
Introduction
Welcome to Fedora 40! This guide will help you get started with the essential settings you need to configure after installing Fedora 40. Whether you're a new user or an experienced one, getting your system set up correctly ensures a smooth and efficient experience. let's get started.
System Updates
After Fedora Server has been a production System, maybe it's difficult to update System, but at least after Installing, Update Fedora Server to the latest.
Step [1]Update System like follows.
dnf -y upgrade[root@bizantum ~]# dnf -y upgrade Fedora 40 - x86_64 8.9 MB/s | 20 MB 00:02 Fedora 40 openh264 (From Cisco) - x86_64 1.1 kB/s | 1.8 kB 00:01 Fedora 40 - x86_64 - Updates 2.7 MB/s | 2.1 MB 00:00 Last metadata expiration check: 0:00:01 ago on Wed 24 Apr 2024 10:03:24 AM JST. Dependencies resolved. ================================================================================ Package Arch Version Repo Size ================================================================================ Installing: kernel x86_64 6.8.7-300.fc40 updates 159 k Upgrading: amd-gpu-firmware noarch 20240410-1.fc40 updates 18 M amd-ucode-firmware noarch 20240410-1.fc40 updates 243 k atheros-firmware noarch 20240410-1.fc40 updates 26 M b43-fwcutter x86_64 019-36.fc40 updates 30 k bluez x86_64 5.75-1.fc40 updates 1.1 M bluez-libs x86_64 5.75-1.fc40 updates 83 k brcmfmac-firmware noarch 20240410-1.fc40 updates 9.6 M c-ares x86_64 1.28.1-1.fc40 updates 158 k cirrus-audio-firmware noarch 20240410-1.fc40 updates 1.2 M cryptsetup x86_64 2.7.2-1.fc40 updates 326 k cryptsetup-libs x86_64 2.7.2-1.fc40 updates 527 k curl x86_64 8.6.0-8.fc40 updates 301 k dbus-broker x86_64 36-2.fc40 updates 171 k dnf noarch 4.19.2-1.fc40 updates 504 k dnf-data noarch 4.19.2-1.fc40 updates 40 k ..... ..... Installed: kernel-6.8.7-300.fc40.x86_64 kernel-core-6.8.7-300.fc40.x86_64 kernel-modules-6.8.7-300.fc40.x86_64 kernel-modules-core-6.8.7-300.fc40.x86_64 rpm-plugin-systemd-inhibit-4.19.1.1-1.fc40.x86_64 sqlite-3.45.1-2.fc40.x86_64 tpm2-tools-5.6-2.fc40.x86_64 tpm2-tss-fapi-4.0.1-7.fc40.x86_64 Complete!
User Account Management
To add user accounts on Fedora Server, Configure like follows.
Step [1]For example, Add [fedora] user.
useradd fedora
passwd fedora
[root@bizantum ~]# useradd fedora [root@bizantum ~]# passwd fedora Changing password for user fedora. New UNIX password: # input any password you'd like to set Retype new UNIX password: # confirm passwd: all authentication tokens updated successfully.
Step [2]If you'd like to switch to root account from a user added above, use [su] command to do so.
su -bizantum login: fedora # login username password: # input user password [fedora@bizantum ~]$ su - # switch to root Password: # input root password [root@bizantum ~]#
Step [3] If you'd like to limit users to run [su] command, configure like follows. On the example below, only users in [wheel] group can run [su] command.
usermod -aG wheel fedora
vi /etc/pam.d/su
su -
[root@bizantum ~]# usermod -aG wheel fedora [root@bizantum ~]# vi /etc/pam.d/su #%PAM-1.0 auth sufficient pam_rootok.so # Uncomment the following line to implicitly trust users in the "wheel" group. #auth sufficient pam_wheel.so trust use_uid # Uncomment the following line to require a user to be in the "wheel" group. # uncomment the following line auth required pam_wheel.so use_uid auth substack system-auth auth include postlogin account sufficient pam_succeed_if.so uid = 0 use_uid quiet account include system-auth password include system-auth session include system-auth session include postlogin session optional pam_xauth.so # verify settings with a user that is not in allowed group [redhat@bizantum ~]$ su - Password: su: Permission denied # denied normally
Step [4]If you'd like to remove a user accounts, Set like follows.
userdel fedora
userdel -r fedora
# remove a user [fedora] (only removed user account) [root@bizantum ~]# userdel fedora # remove a user [fedora] (removed user account and his home directory both) [root@bizantum ~]# userdel -r fedora
Network Configuration
If you did not configure network settings during the Fedora Server Installation, Configure it like follows.
