_html/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
UserDir Test Page
</div>
</body>
</html>
Apache httpd : Use CGI Scripts
Use CGI (Common Gateway Interface) Scripts.
Step [1] By default, CGI is allowed under the [/var/www/cgi-bin] directory. It's possible to use CGI Scripts to put under the directory. All files under it are processed as CGI.
# CGI is allowed under the directory
[root@bizantum ~]# grep -n "^ *ScriptAlias" /etc/httpd/conf/httpd.conf
252: ScriptAlias /cgi-bin/ "/var/www/cgi-bin/"
# verify working to create test script
# any languages are OK for CGI scripts (example below is Python3)
[root@bizantum ~]# cat > /var/www/cgi-bin/index.cgi <<'EOF'
#!/usr/bin/python3
print("Content-type: text/html\n")
print("CGI Script Test Page")
EOF
[root@bizantum ~]# chmod 755 /var/www/cgi-bin/index.cgi
[root@bizantum ~]# curl localhost/cgi-bin/index.cgi
CGI Script Test Page
Step [2]If you'd like to allow CGI in other directories, configure like follows. For example, allow in [/var/www/html/cgi-enabled].
[root@bizantum ~]# vi /etc/httpd/conf.d/cgi-enabled.conf
# create new
# specify extension that are processed as CGI on [AddHandler cgi-script] line
<Directory "/var/www/html/cgi-enabled">
Options +ExecCGI
AddHandler cgi-script .cgi .pl .py .rb
</Directory>
[root@bizantum ~]# mkdir /var/www/html/cgi-enabled
[root@bizantum ~]# systemctl reload httpd
Step [3]If SELinux is enabled and also enable CGI except default location like above, add rules like follows.
[root@bizantum ~]# semanage fcontext -a -t httpd_sys_script_exec_t /var/www/html/cgi-enabled
[root@bizantum ~]# restorecon /var/www/html/cgi-enabled
Step [4]Create a CGI test page and access to it from any client computer with web browser.
[root@bizantum ~]# vi /var/www/html/cgi-enabled/index.cgi
#!/usr/bin/python3
print("Content-type: text/html\n")
print("<html>\n<body>")
print("<div style=\"width: 100%; font-size: 40px; font-weight: bold; text-align: center;\">")
print("CGI Script Test Page")
print("</div>")
print("</body>\n</html>")
[root@bizantum ~]# chmod 755 /var/www/html/cgi-enabled/index.cgi
Apache httpd : Use PHP Scripts
Configure httpd to use PHP scripts.
Step [1]Install PHP.
[root@bizantum ~]# dnf -y install php php-mbstring php-pear
Step [2]After installing PHP, Restart httpd, it's OK to do it only. [mod_php] has been Deprecated and PHP-FPM (FPM : FastCGI Process Manager) is configured by default. When [httpd] starts, [php-fpm] also starts for dependency by setting file [/usr/lib/systemd/system/httpd.service.d/php-fpm.conf].
[root@bizantum ~]# systemctl restart httpd
[root@bizantum ~]# systemctl status php-fpm
* php-fpm.service - The PHP FastCGI Process Manager
Loaded: loaded (/usr/lib/systemd/system/php-fpm.service; disabled; preset:6gt;
Drop-In: /usr/lib/systemd/system/service.d
+-- 10-timeout-abort.conf
Active: active (running) since Tue 2024-05-14 10:46:37 JST; 3s ago
Main PID: 2845 (php-fpm)
Status: "Ready to handle connections"
Tasks: 6 (limit: 4638)
Memory: 12.2M (peak: 12.5M)
CPU: 30ms
CGroup: /system.slice/php-fpm.service
.....
.....
# create PHPInfo test page
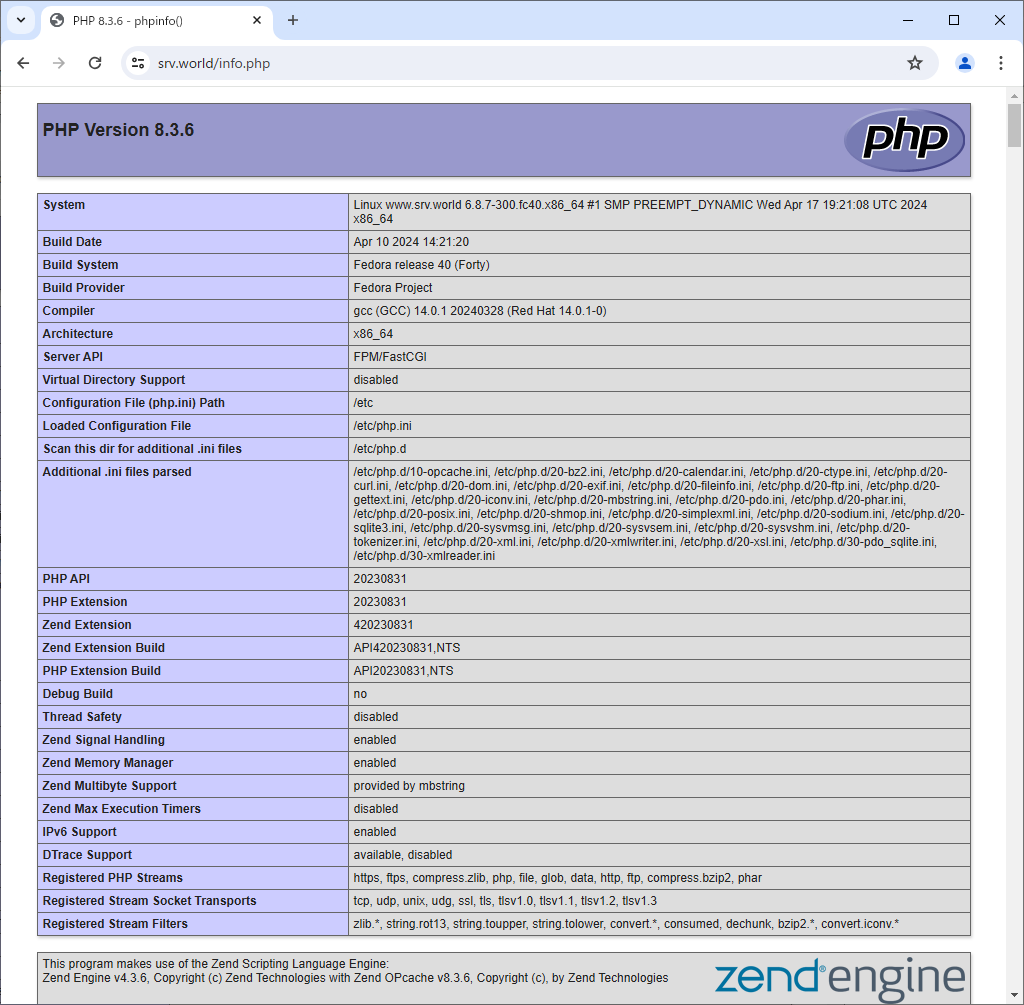
[root@bizantum ~]# echo '<?php phpinfo(); ?>' > /var/www/html/info.php
Step [3]Verify to access to PHPInfo test page from any client computer.
