
Introduction
This guide covers the installation and configuration of HAProxy on Fedora 40. HAProxy is a free, very fast, and reliable solution offering high availability, load balancing, and proxying for TCP and HTTP-based applications.
Overview
What
HAProxy (High Availability Proxy) is a fast and reliable solution for providing high availability, load balancing, and proxying for TCP and HTTP-based applications. It is widely used in the industry to improve the performance and reliability of web applications by distributing the workload across multiple servers.
Who
This guide is intended for system administrators and IT professionals who are responsible for managing network services and want to implement HAProxy to enhance the availability and performance of their applications on Fedora 40.
Where
The steps outlined in this guide should be performed on a Fedora 40 system with administrative privileges. Ensure that your system is connected to the internet and has sufficient resources to run HAProxy effectively.
When
This guide can be followed whenever you need to set up high availability and load balancing for your applications on Fedora 40. There are no specific timing requirements, but make sure to perform regular maintenance and updates to keep HAProxy running smoothly.
Why
Installing HAProxy on Fedora 40 provides several advantages, including improved application performance and increased reliability. However, there are also some potential drawbacks to consider.
| Pros | Cons |
|---|---|
| Improved application performance through load balancing | Requires proper configuration and regular maintenance |
| Increased reliability and availability of applications | Potential complexity in setting up and managing HAProxy |
| Enhanced security features for web applications | Additional resources needed for managing the proxy functions |
| Supports multiple protocols (TCP, HTTP, HTTPS) | Possible issues if misconfigured, leading to downtime |
How
Follow these steps to set up Apache HTTPD on Fedora 40:
Follow these steps to install and configure HAProxy on Fedora 40:
- Update your system: sudo dnf update -y
- Install HAProxy: sudo dnf install haproxy -y
- Start and enable HAProxy service: sudo systemctl start haproxy and sudo systemctl enable haproxy
- Edit the HAProxy configuration file: sudo nano /etc/haproxy/haproxy.cfg
- Add necessary configuration settings (e.g., front-end and back-end definitions, load balancing algorithms)
- Restart the HAProxy service: sudo systemctl restart haproxy
- Verify HAProxy is running: sudo systemctl status haproxy
Consequences
Implementing HAProxy on Fedora 40 can have several consequences:
| Positive |
|
| Negative |
|
Conclusion
Installing and configuring HAProxy on Fedora 40 can significantly improve the performance and reliability of your applications. While there are some potential drawbacks, such as the need for proper configuration and maintenance, the benefits of using HAProxy as a load balancer and proxy outweigh the disadvantages. By following this guide, system administrators can set up HAProxy efficiently and ensure their applications operate smoothly and securely.
HTTP Load Balancing
Install HAProxy to configure Load Balancing Server. This example is based on the environment like follows.
-----------+---------------------------+--------------------------+------------
| | |
|10.0.0.30 |10.0.0.51 |10.0.0.52
+----------+------------+ +----------+------------+ +---------+--------------+
| [ dlp.bizantum.lab ] | | [node01.bizantum.lab] | | [node02.bizantum.lab] |
| HAProxy | | Web Server#1 | | Web Server#2 |
+-----------------------+ +-----------------------+ +------------------------+
Configure Servers that HTTP connection to HAProxy Server is forwarded to backend Web Servers.
Step [1]Install HAProxy.
[root@bizantum ~]# dnf -y install haproxy
Step [2]Configure HAProxy.
[root@bizantum ~]# vi /etc/haproxy/haproxy.cfg
# comment out all for existing [frontend ***] [backend ***] sections
# and add follows to the end
# define frontend ( any name is OK for [http-in] )
frontend http-in
# listen 80 port
bind *:80
# set default backend
default_backend backend_servers
# send X-Forwarded-For header
option forwardfor
# define backend
backend backend_servers
# balance with roundrobin
balance roundrobin
# define backend servers
server node01 10.0.0.51:80 check
server node02 10.0.0.52:80 check
[root@bizantum ~]# systemctl enable --now haproxy
Step [3]If Firewalld is running, allow ports HAProxy listens.
[root@bizantum ~]# firewall-cmd --add-service=http
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [4]By default setting of HAproxy, logs are sent to [local2] facility, so Configure Rsyslog to record it to a file.