Step [1]Set static IP address to the server. ( Replace the interface name [enp1s0] to your own one because it's not the same on any System )
hostnamectl set-hostname dns1.bizantum.local
nmcli connection
nmcli connection modify enp1s0 ipv4.addresses 10.0.0.30/24
nmcli connection modify enp1s0 ipv4.gateway 10.0.0.1
nmcli connection modify enp1s0 ipv4.dns 10.0.0.10
nmcli connection modify enp1s0 ipv4.dns-search srv.world
nmcli connection modify enp1s0 ipv4.method manual
nmcli connection up enp1s0
nmcli device show enp1s0
ip address show
# if you did not set HostName, set it like follows
[root@bizantum ~]# hostnamectl set-hostname dns1.bizantum.local
# display connections
[root@bizantum ~]# nmcli connection
NAME UUID TYPE DEVICE
enp1s0 29640ff0-a471-3f92-b3b1-a99a0c81f6e9 ethernet enp1s0
lo 3dd5c324-4e05-44d4-bab2-a0ced0f08468 loopback lo
# set IPv4 address
[root@bizantum ~]# nmcli connection modify enp1s0 ipv4.addresses 10.0.0.30/24
# set gateway
[root@bizantum ~]# nmcli connection modify enp1s0 ipv4.gateway 10.0.0.1
# set DNS
# if set multiple DNS, specify with space separated ⇒ ipv4.dns "10.0.0.10 10.0.0.11 10.0.0.12"
[root@bizantum ~]# nmcli connection modify enp1s0 ipv4.dns 10.0.0.10
# set DNS search base (your domain name)
[root@bizantum ~]# nmcli connection modify enp1s0 ipv4.dns-search srv.world
# set manual for static setting (it's [auto] for DHCP)
[root@bizantum ~]# nmcli connection modify enp1s0 ipv4.method manual
# restart the interface to reload settings
[root@bizantum ~]# nmcli connection up enp1s0
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/3)
# confirm settings
[root@bizantum ~]# nmcli device show enp1s0
GENERAL.DEVICE: enp1s0
GENERAL.TYPE: ethernet
GENERAL.HWADDR: 52:54:00:89:1B:BD
GENERAL.MTU: 1500
GENERAL.STATE: 100 (connected)
GENERAL.CONNECTION: enp1s0
GENERAL.CON-PATH: /org/freedesktop/NetworkManager/ActiveC>
WIRED-PROPERTIES.CARRIER: on
IP4.ADDRESS[1]: 10.0.0.30/24
IP4.GATEWAY: 10.0.0.1
IP4.ROUTE[1]: dst = 0.0.0.0/0, nh = 10.0.0.1, mt = 100
IP4.ROUTE[2]: dst = 10.0.0.0/24, nh = 0.0.0.0, mt = 1>
IP4.DNS[1]: 10.0.0.10
IP4.SEARCHES[1]: srv.world
IP6.ADDRESS[1]: fe80::5054:ff:fe89:1bbd/64
IP6.GATEWAY: --
IP6.ROUTE[1]: dst = fe80::/64, nh = ::, mt = 1024
# confirm state
[root@bizantum ~]# ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:89:1b:bd brd ff:ff:ff:ff:ff:ff
inet 10.0.0.30/24 brd 10.0.0.255 scope global noprefixroute enp1s0
valid_lft forever preferred_lft forever
inet6 fe80::5054:ff:fe89:1bbd/64 scope link noprefixroute
valid_lft forever preferred_lft forever
Step [2]If you don't need IPv6, it's possible to disable it like follows.
grubby --update-kernel ALL --args ipv6.disable=1
reboot
ip address show
grubby --update-kernel ALL --remove-args ipv6.disable
# disable IPv6
[root@bizantum ~]# grubby --update-kernel ALL --args ipv6.disable=1
[root@bizantum ~]# reboot
[root@bizantum ~]# ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:89:1b:bd brd ff:ff:ff:ff:ff:ff
inet 10.0.0.30/24 brd 10.0.0.255 scope global noprefixroute enp1s0
valid_lft forever preferred_lft forever
# if falling back to enable, run like follows
[root@bizantum ~]# grubby --update-kernel ALL --remove-args ipv6.disable
Services Management
To enable or disable services, Configure like follows.