Apache httpd : Basic Authentication
Set Basic Authentication to limit access on specific web pages.
Step [1]Username and password are sent with plain text on Basic Authentication, so Use secure connection with SSL/TLS setting, refer to here.
Step [2]Configure httpd. For example, set Basic Authentication to the directory [/var/www/html/auth-basic].
[root@bizantum ~]# vi /etc/httpd/conf.d/auth_basic.conf
# create new
<Directory /var/www/html/auth-basic>
SSLRequireSSL
AuthType Basic
AuthName "Basic Authentication"
AuthUserFile /etc/httpd/conf/.htpasswd
Require valid-user
</Directory>
# add a user : create a new file with [-c]
[root@bizantum ~]# htpasswd -5 -c /etc/httpd/conf/.htpasswd fedora
New password: # set password
Re-type new password:
Adding password for user fedora
[root@bizantum ~]# mkdir /var/www/html/auth-basic
[root@bizantum ~]# systemctl reload httpd
# create a test page
[root@bizantum ~]# vi /var/www/html/auth-basic/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
Test Page for Basic Authentication
</div>
</body>
</html>
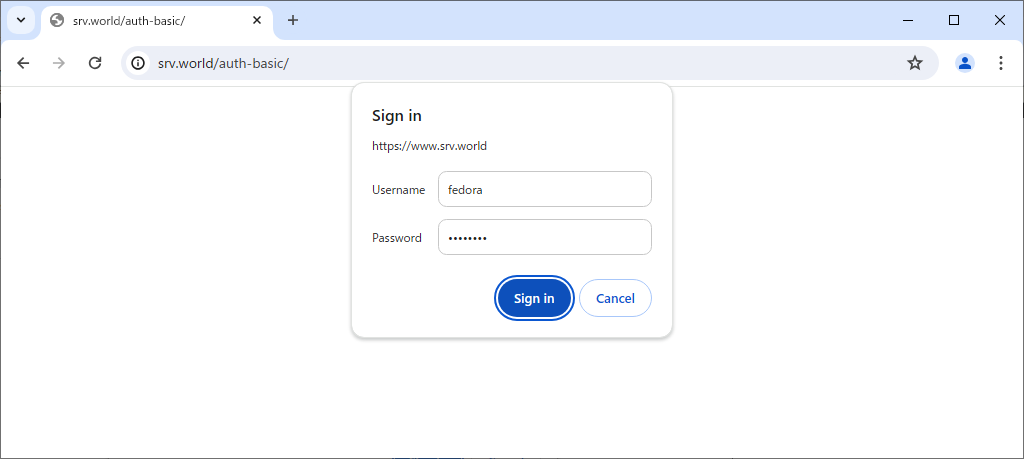
Step [3]Access to the test page from any client computer with web browser. Then authentication is required as settings, answer with a user added in [1].
Step [4]That's OK if authentication is successfully passed and test page is displayed normally.
Apache httpd : Configure WebDAV
Configure WebDAV Folder.
Step [1] Configure SSL/TLS Setting, refer to here.
Step [2]For example, Create a directory [/var/www/webdav] and it makes possible to connect to WebDAV folder only by HTTPS.
[root@bizantum ~]# mkdir /var/www/webdav
[root@bizantum ~]# chown apache:apache /var/www/webdav
[root@bizantum ~]# chmod 770 /var/www/webdav
[root@bizantum ~]# vi /etc/httpd/conf.d/webdav.conf
# create new
Alias /webdav /var/www/webdav
<Location /webdav>
DAV On
SSLRequireSSL
Options +Indexes
AuthType Basic
AuthName WebDAV
AuthUserFile /etc/httpd/conf/.htpasswd
<RequireAny>
Require method GET POST OPTIONS
Require valid-user
</RequireAny>
</Location>
# add a user : create a new file with [-c]
[root@bizantum ~]# htpasswd -5 -c /etc/httpd/conf/.htpasswd fedora
New password: # set password
Re-type new password:
Adding password for user fedora
[root@bizantum ~]# systemctl reload httpd
Step [3]If SELinux is enabled, add rules to allow accesses to target WebDAV directory.
[root@bizantum ~]# chcon -R -t httpd_sys_rw_content_t /var/www/webdav
[root@bizantum ~]# semanage fcontext -a -t httpd_sys_rw_content_t /var/www/webdav
Step [4]Configure WebDAV client on client computer. This example is on Windows 11. Open [PC] and Click [Add a network location] icon on the upper-menu.