[root@bizantum ~]# vi /etc/rsyslog.conf
# line 31, 32 : uncomment and add a line
module(load="imudp") # needs to be done just once
input(type="imudp" port="514")
$AllowedSender UDP, 127.0.0.1
# line 47 : change like follows
*.info;mail.none;authpriv.none;cron.none;local2.none /var/log/messages
local2.* /var/log/haproxy.log
[root@bizantum ~]# systemctl restart rsyslog
Step [5]Change settings on Backend Web servers (Apache httpd on this example) to logging X-Forwarded-For header.
[root@node01 ~]# vi /etc/httpd/conf/httpd.conf
# line 201, 202 : change like follows
LogFormat "\"%{X-Forwarded-For}i\" %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" combined
LogFormat "\"%{X-Forwarded-For}i\" %l %u %t \"%r\" %>s %b" common
[root@node01 ~]# systemctl restart httpd
Step [6]Verify working normally to access to frontend HAproxy Server.
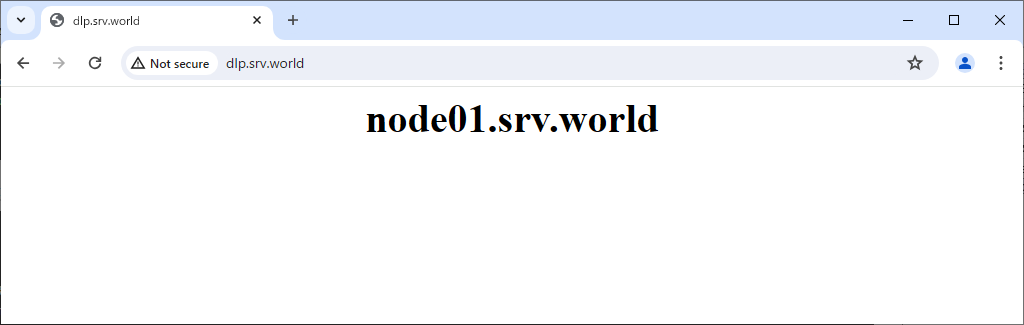
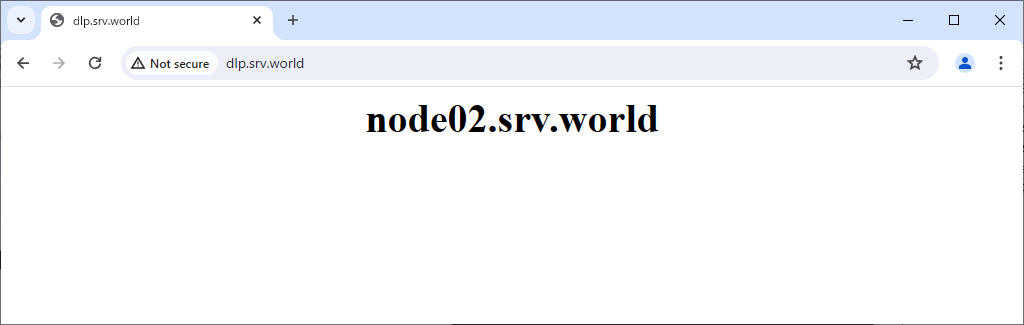
SSL/TLS Setting
Configure HAProxy with SSL/TLS connection. The connection between HAproxy and Clients are encrypted with SSL.
-----------+---------------------------+--------------------------+------------
| | |
|10.0.0.30 |10.0.0.51 |10.0.0.52
+----------+-----------+ +-----------+-----------+ +-----------+------------+
| [ dlp.bizantum.lab ] | | [node01.bizantum.lab] | | [node02.bizantum.lab] |
| HAProxy | | Web Server#1 | | Web Server#2 |
+----------------------+ +-----------------------+ +------------------------+
Step [1]Get SSL certificates, refer to here.
Step [2]In addition to previous basic HTTP Load Balancing setting, add settings for SSL/TLS.
# concatenate cert and key
[root@bizantum ~]# cat /etc/letsencrypt/live/dlp.bizantum.lab/{fullchain.pem,privkey.pem} > /etc/haproxy/haproxy.pem
[root@bizantum ~]# vi /etc/haproxy/haproxy.cfg
# add into frontend section
# * comment out the 80 port line if you do not need unencrypted connection
frontend http-in
bind *:80
bind *:443 ssl crt /etc/haproxy/haproxy.pem
[root@bizantum ~]# systemctl reload haproxy
Step [3]If Firewalld is running, allow ports HAProxy listens.
[root@bizantum ~]# firewall-cmd --add-service=https
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [4]Verify working normally to access to frontend HAproxy Server.