Step [1]Display services list.
systemctl -t service
systemctl list-unit-files -t service
# the list of services that are active now
# to add [--all], display all included inactive services
# to add [--no-pager], do not use pagers like [less/more]
[root@bizantum ~]# systemctl -t service
UNIT LOAD ACTIVE SUB DESCRIPTION >
abrt-journal-core.service loaded active running ABRT coredumpc>
abrt-oops.service loaded active running ABRT kernel lo>
abrt-xorg.service loaded active running ABRT Xorg log >
abrtd.service loaded active running ABRT Daemon
atd.service loaded active running Deferred execu>
auditd.service loaded active running Security Audit>
chronyd.service loaded active running NTP client/ser>
crond.service loaded active running Command Schedu>
dbus-broker.service loaded active running D-Bus System M>
.....
.....
systemd-zram-setup@zram0.service loaded active exited Create swap on>
user-runtime-dir@0.service loaded active exited User Runtime D>
user@0.service loaded active running User Manager f>
Legend: LOAD �� Reflects whether the unit definition was properly loaded.
ACTIVE �� The high-level unit activation state, i.e. generalization of S>
SUB �� The low-level unit activation state, values depend on unit typ>
52 loaded units listed. Pass --all to see loaded but inactive units, too.
To show all installed unit files use 'systemctl list-unit-files'.
# list of all services
[root@bizantum ~]# systemctl list-unit-files -t service
UNIT FILE STATE PRESET
abrt-journal-core.service enabled enabled
abrt-oops.service enabled enabled
abrt-pstoreoops.service disabled disabled
abrt-vmcore.service enabled enabled
abrt-xorg.service enabled enabled
abrtd.service enabled enabled
arp-ethers.service disabled disabled
atd.service enabled enabled
audit-rules.service enabled enabled
auditd.service enabled enabled
.....
.....
udisks2.service enabled enabled
usb_modeswitch@.service static -
user-runtime-dir@.service static -
user@.service static -
wpa_supplicant.service disabled disabled
255 unit files listed.
Step [2]Stop and turn OFF auto-start setting for a service if you don't need it. The example below means stopping and disable smartd service.
systemctl disable --now smartd
[root@bizantum ~]# systemctl disable --now smartd
Firewall Management
Configure Firewall and SELinux.
Configure Firewall
Step [1]It's possible to see FireWall Service Status like follows. (enabled by default).
systemctl status firewalld
[root@bizantum ~]# systemctl status firewalld
* firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; preset>
Drop-In: /usr/lib/systemd/system/service.d
+-- 10-timeout-abort.conf
Active: active (running) since Wed 2024-04-24 09:37:26 JST; 7min ago
Docs: man:firewalld(1)
Main PID: 868 (firewalld)
Tasks: 2 (limit: 4637)
Memory: 42.2M (peak: 42.4M)
CPU: 244ms
CGroup: /system.slice/firewalld.service
.....
.....
# [Active: active (running) ***] means firewalld is running now
Step [2]If you use FireWall service, it needs to modify FireWall settings manually because incoming requests for services are mostly not allowed by default. Refer to here for basic Firewall operation and settings (CentOS Stream 9). Configuration examples of Fedora 40 on this site are based on the environment Firewalld service is always enabled.
Step [3]If you don't need FireWall service because of some reasons like that some FireWall Machines are running in your Local Netowrk or others, it's possible to stop and disable FireWall service on Fedora server like follows.
systemctl stop firewalld
systemctl disable firewalld
# stop service [root@bizantum ~]# systemctl stop firewalld # disable service [root@bizantum ~]# systemctl disable firewalld Removed "/etc/systemd/system/multi-user.target.wants/firewalld.service". Removed "/etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service".