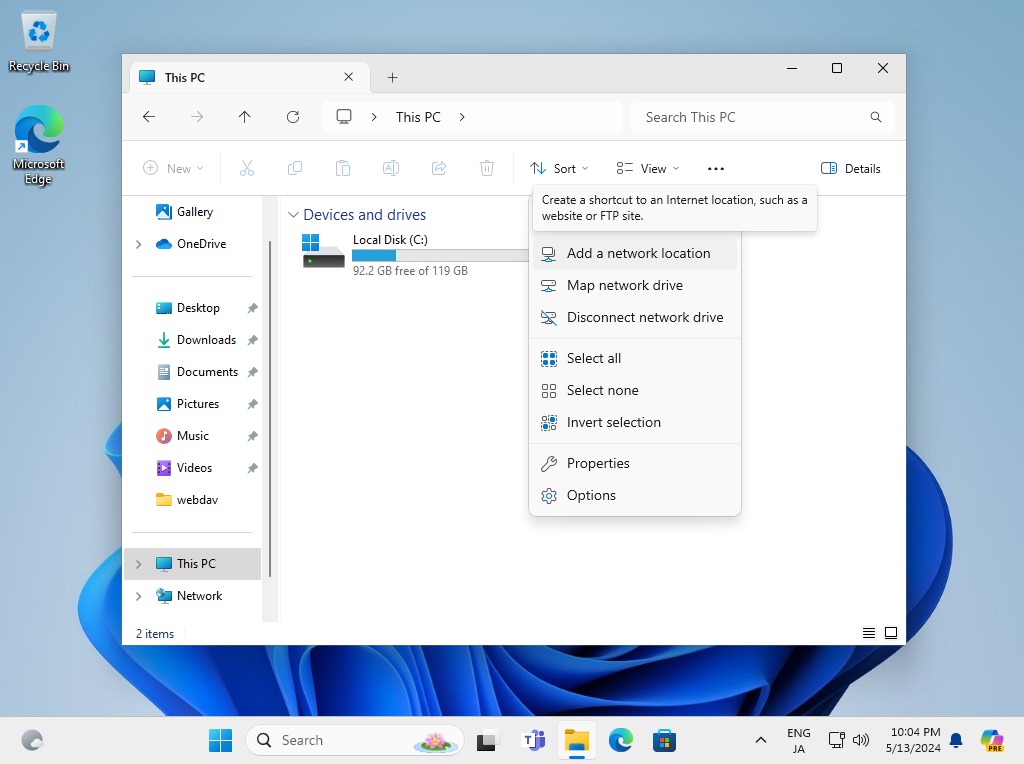
Step [5]Click [Next] button.
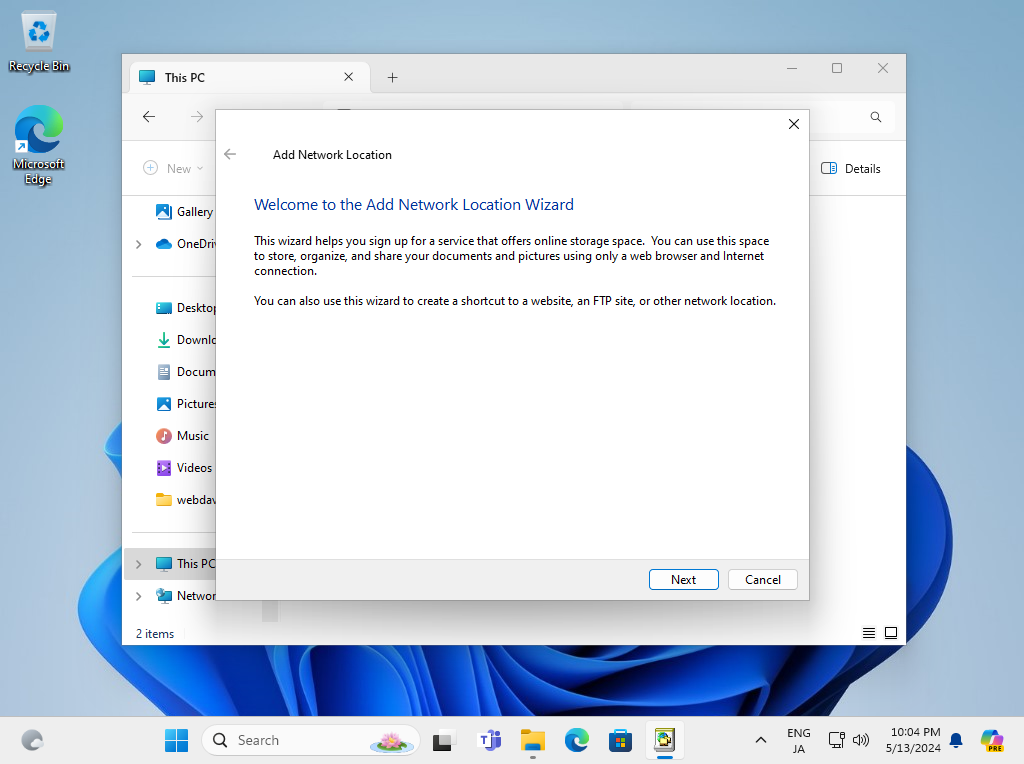
Step [6]Click [Next] button.