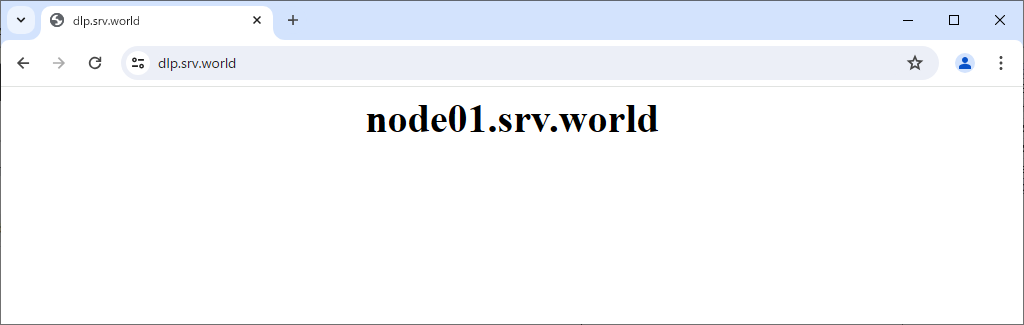
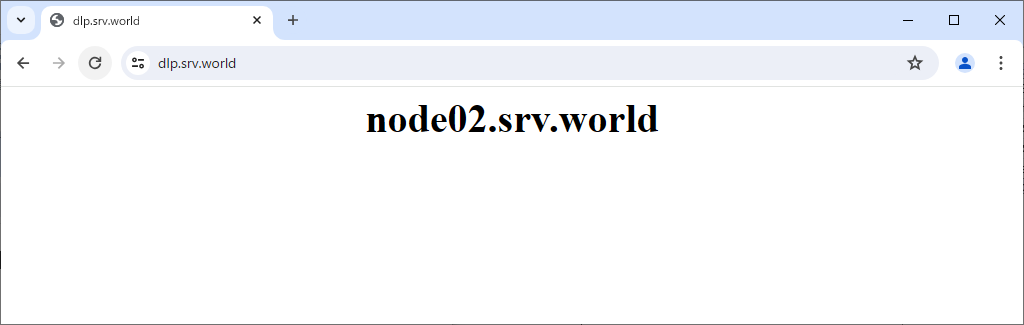
Refer to the Statistics (Web)
Configure HAProxy to see HAProxy's Statistics on the web.
Step [1]In addition to previous basic setting, Configure HAProxy.
[root@bizantum ~]# vi /etc/haproxy/haproxy.cfg
# add into [backend] section
backend backend_servers
# enable statistics reports
stats enable
# auth info for statistics site
stats auth admin:adminpassword
# hide version of HAProxy
stats hide-version
# display HAProxy hostname
stats show-node
# refresh time
stats refresh 60s
# statistics reports URI
stats uri /haproxy?stats
[root@bizantum ~]# systemctl reload haproxy
Step [2]Access to the frontend HAProxy server from a Client Host with HTTP/HTTPS, then authentication is required like follows, input the user and password you set in configuration.
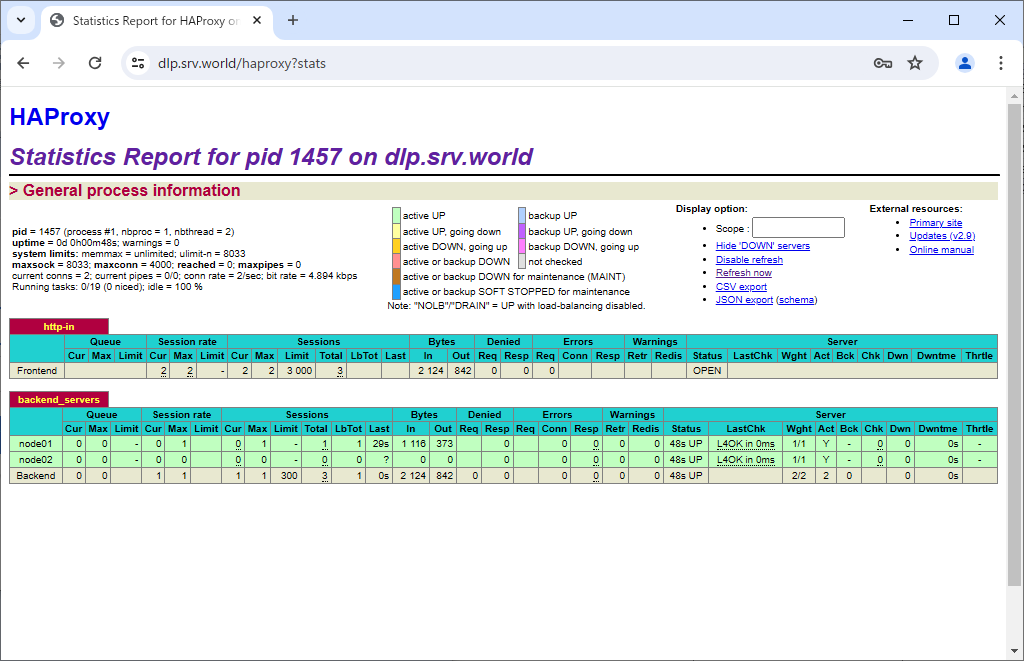
Step [3]If authentication successfully passed, it's possible to see HAProxy Statistics Reports.