Configure SELinux
Step [4]It's possible to show current SELinux (Security-Enhanced Linux) Status like follows. (enabled by default).
getenforce
[root@bizantum ~]# getenforce Enforcing # SELinux is enabled
Step [5]If you enable SELinux, there are cases to modify SELinux policy manually because sometimes SELinux stop applications. Refer to here for basic SELinux operation and settings (CentOS Stream 9). Configuration examples of Fedora 40 on this site are based on the environment SELinux is always Enforcing.
Step [6]If you don't need SELinux feature because of some reasons like that your server is running only in Local safety Network or others, it's possible to disable SELinux like follows.
grubby --update-kernel ALL --args selinux=0
reboot
grubby --update-kernel ALL --remove-args selinux
# disable SELinux [root@bizantum ~]# grubby --update-kernel ALL --args selinux=0 # restart computer to apply changes [root@bizantum ~]# reboot # if falling back to enable, run like follows [root@bizantum ~]# grubby --update-kernel ALL --remove-args selinux
Sudo Management
Configure Sudo to separate users' duty if some people share privileges. It does not need to install sudo manually because it is installed by default even if Minimal installed environment.
Step [1]Transfer root privilege all to a user.
visudo
/usr/bin/cat /etc/shadow
sudo /usr/bin/cat /etc/shadow
[root@bizantum ~]# visudo # add to last line : user [fedora] can use all root privilege fedora ALL=(ALL) ALL # how to write ⇒ destination host=(owner) command # verify with user [fedora] [fedora@bizantum ~]$ /usr/bin/cat /etc/shadow /usr/bin/cat: /etc/shadow: Permission denied # denied normally [fedora@bizantum ~]$ sudo /usr/bin/cat /etc/shadow [sudo] password for fedora: # user password ..... ..... dnsmasq:!:19837:::::: tcpdump:!:19837:::::: # executed
Step [2]In addition to the setting of [1], set some commands prohibit.
visudo
sudo /usr/sbin/reboot
[root@bizantum ~]# visudo # line 49 : add # for example, set alias for the kind of shutdown commands Cmnd_Alias SHUTDOWN = /usr/sbin/halt, /usr/sbin/shutdown, \ /usr/sbin/poweroff, /usr/sbin/reboot, /usr/sbin/init, /usr/bin/systemctl # add ( prohibit commands in alias [SHUTDOWN] ) fedora ALL=(ALL) ALL, !SHUTDOWN # verify with user [fedora] [fedora@bizantum ~]$ sudo /usr/sbin/reboot [sudo] password for fedora: Sorry, user fedora is not allowed to execute '/usr/sbin/reboot' as root on dns1.bizantum.local. # denied normally
Step [3]Transfer some commands with root privilege to users in a group.
visudo
groupadd usermgr
usermod -aG usermgr redhat
sudo /usr/sbin/useradd testuser
sudo /usr/bin/passwd testuser
[root@bizantum ~]# visudo # line 51 : add # for example, set alias for the kind of user management commands Cmnd_Alias USERMGR = /usr/sbin/useradd, /usr/sbin/userdel, /usr/sbin/usermod, \ /usr/bin/passwd # add to last line %usermgr ALL=(ALL) USERMGR [root@bizantum ~]# groupadd usermgr [root@bizantum ~]# usermod -aG usermgr redhat # verify with user [redhat] [redhat@bizantum ~]$ sudo /usr/sbin/useradd testuser [redhat@bizantum ~]$ sudo /usr/bin/passwd testuser New password: Retype new password: passwd: password updated successfully # executed
Step [4]Transfer a command with root privilege to a user.