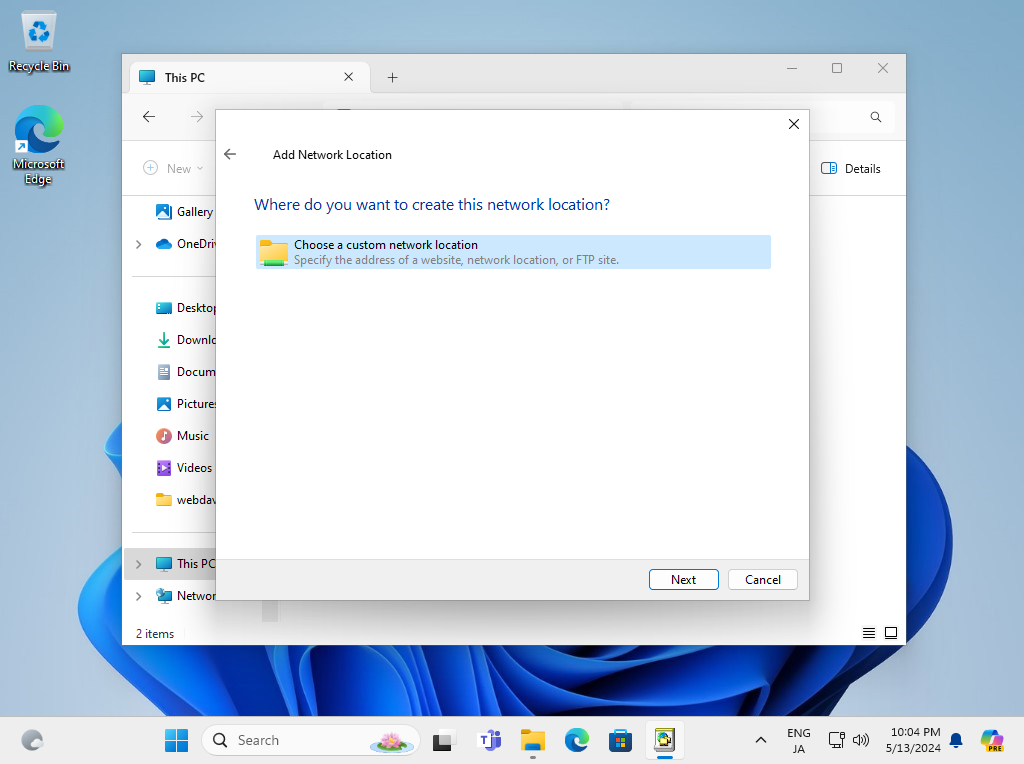
Step [7]Input the URL of WebDav folder.
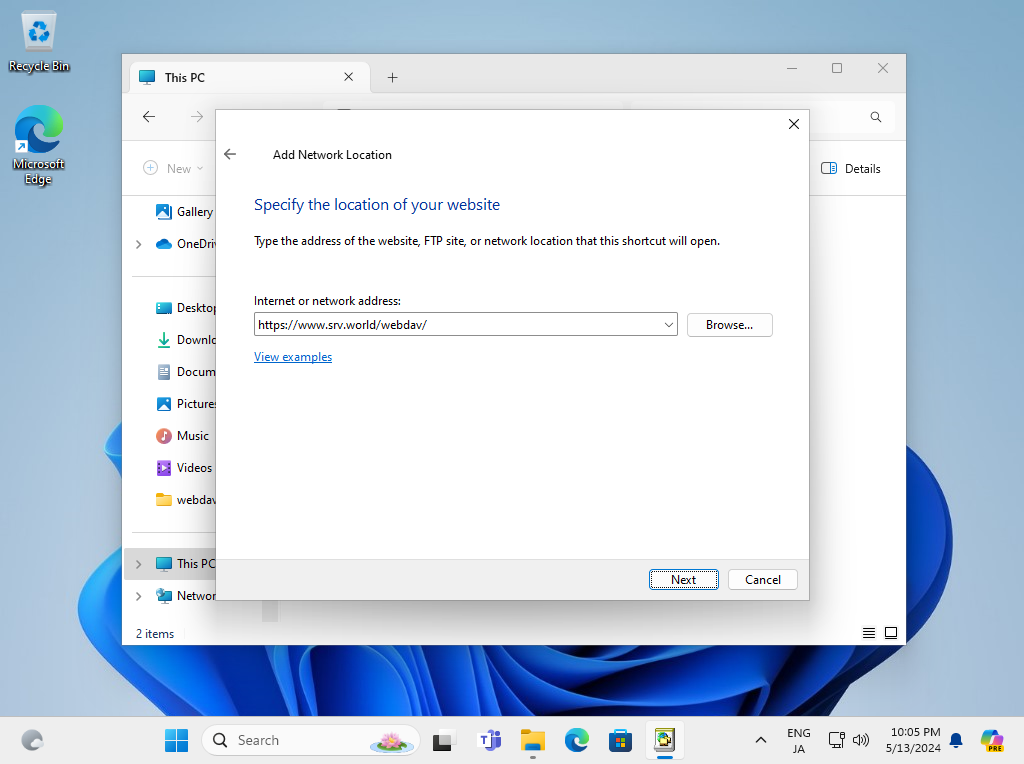
Step [8]Authentication is required, input username and password you added in section [1] by [htpasswd].