Refer to the Statistics (CUI)
Configure HAProxy to see HAProxy Statistics Reports with commands.
Step [1]Install required package.
[root@bizantum ~]# dnf -y install socat
Step [2]Configure HAProxy.
[root@bizantum ~]# vi /etc/haproxy/haproxy.cfg
# confirm settings
# OK if following line exists in [global] section
global
.....
.....
stats socket /var/lib/haproxy/stats
[root@bizantum ~]# systemctl reload haproxy
Step [3]Refer to the Statistics like follows.
# display current stats
[root@bizantum ~]# echo "show info" | socat /var/lib/haproxy/stats stdio
Name: HAProxy
Version: 2.9.4-4e071ad
Release_date: 2024/01/31
Nbthread: 2
Nbproc: 1
Process_num: 1
Pid: 1457
Uptime: 0d 0h03m57s
Uptime_sec: 237
Memmax_MB: 0
PoolAlloc_MB: 0
.....
.....
Start_time_sec: 1715824155
Tainted: 0
TotalWarnings: 0
MaxconnReached: 0
BootTime_ms: 10
Niced_tasks: 0
# display current stats with CSV style
[root@bizantum ~]# echo "show stat" | socat /var/lib/haproxy/stats stdio
# pxname,svname,qcur,qmax,scur,smax,slim,stot,bin,bout,dreq,dresp,ereq,econ,eresp,wretr,wredis,status,weight,act,bck,chkfail,chkdown,lastchg,downtime,qlimit,pid,iid,sid,throttle,lbtot,tracked,type,rate,rate_lim,rate_max,check_status,check_code,check_duration,hrsp_1xx,hrsp_2xx,hrsp_3xx,hrsp_4xx,hrsp_5xx,hrsp_other,hanafail,req_rate,req_rate_max,req_tot,cli_abrt,srv_abrt,comp_in,comp_out,comp_byp,comp_rsp,lastsess,last_chk,last_agt,qtime,ctime,rtime,ttime,agent_status,agent_code,agent_duration,check_desc,agent_desc,check_rise,check_fall,check_health,agent_rise,agent_fall,agent_health,addr,cookie,mode,algo,conn_rate,conn_rate_max,conn_tot,intercepted,dcon,dses,wrew,connect,reuse,cache_lookups,cache_hits,srv_icur,src_ilim,qtime_max,ctime_max,rtime_max,ttime_max,eint,idle_conn_cur,safe_conn_cur,used_conn_cur,need_conn_est,uweight,agg_server_status,agg_server_check_status,agg_check_status,srid,sess_other,h1sess,h2sess,h3sess,req_other,h1req,h2req,h3req,proto,-,ssl_sess,ssl_reused_sess,ssl_failed_handshake,h2_headers_rcvd,h2_data_rcvd,h2_settings_rcvd,h2_rst_stream_rcvd,h2_goaway_rcvd,h2_detected_conn_protocol_errors,h2_detected_strm_protocol_errors,h2_rst_stream_resp,h2_goaway_resp,h2_open_connections,h2_backend_open_streams,h2_total_connections,h2_backend_total_streams,h1_open_connections,h1_open_streams,h1_total_connections,h1_total_streams,h1_bytes_in,h1_bytes_out,h1_spliced_bytes_in,h1_spliced_bytes_out,
http-in,FRONTEND,,,0,2,3000,3,3201,19973,0,0,1,,,,,OPEN,,,,,,,,,1,2,0,,,,0,0,0,2,,,,0,2,0,2,0,0,,0,1,4,,,0,0,0,0,,,,,,,,,,,,,,,,,,,,,http,,0,2,3,0,0,0,0,,,0,0,,,,,,,0,,,,,,,,,,0,1,2,0,0,1,3,0,,-,1,1,0,3,0,6,0,0,0,0,0,0,0,0,2,3,0,0,1,0,0,233,0,0,
backend_servers,node01,0,0,0,1,,1,1116,373,,0,,0,0,0,0,UP,1,1,0,0,0,280,0,,1,3,1,,1,,2,0,,1,L4OK,,0,0,1,0,0,0,0,,,,1,0,0,,,,,261,,,0,0,1,6,,,,Layer4 check passed,,2,3,4,,,,10.0.0.51:80,,http,,,,,,,,0,1,0,,,0,,0,0,1,6,0,0,0,0,1,1,,,,0,,,,,,,,,,-,0,0,0,,,,,,,,,,,,,,,,,,,,,,