visudo
sudo /usr/sbin/visudo
[root@bizantum ~]# visudo # add to the end : settings for each user fedora ALL=(ALL) /usr/sbin/visudo ubuntu ALL=(ALL) /usr/sbin/useradd, /usr/sbin/userdel, /usr/sbin/usermod, /usr/bin/passwd debian ALL=(ALL) /usr/bin/vi # for example, verify with user [fedora] [fedora@bizantum ~]$ sudo /usr/sbin/visudo ## Sudoers allows particular users to run various commands as ## the root user, without needing the root password. ## # executed
Step [5]It's possible to display Sudo logs on Journald ( with [journalctl] command ) or Rsyslogd ( in [/var/log/secure] file ), but if you'd like to keep only Sudo logs in another file, Configure like follows.
visudo
vi /etc/rsyslog.conf
systemctl restart rsyslog
[root@bizantum ~]# visudo # add to the end # for example, output logs to [local1] facility Defaults syslog=local1 [root@bizantum ~]# vi /etc/rsyslog.conf # line 47,48 : add like follows *.info;mail.none;authpriv.none;cron.none;local1.none /var/log/messages local1.* /var/log/sudo.log # The authpriv file has restricted access. authpriv.* /var/log/secure [root@bizantum ~]# systemctl restart rsyslog
Web Admin Console
Cockpit Admin Console is installed and starts by default if you installed [Fedora Server] group. It's possible to manage your Fedora server on this admin console on a web browser. If you'd like to access to Cockpit from remote computer and if Firewalld is running on your Fedora Server, it needs to allow service [cockpit] or allow port [9090]. (allowed them by default, though)