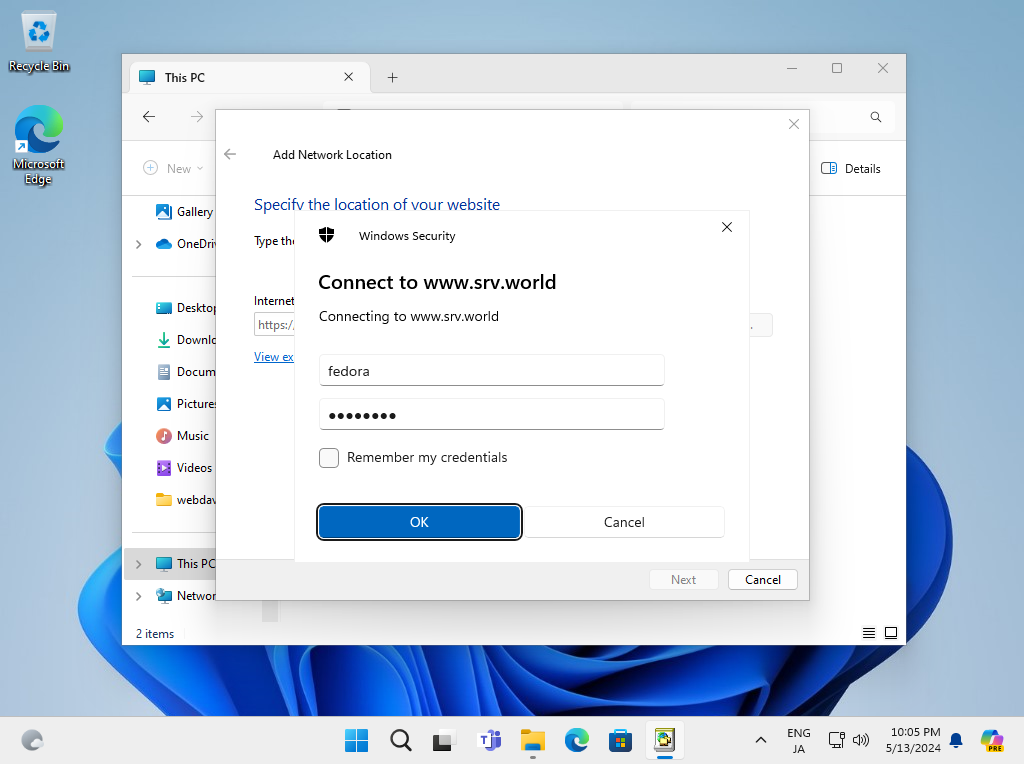
Step [9]Input WebDav Folder Name. Any name is OK, it's used on your Windows Computer.
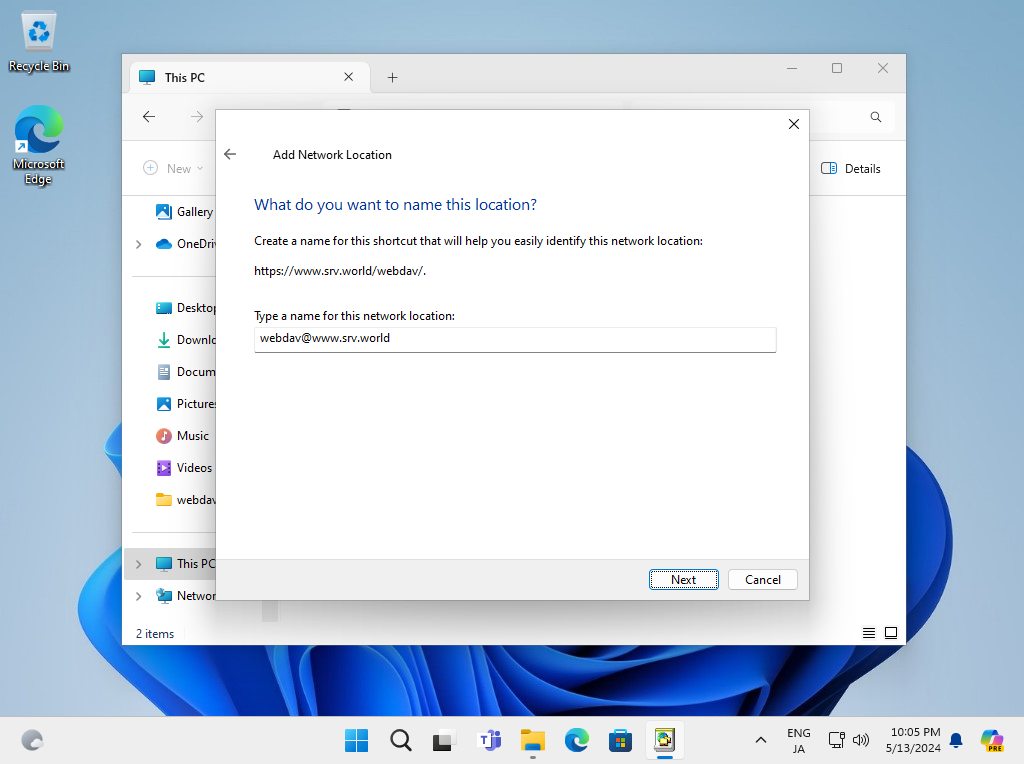
Step [10]Click [Finish] button.
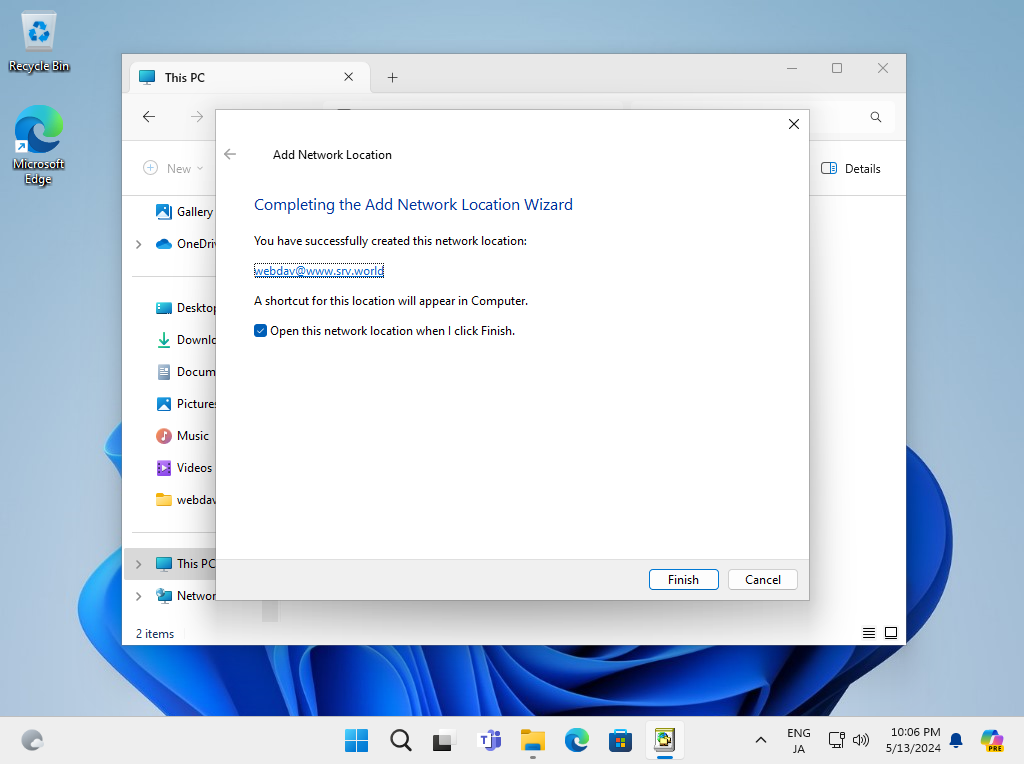
Step [11]Just accessed to WebDav Folder.