backend_servers,node02,0,0,0,0,,0,0,0,,0,,0,0,0,0,UP,1,1,0,0,0,280,0,,1,3,2,,0,,2,0,,0,L4OK,,0,0,0,0,0,0,0,,,,0,0,0,,,,,-1,,,0,0,0,0,,,,Layer4 check passed,,2,3,4,,,,10.0.0.52:80,,http,,,,,,,,0,0,0,,,0,,0,0,0,0,0,0,0,0,1,1,,,,0,,,,,,,,,,-,0,0,0,,,,,,,,,,,,,,,,,,,,,,
backend_servers,BACKEND,0,0,0,1,300,3,3201,19973,0,0,,0,0,0,0,UP,2,2,0,,0,280,0,,1,3,0,,1,,1,0,,1,,,,0,2,0,1,0,0,,,,3,1,0,0,0,0,0,232,,,0,0,1,3,,,,,,,,,,,,,,http,roundrobin,,,,,,,0,1,0,0,0,,,0,0,1,6,0,,,,,2,0,0,0,,,,,,,,,,,-,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,405,1202,0,0,
# display current session
[root@bizantum ~]# echo "show sess" | socat /var/lib/haproxy/stats stdio
0x557788101d90: proto=unix_stream src=unix:1 fe=GLOBAL be=<NONE> srv=<none> ts=00 epoch=0 age=0s calls=1 rate=0 cpu=0 lat=0 rq[f=808000h,i=0,an=00h,ax=] rp[f=80008000h,i=0,an=00h,ax=] scf=[8,600h,fd=14,rex=,wex=] scb=[8,1h,fd=-1,rex=,wex=] exp=10s rc=0 c_exp=
Layer 4 Load Balancing
Configure HAProxy on Layer 4 Mode. On this example, configure MariaDB backend like the following environment.
-----------+---------------------------+--------------------------+------------
| | |
|10.0.0.30 |10.0.0.51 |10.0.0.52
+----------+-----------+ +-----------+------------+ +---------+------------+
| [ dlp.bizantum.lab ] | | [node01.bizantum.lab] | | [node02.bizantum.lab]|
| HAProxy | | MariaDB Server#1 | | MariaDB Server#2 |
+----------------------+ +------------------------+ +----------------------+
Step [1]Configure HAProxy.
[root@bizantum ~]# vi /etc/haproxy/haproxy.cfg
# change [mode] value in [defaults] section
defaults
mode tcp
# define MariaDB for frontend, backend
frontend mysql-in
bind *:3306
default_backend backend_servers
backend backend_servers
balance roundrobin
server node01 10.0.0.51:3306 check
server node02 10.0.0.52:3306 check
[root@bizantum ~]# systemctl restart haproxy
Step [2]If SELinux is enabled, change boolean setting.
[root@bizantum ~]# setsebool -P haproxy_connect_any on
Step [3]If Firewalld is running, allow ports HAProxy listens.
[root@bizantum ~]# firewall-cmd --add-service=mysql
success
[root@bizantum ~]# firewall-cmd --runtime-to-permanent
success
Step [4]Verify working normally to access to frontend HAproxy Server.
[root@client ~]# mysql -u bizantum -p -h dlp.bizantum.lab -e "show variables like 'hostname';"
Enter password:
+---------------+---------------------+
| Variable_name | Value |
+---------------+---------------------+
| hostname | node02.bizantum.lab |
+---------------+---------------------+
[root@client ~]# mysql -u bizantum -p -h dlp.bizantum.lab -e "show variables like 'hostname';"
Enter password:
+---------------+---------------------+
| Variable_name | Value |
+---------------+---------------------+
| hostname | node01.bizantum.lab |
+---------------+---------------------+
- Get link
- X
- Other Apps









Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.