Step [1]Access to [https://(server's hostname or IP address):9090/] with Web browser from bizantum or Client compuer, then Cockpit login form is displayed like follows. Login with a user except root user account. (root login is prohibited by default )
Step [2]This is the Cockpit index page. It's possible to manage various system settings on here. If you like to use admin privilege, click the [Turn on administrative access] button to authenticate.
Step [3] For [Logs] on the left pane, it's possible to manage or operate [Journal] service that is the log management tool.
Step [4]For [Storage] on the left pane, it's possible to manage or operate Storages.
Step [5]For [Networking] on the left pane, it's possible to manage or operate Network settings.
Step [6]For [Accounts] on the left pane, it's possible to manage or operate system accounts.
Step [7]For [Services] on the left pane, it's possible to manage or operate system services.
Step [8]For [Applications] on the left pane, it's possible to install or remove applications.
Step [9]For [SELinux] on the left pane, it's possible to see SELinux alert logs. (based on SELinux enabled state).
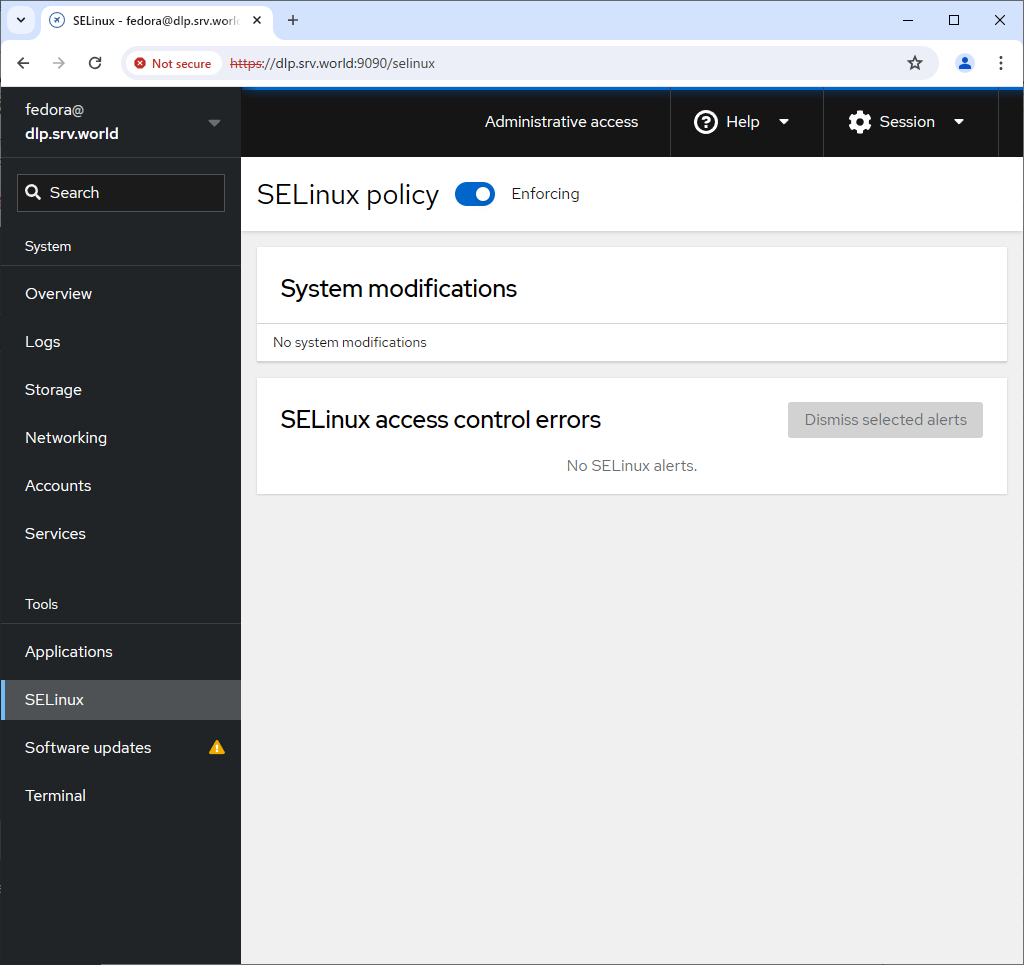
Step [10]For [Software Updates] on the left pane, it's possible to confirm updates or run update packages.
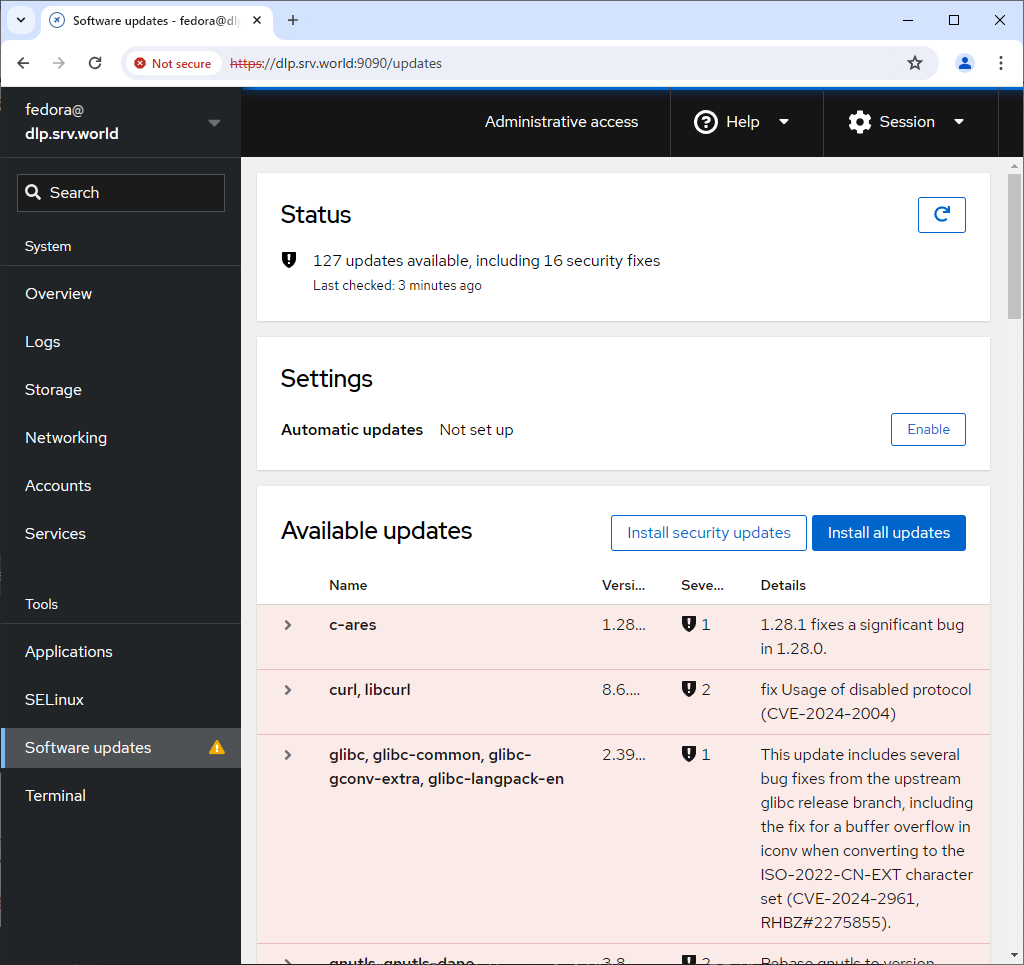
Step [11]For [Terminal] on the left pane, it's possible to operate system with commands directly.