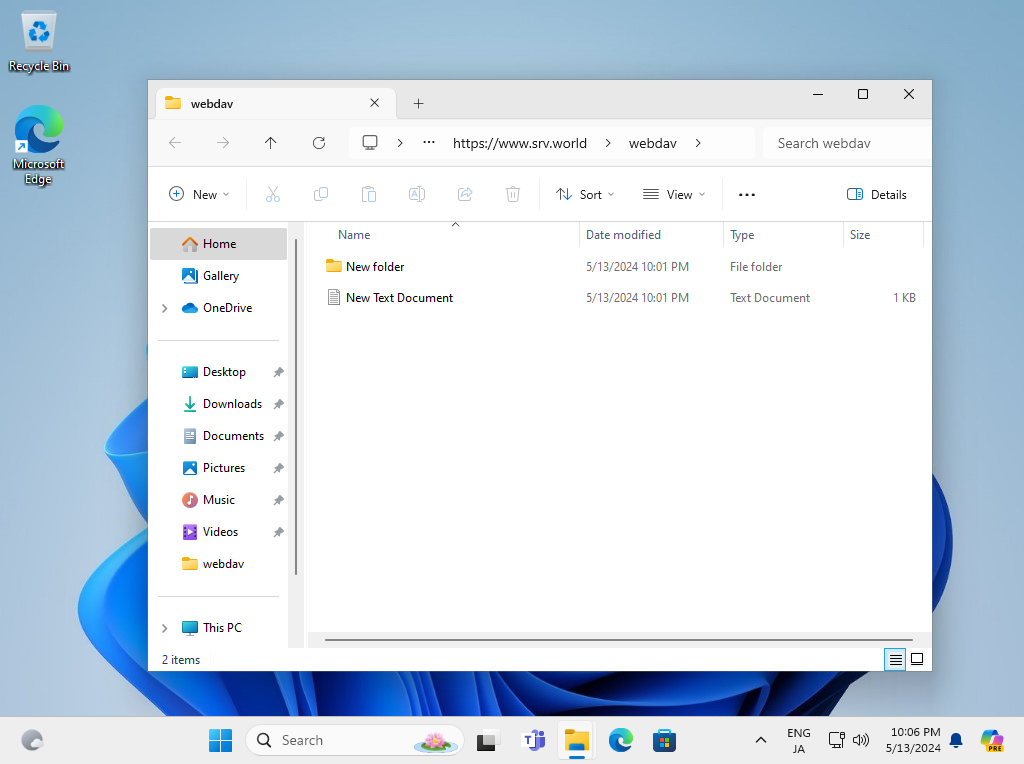
Apache httpd : Basic Auth + LDAP
Configure [mod_ldap] to use LDAP directory users on httpd Basic authentication. On this example, it uses Active Directory like following environment for it. Domain Server : Windows Server 2022 Domain Name : srv.world Hostname : fd3s.srv.world NetBIOS Name : FD3S01 Realm : SRV.WORLD
Step [1] Username and password are sent with plain text on Basic Authentication, so Use secure connection with SSL/TLS setting, refer to here.
Step [2] Create a user on Active Directory for binding Active Directory from httpd. On this example, it creates [ldapuser], it's OK to grant [Domain Users] rights only for it.
Step [3]Install [mod_ldap].
[root@bizantum ~]# dnf -y install mod_ldap
Step [4] Configure Basic authentication + LDAP. For example, set Basic Authentication to the directory [/var/www/html/auth-ldap].
[root@bizantum ~]# vi /etc/httpd/conf.d/authnz_ldap.conf
# create new
# on example below, it limits the range to search the directory only [LDAPUsers] OU
# so only users under the [LDAPUsers] OU can authenticate with this setting
# for [AuthLDAPBindDN] and [AuthLDAPBindPassword], specify the AD user for binding
<Directory "/var/www/html/auth-ldap">
SSLRequireSSL
AuthType Basic
AuthName "LDAP Authentication"
AuthBasicProvider ldap
AuthLDAPURL "ldap://fd3s.srv.world:389/ou=LDAPUsers,dc=srv,dc=world?sAMAccountName?sub?(objectClass=*)"
AuthLDAPBindDN ldapuser@srv.world
AuthLDAPBindPassword Password
Require valid-user
</Directory>
[root@bizantum ~]# chgrp apache /etc/httpd/conf.d/authnz_ldap.conf
[root@bizantum ~]# chmod 640 /etc/httpd/conf.d/authnz_ldap.conf
[root@bizantum ~]# systemctl restart httpd
# create a test page
[root@bizantum ~]# mkdir /var/www/html/auth-ldap
[root@bizantum ~]# vi /var/www/html/auth-ldap/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
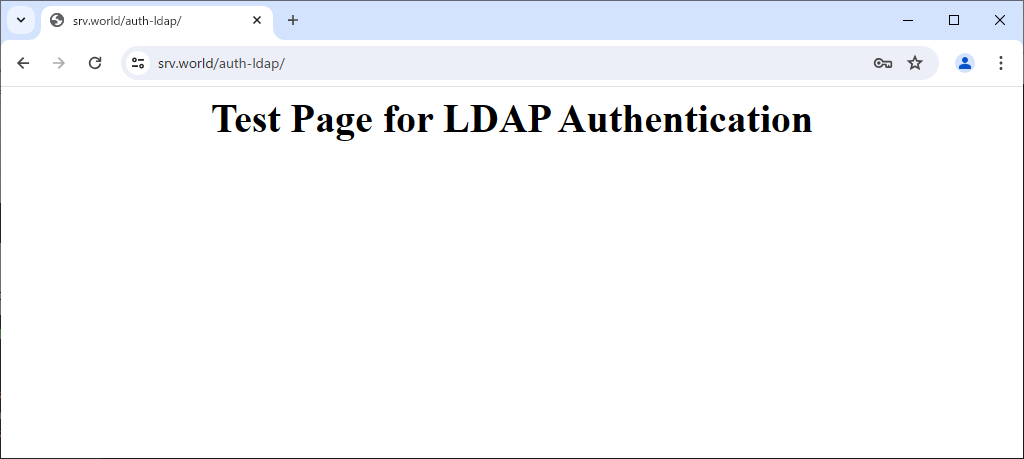
Test Page for LDAP Authentication
</div>
</body>
</html>
Step [5]If SELinux is enabled, change policy like follows.
[root@bizantum ~]# setsebool -P httpd_can_network_connect on
[root@bizantum ~]# setsebool -P httpd_can_connect_ldap on
Step [6]Access to the test page from any client computer with web browser. Then authentication is required as settings, answer with any AD user.
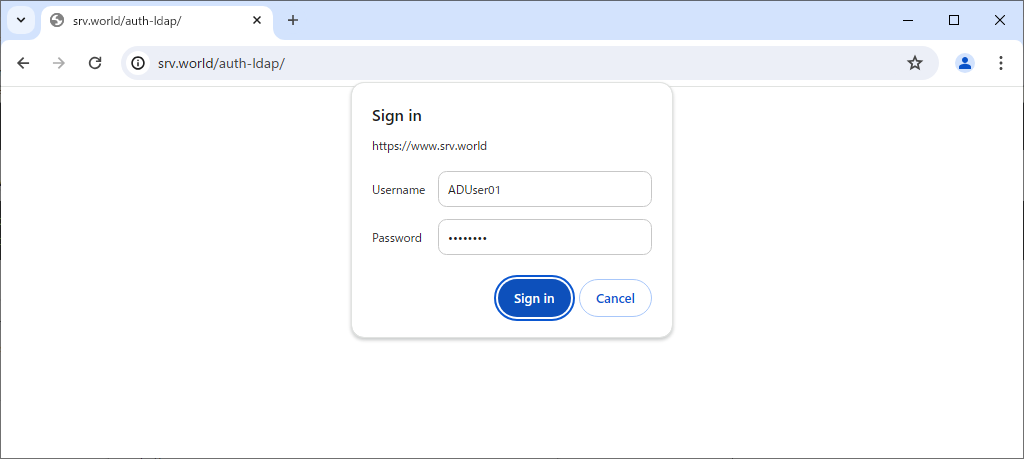
Step [7]That's OK if authentication is successfully passed and test page is displayed normally.
Apache httpd : Configure mod_md
Install and Configure [mod_md] to automate managing certificates from Let's Encrypt. It's possible to configure each VirtualHost. And it's not need to configure manual SSL/TLS setting like here for the Site with [mod_md]. Also it needs that it's possible to access from the Internet to the Site with [mod_md] because of verification from Let's Encrypt.
Step [1]Install [mod_md].
[root@bizantum ~]# dnf -y install mod_md
[root@bizantum ~]# systemctl restart httpd
# after installing, [mod_md] is enabled
[root@bizantum ~]# cat /etc/httpd/conf.modules.d/01-md.conf
LoadModule md_module modules/mod_md.so
Step [2]Configure [mod_md].
[root@bizantum ~]# vi /etc/httpd/conf.d/acme.conf
# create new
MDBaseServer on
MDCertificateProtocol ACME
MDCAChallenges http-01
MDDriveMode auto
MDPrivateKeys RSA 2048
MDRenewWindow 33%
MDStoreDir md
MDCertificateAuthority https://acme-v02.api.letsencrypt.org/directory
MDCertificateAgreement https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf
<Location "/md-status">
SetHandler md-status
Require ip 127.0.0.1 10.0.0.0/24
</Location>
# [MDRenewWindow]
# default is [33%] if not specified
# if validity of certificates falls specified duration,
# [mod_md] will get new certificates
# 90 days * 33% ≒ 30 days
# if you'd like to set with day, specify [d]
# 30 days ⇒ [30d]
# [MDStoreDir]
# the directory certificates or other data are stored
# if not specified, default is [md]
# it is relative path from [ServerRoot] in [httpd.conf]
# [md-status]
# monitor MD status
Step [3]If SELinux is enabled, change policy.