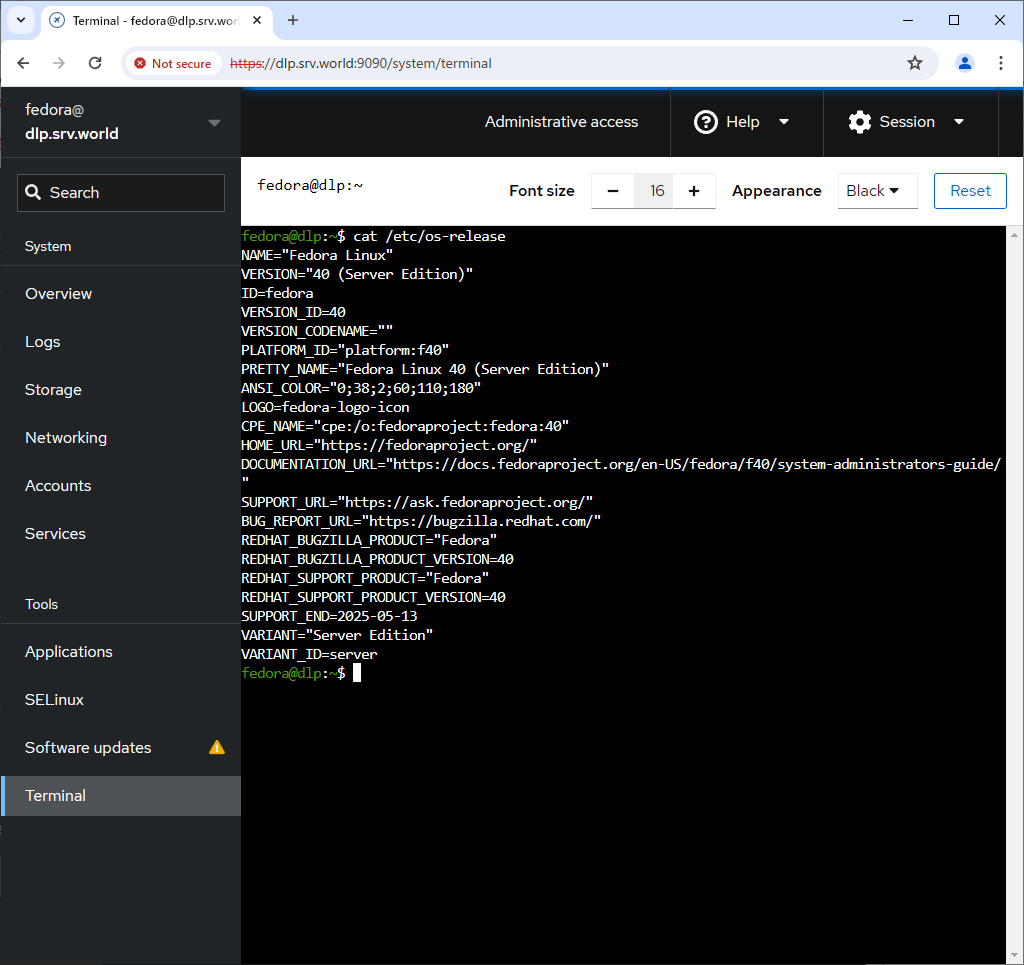
- Get link
- X
- Other Apps








Comments
Post a Comment
Thank you for your comment! We appreciate your feedback, feel free to check out more of our articles.
Best regards, Bizantum Blog Team.