[root@bizantum ~]# setsebool -P httpd_can_network_connect on
[root@bizantum ~]# vi mod-md.te
# create new
module mod-md 1.0;
require {
type httpd_config_t;
type httpd_t;
class dir { add_name create remove_name rename reparent rmdir setattr write };
class file { create rename setattr unlink write };
}
#============= httpd_t ==============
allow httpd_t httpd_config_t:dir { add_name create remove_name rename reparent rmdir setattr write };
allow httpd_t httpd_config_t:file { create rename setattr unlink write };
[root@bizantum ~]# checkmodule -m -M -o mod-md.mod mod-md.te
[root@bizantum ~]# semodule_package --outfile mod-md.pp --module mod-md.mod
[root@bizantum ~]# semodule -i mod-md.pp
Step [4]Configure each VirtualHost you'd like to set [mod_md]. It needs to specify valid email address for each [ServerAdmin] directive because Let's Encrypt will send various notification.
# for example, set on the site [rx-9.srv.world] site
[root@bizantum ~]# vi /etc/httpd/conf.d/rx-9.srv.world.conf
MDomain rx-9.srv.world
MDCertificateAgreement accepted
DirectoryIndex index.html
ServerAdmin root@rx-9.srv.world
<VirtualHost *:80>
DocumentRoot /var/www/rx-9.srv.world
ServerName rx-9.srv.world
</VirtualHost>
<VirtualHost *:443>
SSLEngine on
DocumentRoot /var/www/rx-9.srv.world
ServerName rx-9.srv.world
</VirtualHost>
[root@bizantum ~]# systemctl reload httpd
# on initial start, some validation checks run and
# dumy certificate is created under the directory you set for [MDStoreDir]
[root@bizantum ~]# ll /etc/httpd/md/domains/rx-9.srv.world
total 12
-rw-------. 1 root root 1704 May 14 13:19 fallback-privkey.pem
-rw-------. 1 root root 1168 May 14 13:19 fallback-pubcert.pem
-rw-------. 1 root root 596 May 14 13:19 md.json
# reload again
[root@bizantum ~]# systemctl reload httpd
# if all checks passed, valid certificate is gotten
[root@bizantum ~]# ll /etc/httpd/md/domains/rx-9.srv.world
total 20
-rw-------. 1 root root 4895 May 14 13:19 job.json
-rw-------. 1 root root 654 May 14 13:19 md.json
-rw-------. 1 root root 1704 May 14 13:19 privkey.pem
-rw-------. 1 root root 3591 May 14 13:19 pubcert.pem
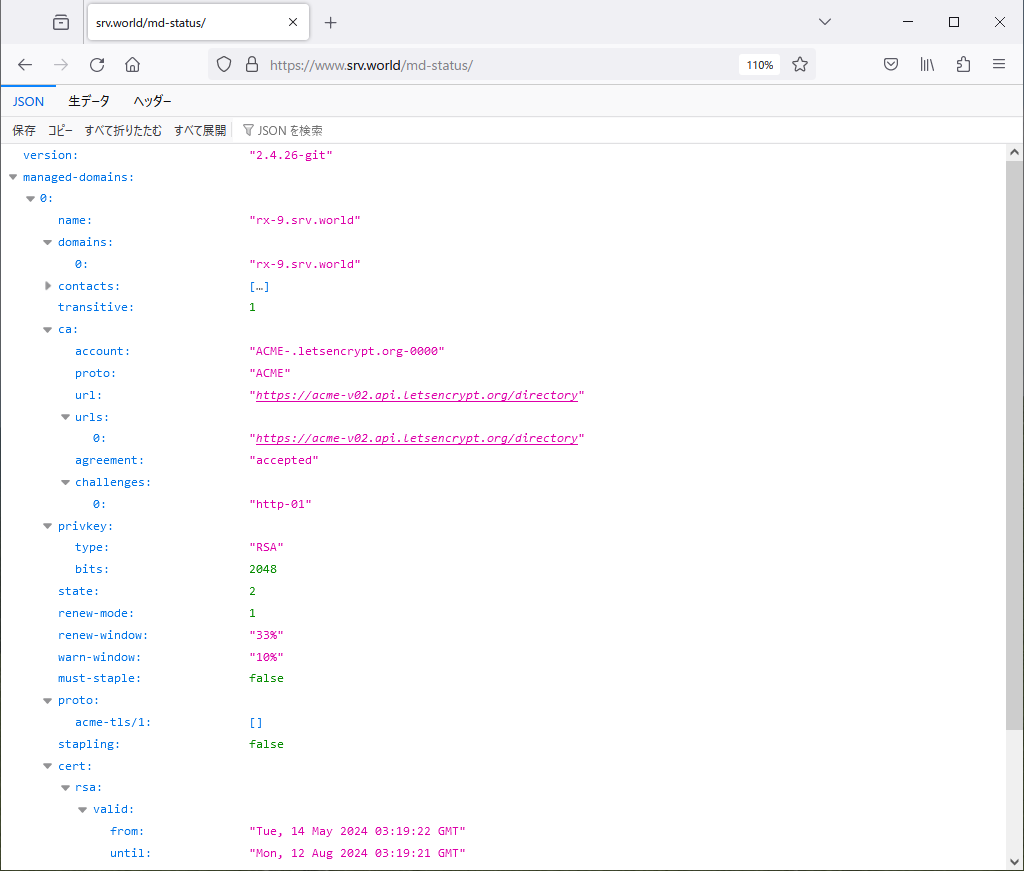
Step [5]It's possible to confirm expiration date and others of certificate with [openssl] command like follows. Or it's possible to see them to access to the URL of [md-status] you set on [2].
[root@bizantum ~]# openssl s_client -connect rx-9.srv.world:443 | openssl x509 -noout -startdate -enddate
depth=2 C=US, O=Internet Security Research Group, CN=ISRG Root X1
verify return:1
depth=1 C=US, O=Let's Encrypt, CN=R3
verify return:1
depth=0 CN=rx-9.srv.world
verify return:1
notBefore=May 14 03:19:22 2024 GMT
notAfter=Aug 12 03:19:21 2024 GMT
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.